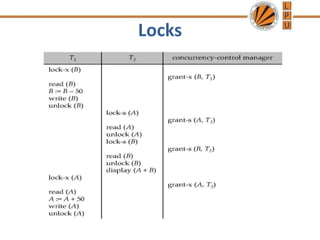
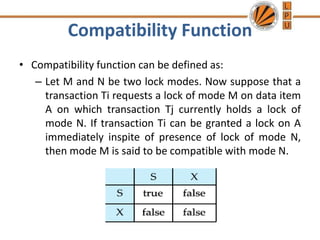
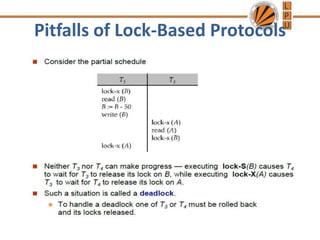
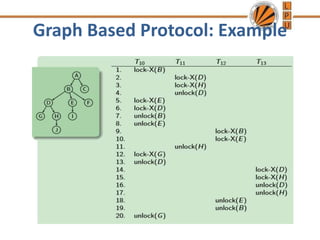
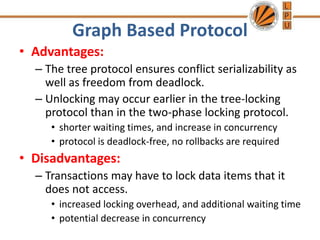
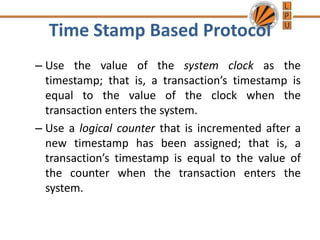
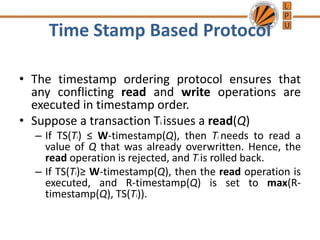
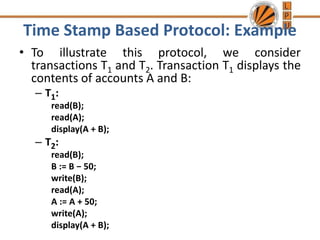
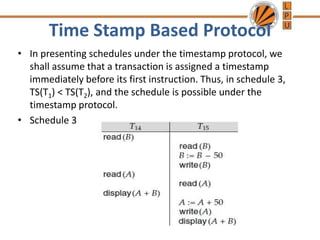
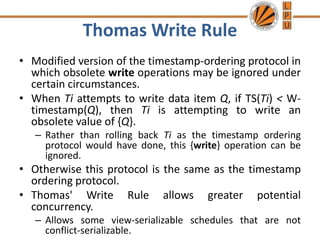
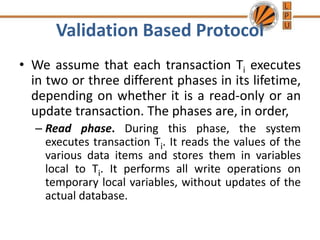
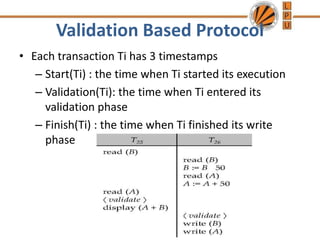
Concurrency control mechanisms use various protocols like lock-based, timestamp-based, and validation-based to maintain database consistency when transactions execute concurrently. Lock-based protocols use locks on data items to control concurrent access, with two-phase locking being a common approach. Timestamp-based protocols order transactions based on timestamps to ensure serializability. Validation-based protocols validate that a transaction's writes do not violate serializability before committing its writes.