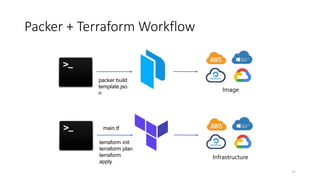
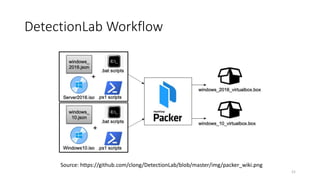
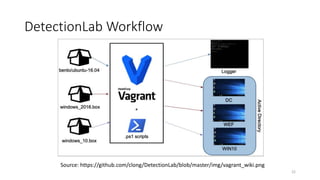
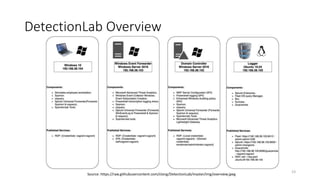
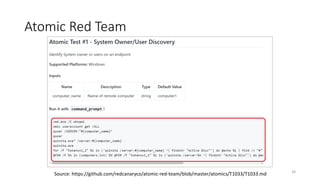
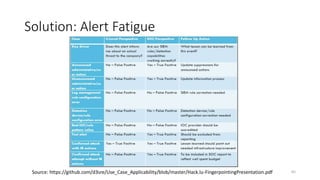
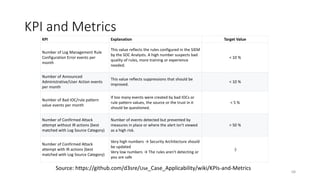
This document discusses improving detection rules coverage through infrastructure automation tools, testing frameworks, and metrics. It introduces tools like Packer, Vagrant, Terraform, and DetectionLab for building detection environments. Atomic Red Team and the MITRE ATT&CK framework are covered for testing detections. Metrics like the ATT&CK heatmap and KPIs are suggested for measuring coverage. Common pitfalls like assuming full coverage and not prioritizing are addressed.