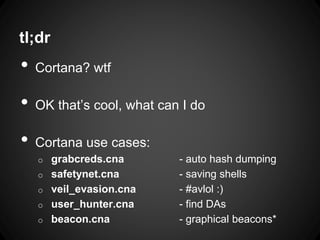
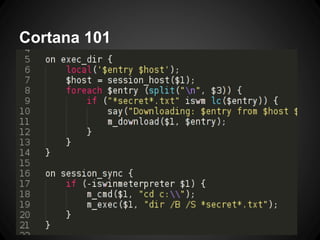
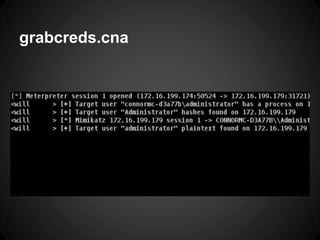
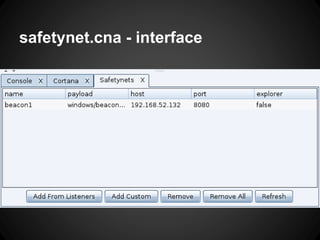
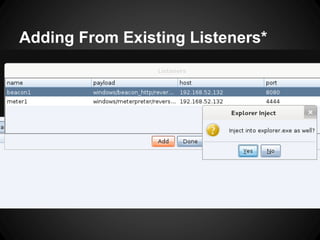
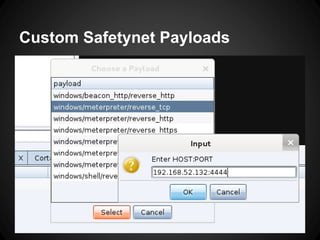
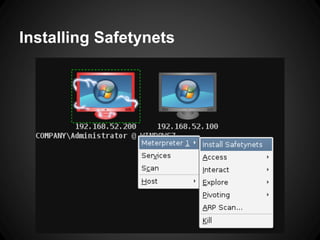
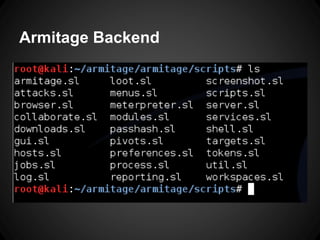
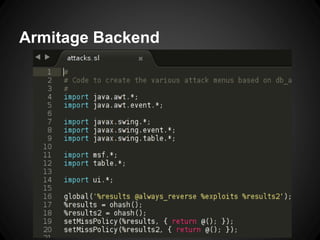
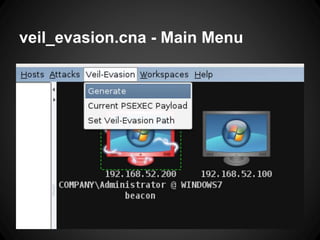
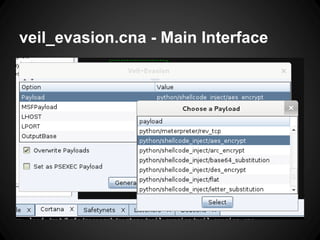
The document outlines the functionalities and use cases of Cortana, an extension for automating tasks in Armitage and Metasploit, which is beneficial for penetration testing. It presents several scripts and modules, such as grabcreds.cna, safetynet.cna, and user_hunter.cna, that automate various tasks related to credential gathering, session management, and user enumeration. The document emphasizes how Cortana can enhance efficiency in pentesting by minimizing repetitive tasks through scripting and user interface customization.



![Sleep 101
• “Sleep is primarily a glue language and was
designed from the ground up to be
embedded in Java applications…[it] brings
the power of Perl to the Java platform.”
• Much of the backend of Armitage is actually
written in Sleep
https://today.java.net/pub/a/today/2005/07/14/sleep.html](https://image.slidesharecdn.com/wieldingacortana-140321164319-phpapp01/85/Wielding-a-cortana-7-320.jpg)
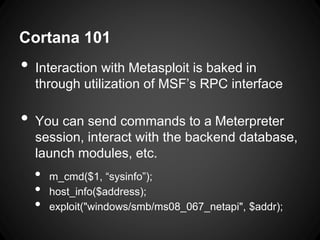








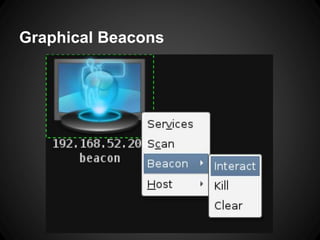







![How Can Cortana Help?
• We can interact fully with the msf database
o @notes = call("db.notes")["notes"];
• We can setup ‘heartbeat’ callbacks to
periodically perform actions
o on heartbeat_5s {…}
• We can modify our gui in useful ways
o filter host_image { …change a host’s gui image …}](https://image.slidesharecdn.com/wieldingacortana-140321164319-phpapp01/85/Wielding-a-cortana-40-320.jpg)