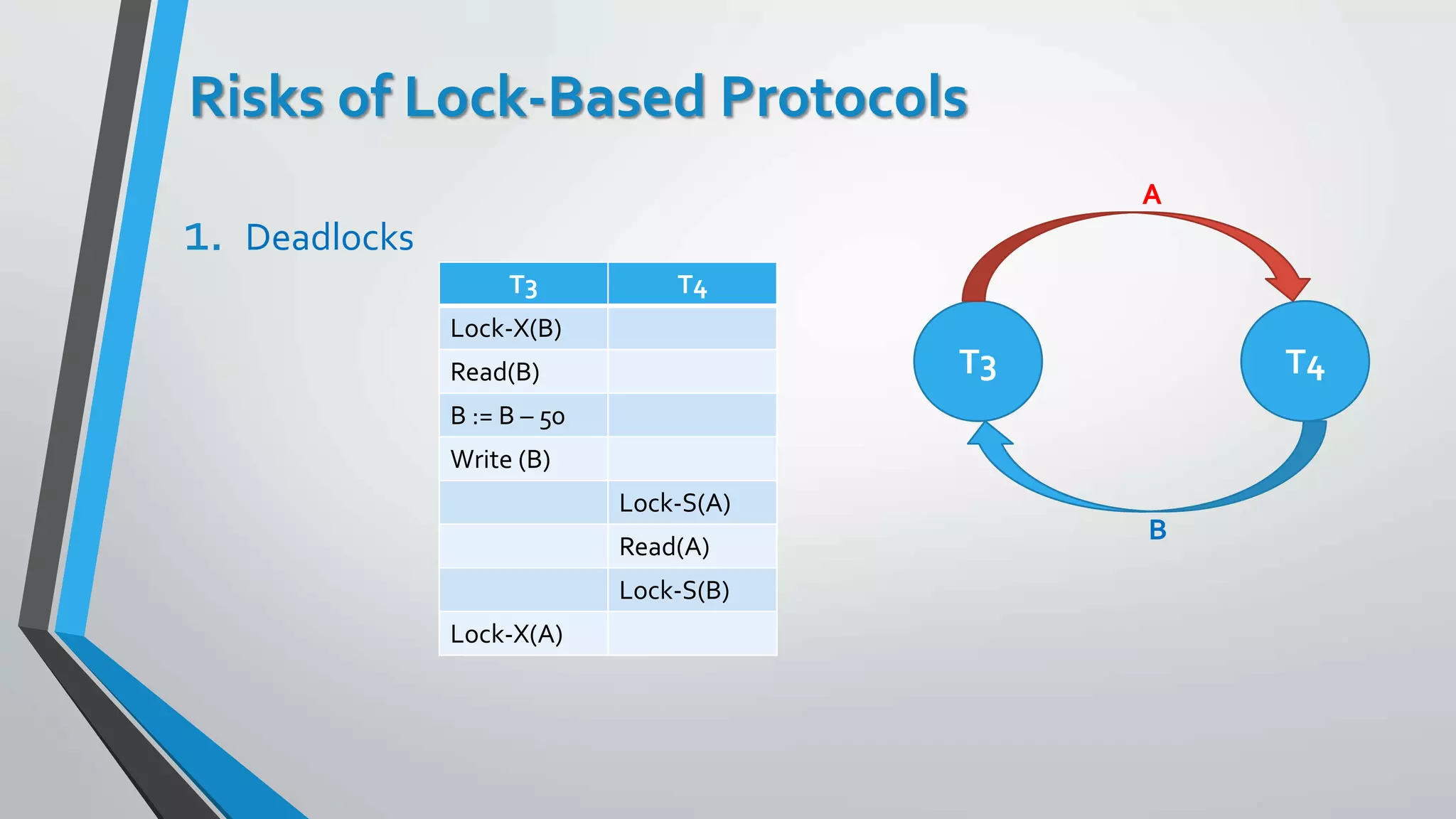
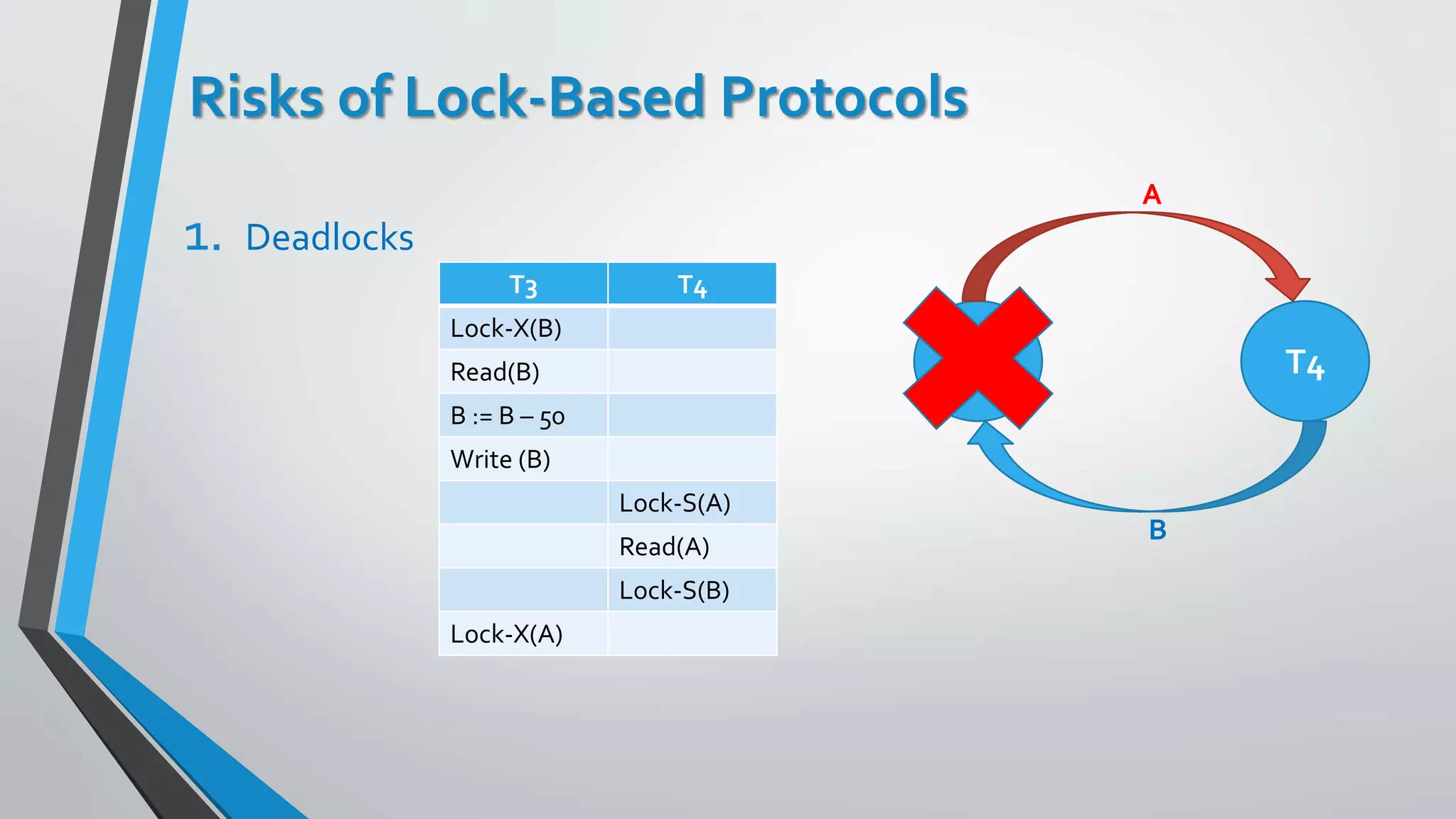
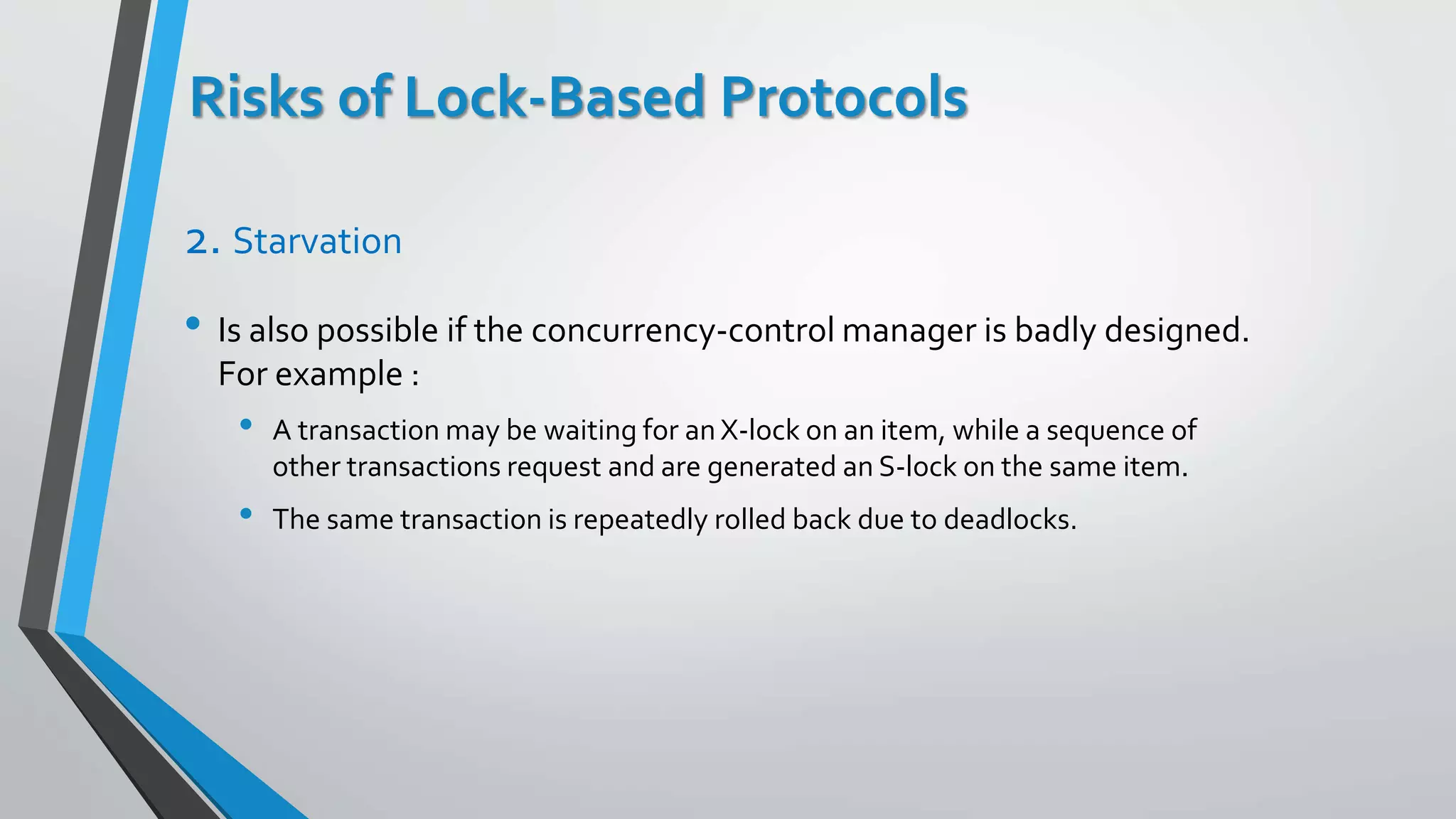
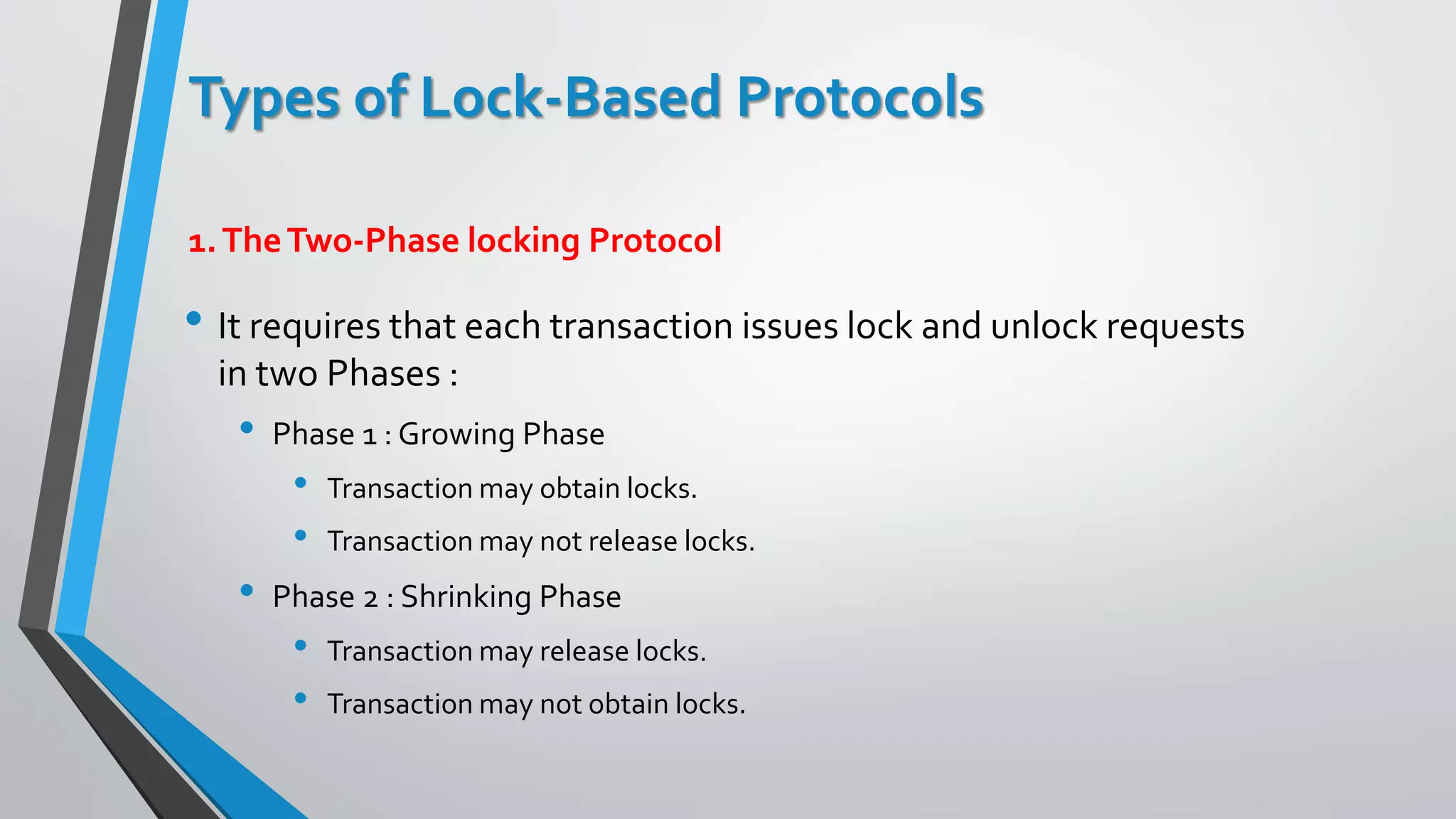
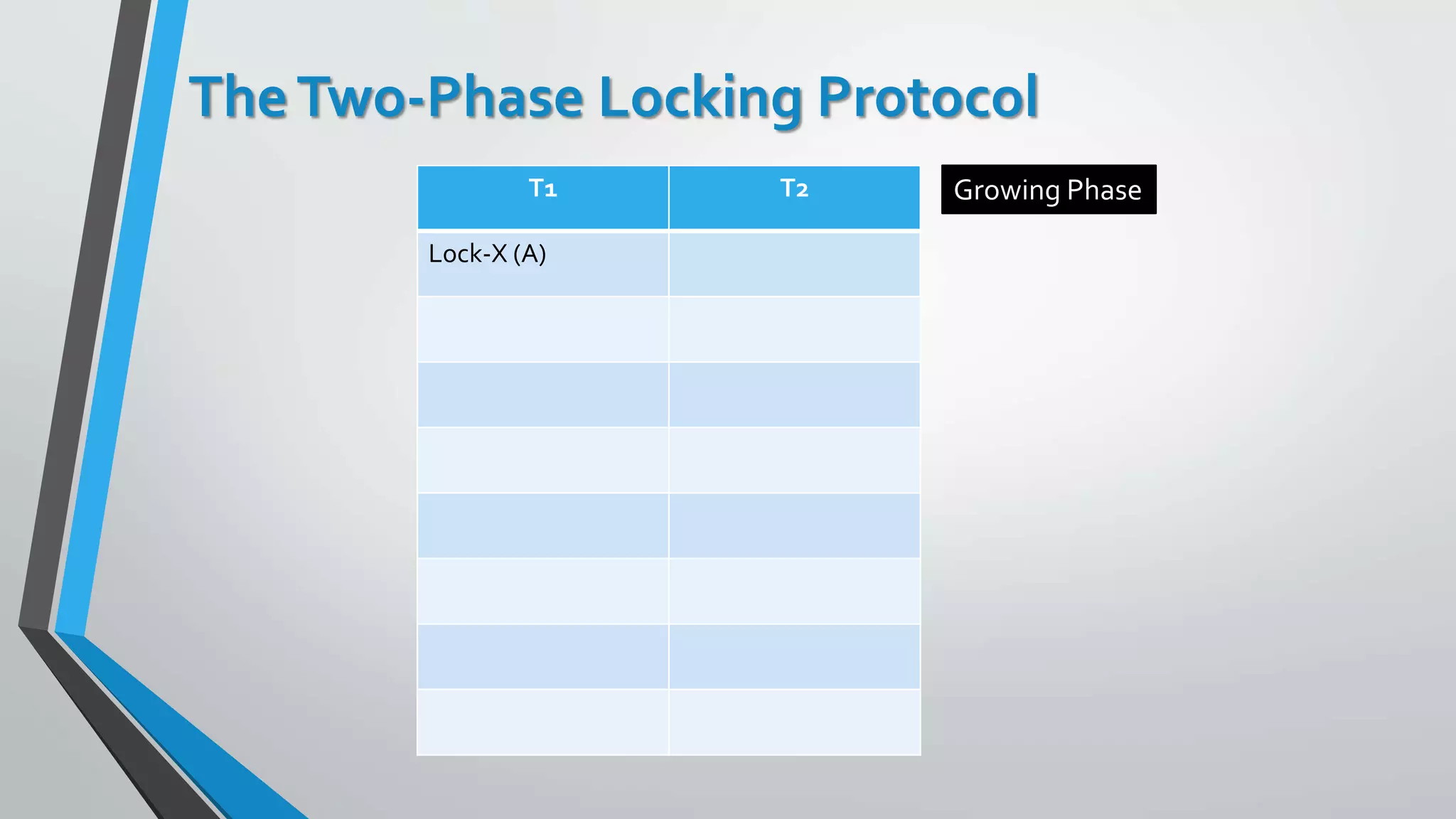
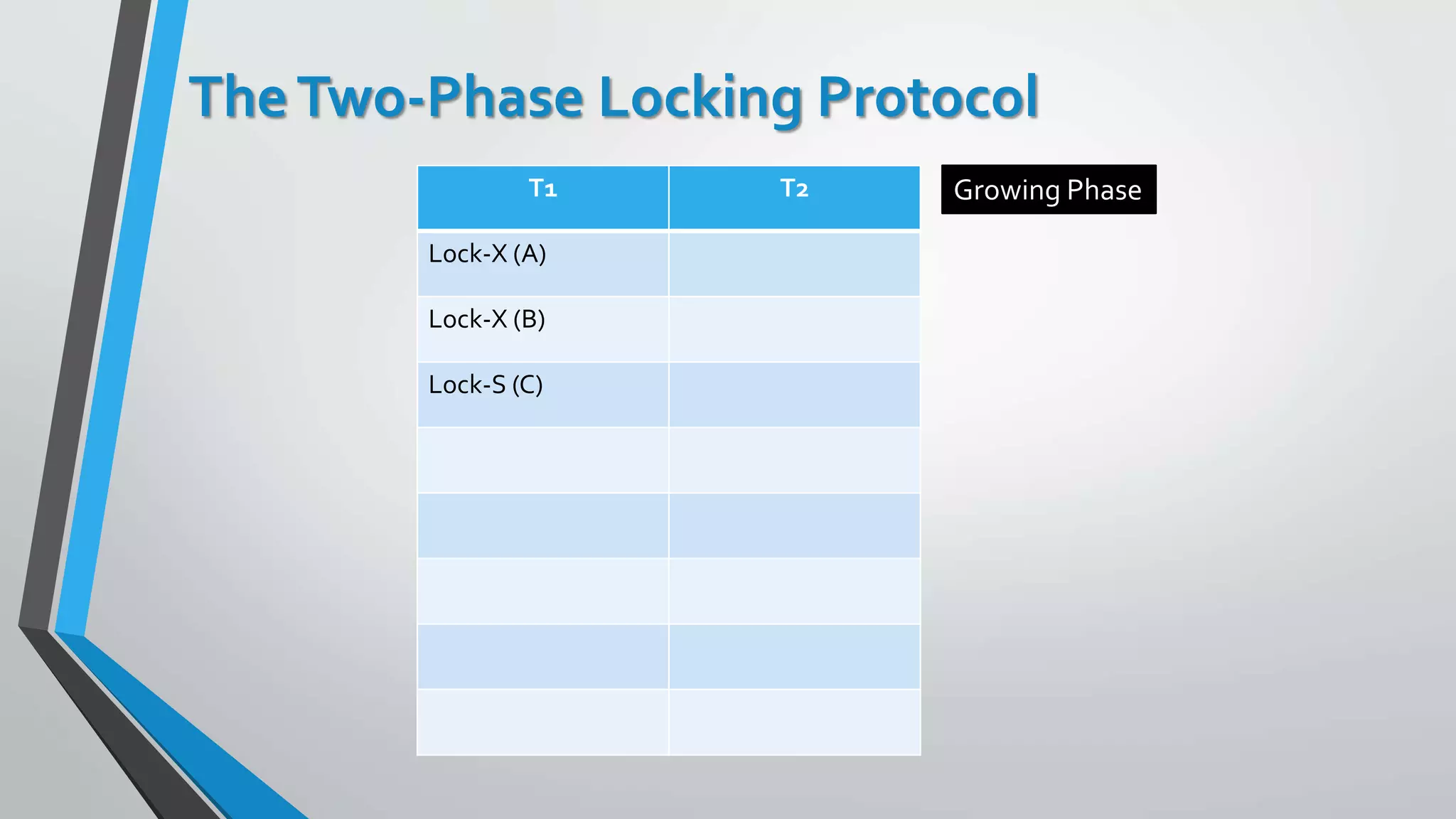
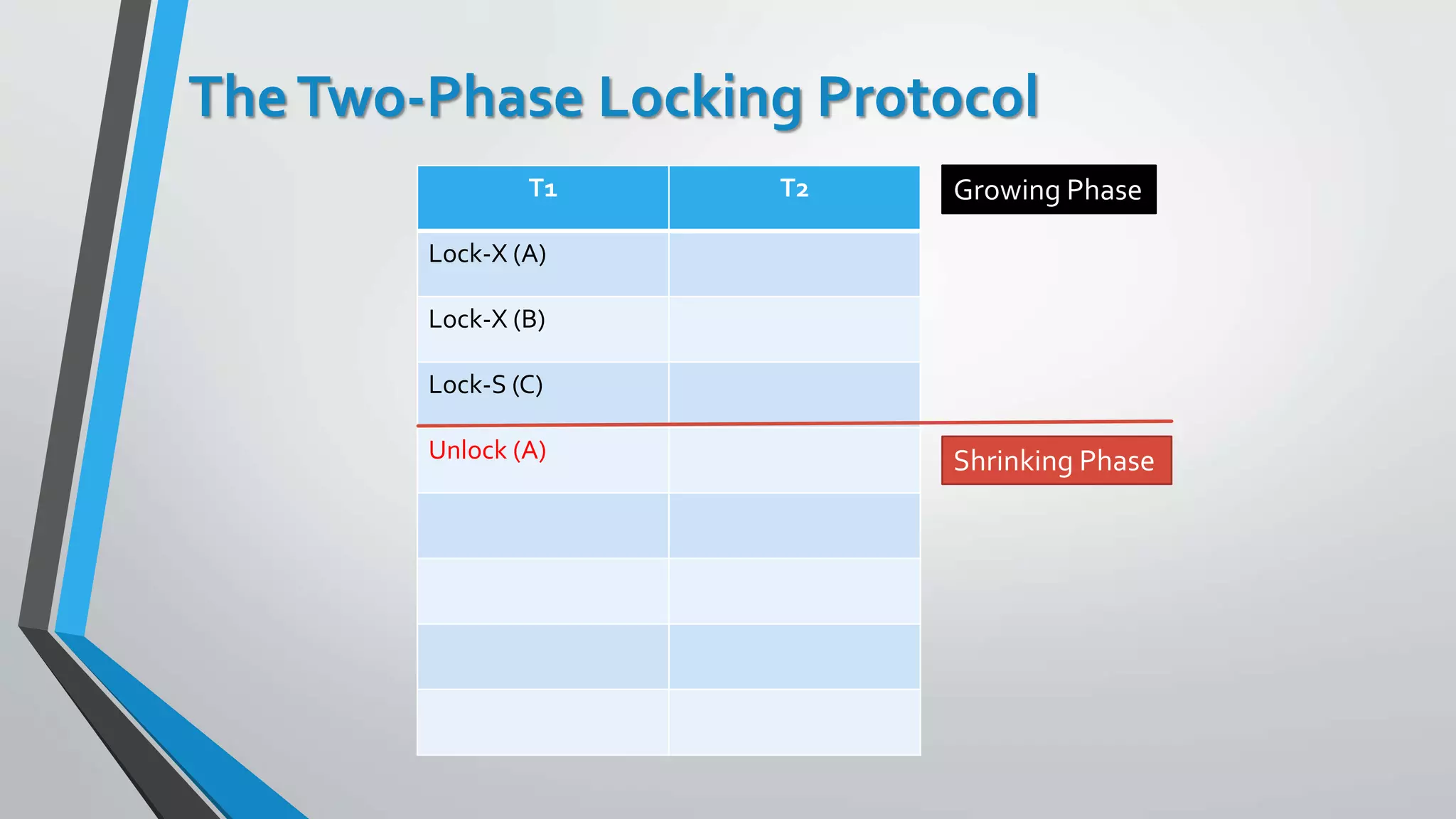
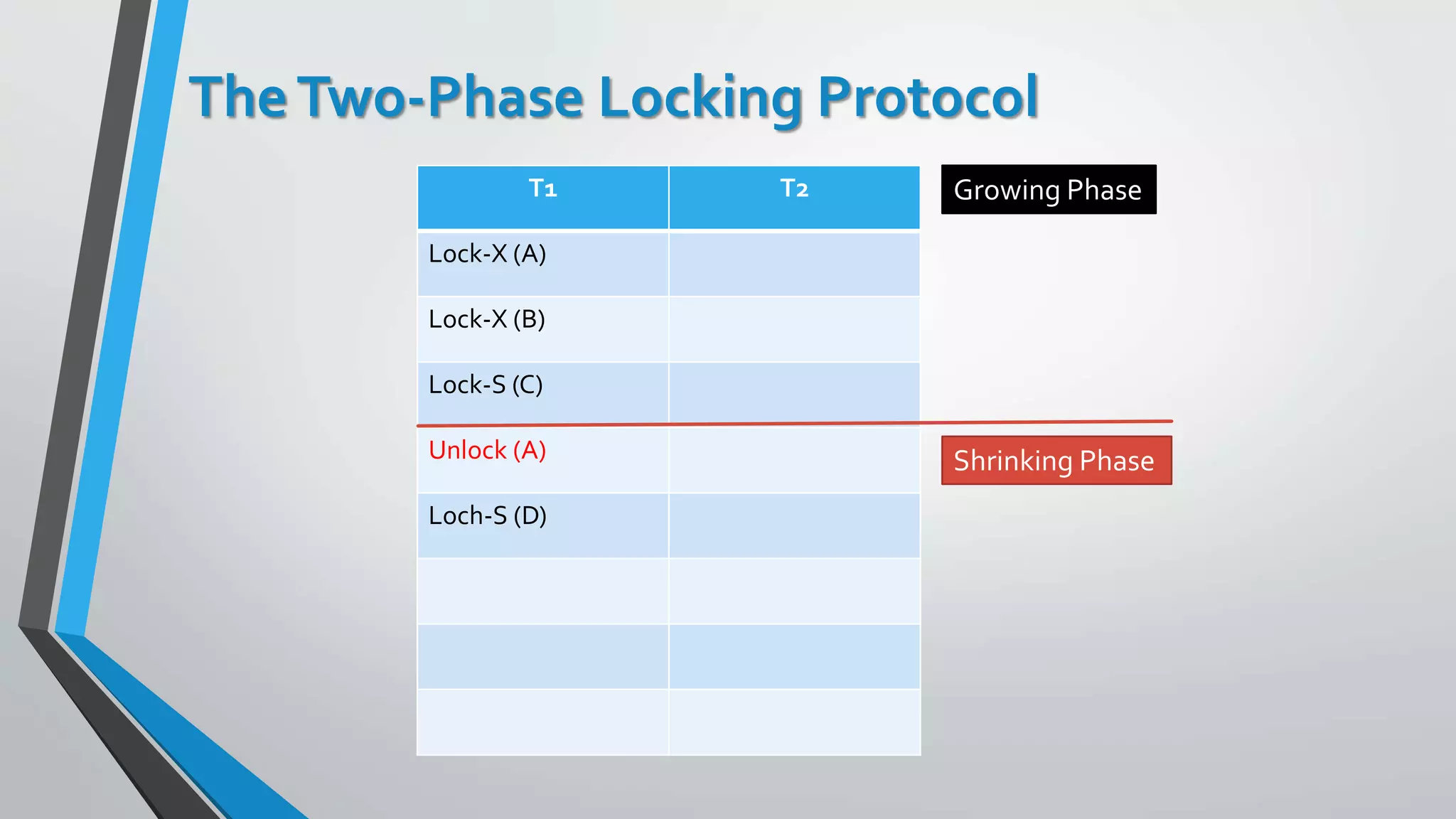
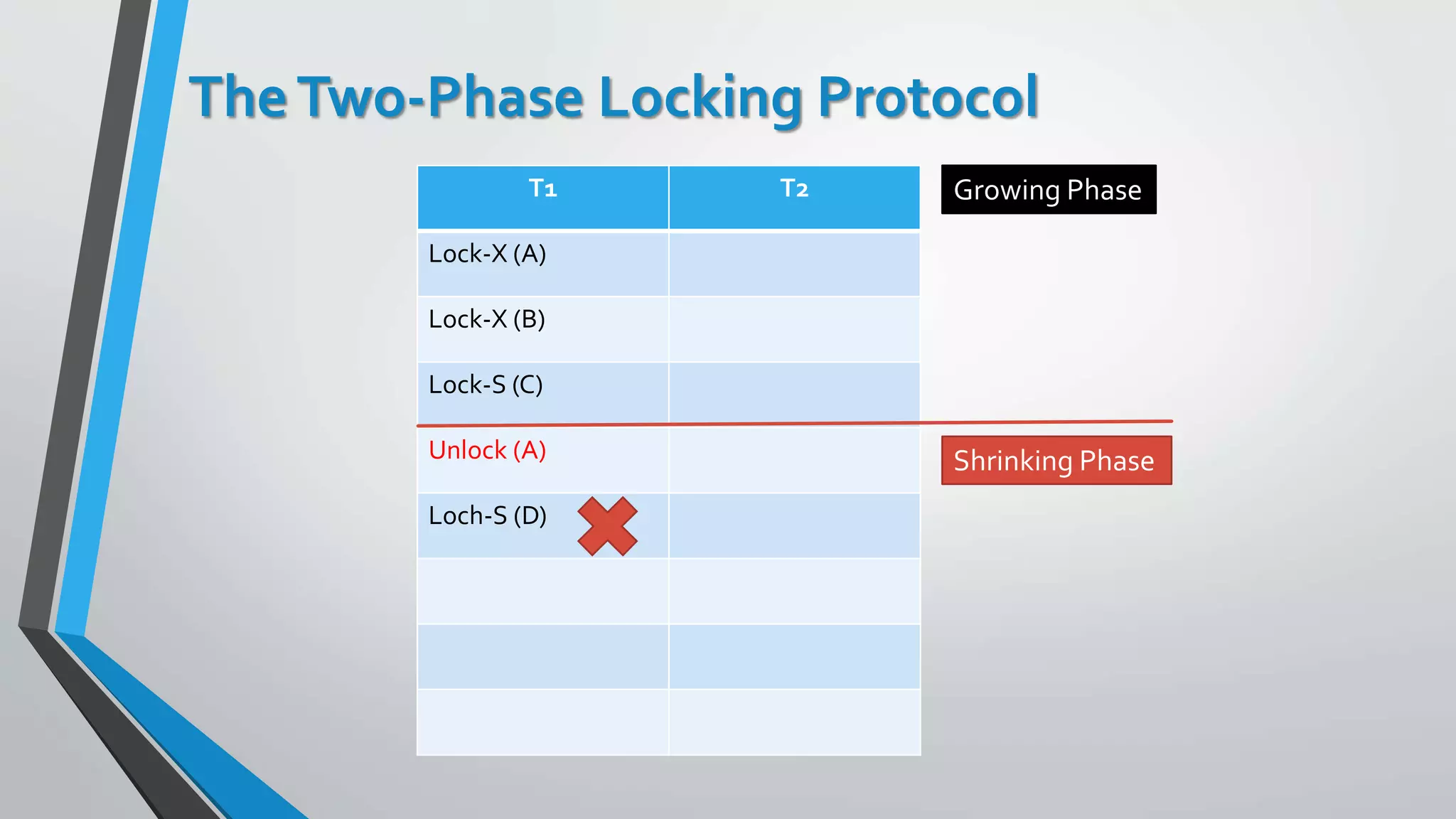
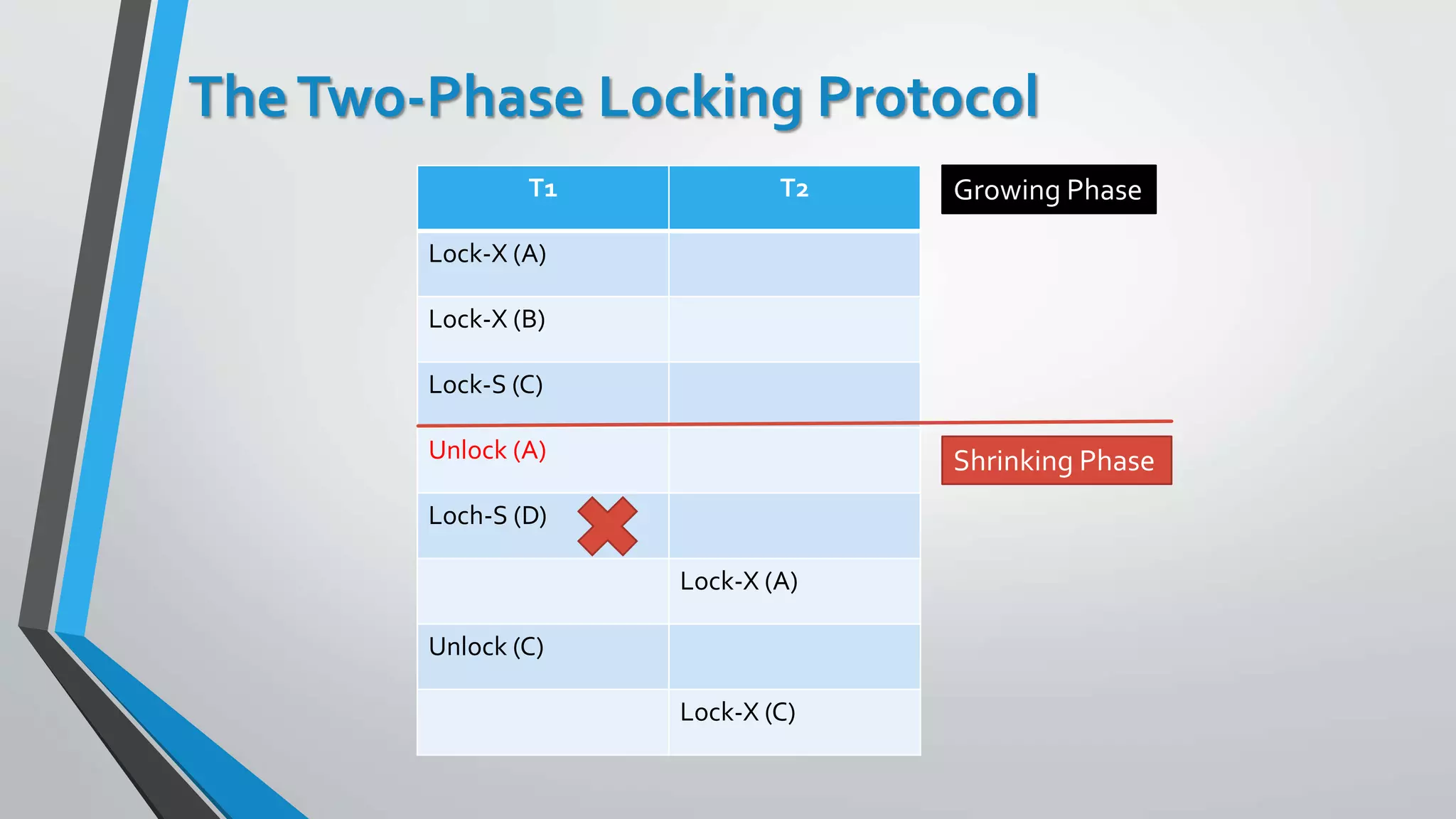
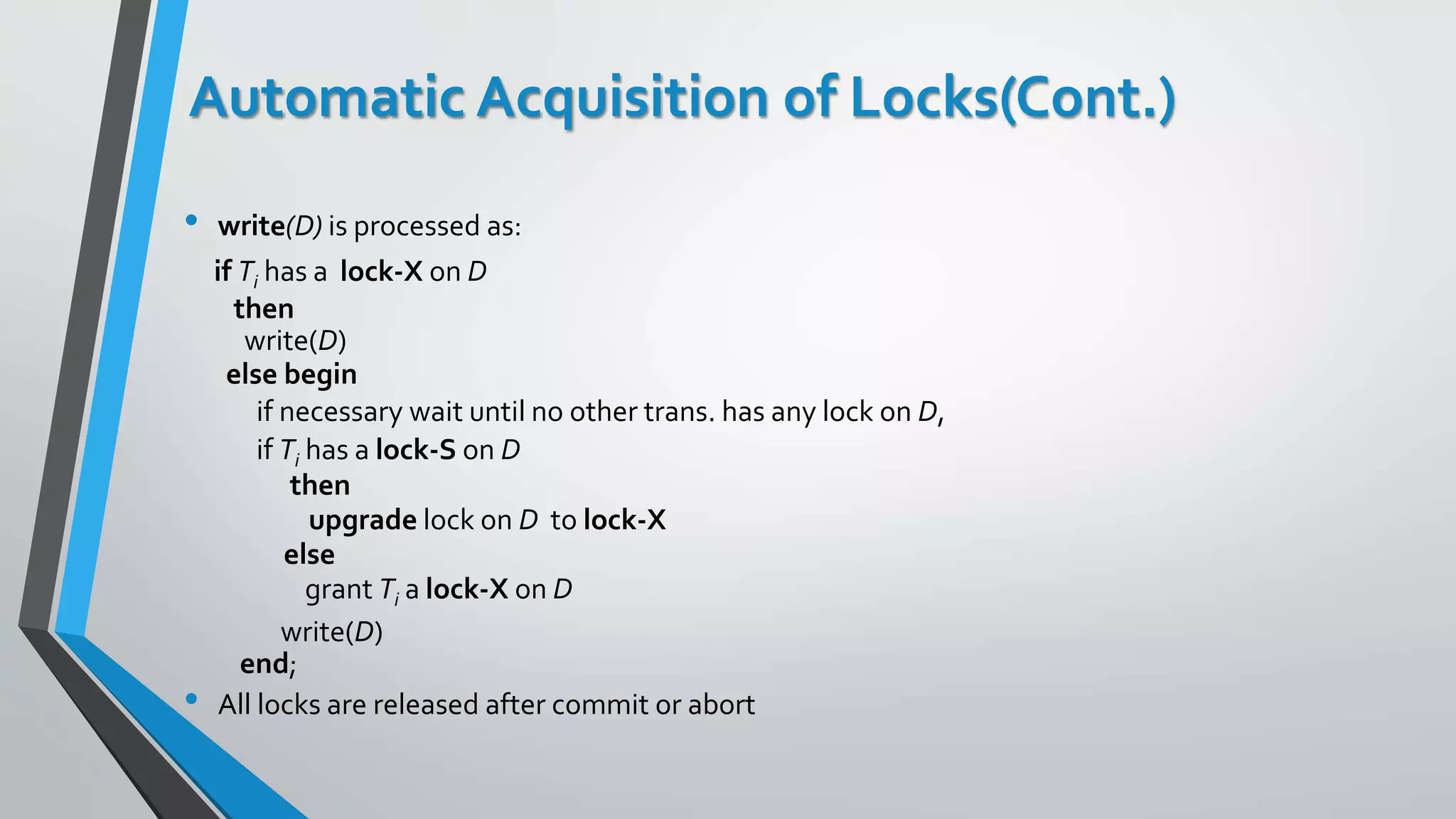
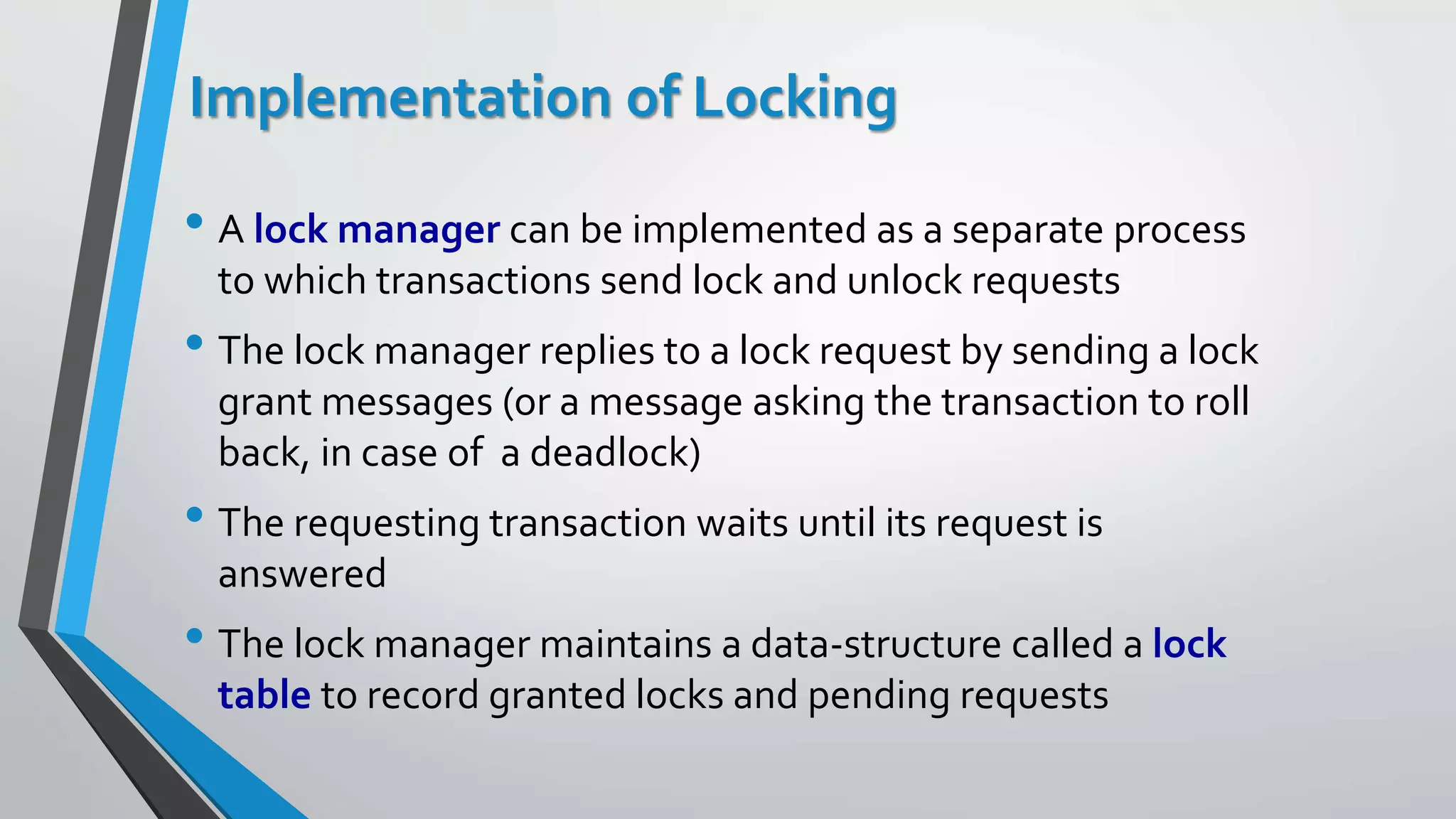
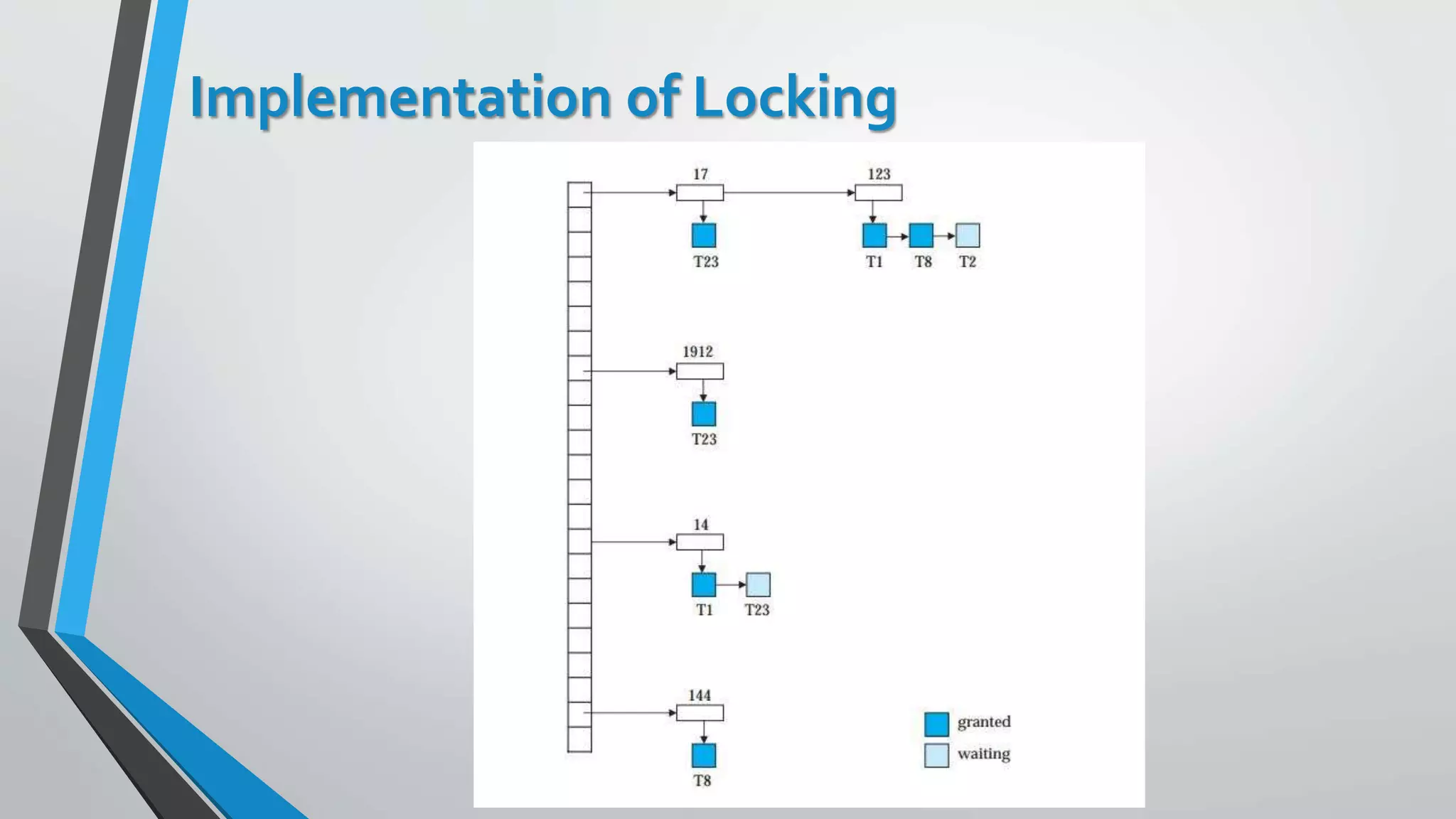
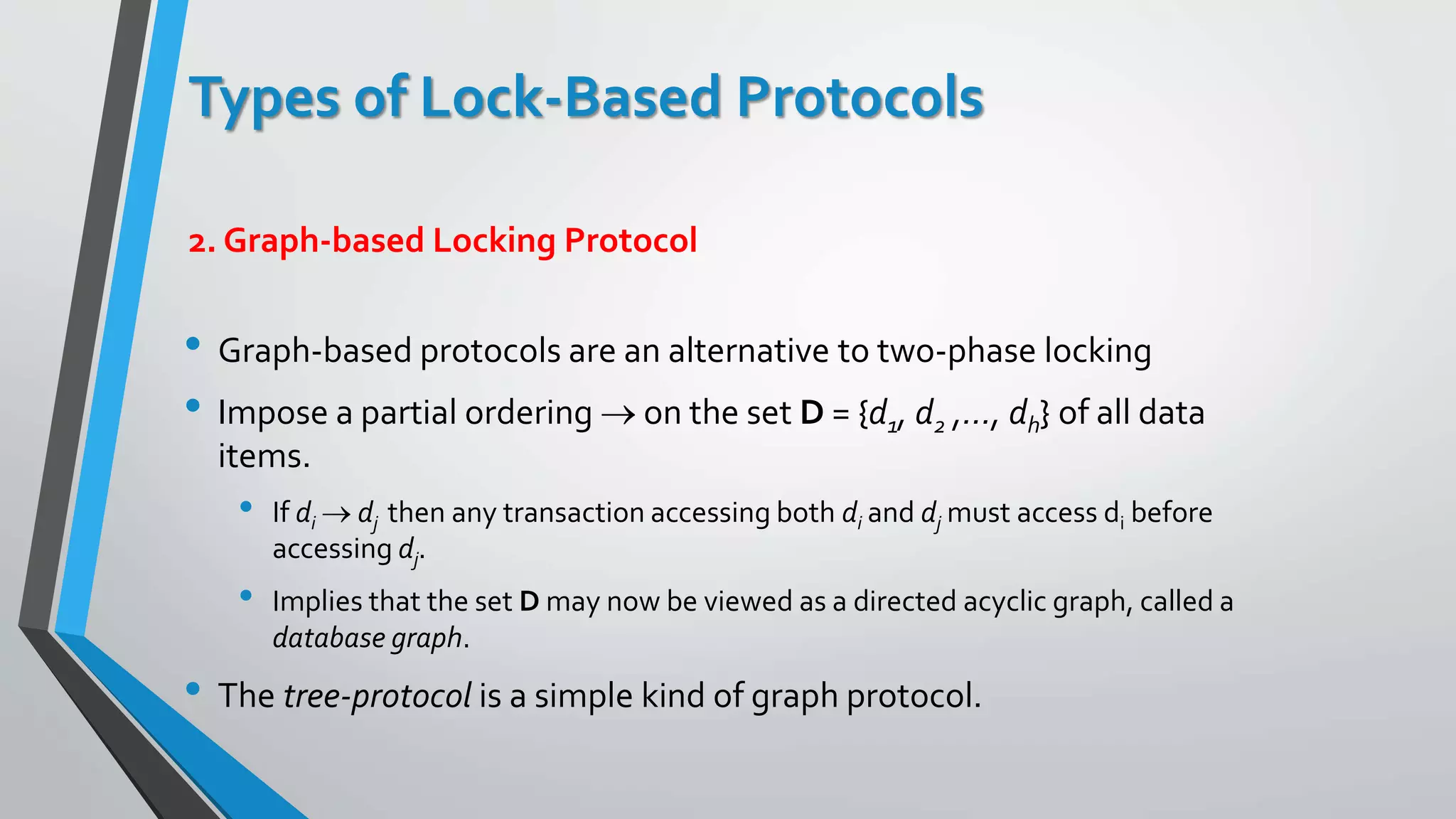
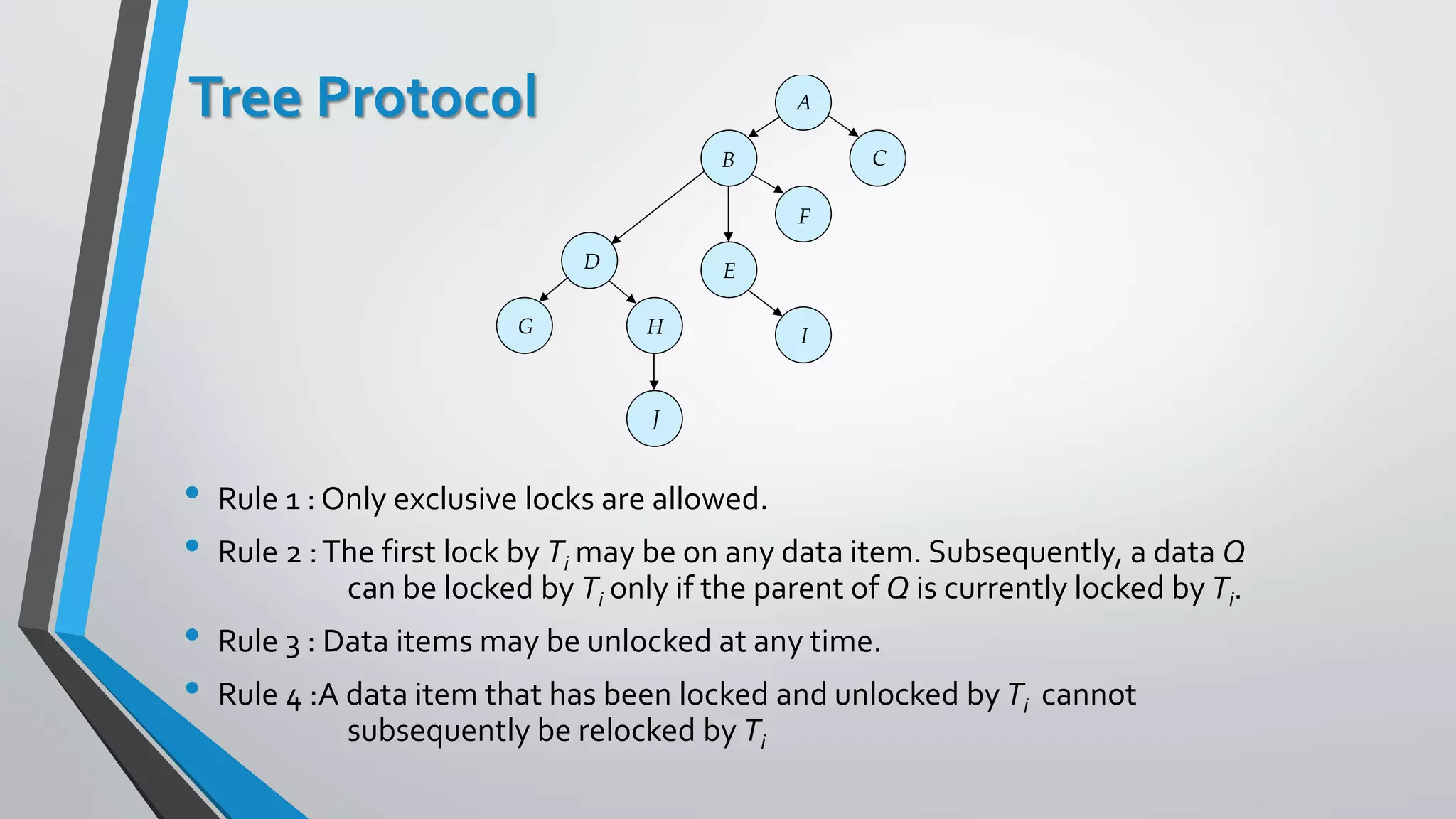
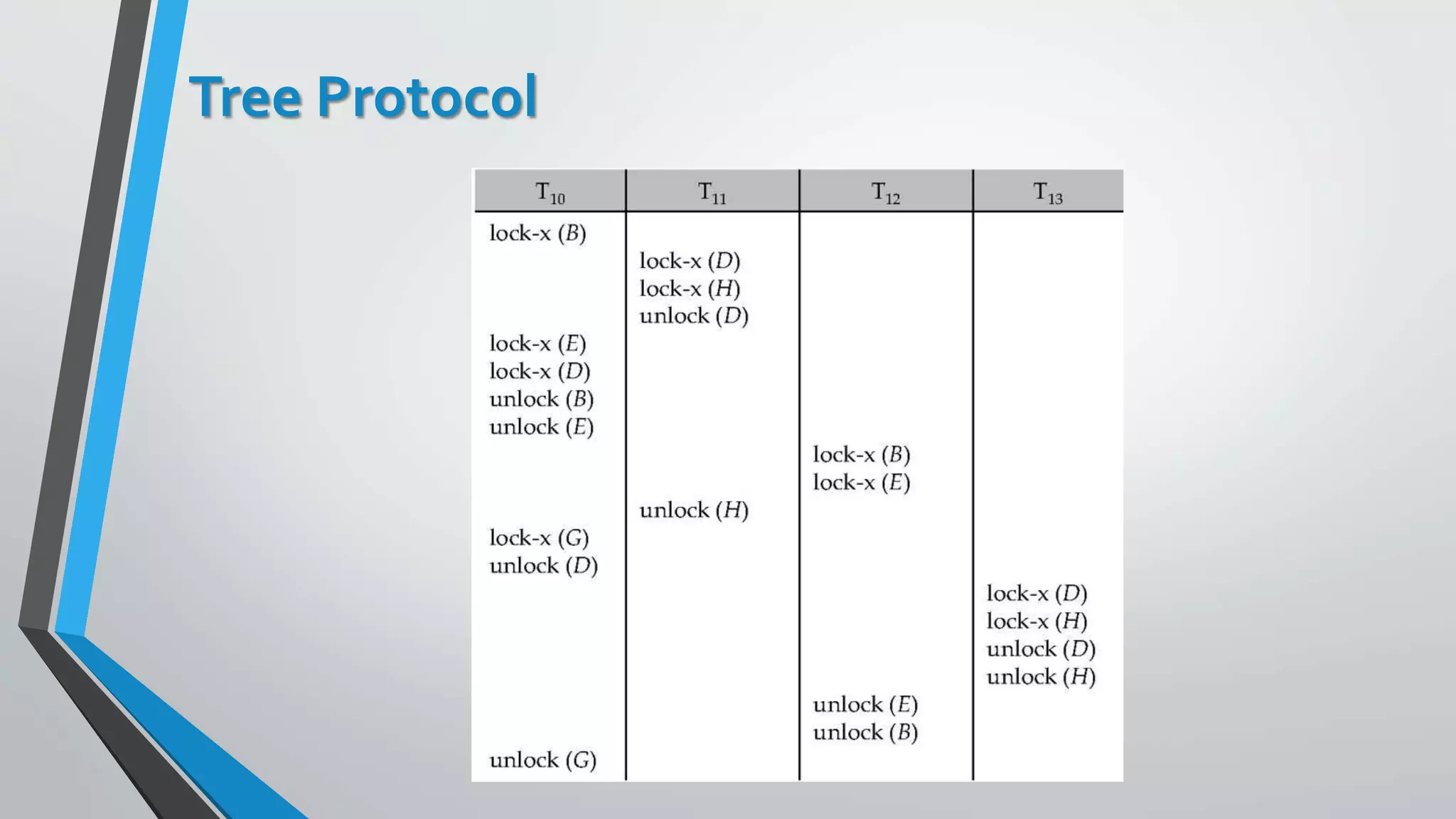
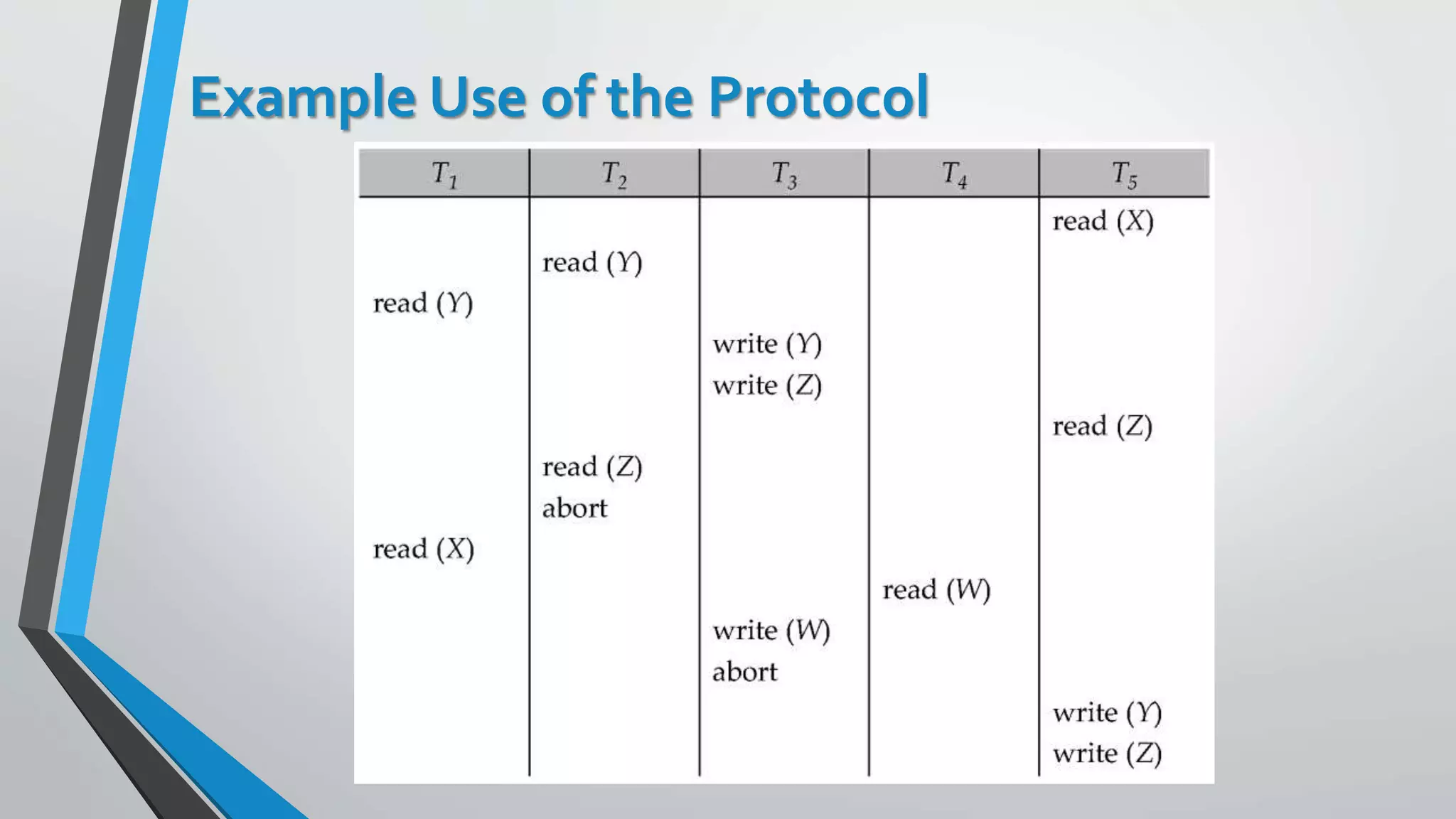
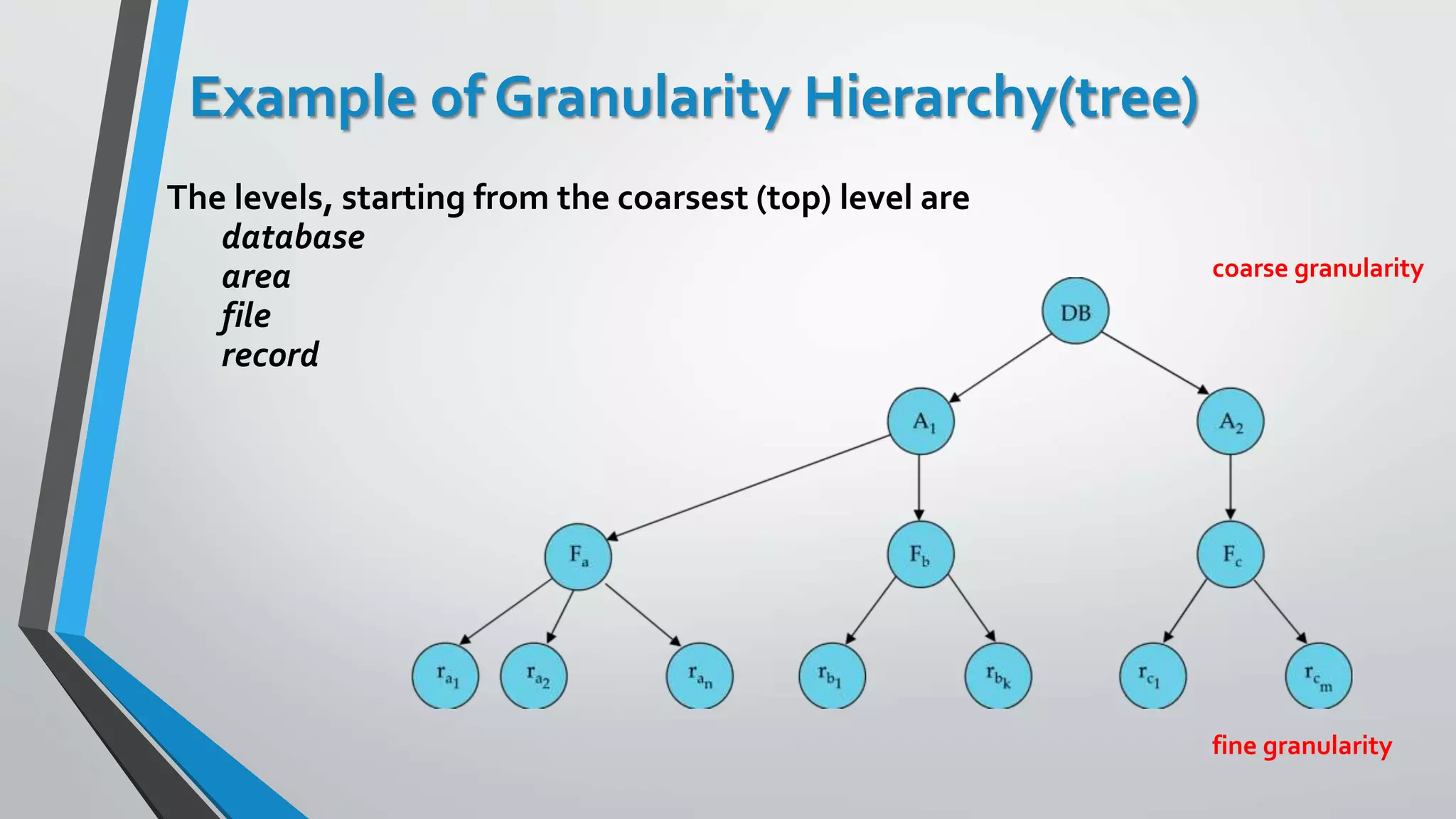
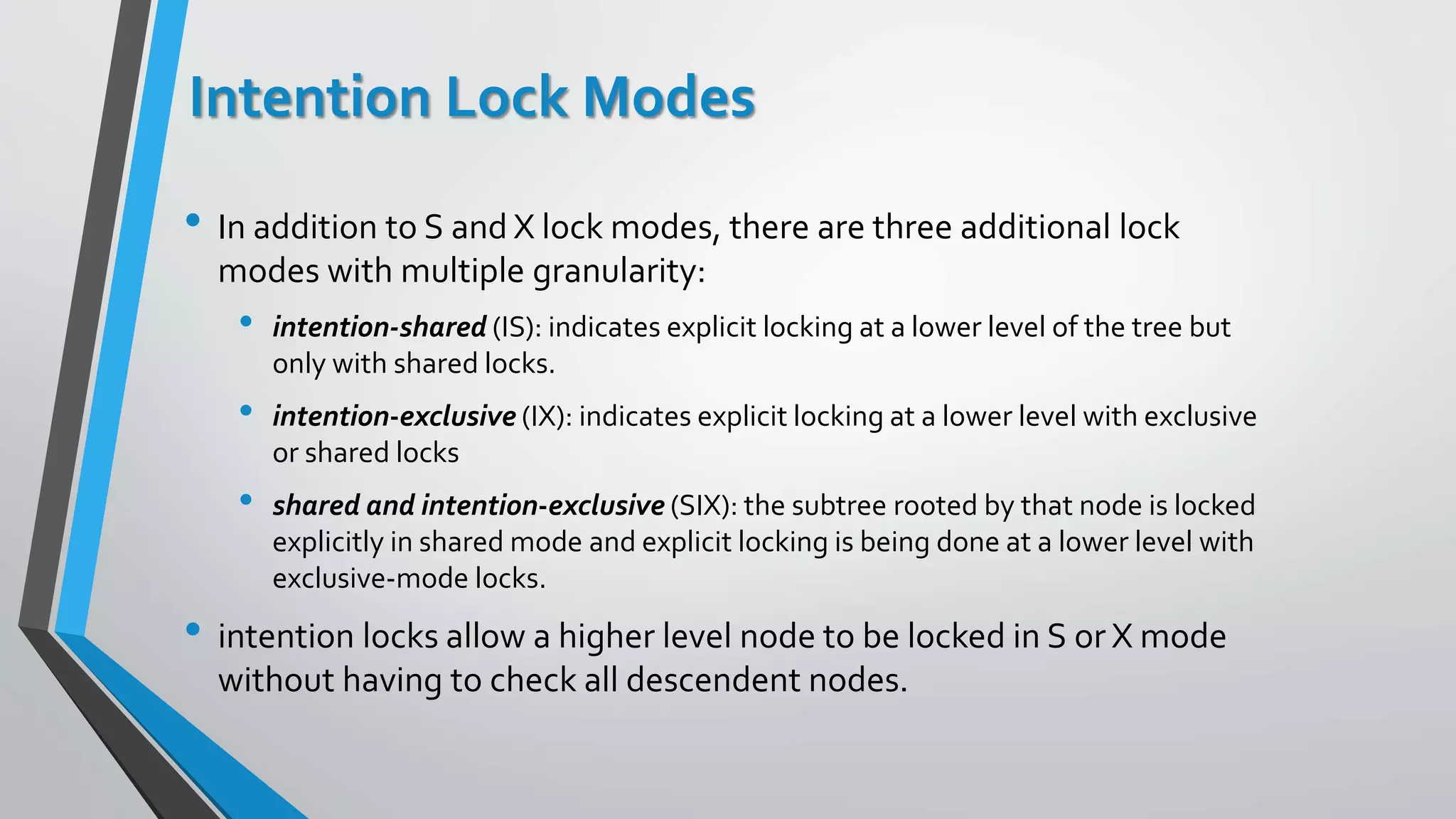
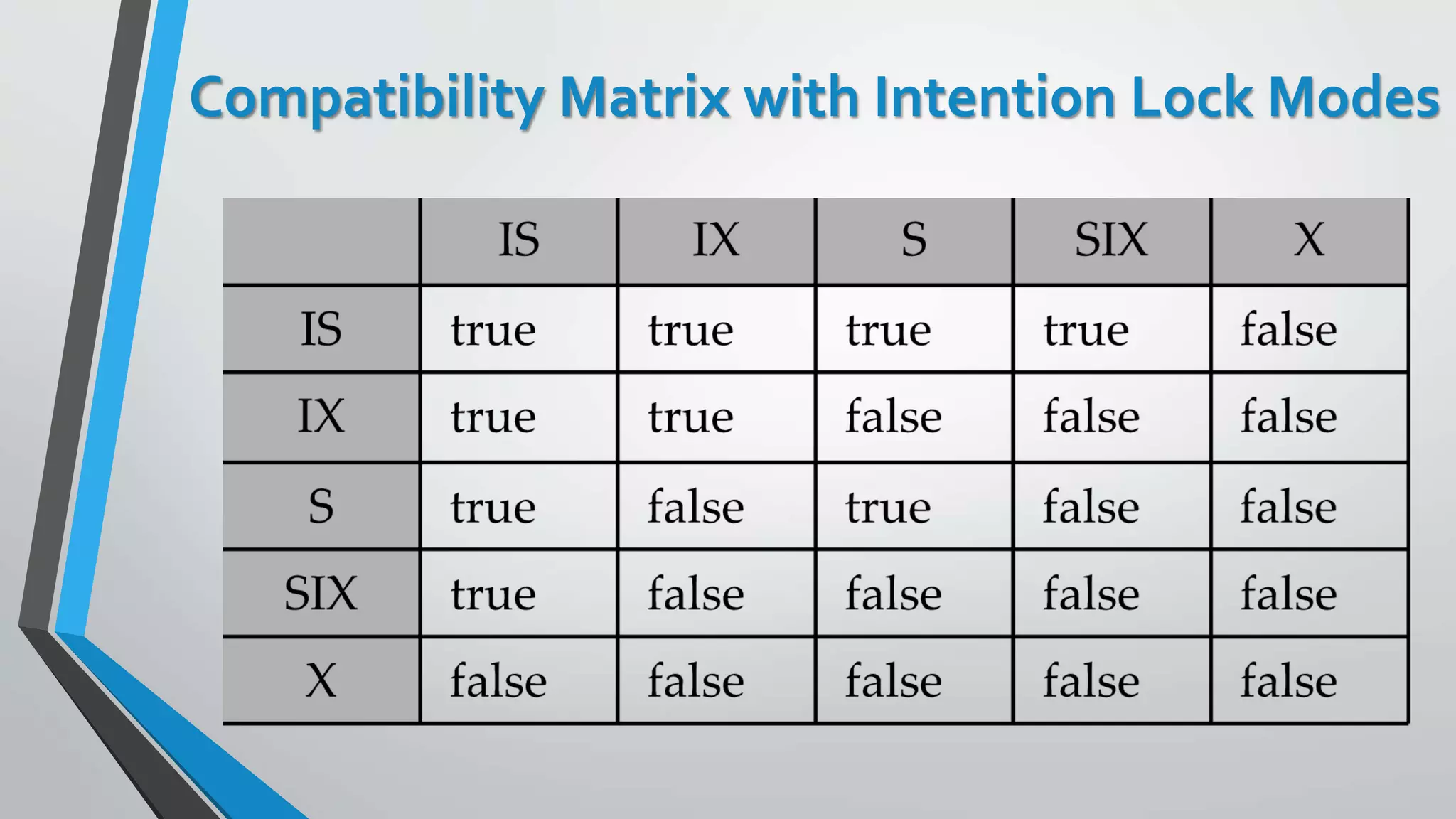
This document outlines different concurrency control protocols used to ensure serializability of transactions in a database. It discusses lock-based protocols like two-phase locking and tree protocols. It also covers timestamp-based protocols that assign timestamps to transactions and validate reads/writes based on timestamp order. Validation-based protocols execute transactions optimistically and validate during a separate validation phase if updates can be committed without violating serializability.