I. Antivirus software identifies and removes viruses and other malware from infected computers, and protects against future attacks. The first antivirus software was created in 1987 to combat real-world computer viruses.
II. Antiviruses work by examining files and comparing them to a database of known virus characteristics and definitions. Infected files that match are quarantined to prevent further spreading.
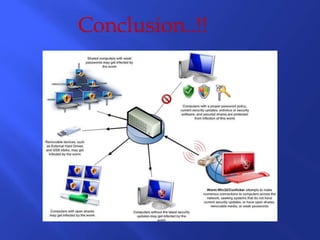
III. Popular antivirus options include free programs like AVG and paid solutions like Norton and Kaspersky, which are effective but may not always restore damaged files to their original state. Regular scanning and updating is needed to maintain protection.