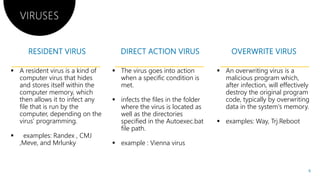
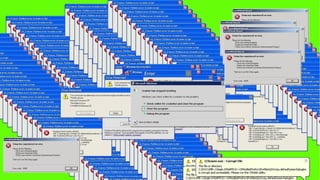
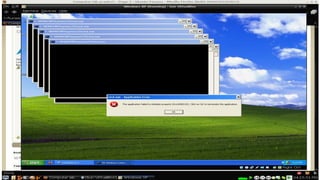
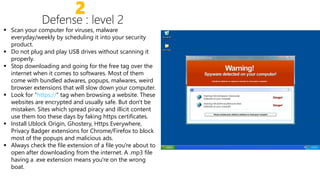
Viruses can enter computers in several ways. There are many types of viruses including resident viruses, overwriting viruses, macro viruses, polymorphic viruses, and Trojan horses. It is important to take steps to protect computers such as installing antivirus software, using firewalls, avoiding suspicious emails and downloads, and regularly backing up files.