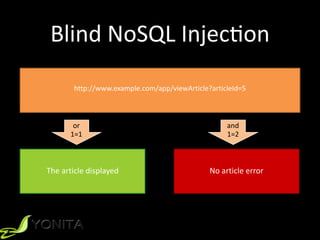
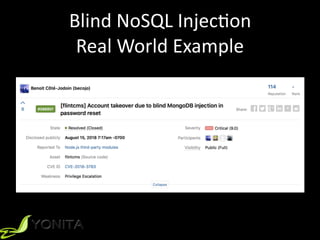
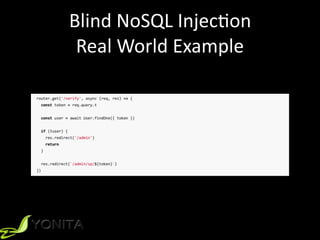
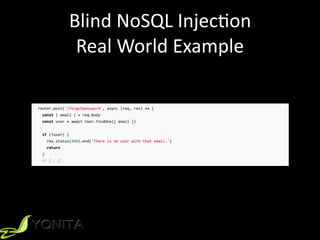
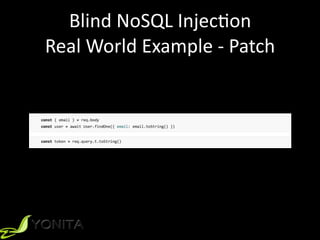
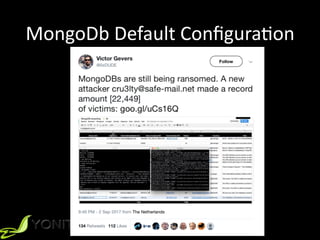
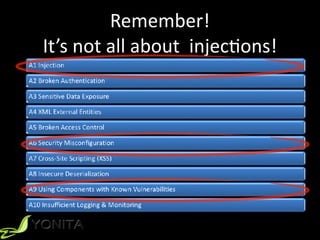
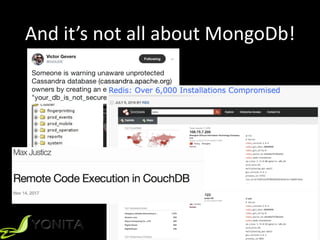
This document summarizes Patrycja Wegrzynowicz's presentation on NoSQL injection at CodeOne 2018. It introduces the speaker's background and covers various types of NoSQL injection attacks like tautologies, union queries, and piggy-backed queries. The presentation demonstrates these attacks on sample applications and provides recommendations for protecting against NoSQL injection like input validation, parameter binding, and secure database configuration. It emphasizes that security risks exist beyond just injections and are not specific to MongoDB.

![About Me
• 20+ professional experience
• SoRware engineer, architect, head of
soRware R&D
• Author and speaker
• JavaOne, Devoxx, JavaZone, TheServerSide
Java Symposium, Jazoon, OOPSLA, ASE,
others
• Top 10 Women in Tech 2016 in Poland
• Founder and CTO of Yon Labs/Yonita
• Consul9ng, trainings and code audits
• Automated detec9on and refactoring of
soRware defects
• Security, performance, concurrency,
databases
• Twi]er @yonlabs](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-2-320.jpg)
![About Me
• 20+ professional experience
• SoRware engineer, architect, head of soRware
R&D
• Author and speaker
• JavaOne, Devoxx, JavaZone, TheServerSide
Java Symposium, Jazoon, OOPSLA, ASE, others
• Top 10 Women in Tech 2016 in Poland
• Founder and CTO of Yon Labs and Yonita
• Bridge the gap between the industry and the
academia
• Automated detec9on and refactoring of
soRware defects
• Trainings and code reviews
• Security, performance, concurrency, databases
• Twi]er @yonlabs](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-3-320.jpg)







![Demo #1
• Bypass Authen9ca9on: Known Account Name
• h]p://demo.yonita.com:3000](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-16-320.jpg)

![Demo #2
• Bypass Authen9ca9on: Unknown Account Name
• h]p://demo.yonita.com:3000
• Please register :-)](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-19-320.jpg)
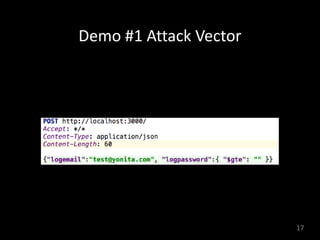
![Demo #2 A]ack Vector](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-20-320.jpg)
![Demo #3
Expose Data
• h]p://demo.yonita.com:3000
• Private notes about CodeOne
• Please register
• Leave your note about CodeOne => I’ll will read all of
them :-)](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-23-320.jpg)
![NoSQL Injec9on
Tautologies
• A]ack Intent
• Bypassing authen9ca9on
• Iden9fying injectable parameters
• Extrac9ng data
• Descrip9on
• Injec9ng code that the condi9on always evaluates to true
• Example
• Demo #1](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-24-320.jpg)
![NoSQL Injec9on
Union Queries
• A]ack Intent
• Bypassing authen9ca9on, extrac9ng data
• Descrip9on
• Changes the data set returned for a given query
• Example
• Demo #2](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-25-320.jpg)
![NoSQL Injec9on
Piggy-Backed Queries
• A]ack Intent
• Extrac9ng data, adding or modifying data, performing
denial of service, execu9ng remote commands
• Descrip9on
• Injec9ng addi9onal JS into the original query
• Example
Robb', $where: ‘func9on(){
sleep(5000); return this.name == “Robb"}'
})](https://image.slidesharecdn.com/codeone2018-nosql-injection-181024234536/85/The-Hacker-s-Guide-to-NoSQL-Injection-26-320.jpg)