The Tiny Encryption Algorithm (TEA) is a symmetric key encryption algorithm created by David Wheeler and Roger Needham of Cambridge University. TEA is one of the fastest and most efficient cryptographic algorithms due to its minimal memory footprint and maximized speed. It is a Feistel cipher that achieves diffusion and confusion after only six rounds, though thirty-two rounds are recommended for security. TEA performs operations on 32-bit words and encrypts data in 64-bit blocks using a 128-bit key split into four 32-bit subkeys.



![FUNCTIONALITY OF TEA
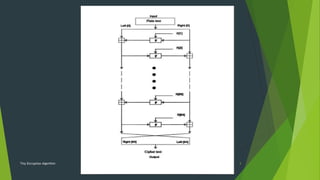
Inputs to encryption algorithm are 64 bits of plain/cipher text , 128 bits of
key and output is a cipher/plain text.
It performs operations on 32 bit words.
Each round has 4 sub key k[i].
Each half of message is used to encrypt the other half over 64 rounds of
processing and then combine to produce the cipher text block.
A half block is processed and swapped iteratively and all operations are
performed on modulo 32‐bit
3/14/2015Tiny Encryption Algorithm 4](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-4-320.jpg)
![OPERATIONS PERFORMED IN A SINGLE
ITERATION
Each round i has inputs Left[i-1] and Right[i-1], derived from the previous
round, as well as a sub key K[i] derived from the 128 bit overall K.
The sub keys K[i] are different from K and from each other.
Delta is defined as a constant, 2^32/(golden ratio), which is 2654435769 as an
integer.
Multiples of delta are used in each round (mod 2^32), Delta is derived from
the golden number ratio to ensure sub keys to be different.
3/14/2015Tiny Encryption Algorithm 6](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-6-320.jpg)
![ In the first feistel round R is used as
an input to several operations. All
addition operations are (mod 2^32).
1. R goes through a left shift of 4 and
then is added to K[0]
2. R is added to Delta
3. R goes through a right shift of 5 and
then is added to K[1]
An XOR operation is then applied to
the result of those three operations
and finally, the result of
the XOR operation is added to L. This
result then becomes R for the next
feistel round, because of the swap.
3/14/2015Tiny Encryption Algorithm 7
TEA has a 128 bit key that is split up into
four 32 bit subkeys, which can be seen as
K[3]in the diagram.
Delta is defined as a constant, 2^32/(golden
ratio), which is 2654435769 as an integer.
Multiples of delta are used in each round
(mod 2^32).](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-7-320.jpg)
![TEA Encryption Function
void encrypt(unsigned long k[], unsigned long text[]) {
unsigned long y = text[0], z = text[1];
unsigned long delta = 0x9e3779b9, sum = 0; int n;
for (n= 0; n < 32; n++) {
sum += delta;
y += ((z << 4) + k[0]) ^ (z+sum) ^ ((z >> 5) + k[1]);
z += ((y << 4) + k[2]) ^ (y+sum) ^ ((y >> 5) + k[3]); }
text[0] = y; text[1] = z; }
3/14/2015Tiny Encryption Algorithm 8](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-8-320.jpg)
![TEA decryption function
void decrypt(unsigned long k[], unsigned long text[]) {
unsigned long y = text[0], z = text[1];
unsigned long delta = 0x9e3779b9, sum = delta << 5; int n;
for (n= 0; n < 32; n++) {
z -= ((y << 4) + k[2]) ^ (y + sum) ^ ((y >> 5) + k[3]);
y -= ((z << 4) + k[0]) ^ (z + sum) ^ ((z >> 5) + k[1]);
sum -= delta;
}
text[0] = y; text[1] = z;
}
3/14/2015Tiny Encryption Algorithm 9](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-9-320.jpg)
![TEA in use
void tea(char mode, FILE *infile, FILE *outfile, unsigned long k[]) {
/* mode is ’e’ for encrypt, ’d’ for decrypt, k[] is the key.*/
char ch, Text[8]; int i;
while(!feof(infile)) {
i = fread(Text, 1, 8, infile); /* read 8 bytes from infile into Text */
if (i <= 0) break;
while (i < 8) { Text[i++] = ' ';} /* pad last block with spaces */
switch (mode) {
case 'e': encrypt(k, (unsigned long*) Text); break;
case 'd':decrypt(k, (unsigned long*) Text); break;
}
fwrite(Text, 1, 8, outfile); /* write 8 bytes from Text to outfile */
}
}
3/14/2015Tiny Encryption Algorithm 10](https://image.slidesharecdn.com/tinyencryptionalgorithm-150314161550-conversion-gate01/85/Tiny-encryption-algorithm-10-320.jpg)
