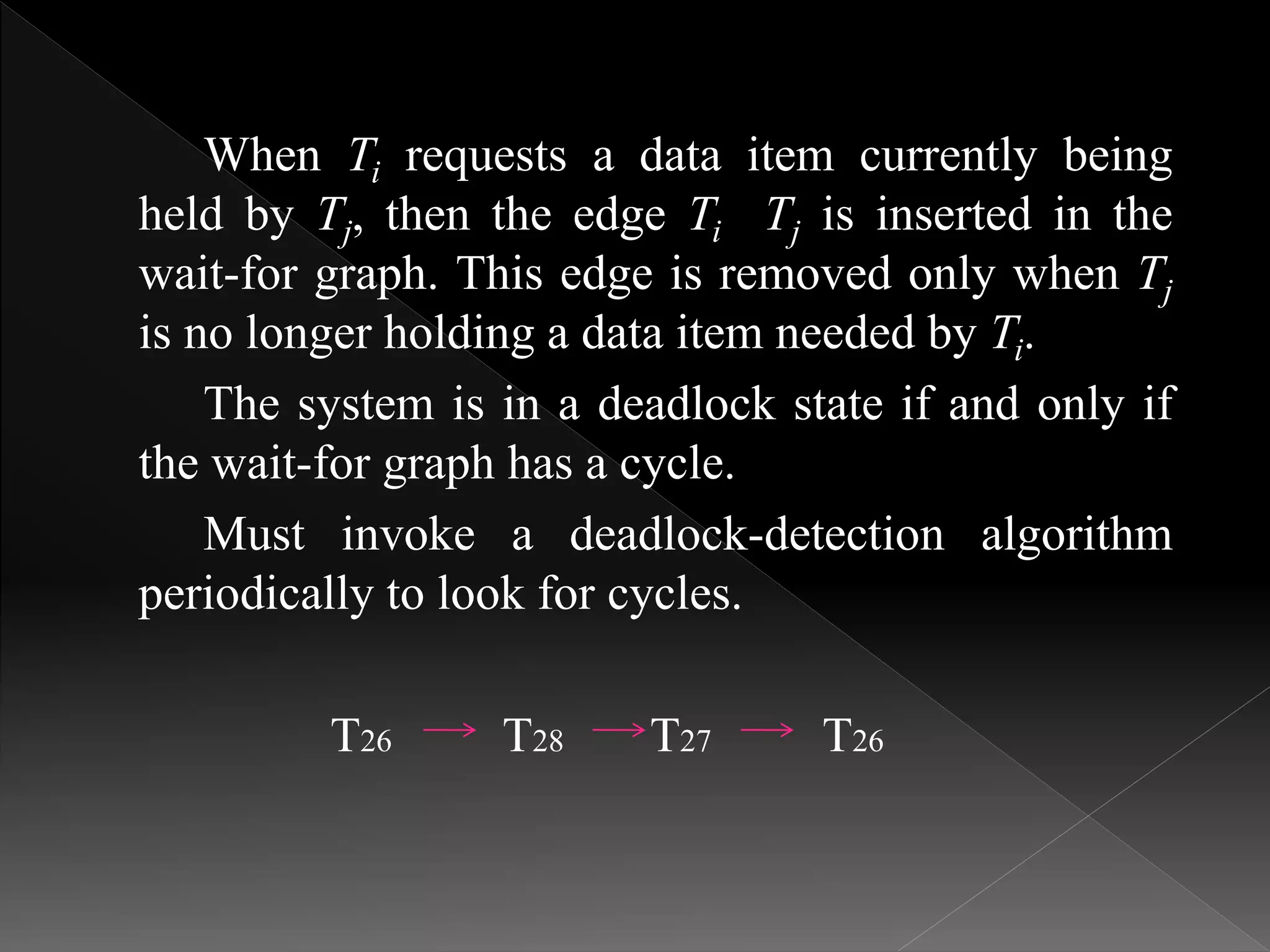
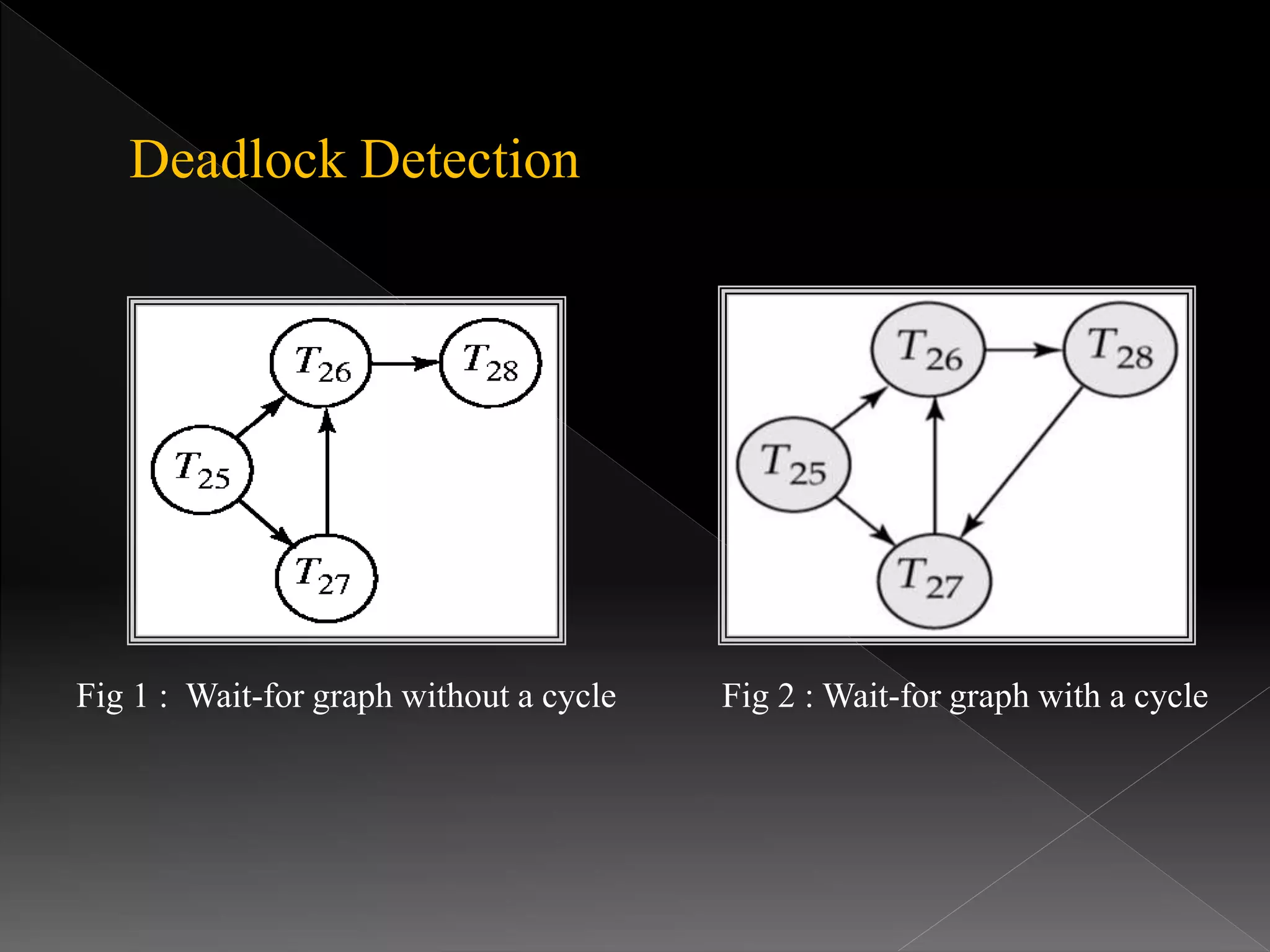
The document discusses different methods for handling deadlocks in transactional systems, including deadlock prevention, detection, and recovery. It describes two main prevention techniques: pre-declaration ordering and partial ordering of locks. It also covers two timestamp-based prevention schemes called wait-die and wound-wait. For detection, it explains using a wait-for graph to model lock dependencies and detect cycles that indicate a deadlock. Recovery involves selecting a victim transaction to rollback to break the deadlock cycle.