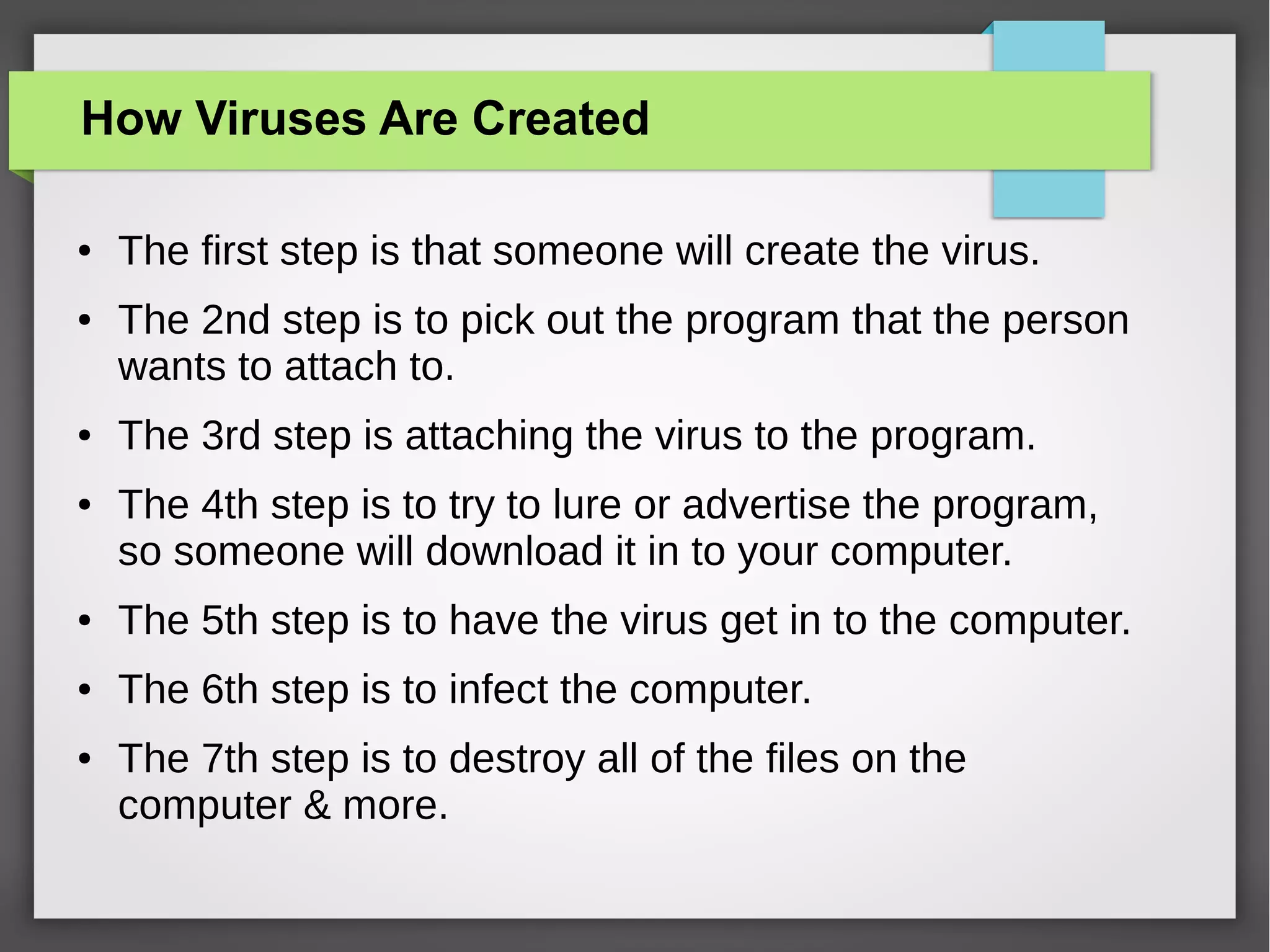
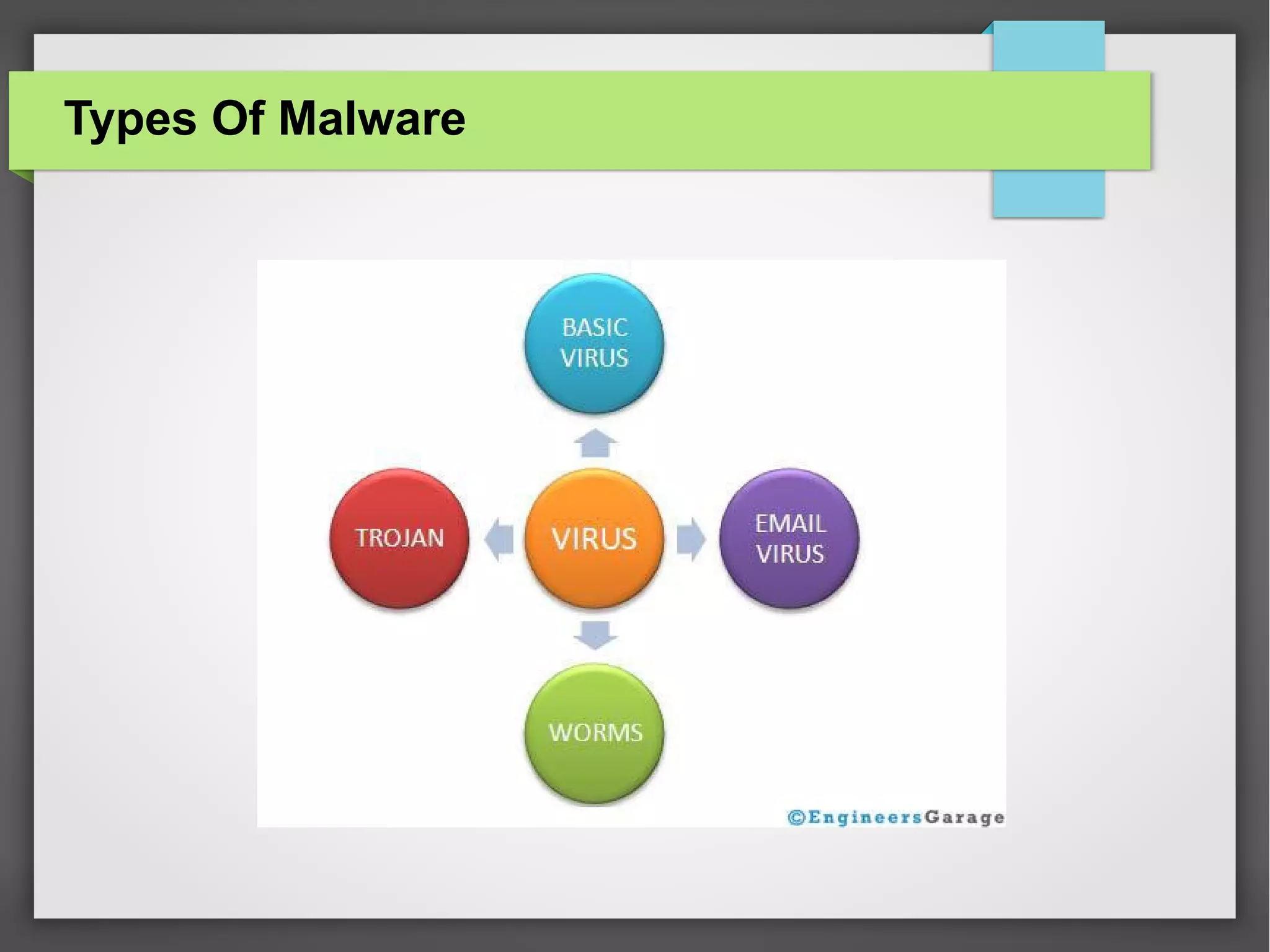
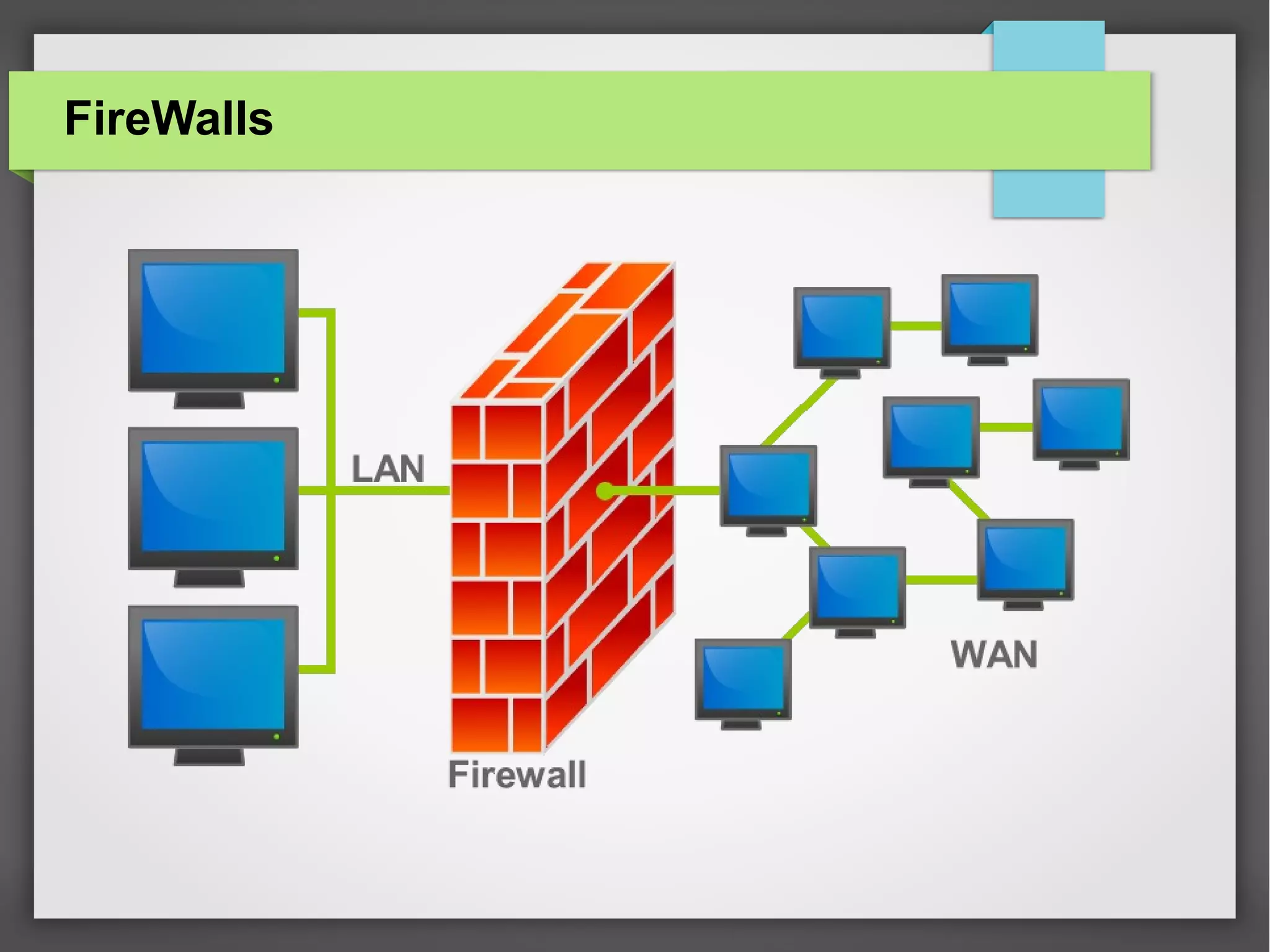
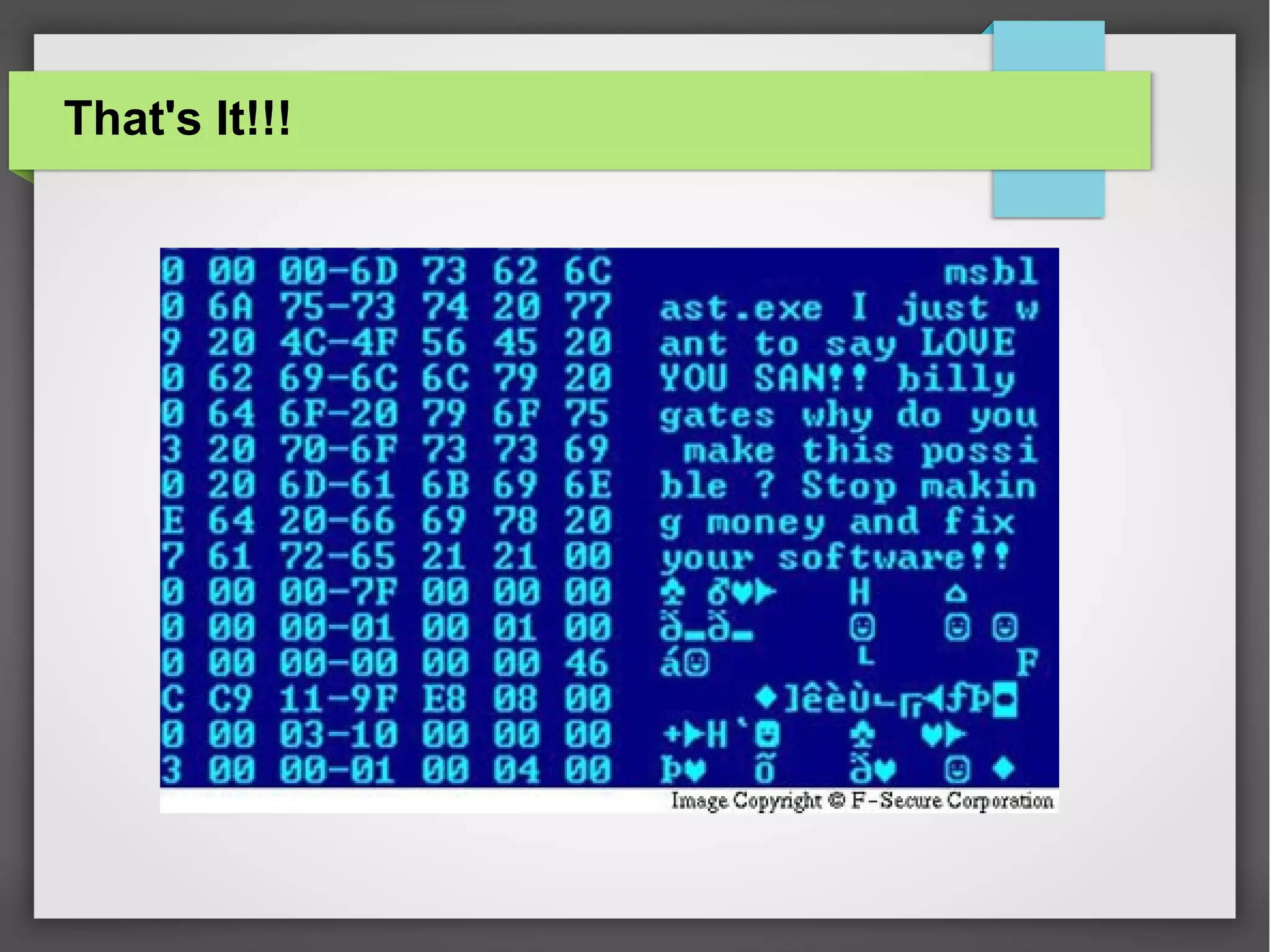
The document discusses computer viruses and various types of malware, such as spyware, adware, and backdoors, detailing how they are created, spread, and how to detect and protect against them. It emphasizes the economic damage caused by these viruses and highlights the importance of using antivirus and firewall programs for protection. The document also includes definitions, examples, and strategies for safeguarding computers from malware.