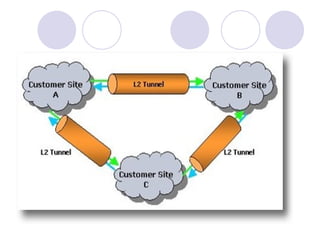
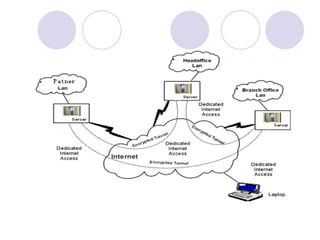
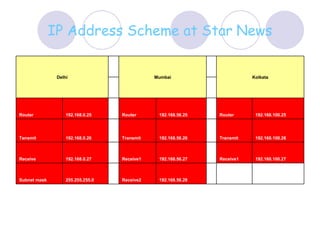
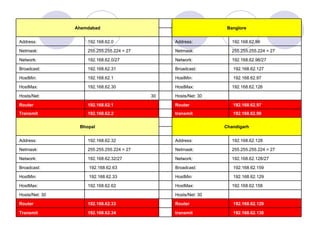
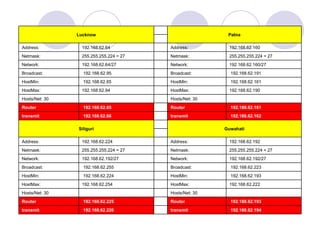
This document provides an overview of VPN (virtual private network) technology. It discusses VPN tunneling which involves encapsulating data packets within other network protocols for secure transmission. There are two main types of VPN tunneling - voluntary and compulsory. It also outlines some popular VPN tunneling protocols like PPTP, L2TP, and IPsec. The document notes that while VPNs provide security and flexibility, they also have disadvantages related to performance, compatibility, and management that require planning.