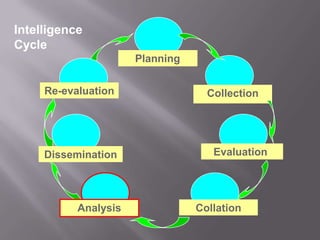
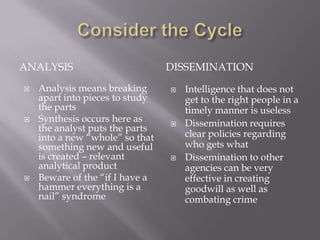
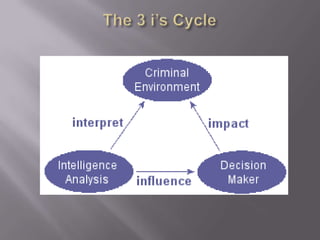
The document discusses intelligence-led policing (ILP) as a strategic framework for law enforcement, emphasizing the importance of data analysis and communication to enhance crime prevention and reduction strategies. It outlines the intelligence cycle, the roles of various levels of law enforcement, and the necessity for collaboration and innovation within policing agencies. Additionally, it highlights the evolving nature of threats due to technological advancements and the need for police leaders to adapt to these changes in order to effectively combat crime.