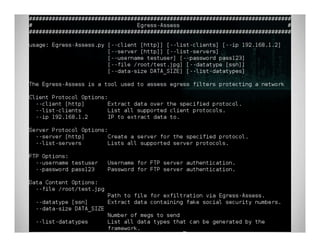
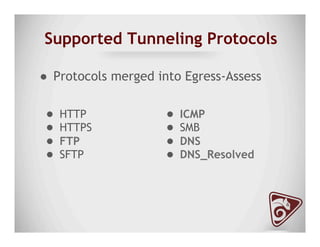
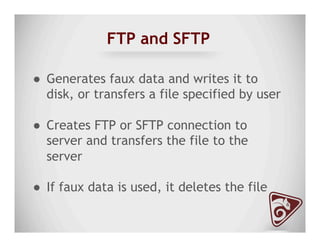
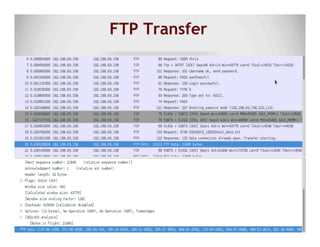
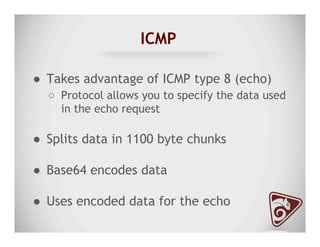
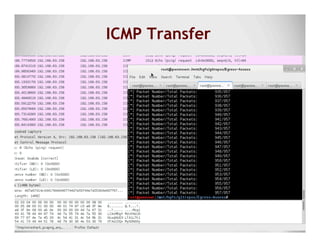
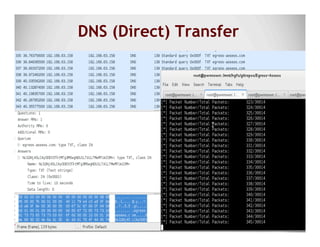
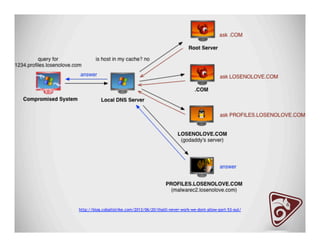
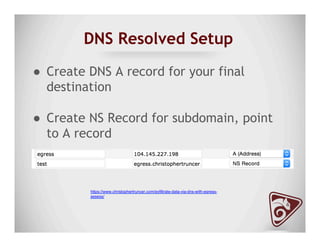
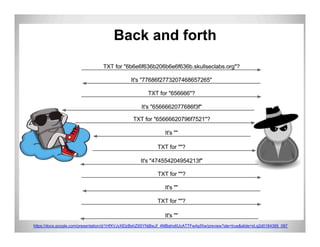
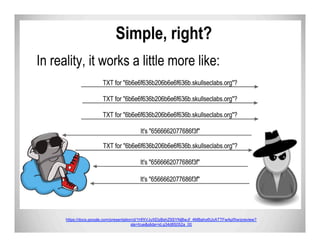
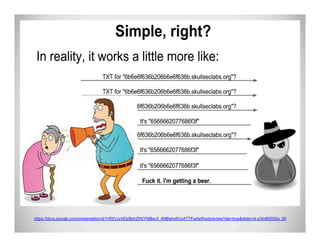
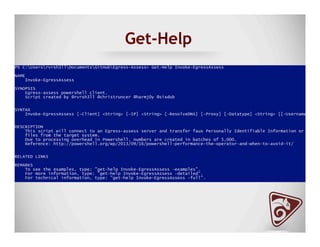
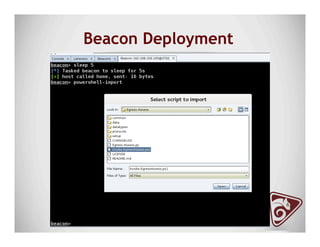
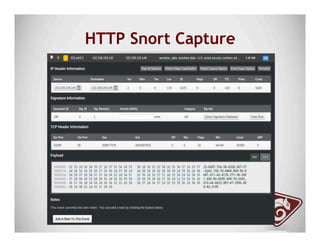
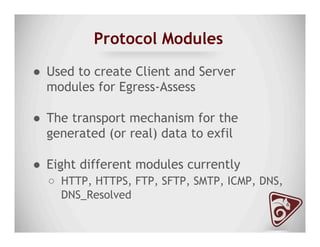
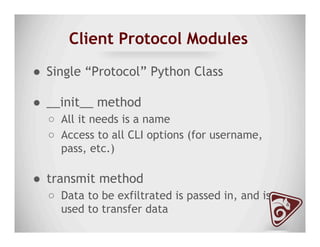
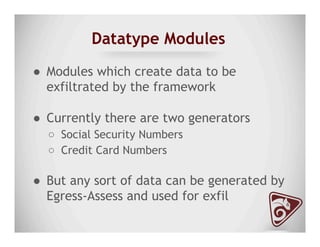
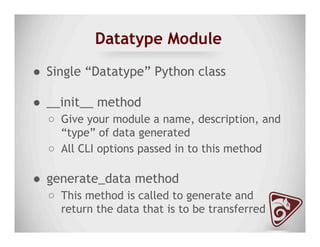
The document discusses data exfiltration techniques and tools developed by Christopher Truncer and Stephan Borosh, focusing on their Egress-Assess framework. It outlines the motivations behind data exfiltration, various tunneling protocols supported, and the project's goals, such as ease of setup and the ability to test blue team detection capabilities. The presentation also includes a discussion on specific case studies, demonstrating various data targets and the importance of simulating real-world attack scenarios to enhance security preparedness.