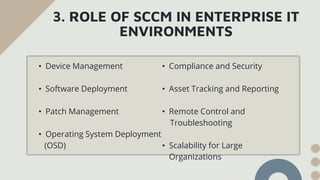
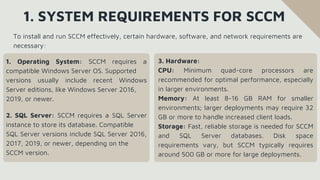
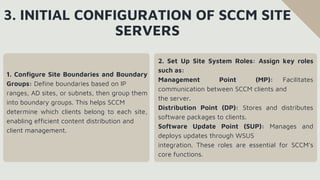
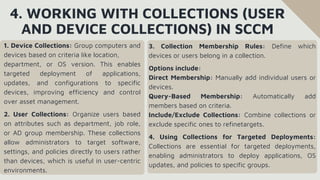
The document provides an overview of System Center Configuration Manager (SCCM), a Microsoft tool for managing devices and applications in an organization to enhance efficiency, security, and compliance. It details SCCM's architecture, key components, and roles in enterprise IT, emphasizing its capabilities for device management, software deployment, and patch management. Additionally, it covers installation requirements, configuration steps, and the benefits of using SCCM for automated IT tasks and resource optimization.