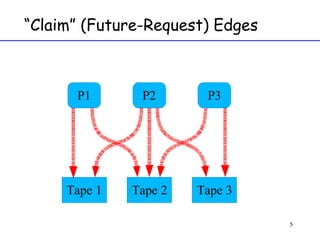
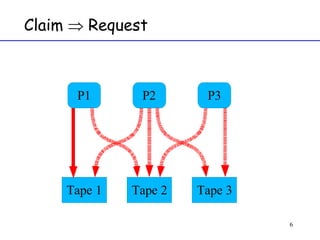
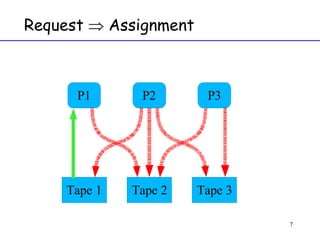
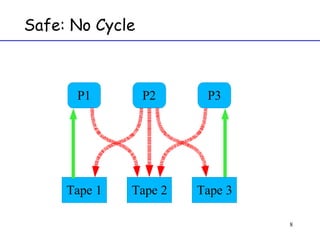
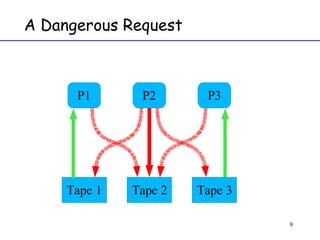
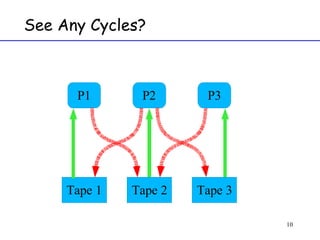
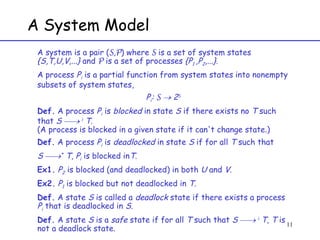
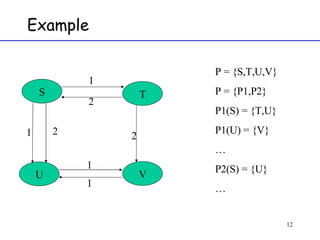
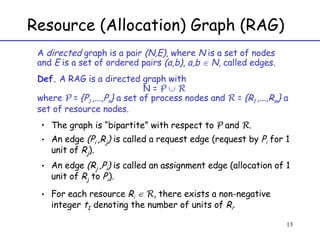
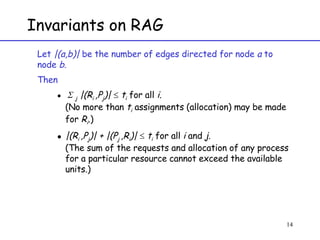
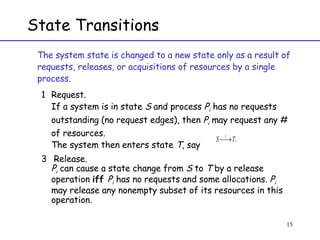
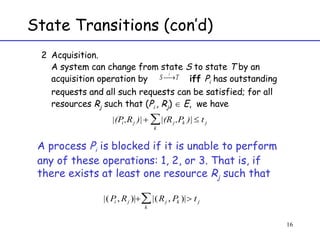
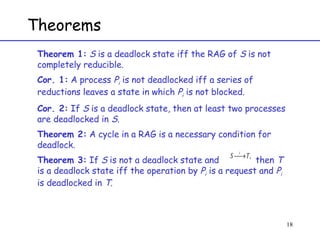
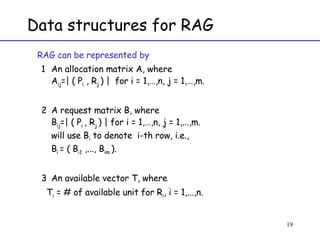
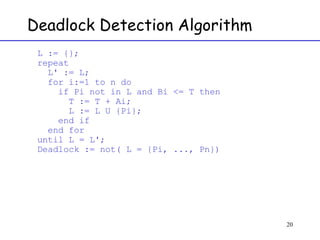
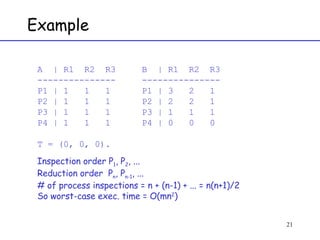
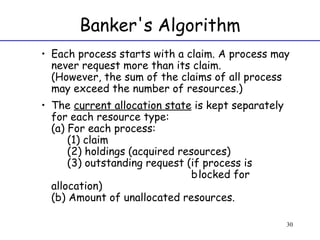
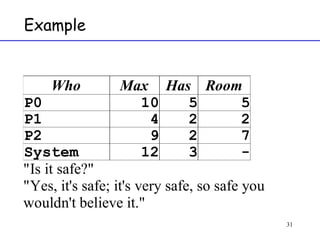
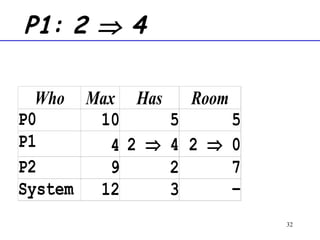
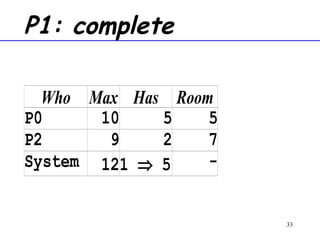
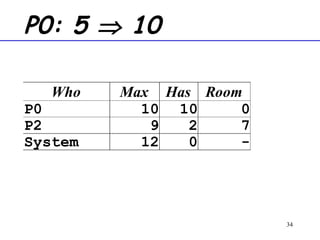
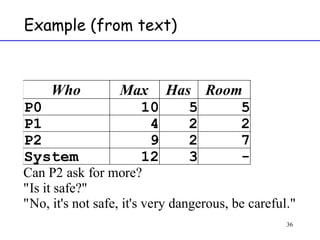
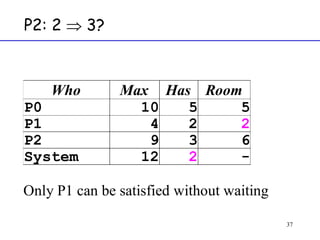
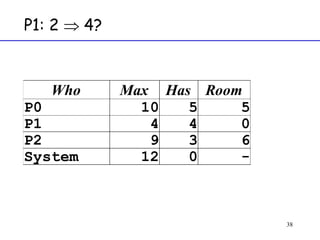
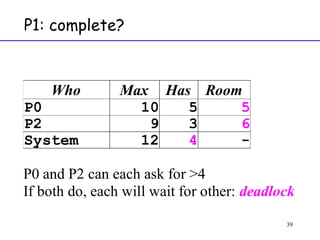
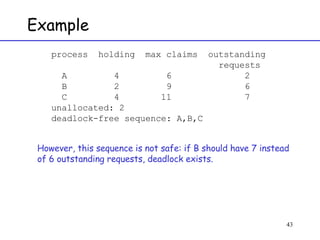
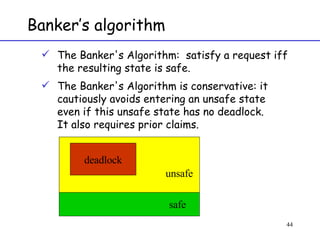
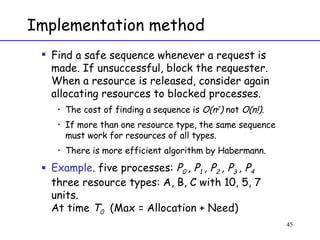
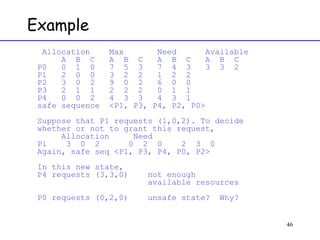
The document discusses deadlock in computer systems. It defines deadlock and lists necessary conditions for deadlock including mutual exclusion, hold and wait, no preemption, and circular wait. It also discusses strategies for dealing with deadlock such as detection, recovery, and prevention/avoidance. The resource allocation graph (RAG) model is introduced as a way to represent system states and detect deadlock. Algorithms like Banker's algorithm aim to avoid deadlock by ensuring safe allocation of resources.