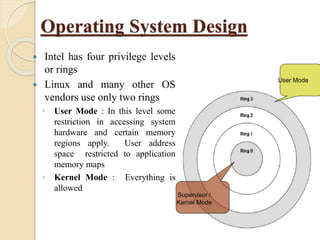
Spyware is software designed to gather information covertly from users, often without their consent, and can take various forms such as system monitors, trojans, adware, and tracking cookies. Major spyware examples include Gator, Cydoor, and Ezula, which collect user data for advertising purposes and can degrade computer performance. Rootkits are another form of malicious software that allows attackers to maintain access and hide their activity within compromised systems.