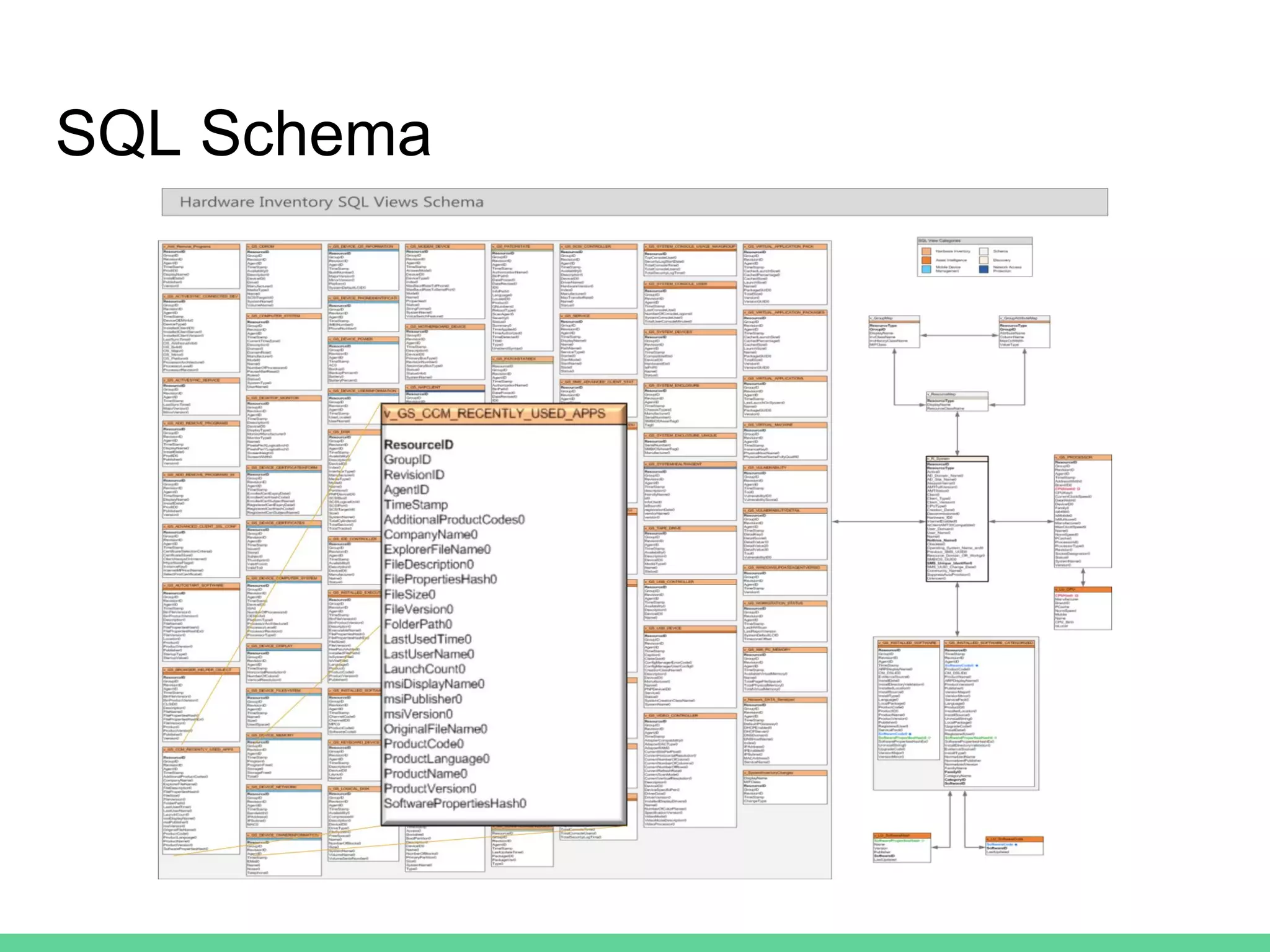
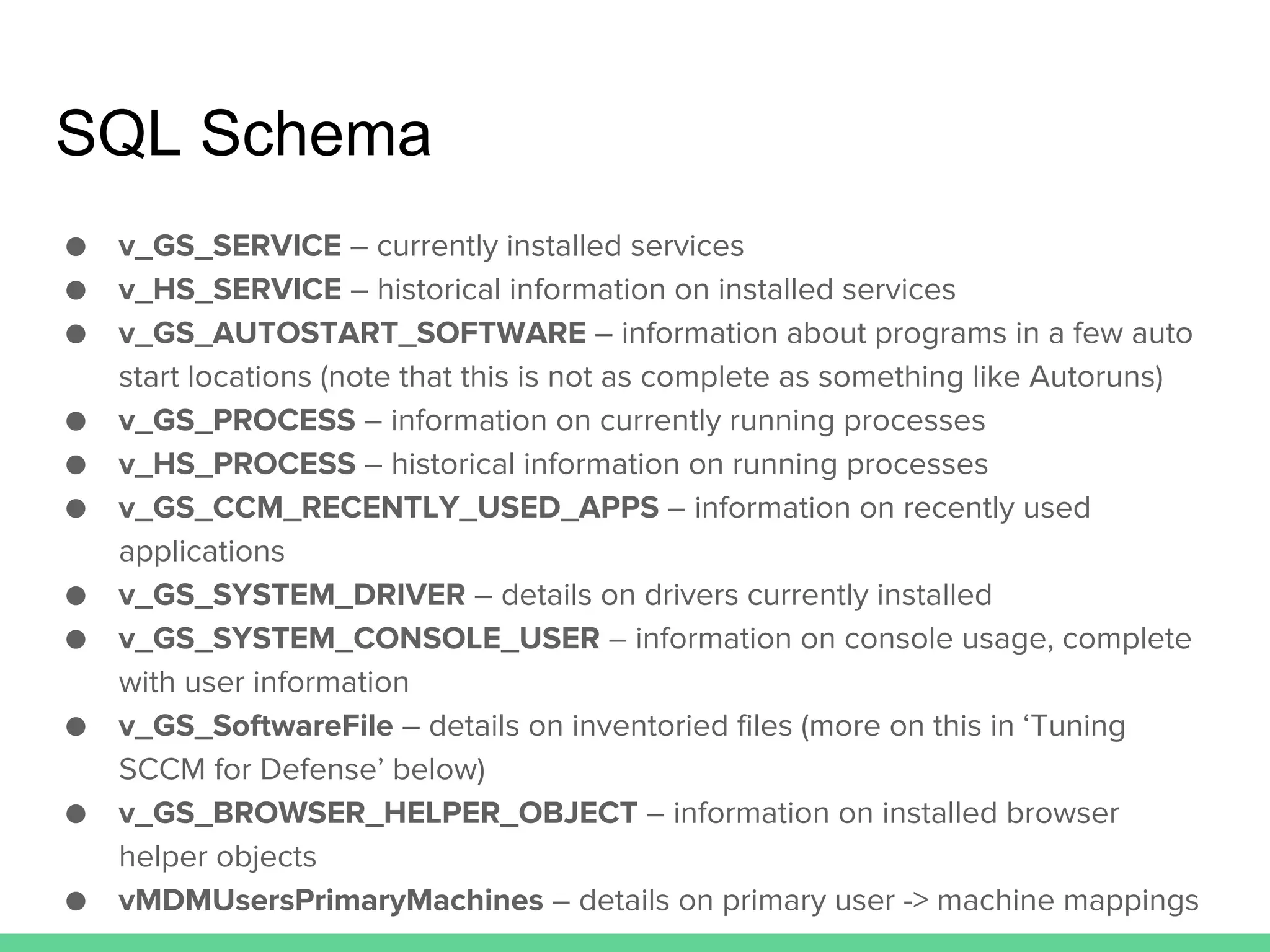
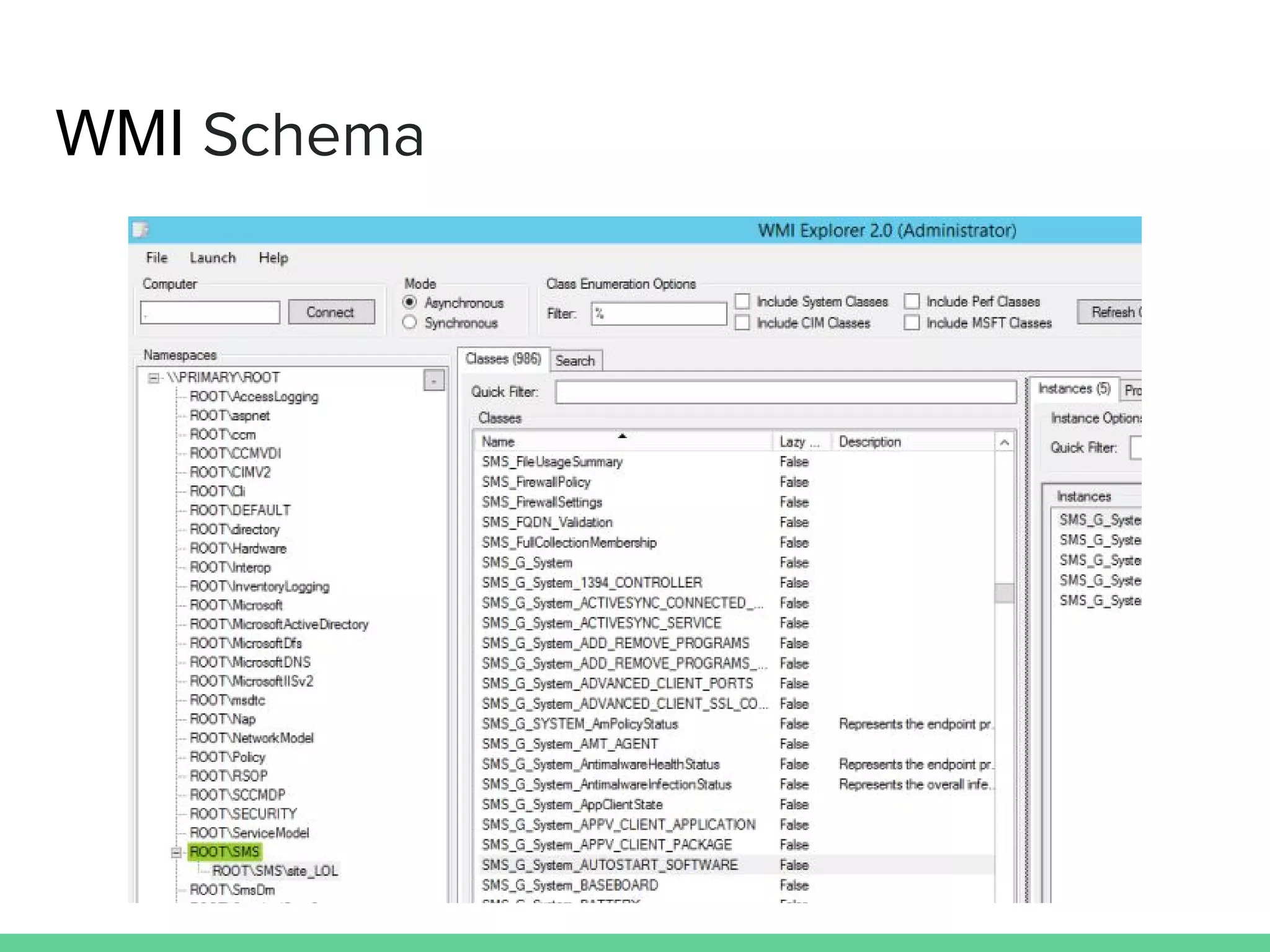
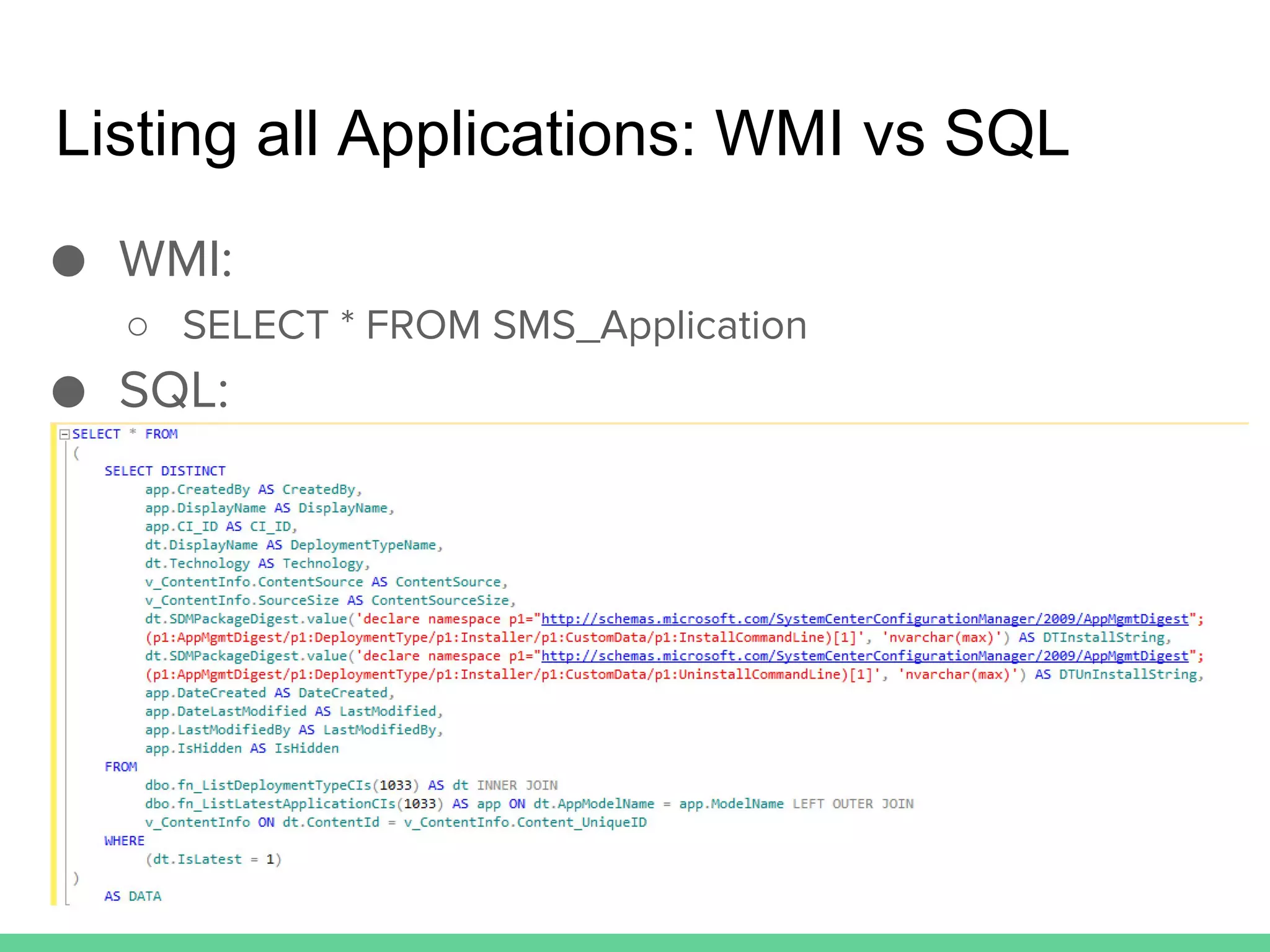
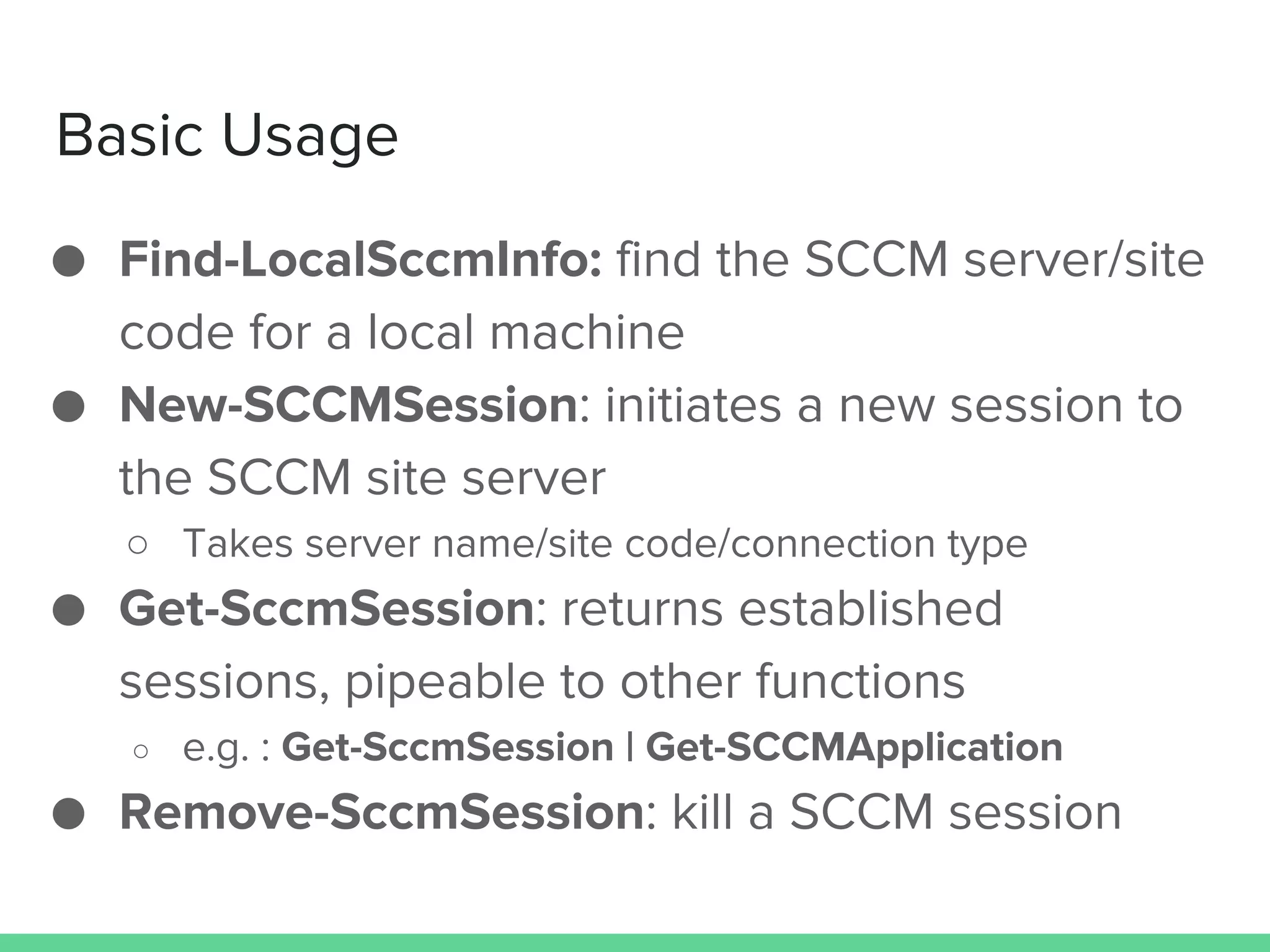
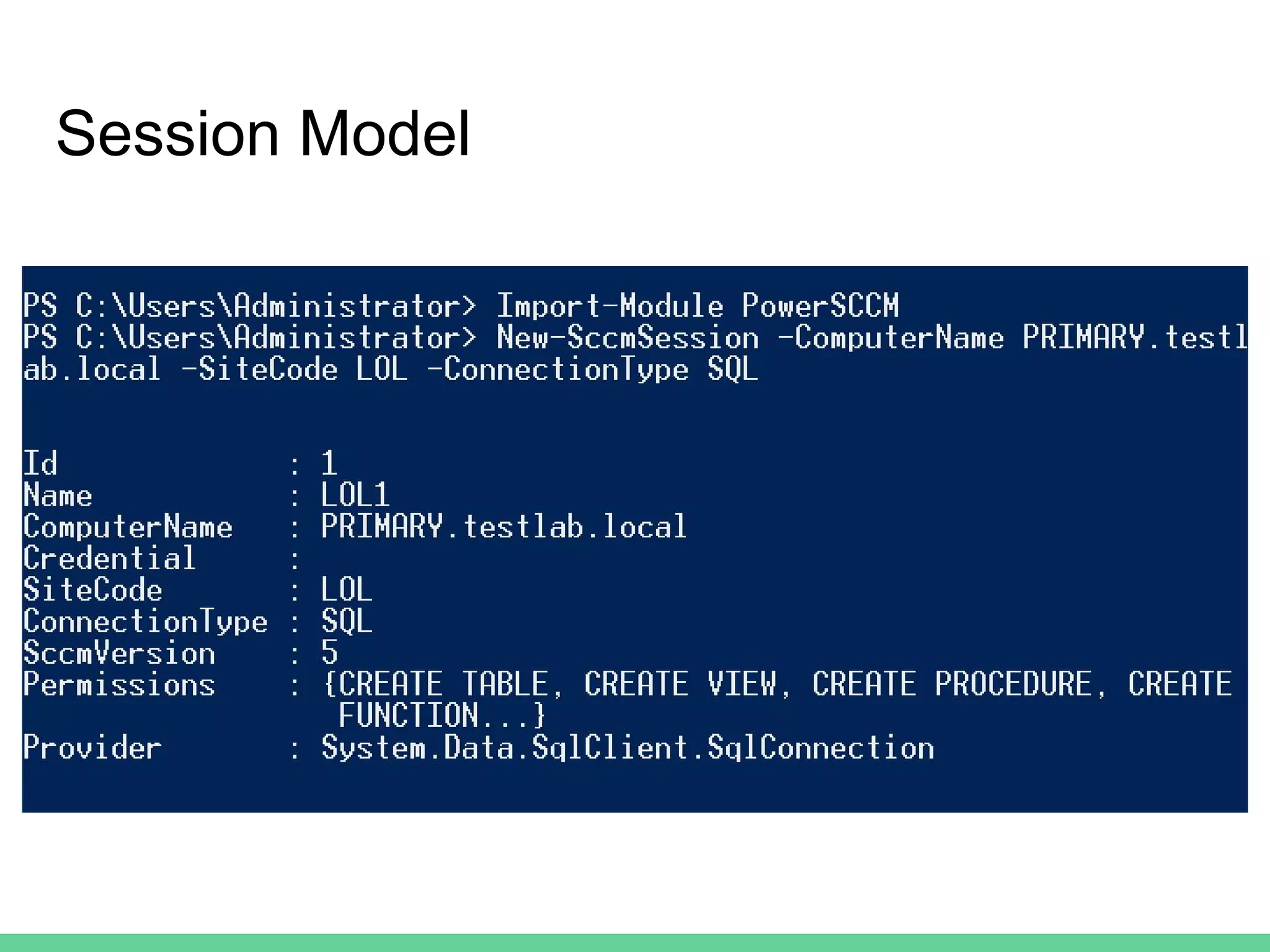
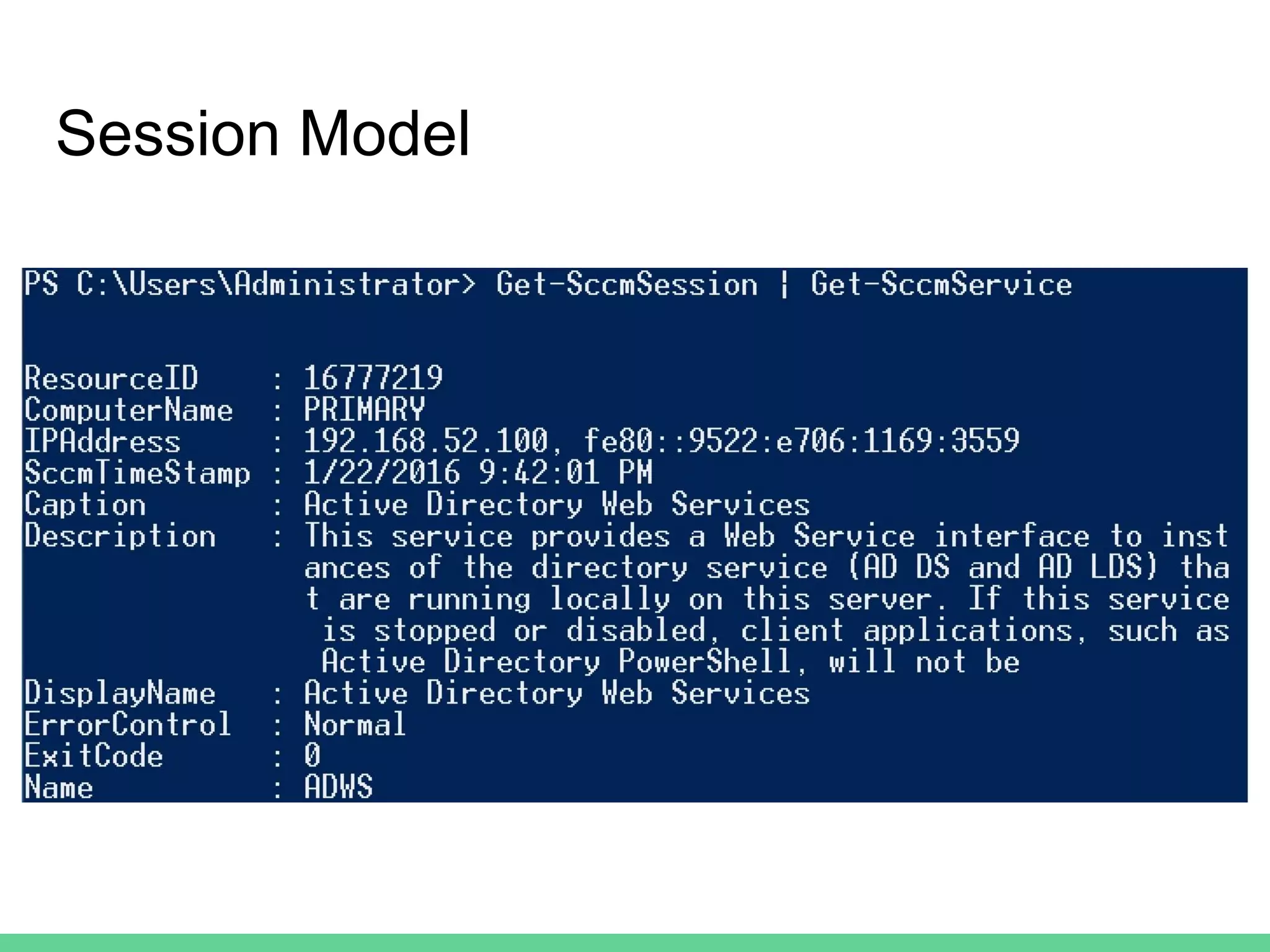
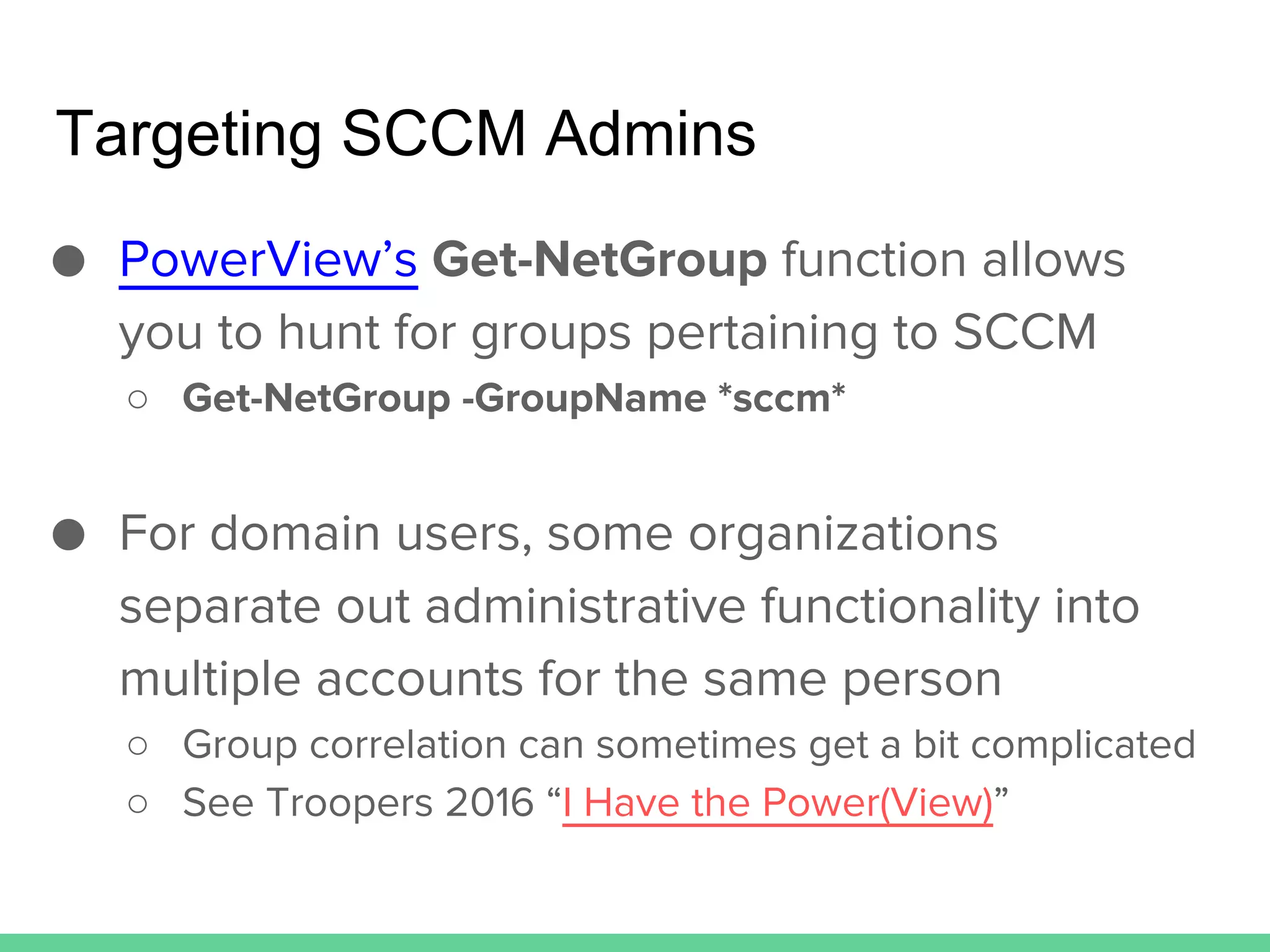
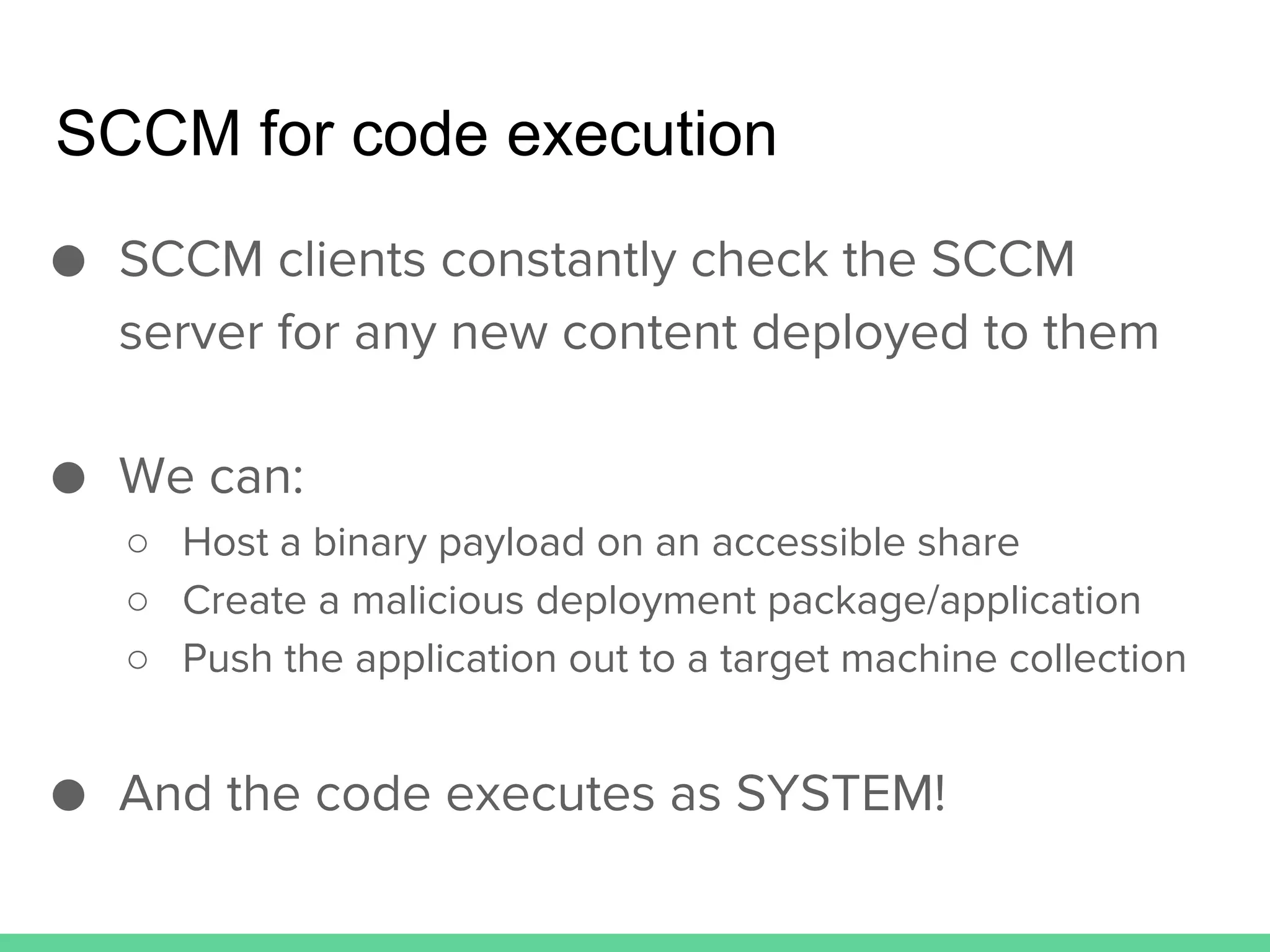
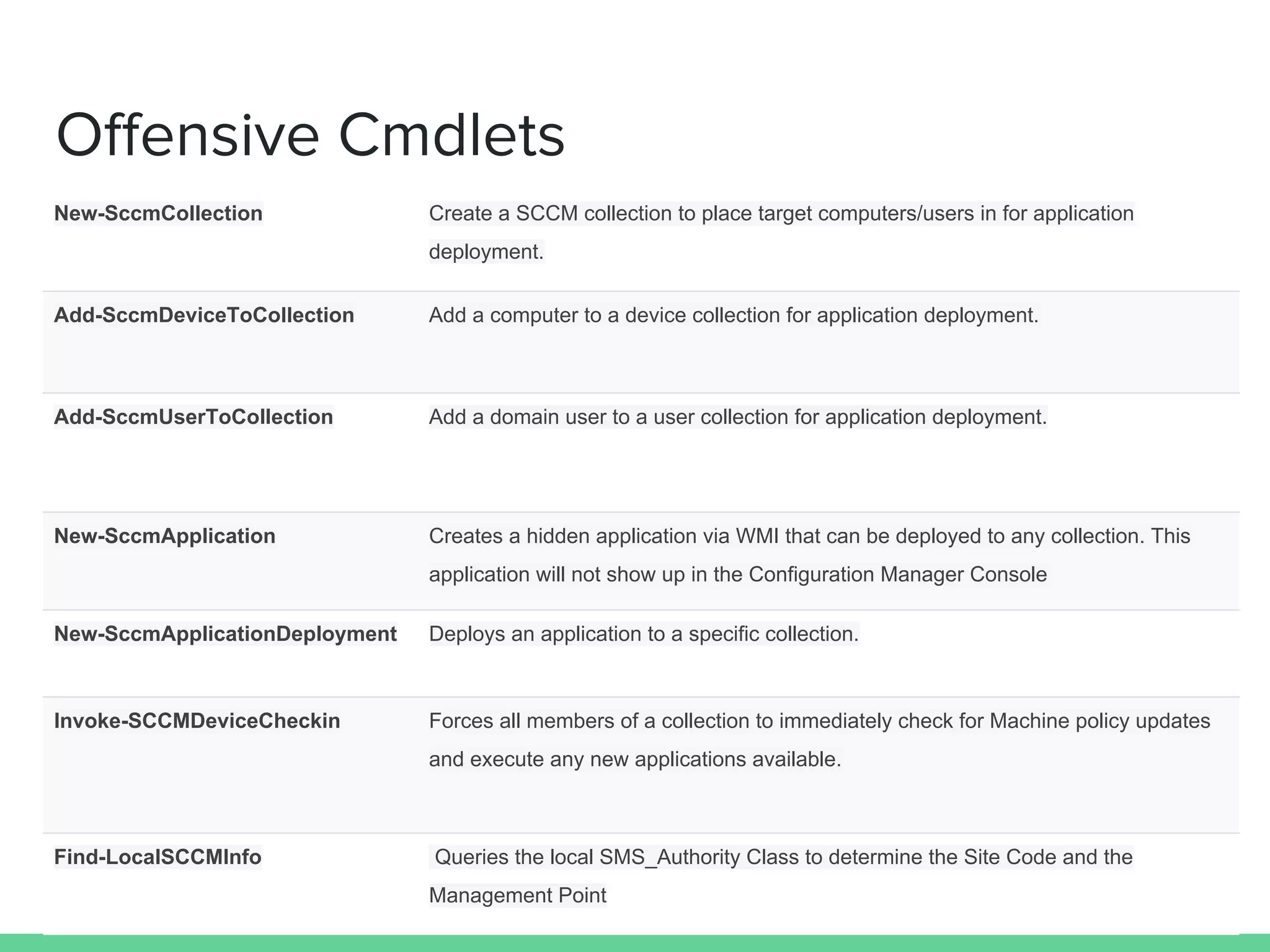
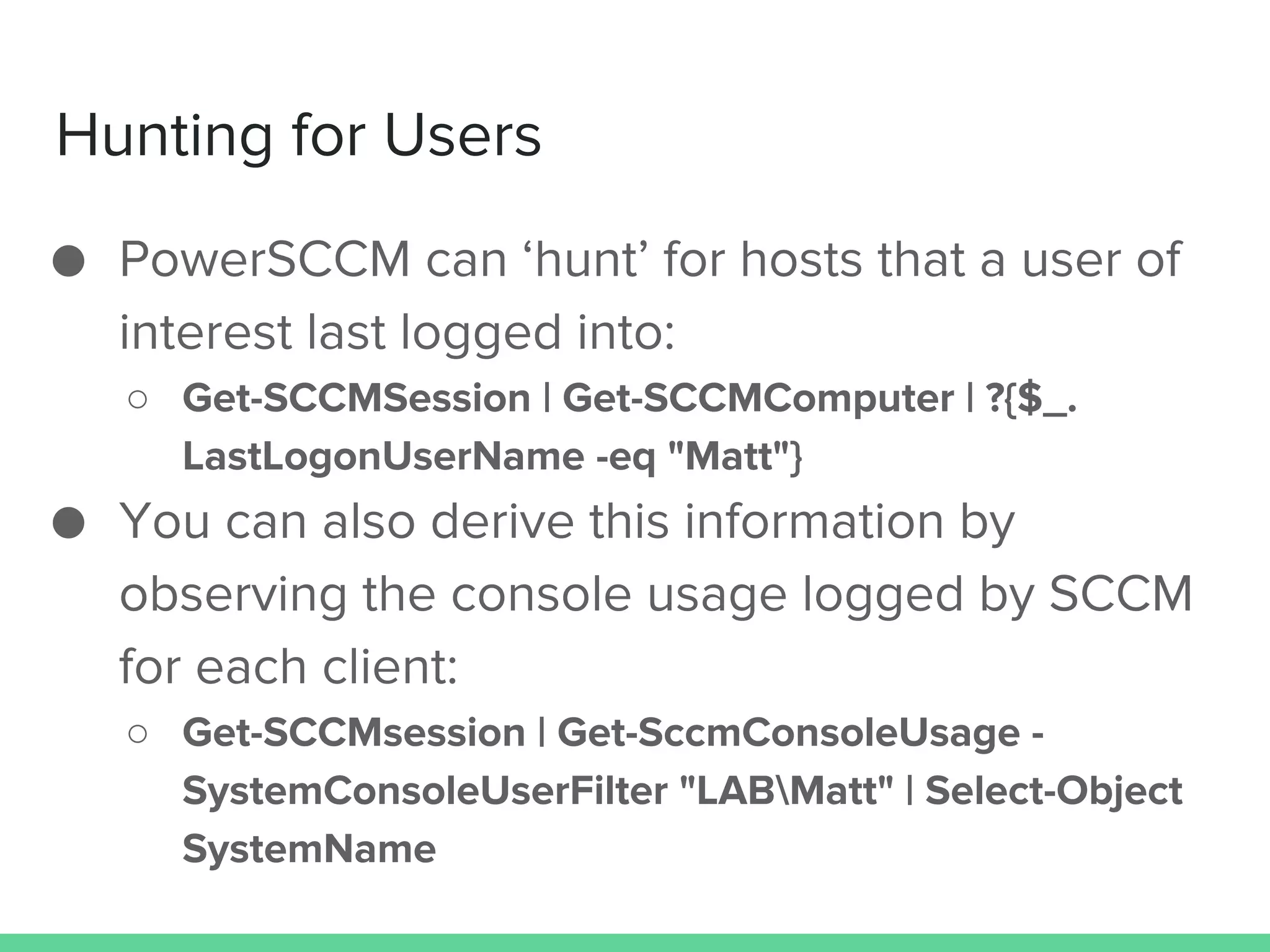
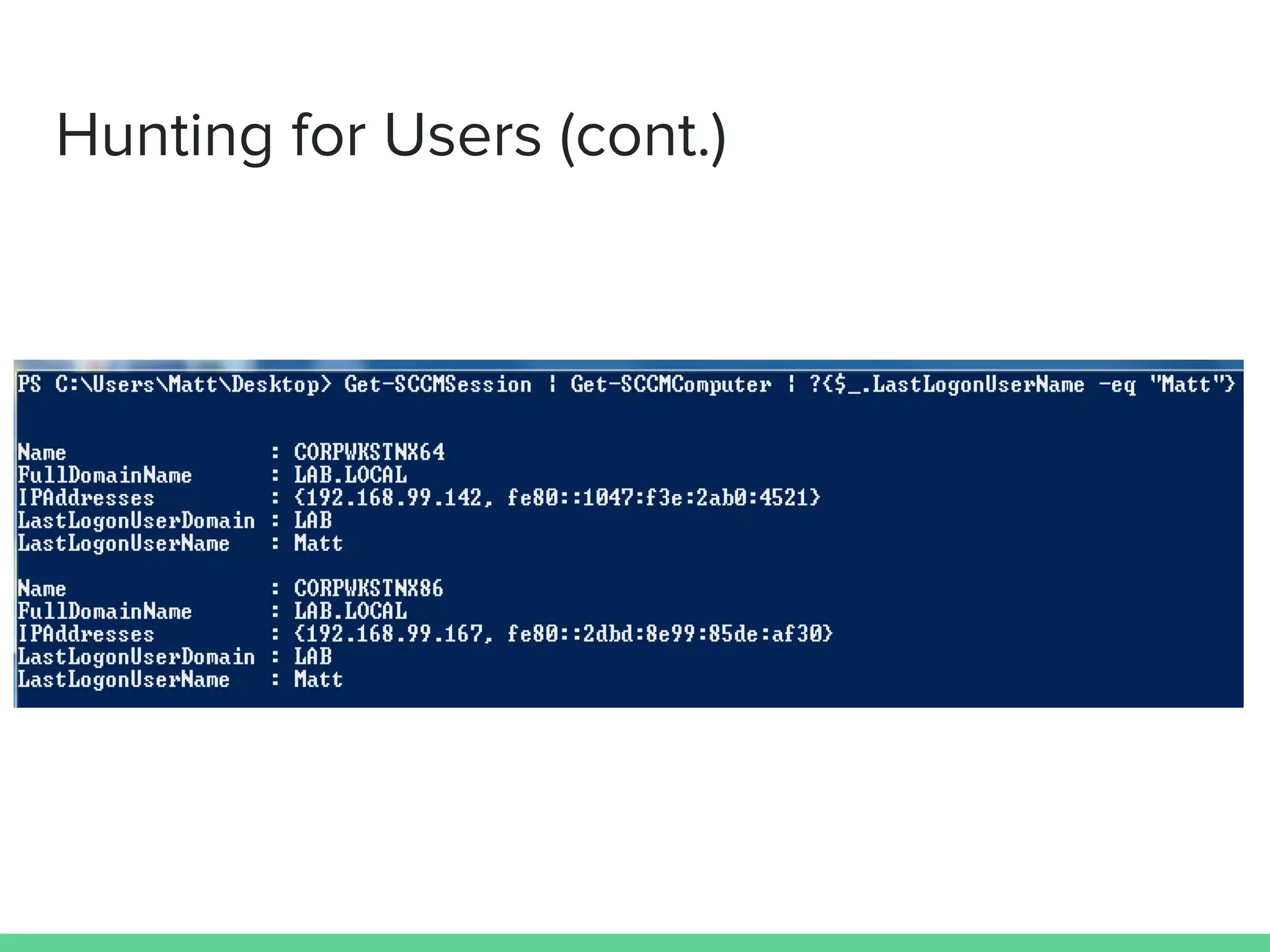
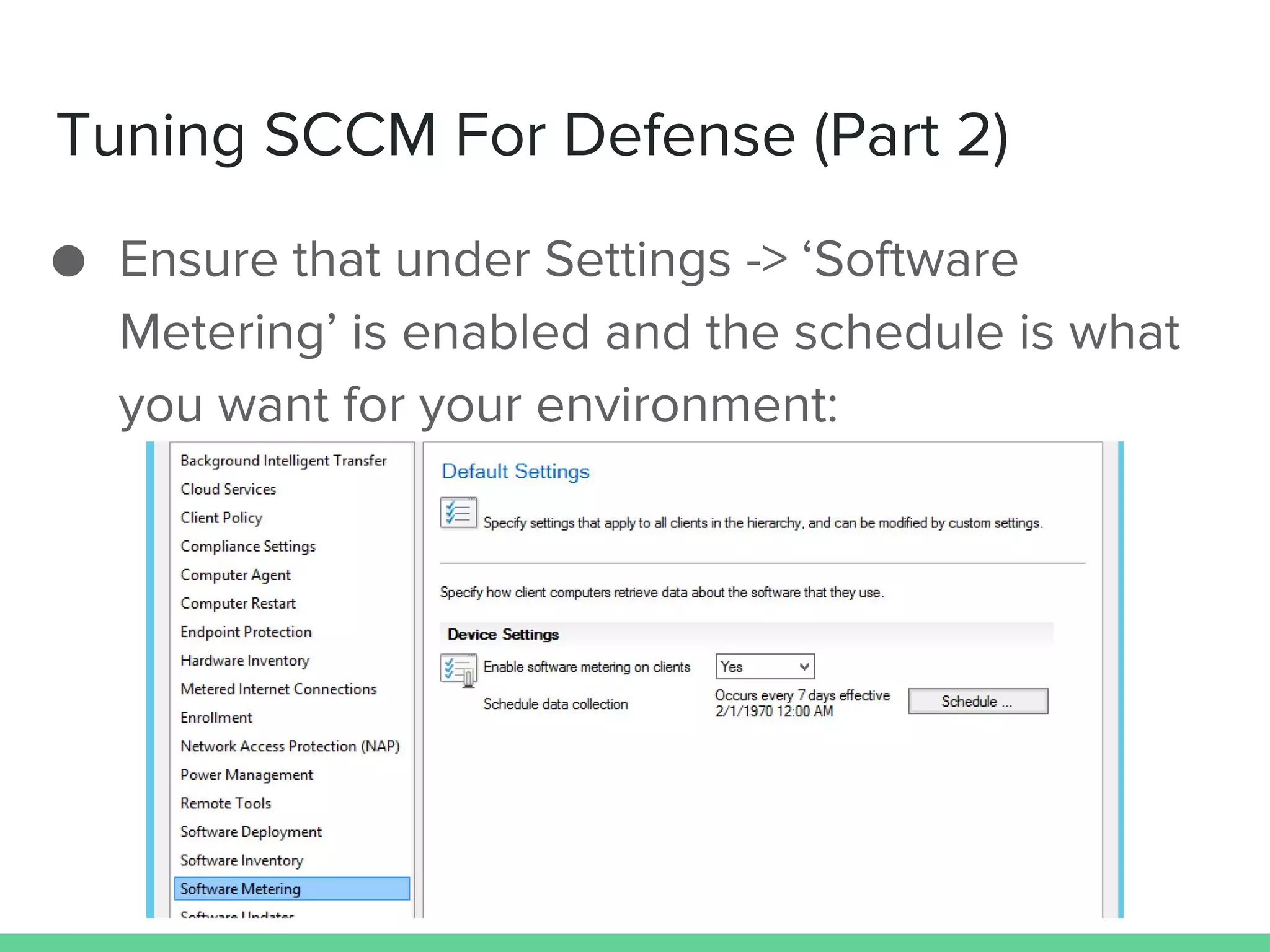
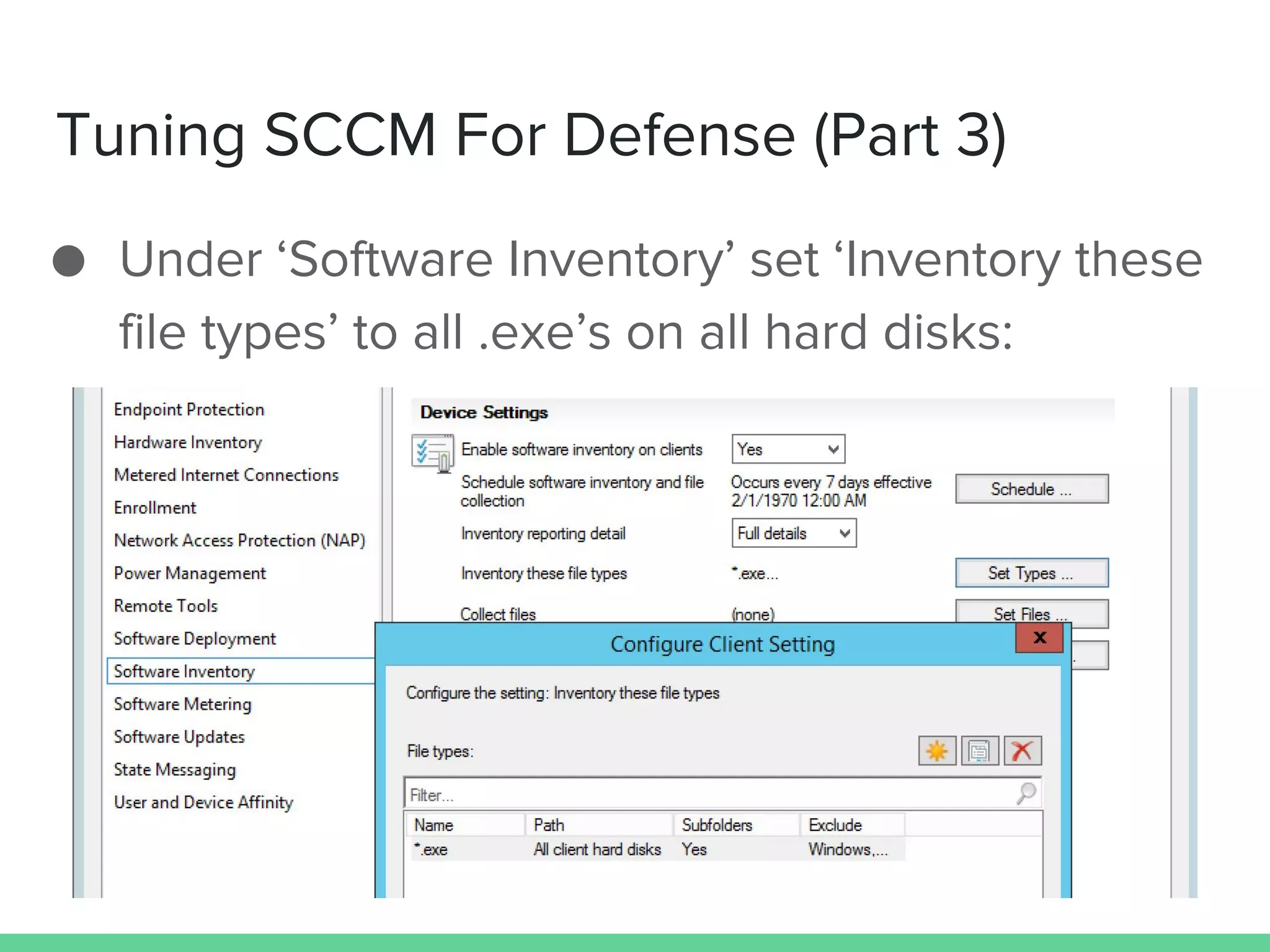
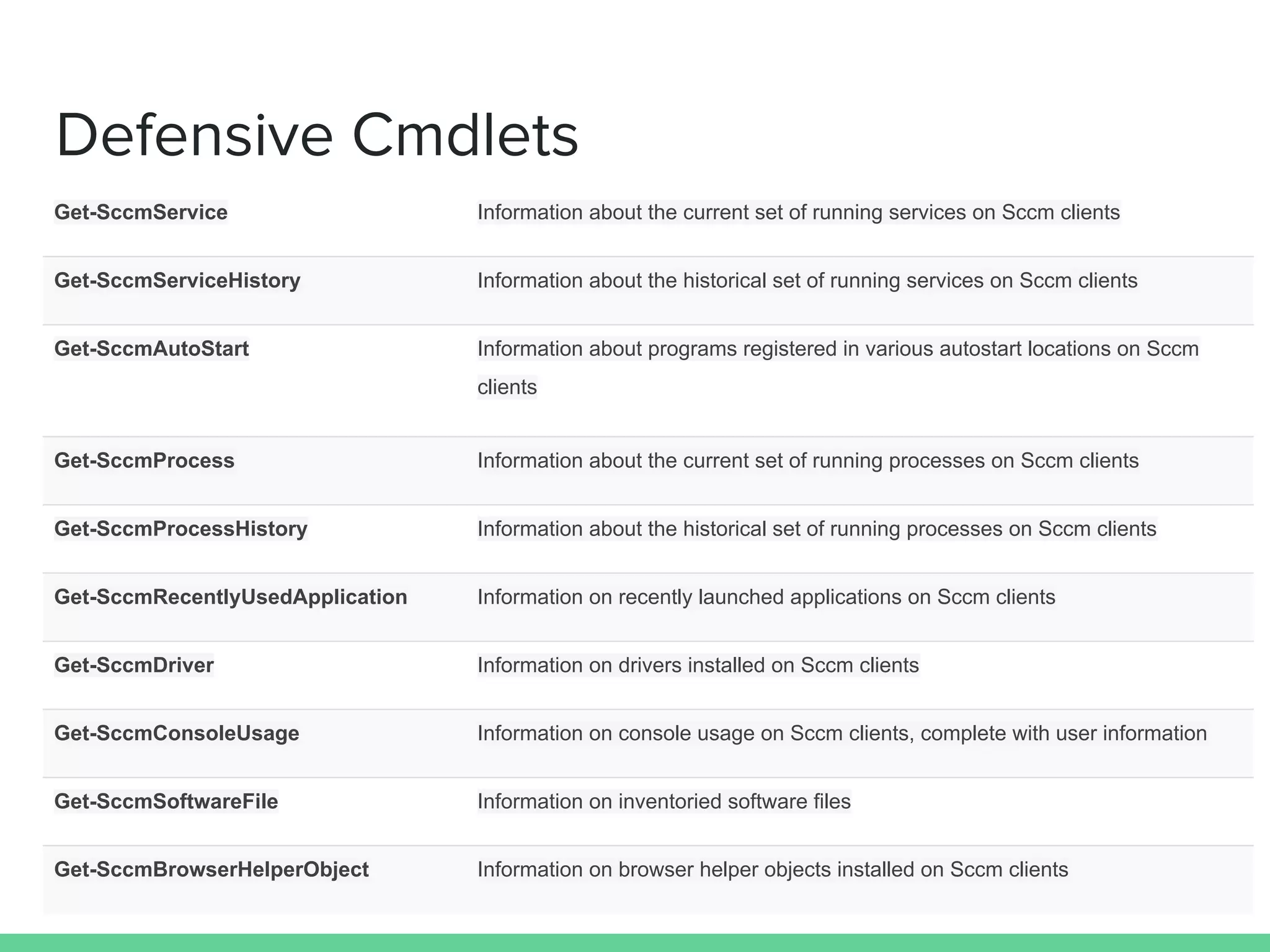
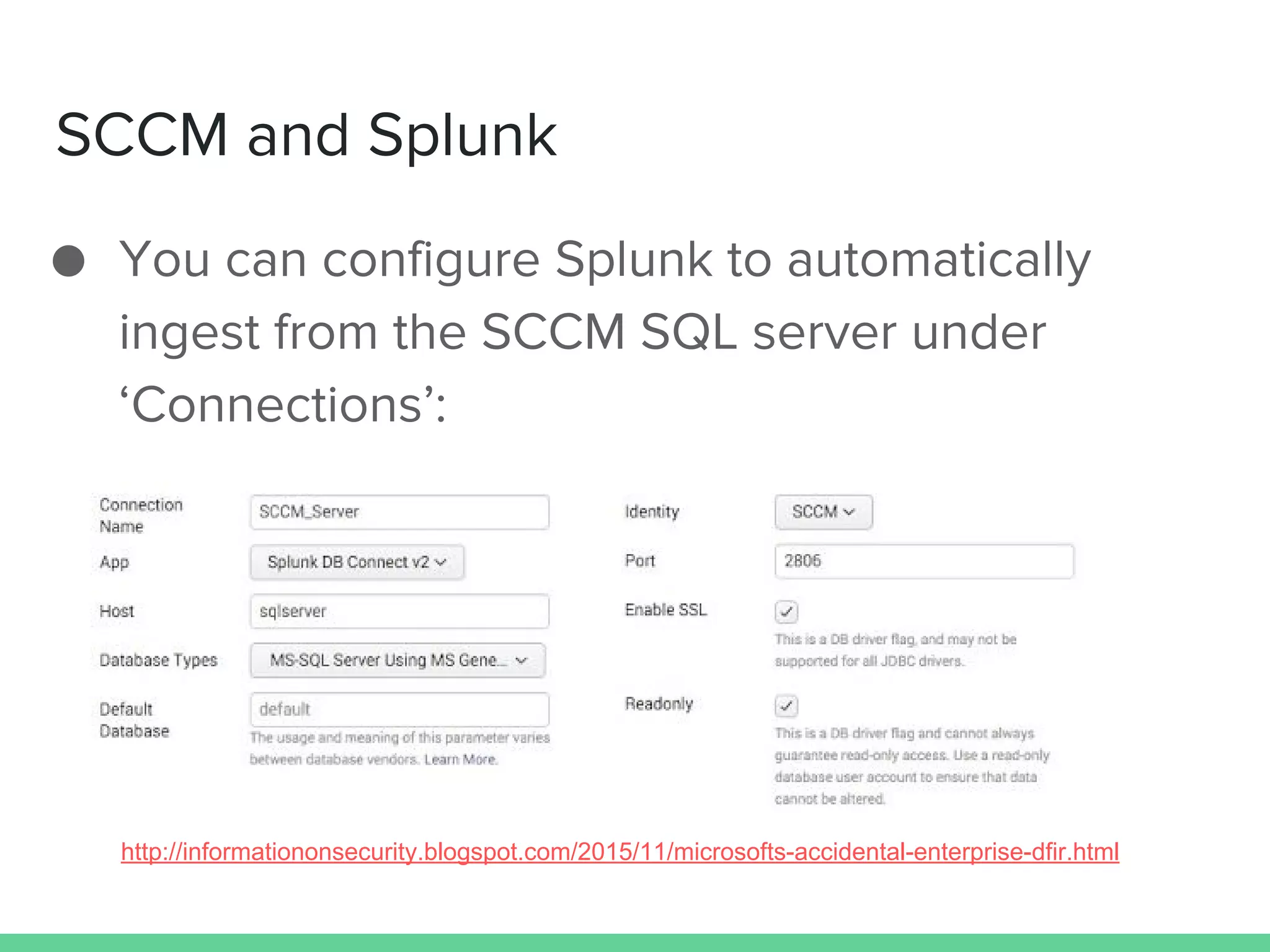
This document discusses using Microsoft's System Center Configuration Manager (SCCM) for both offensive and defensive purposes. It introduces PowerSCCM, a PowerShell toolkit for interacting with SCCM. PowerSCCM can be used to create malicious applications and deploy them to targeted collections of machines. It also provides cmdlets for hunting for compromised users and systems. The document recommends tuning SCCM for improved host-based security monitoring and inventory capabilities. It provides examples of using SCCM data for incident response and hunting activities on the network.