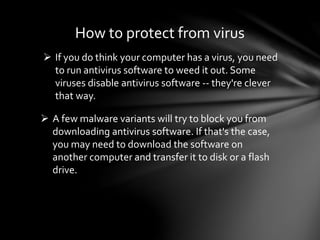
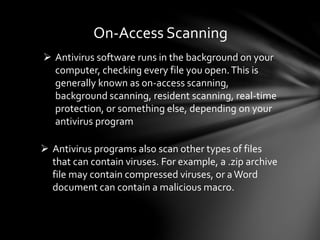
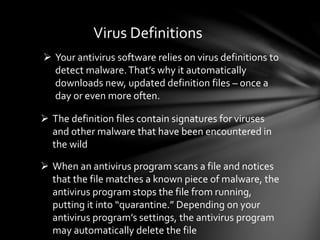
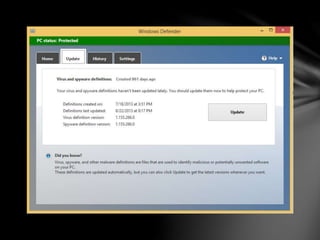
A computer virus is a type of malicious software or malware that attaches itself to other programs and files to replicate itself. Viruses can damage software, steal personal information, slow down systems, and more. Antivirus software uses techniques like on-access scanning, virus definitions, heuristics, and detection testing to identify and remove viruses and other malware from computers. Regularly updating antivirus software and virus definitions is important for protection.