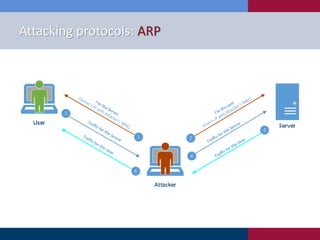
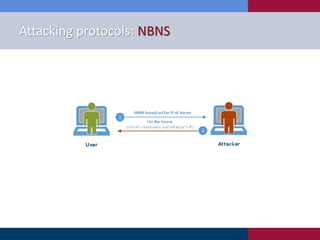
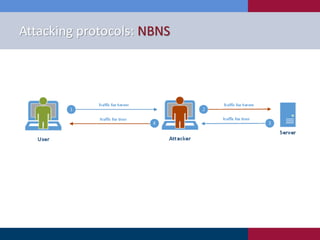
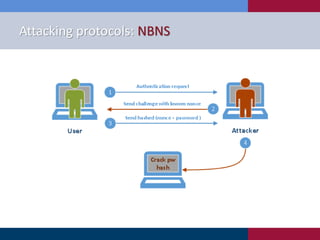
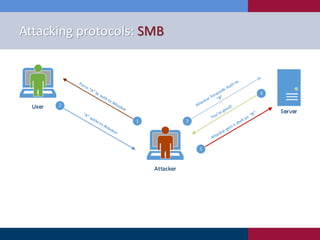
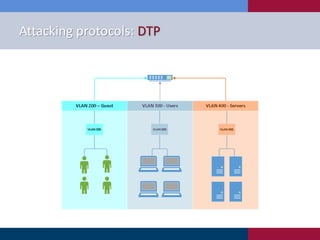
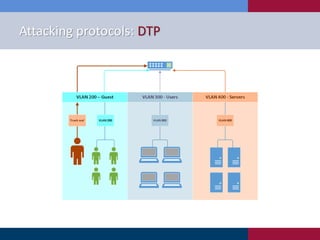
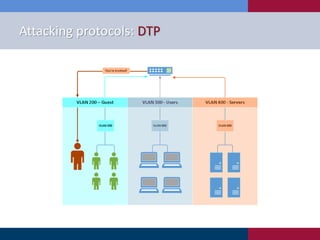
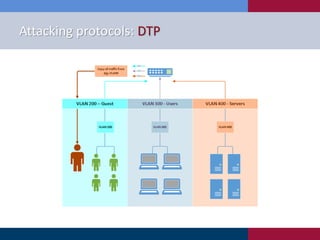
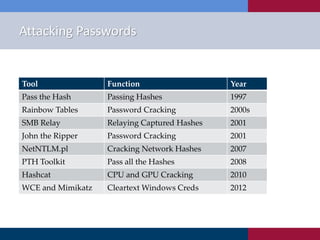
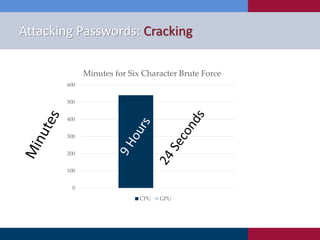
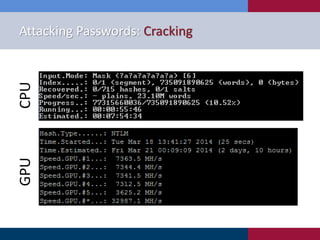
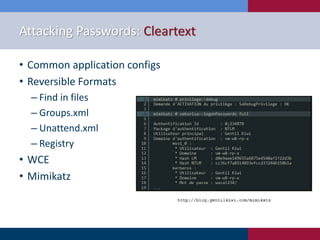
The document discusses various strategies and techniques used in penetration testing, highlighting the importance of such tests for compliance, risk evaluation, and breach prevention. It covers attacking protocols, password vulnerabilities, application flaws, and methods for bypassing endpoint protection, emphasizing common mitigating controls. The findings suggest that most networks, protocols, and applications need improvements to enhance security.