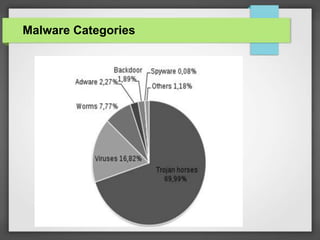
This document defines malware and describes common types like viruses, trojans, worms, spyware, and adware. It explains that malware is hostile software installed without consent that can harm systems. Viruses replicate by inserting copies into other programs and files, while trojans and worms spread automatically but don't replicate on their own. Spyware and adware track users' online activities and display unwanted ads. The document also outlines how antivirus software uses virus definitions and behavior monitoring to detect and remove malware, and provides examples of popular antivirus programs.