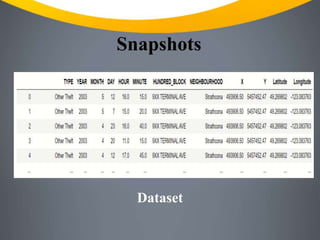
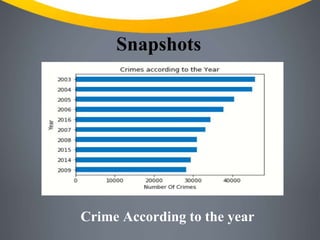
This document outlines a crime detection project that uses machine learning to analyze crime data and predict future crimes. It discusses the current limitations of crime detection systems and how the project aims to provide more accurate and efficient prediction through tools like Python, Pandas, NumPy, Matplotlib and Scikit-learn. The project will preprocess and visualize crime data, train a KNN classifier model, and use location, crime type and time features to predict crimes.