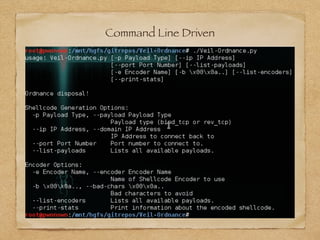
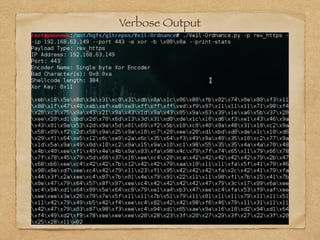
The document discusses shellcode generation methods used in exploits, primarily focusing on the need for a new tool called veil-ordnance that efficiently generates shellcode without reliance on external tools like msfvenom, which can lead to parsing issues. It outlines command line options available in veil-ordnance for different payloads and encoders, and highlights the contribution of Jon Yates in developing these payloads. The author invites feedback and collaboration on encoders and provides contact information for further inquiries.