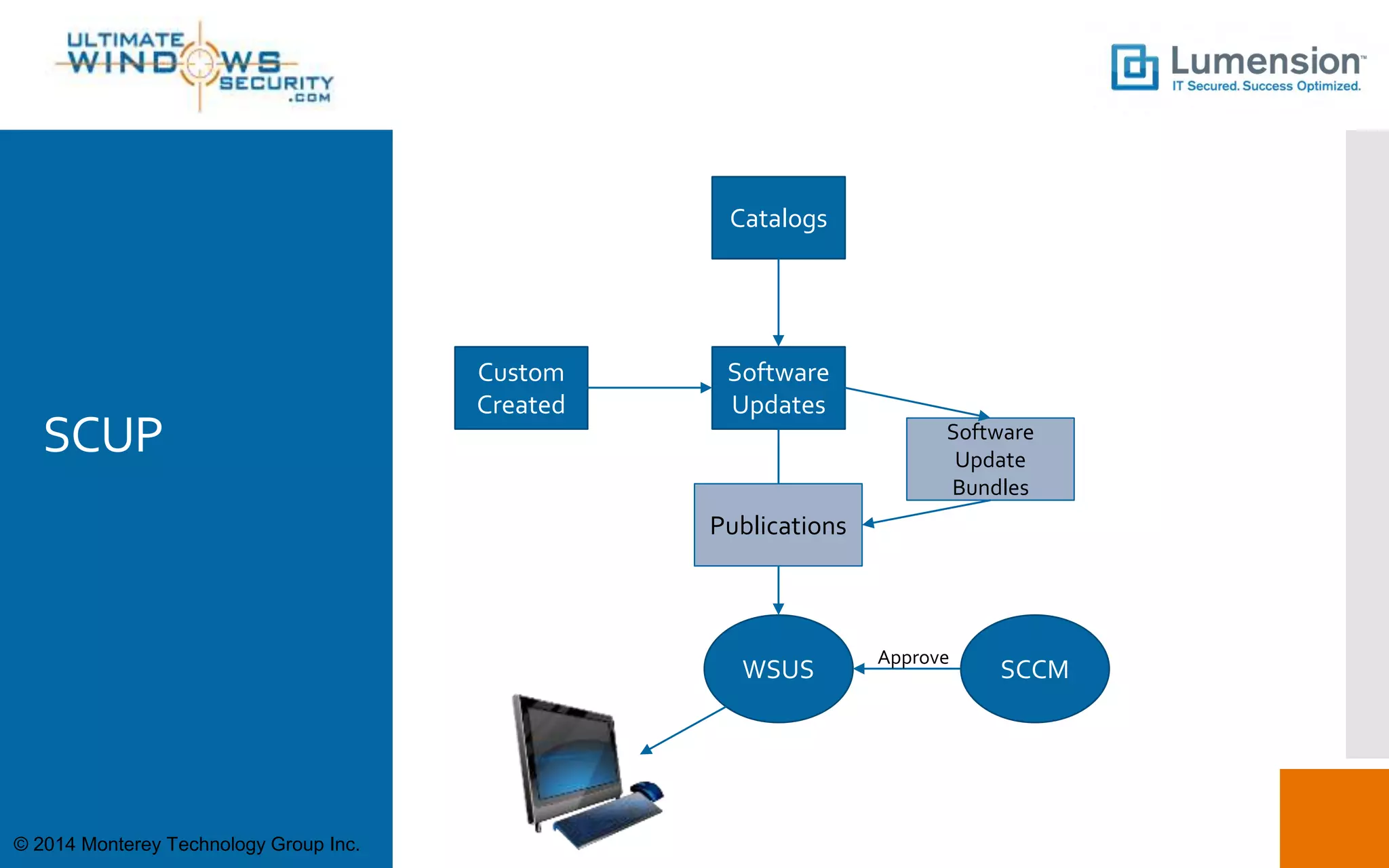
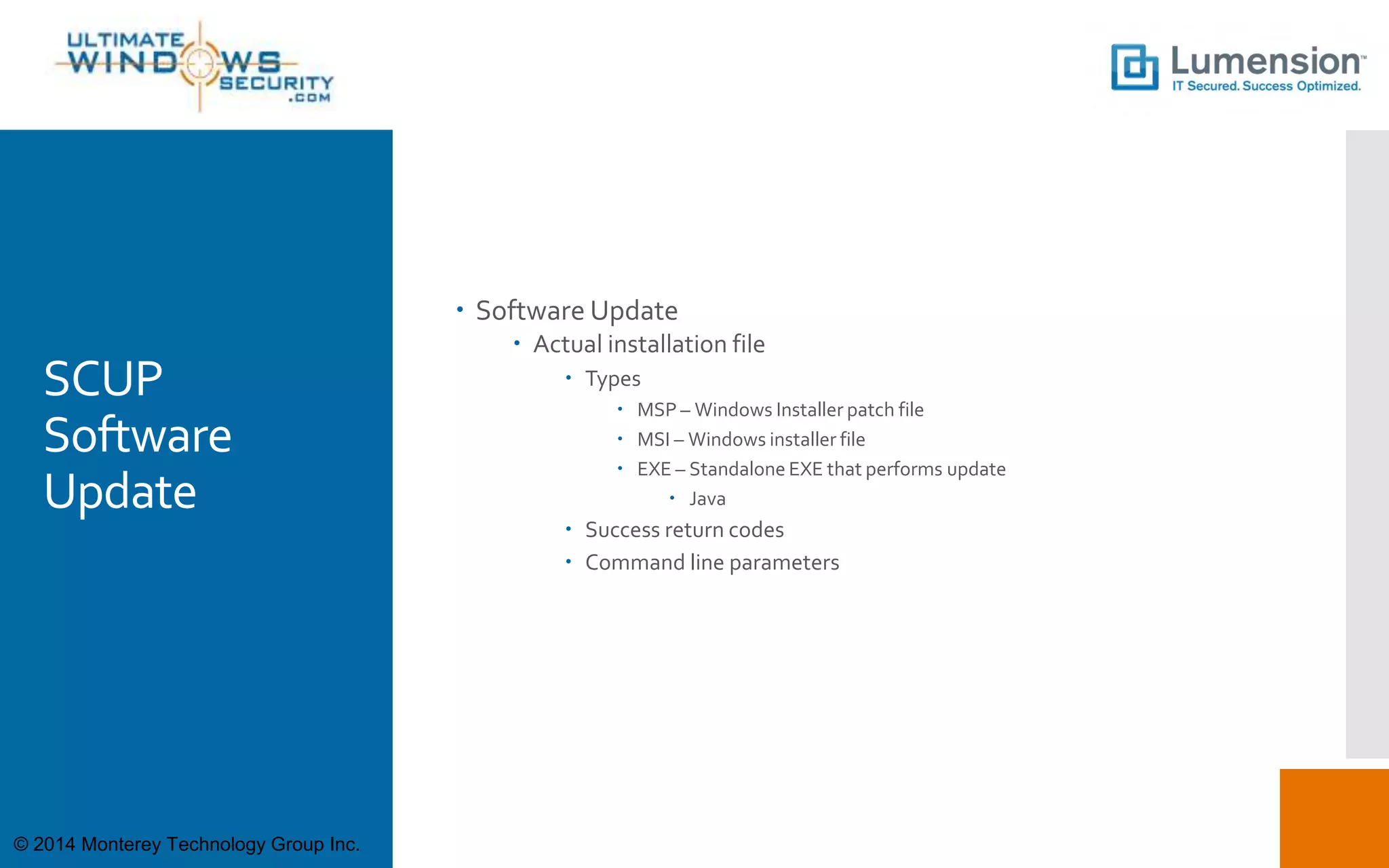
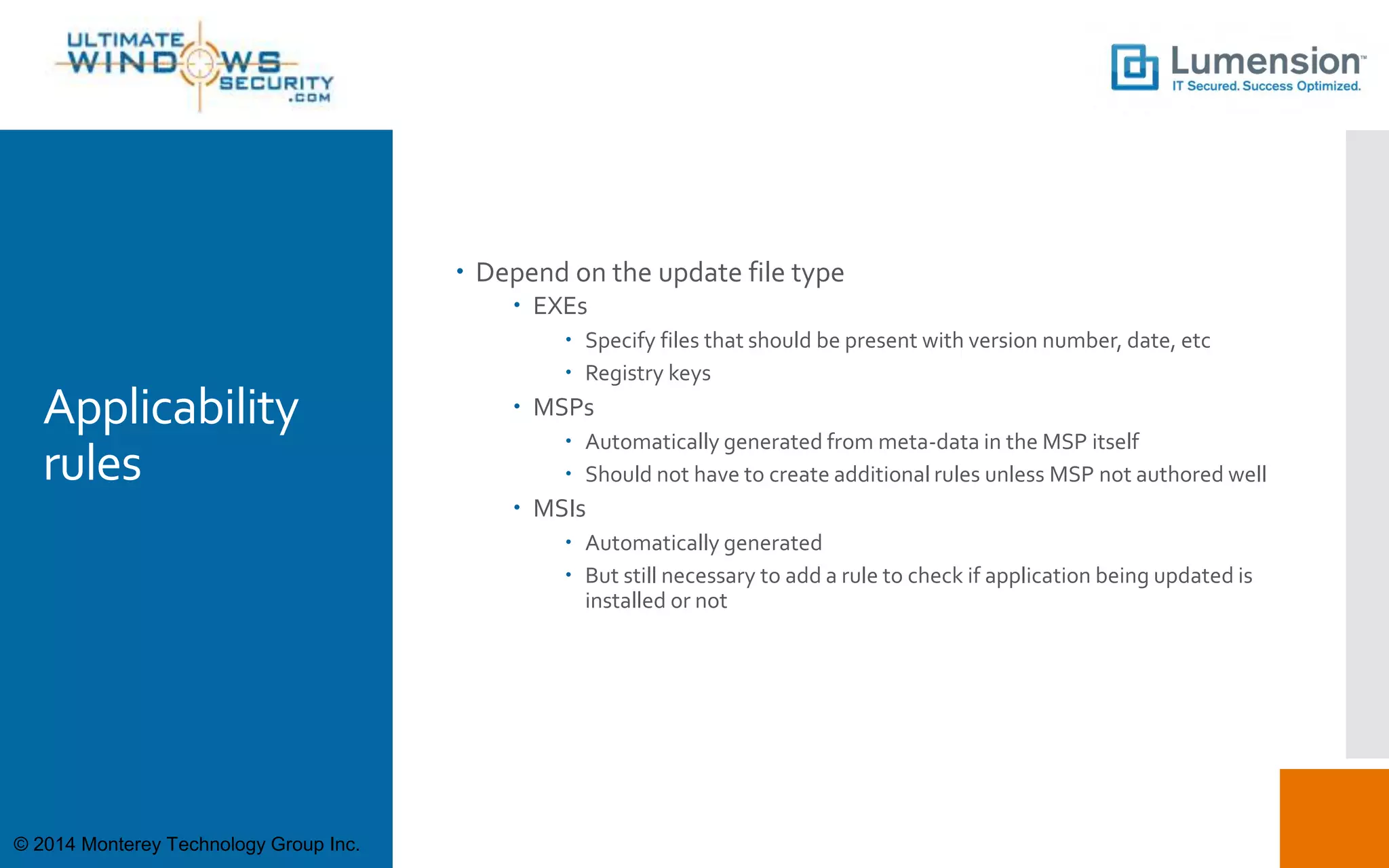
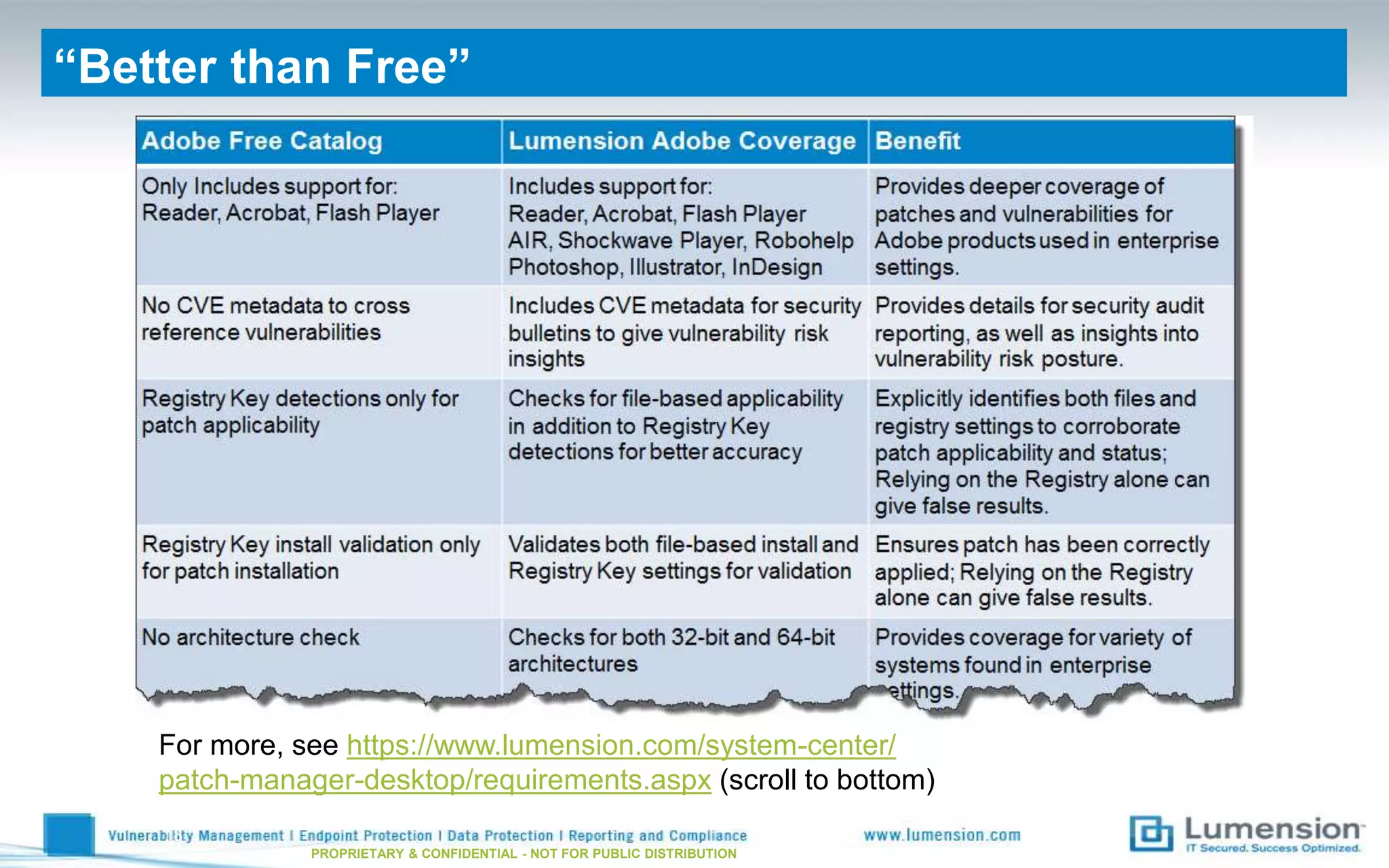
This document discusses using SCUP (SystemCenter Updates Publisher) to patch third-party applications with WSUS (Windows Server Update Services). It provides an overview of SCUP, the process for building software updates, and obtaining pre-built update catalogs. It describes how to define updates in SCUP, including software updates, catalogs, and publications, and publishing the updates to WSUS and SCCM (System Center Configuration Manager). It recommends importing pre-built catalogs from Lumension to simplify the process of third-party patching.