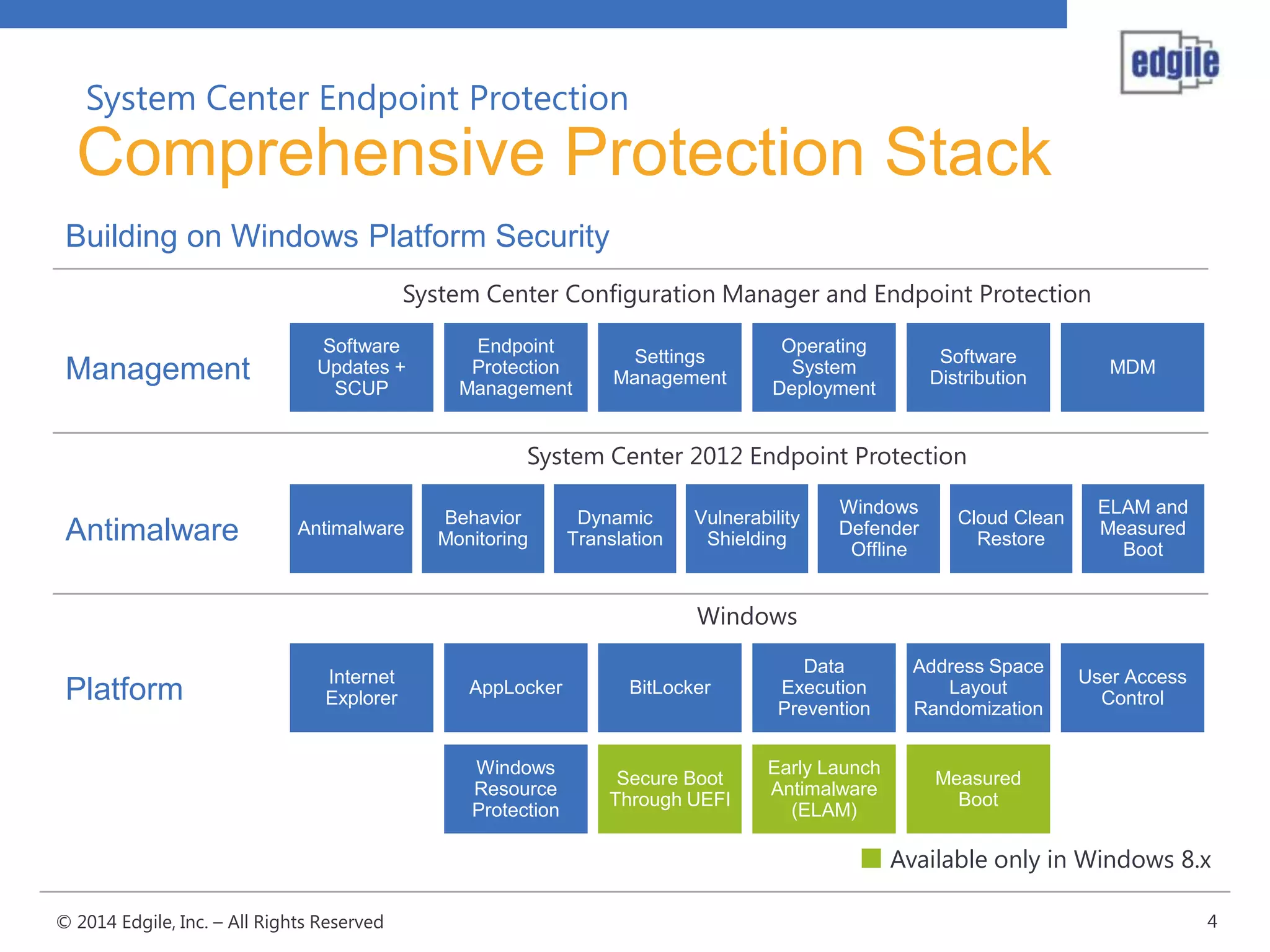
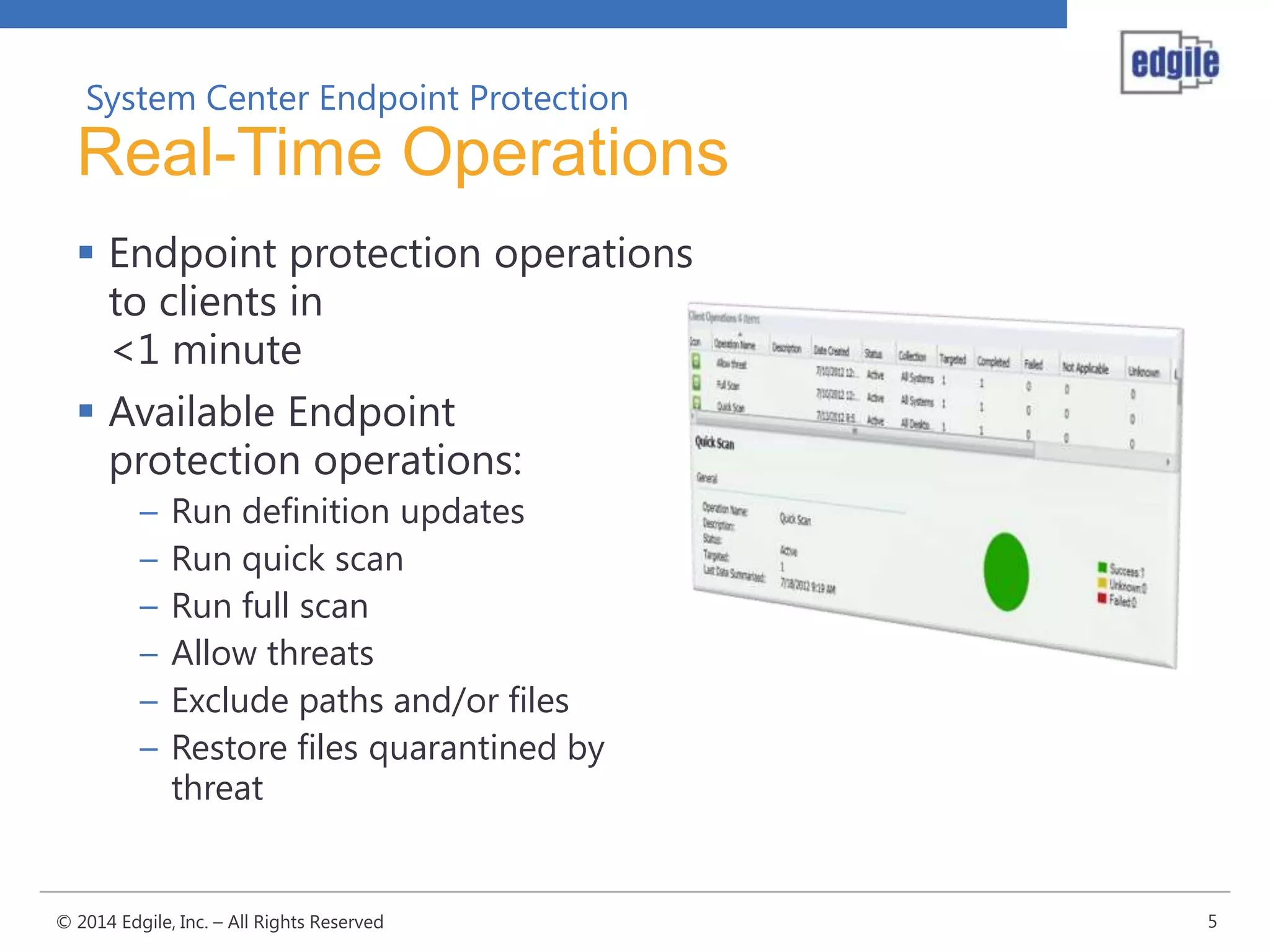
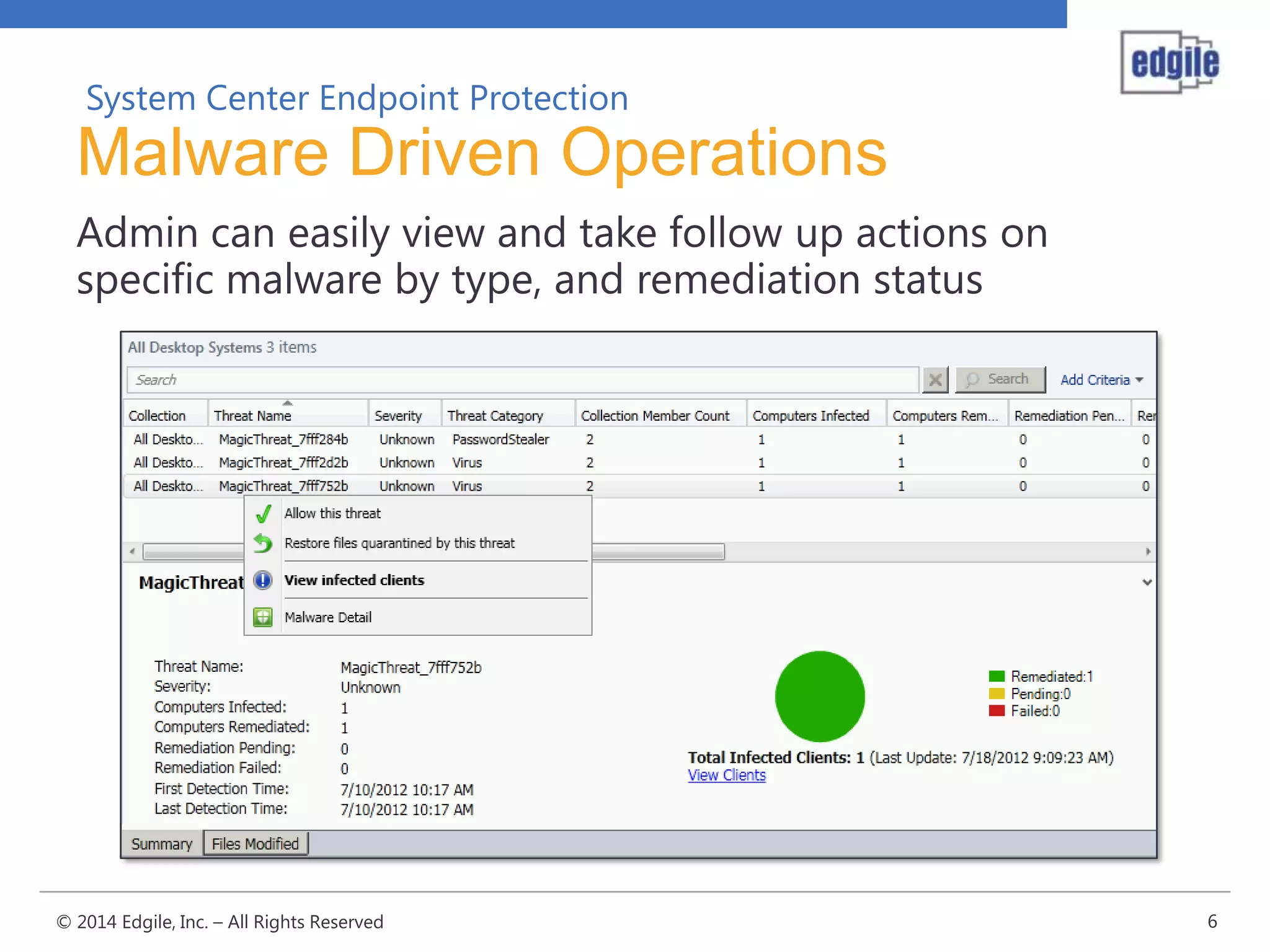
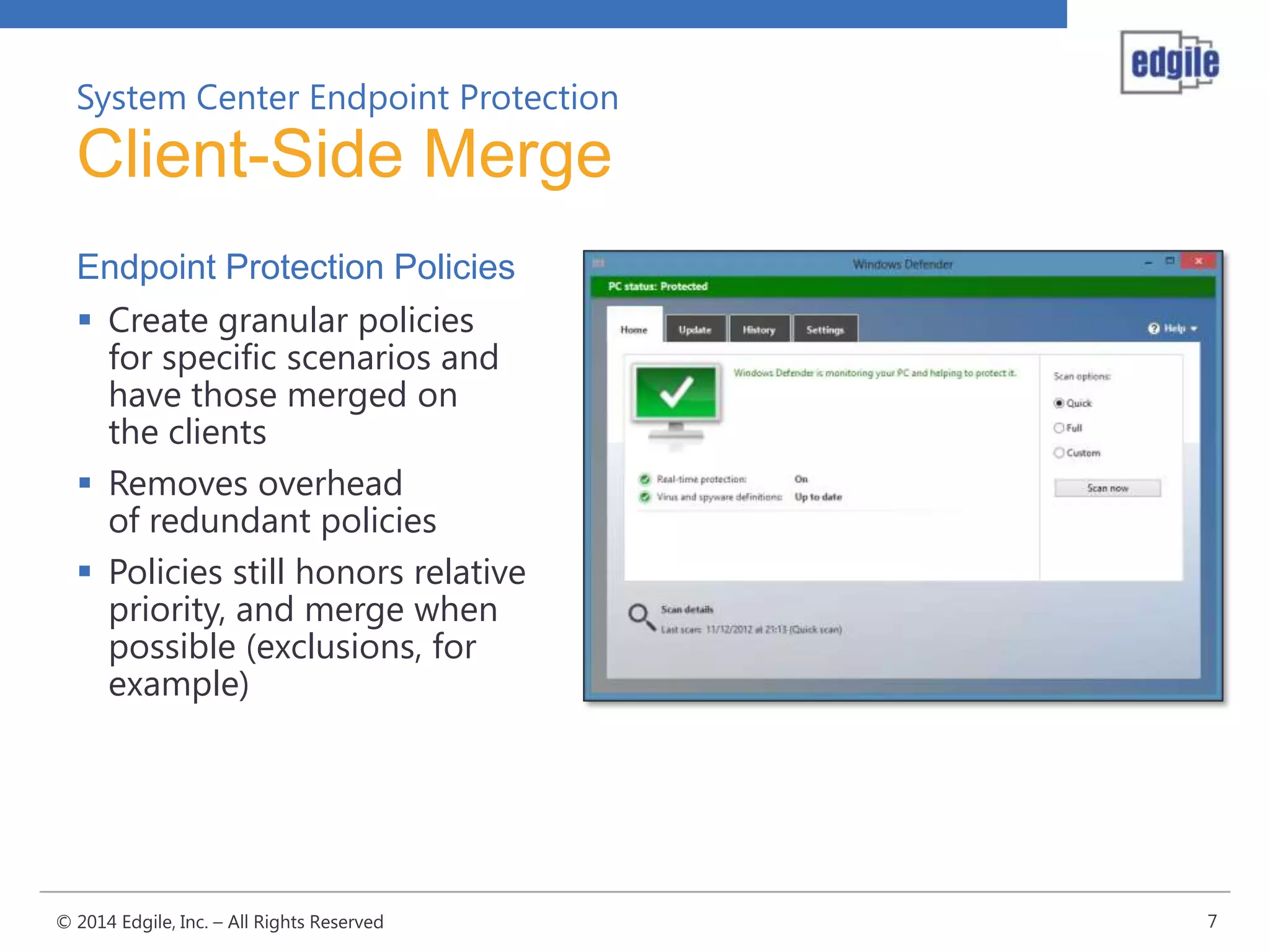
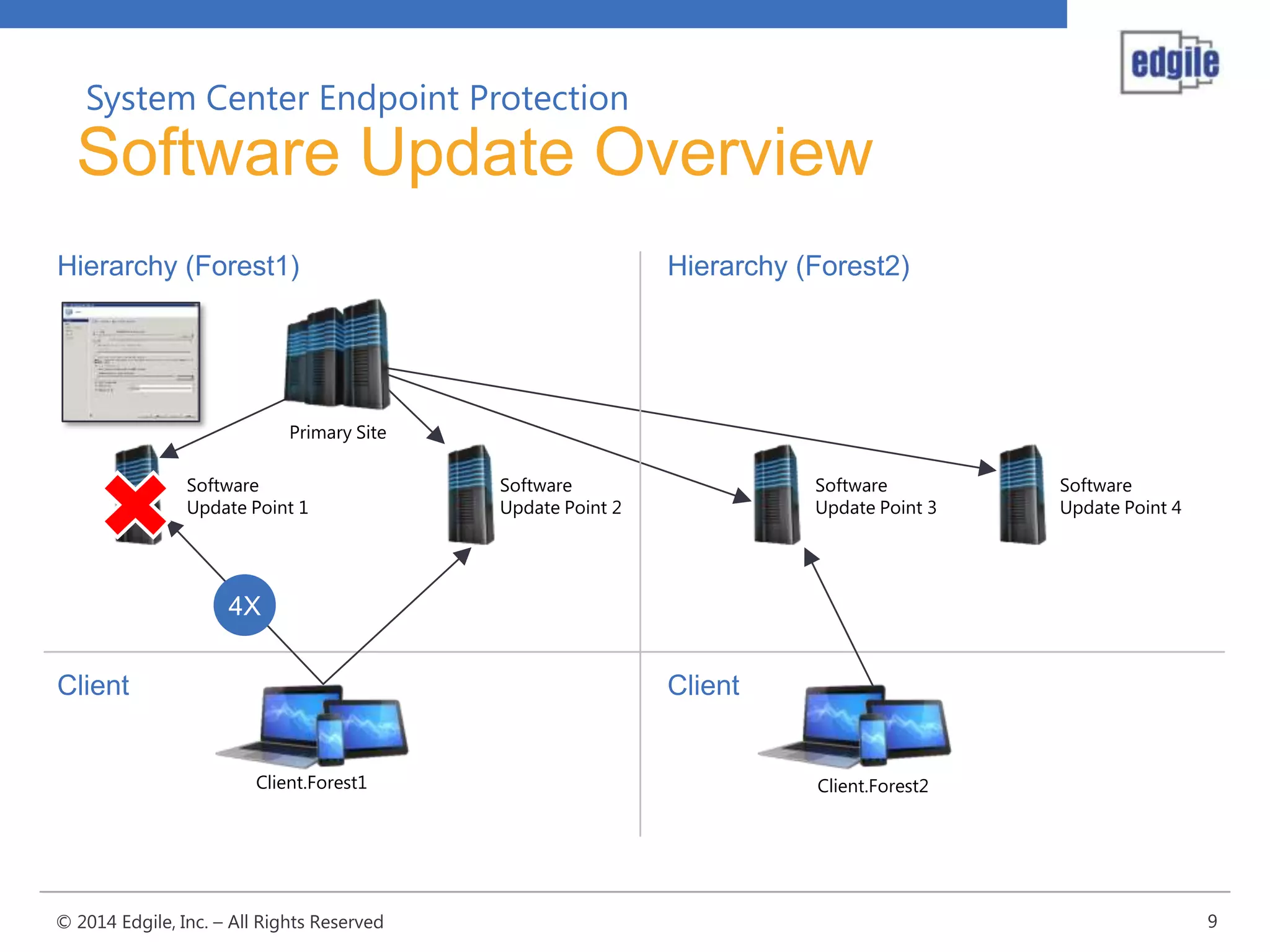
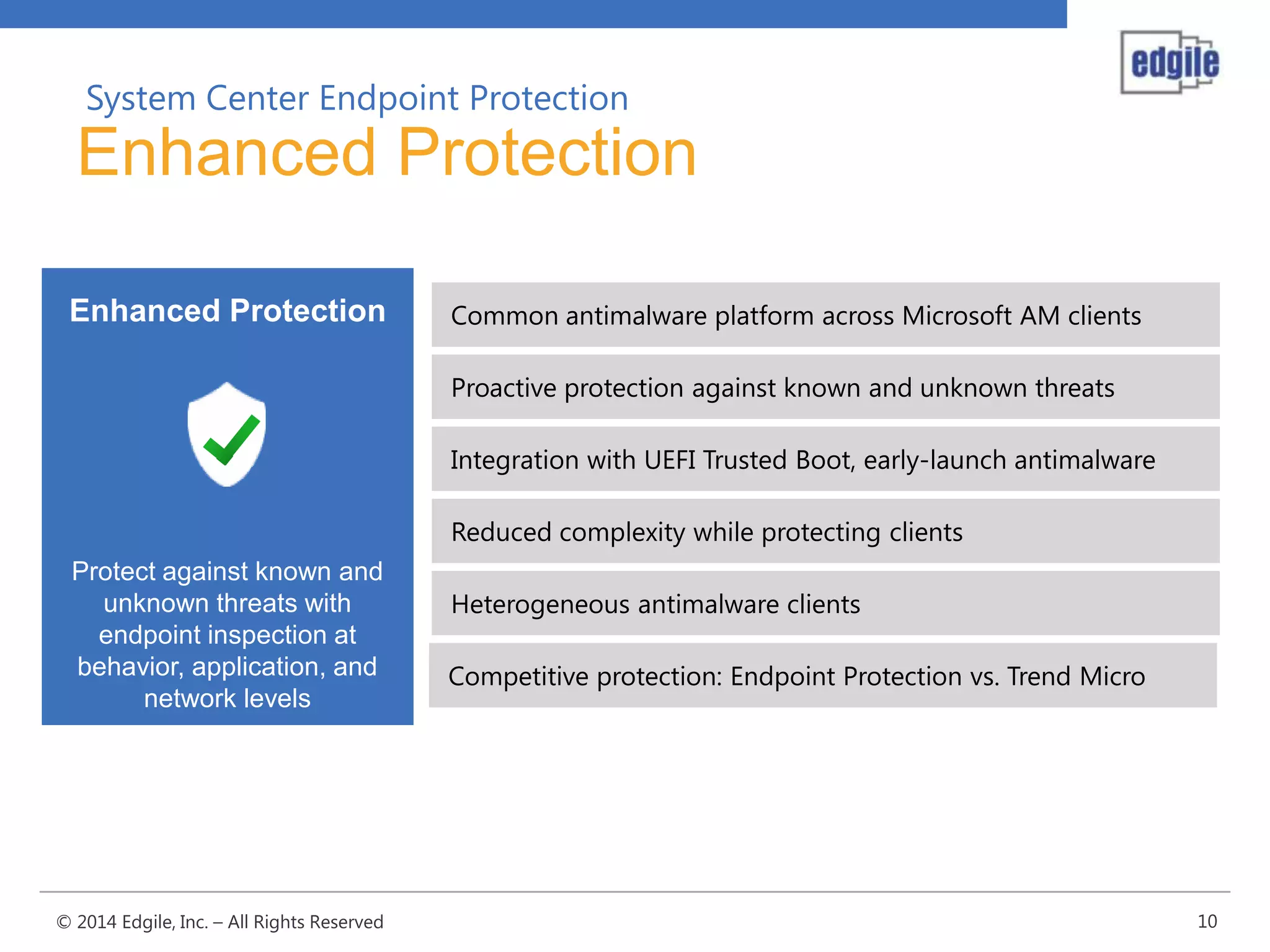
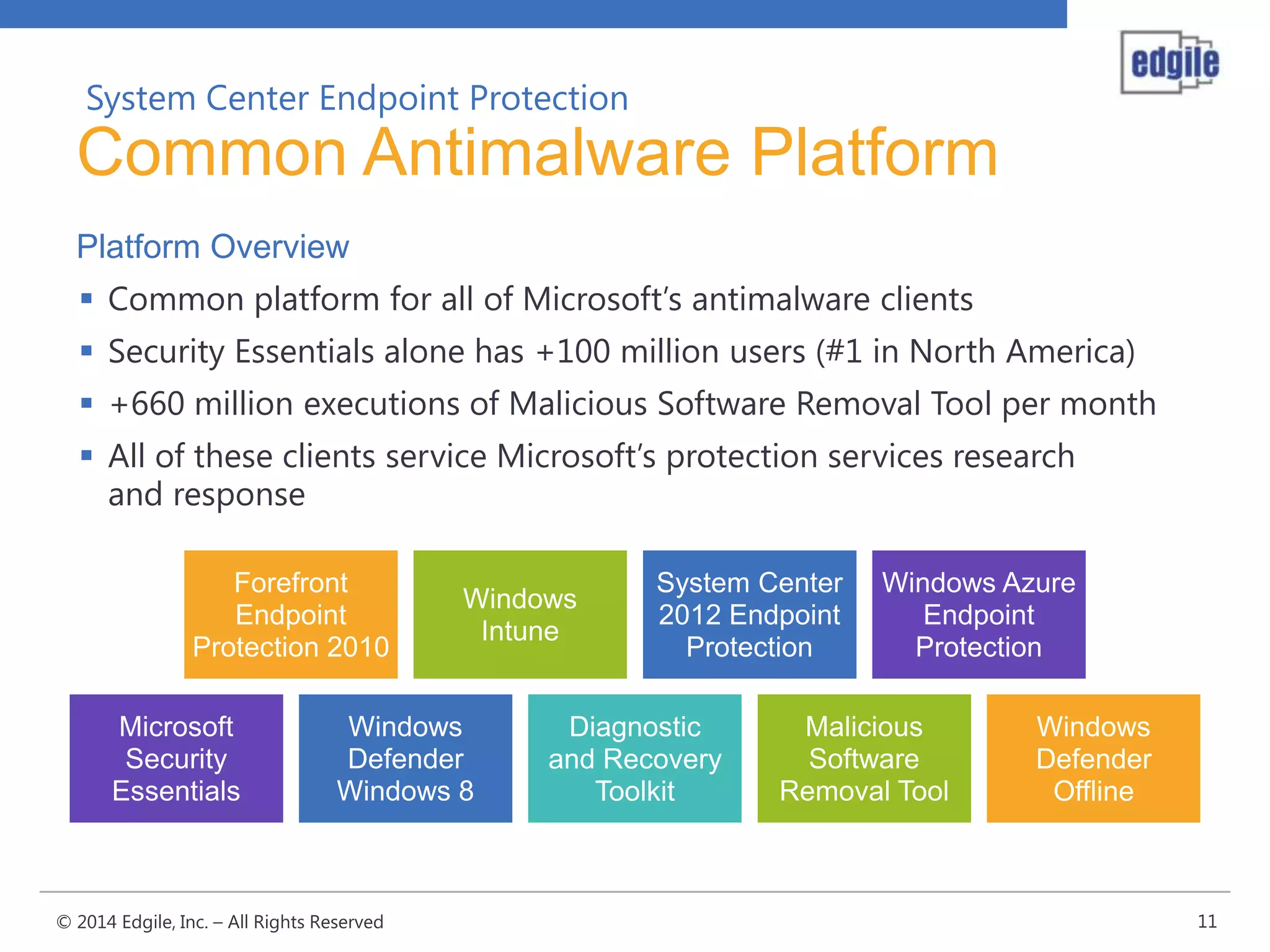
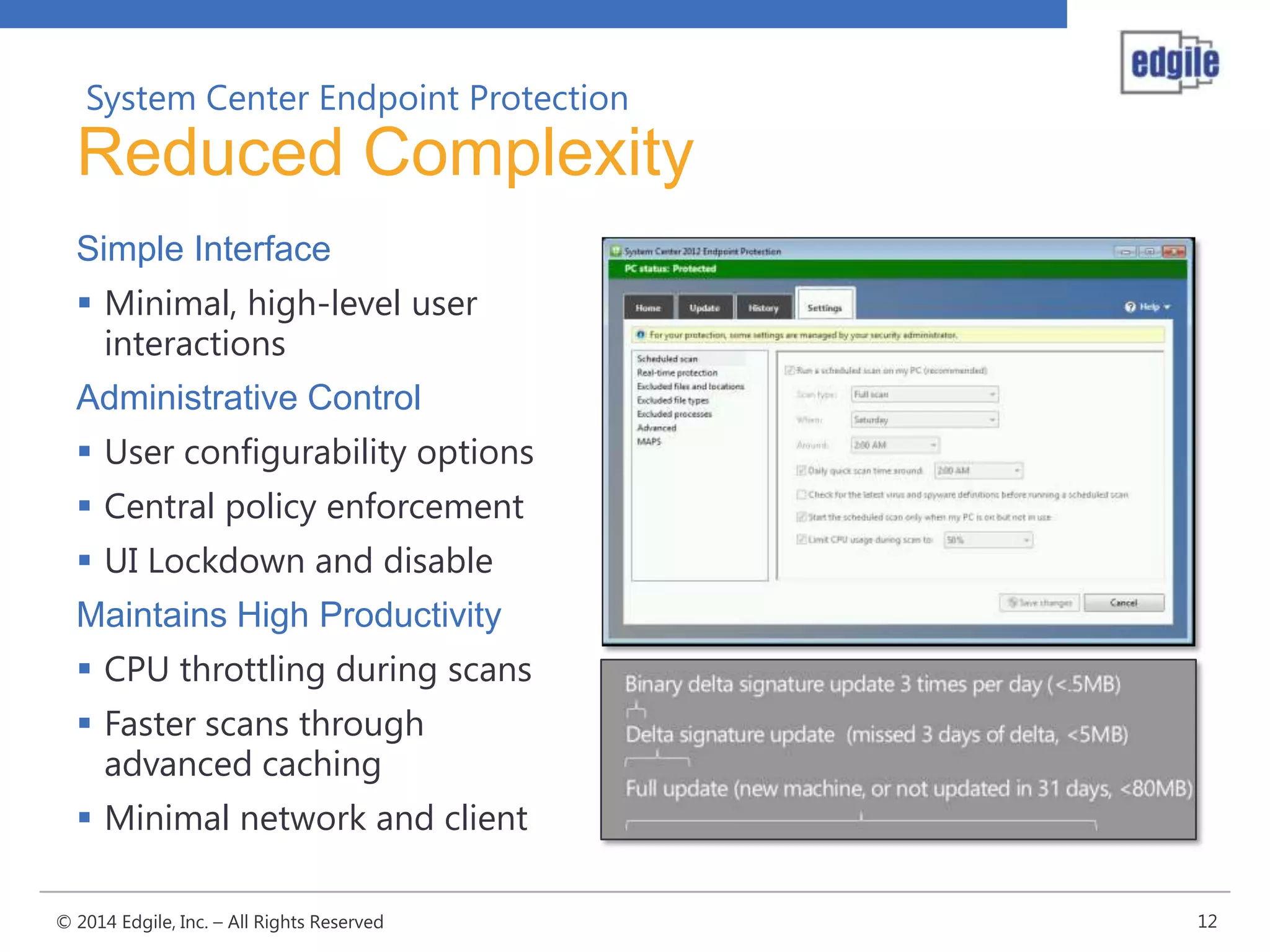
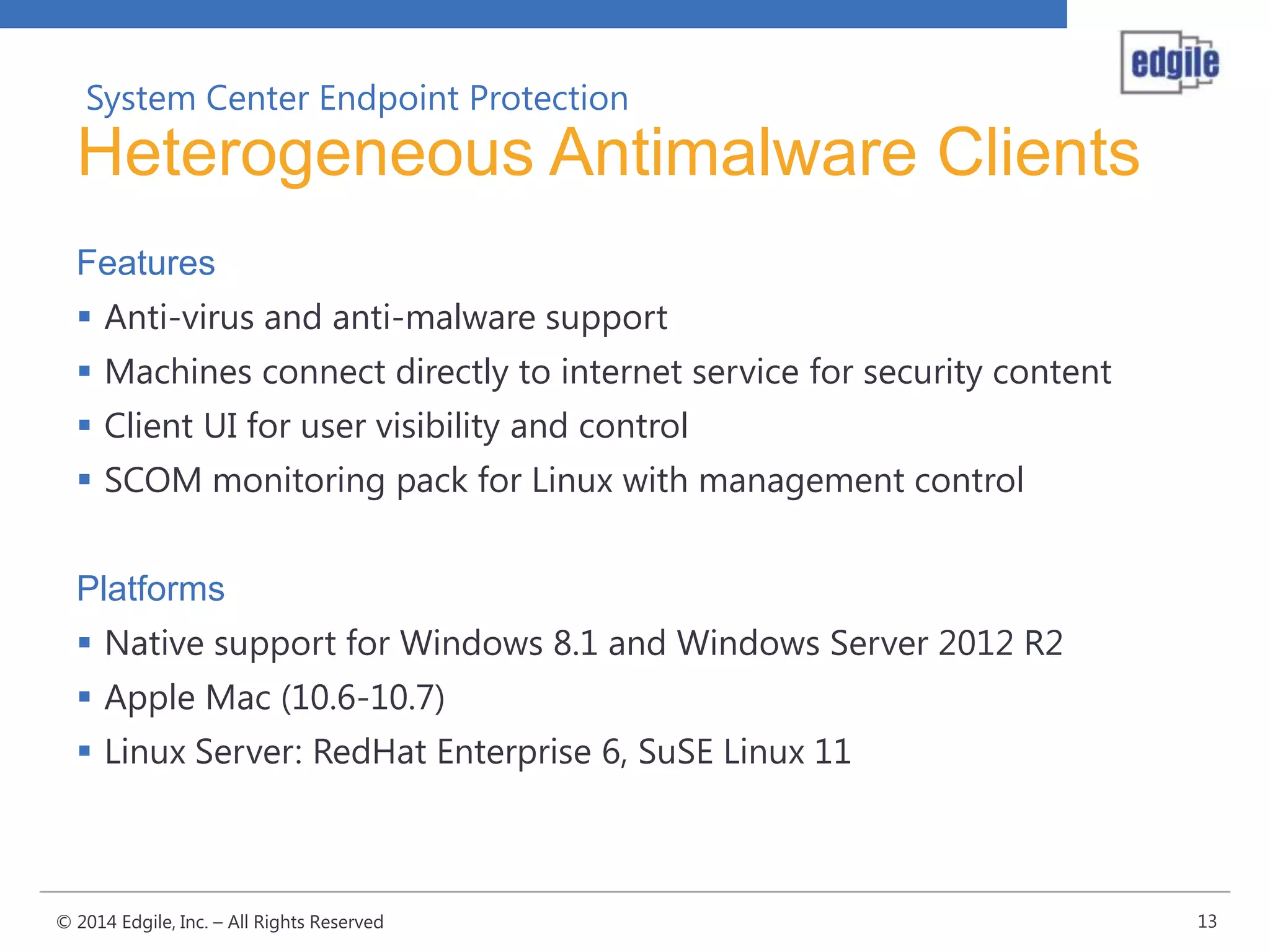
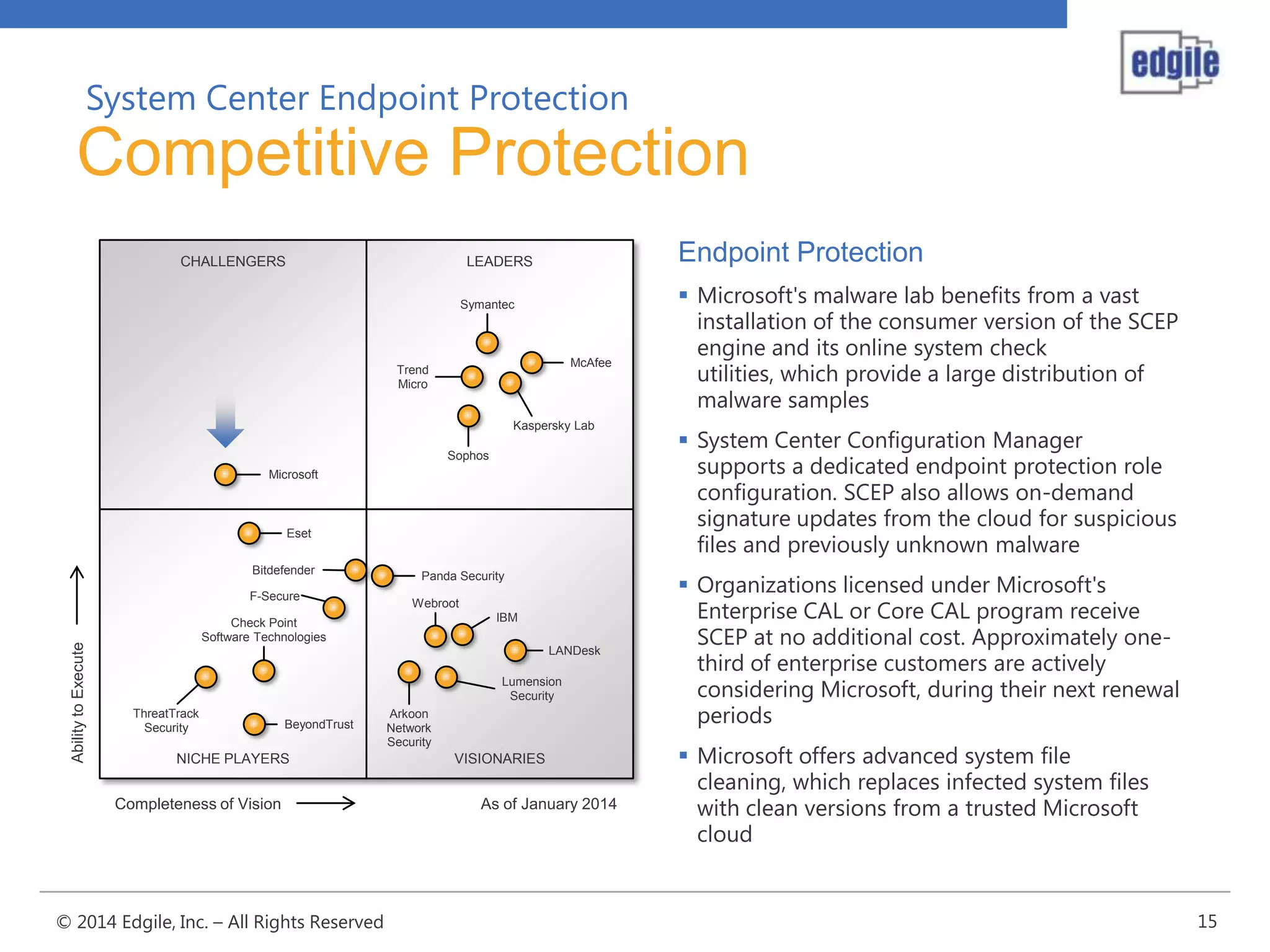
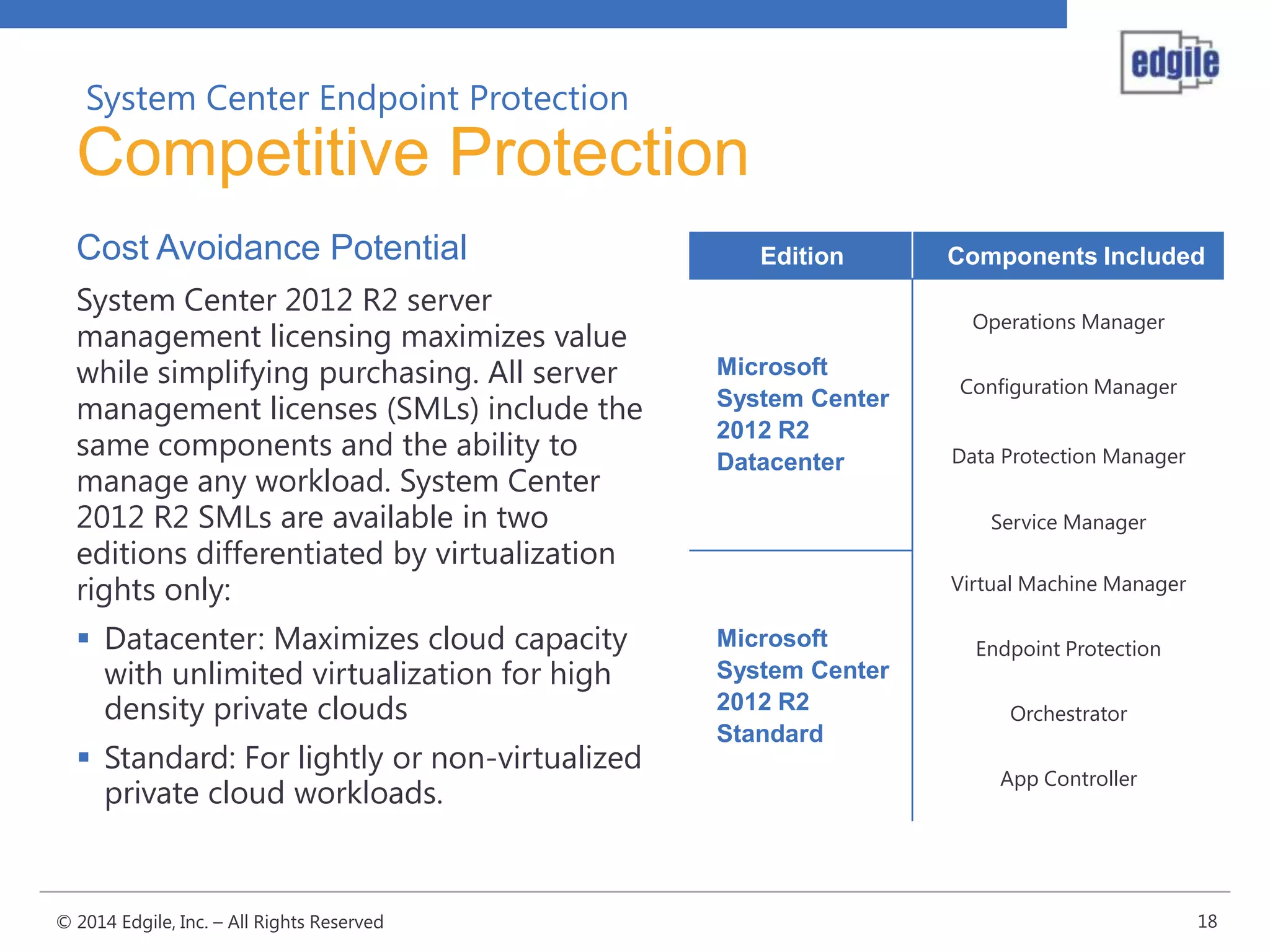
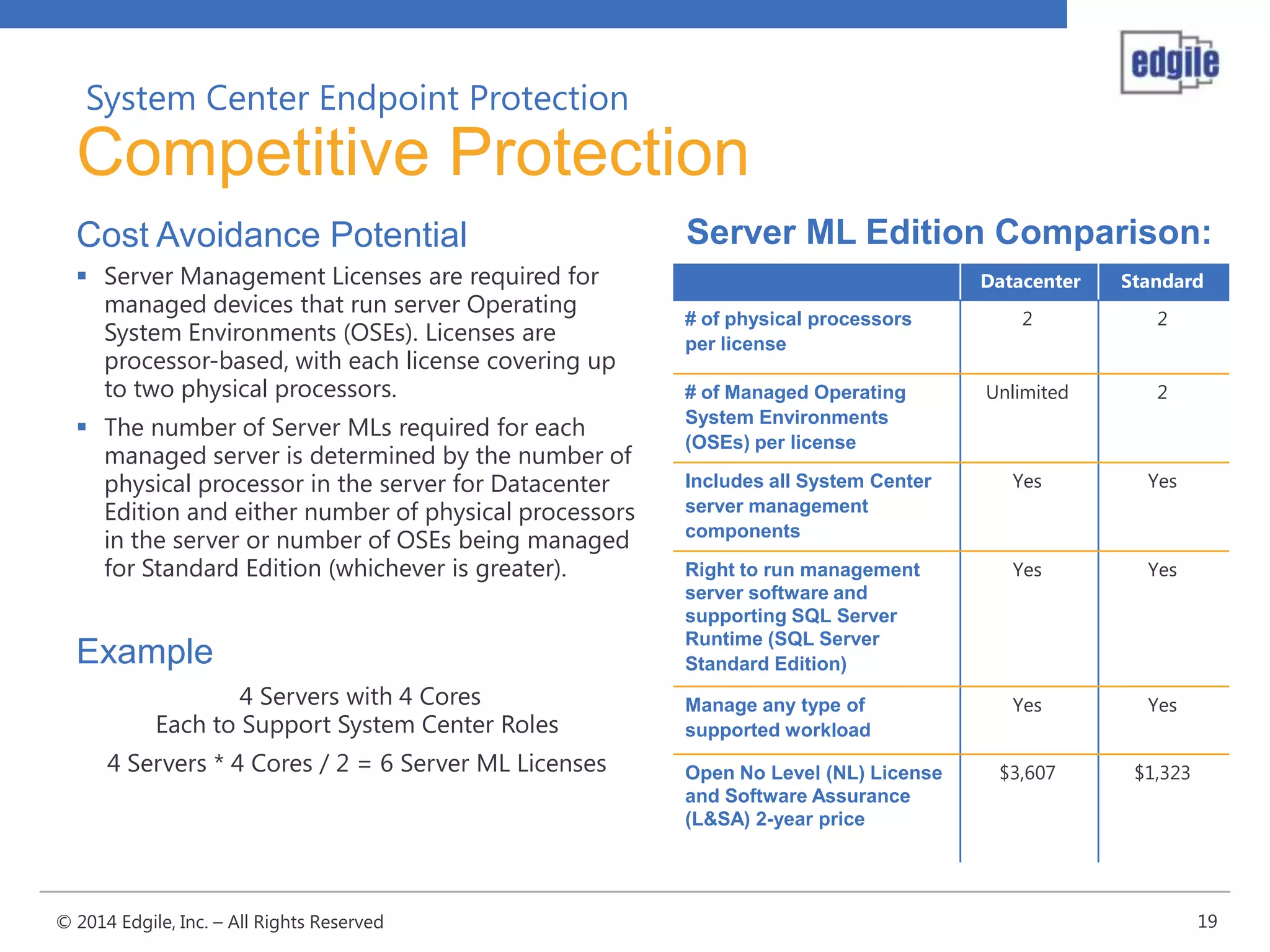
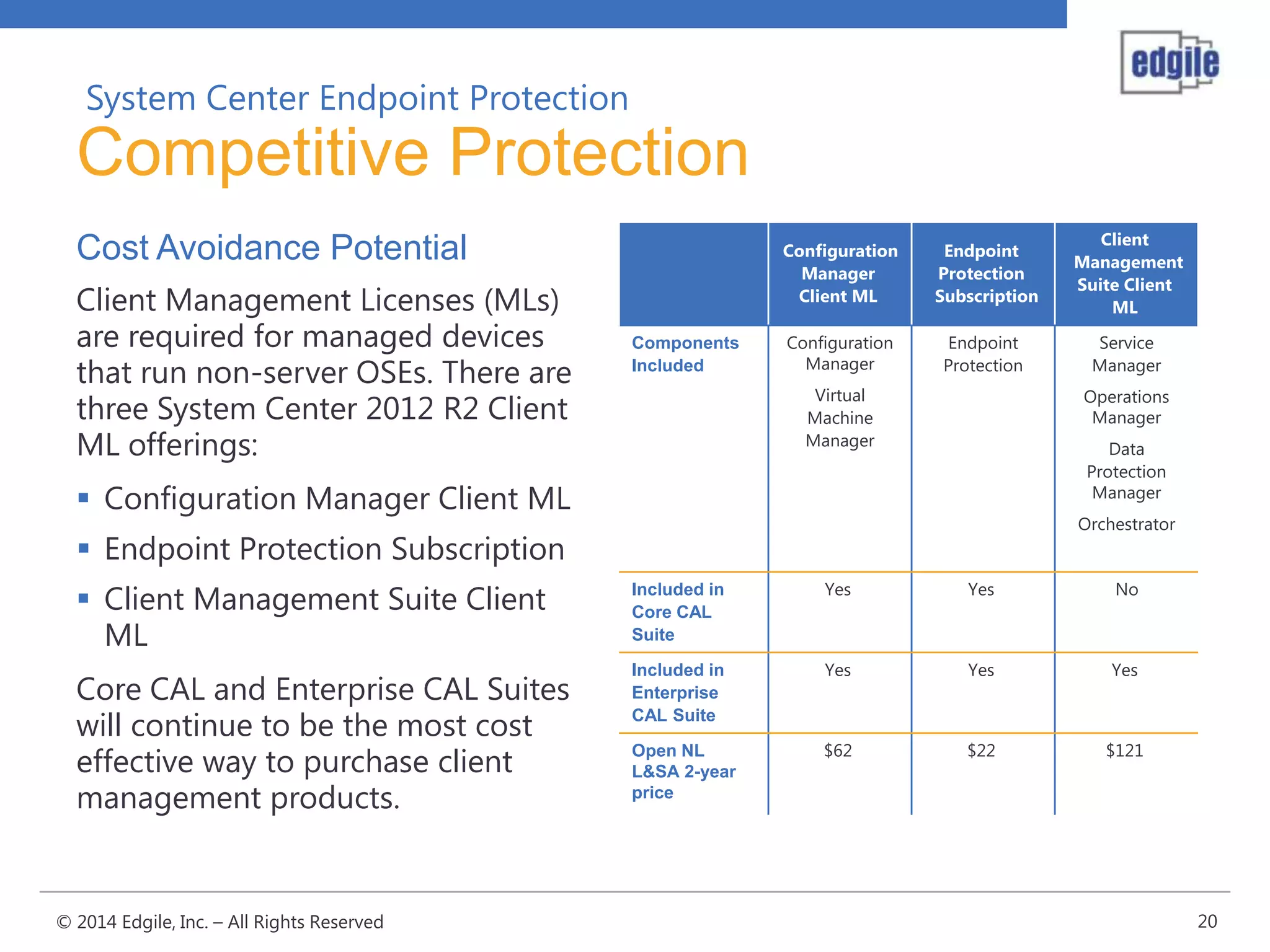
System Center Endpoint Protection 2012 R2 provides comprehensive malware protection and simplified administration capabilities. It features a common antimalware platform across Microsoft clients, proactive protection against known and unknown threats through endpoint inspection, and support for heterogeneous platforms including Windows, Mac, and Linux. While it faces some challenges from competitors like Trend Micro in testing scores and feature breadth, Microsoft leverages other Windows security features and benefits from its large malware sample collection through consumer products.