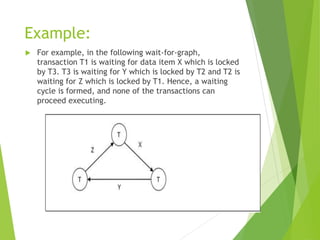
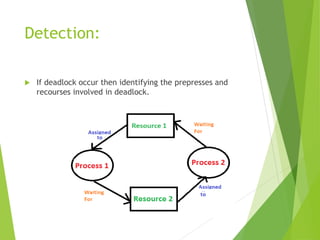
A deadlock occurs in a database when two or more transactions are waiting for each other to release locked data items, resulting in a cycle in the wait-for-graph. Various methods to handle deadlocks include ignoring the issue, detection and removal, prevention through lock acquisition rules, and avoidance using algorithms like wait-die and wound-wait. Additionally, failures can be categorized as soft or hard failures, impacting both volatile memory and persistent storage.