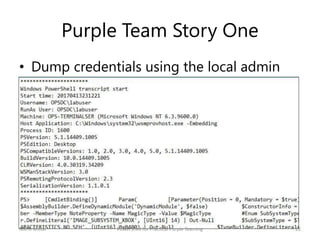
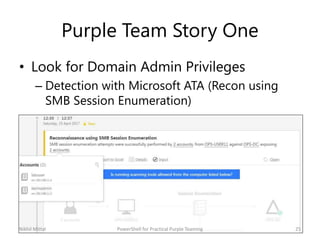
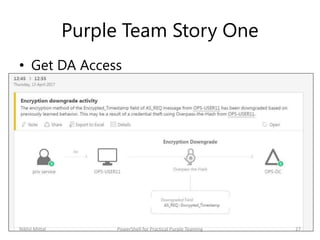
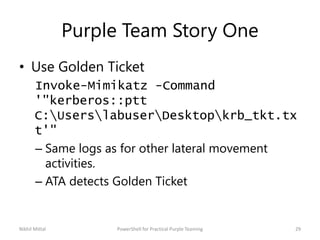
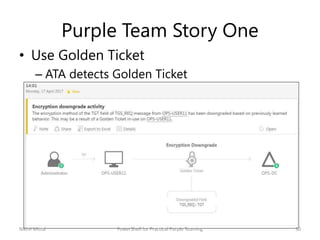
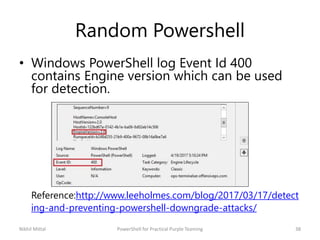
The document discusses purple teaming, which involves red and blue teams working together to improve security. It provides two examples using PowerShell to simulate insider threats and client-side attacks. The first story involves escalating privileges from a normal user to domain admin and creating a golden ticket. The second starts as a non-admin user using a client-side attack like an HTA when PowerShell is blocked. Detection methods like logs, Applocker, and network monitoring are also outlined. The document concludes purple teaming aims to maximize threat simulation benefits by bringing red and blue teams together.
































![Random Powershell
• AMSI can be unloaded using methods like:
amsi.dll hijack (p0wnedshell)
[Ref].Assembly.GetType('System.Management
.Automation.AmsiUtils').GetField('amsiIni
tFailed','NonPublic,Static').SetValue($nu
ll,$true) - by Matt Graeber - Event ID 4104
(Microsoft-Windows-PowerShell/Operational) –
Suspicious script block logging
Nikhil Mittal 42PowerShell for Practical Purple Teaming](https://image.slidesharecdn.com/powershellforpurpleteaming-170502133334/85/PowerShell-for-Practical-Purple-Teaming-42-320.jpg)