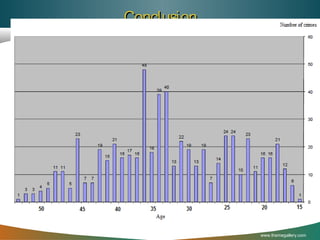
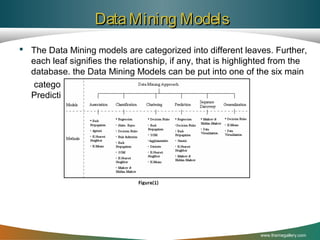
The document discusses the application of data mining techniques in analyzing crime patterns to aid Libyan law enforcement agencies in crime prevention and strategic planning. It outlines the proposed Mining Libyan Criminal Record (MLCR) model, which utilizes association rule mining and clustering methods to identify and classify crime data collected from various cities. Key techniques, challenges in data analysis, and the importance of leveraging existing crime data to inform law enforcement strategies are highlighted.






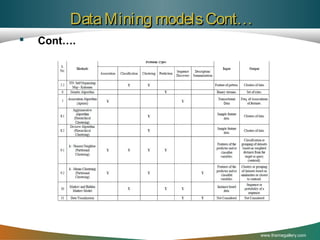





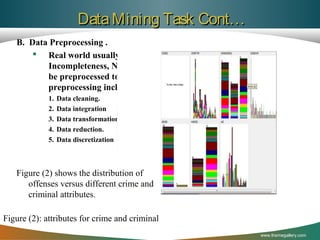

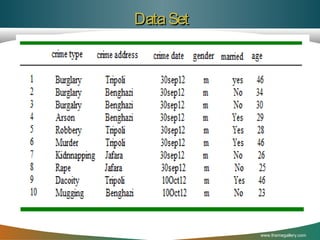


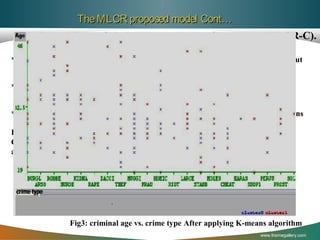
![The MLCR proposed model Cont…
A. Mining Libyan Criminal Record-using
Association rules (MLCR-AR).
Association rule mining is a method used to generate rules from crime
dataset based on frequents occurrence of patterns to help the decision
makers of our security society to make a prevention action.
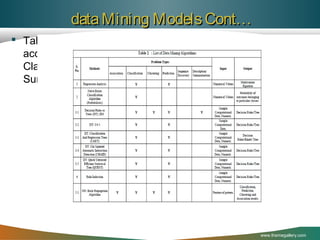
One of the most popular algorithm are called Apriori and FP-growth
Association rule mining classically intends at discovering association
between items in a transactional database.
The Apriori algorithm called also as “Sequential Algorithm” developed
by [Agrawal1994]. Is a great accomplishment in the history of mining
association rules[Cheung1996c]. It is also the most well known
association rules algorithm. This technique uses to perform association
analyze on the attributes of crimes.
www.themegallery.com](https://image.slidesharecdn.com/crimedatamingfinal-131215113806-phpapp01/85/Using-Data-Mining-Techniques-to-Analyze-Crime-Pattern-20-320.jpg)