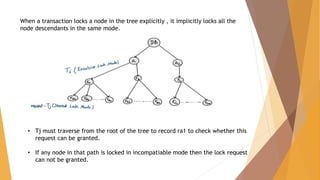
This document discusses validation based protocol, an optimistic concurrency control technique used in database management systems. It has three phases - read, validation, and write. In the read phase, transactions read data into local variables without updating the database. In the validation phase, a test checks for serializability violations between transactions. If there are no violations, the transaction commits its writes to the database in the write phase. The protocol uses timestamps to order transactions and avoid conflicts. It can avoid cascading rollbacks but has a risk of starvation for long transactions. The document also discusses multiple granularity locking, which defines a hierarchy of data sizes from fine to coarse granularity to control concurrent access.