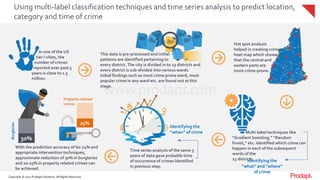
The document discusses the use of predictive analytics in policing, highlighting a case where a U.S. city reduced burglaries by 30% through data-driven predictions of crime. By analyzing various data sources, including historical records and environmental factors, law enforcement can anticipate crime occurrences and effectively allocate resources. The use of machine learning and advanced analytical techniques has proven effective in achieving significant decreases in different types of crimes across various cities.