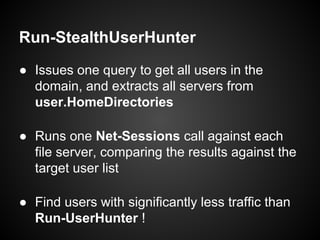
The document discusses Veil-PowerView, a PowerShell framework designed for situational awareness in exploited hosts and networks. It includes various functions that replace traditional 'net' commands, allowing users to gather detailed information about domain users, shares, and machines without dropping binaries to disk. The author highlights its utility for penetration testing, especially in environments where 'net' commands are restricted.