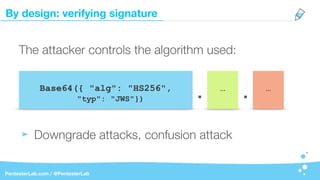
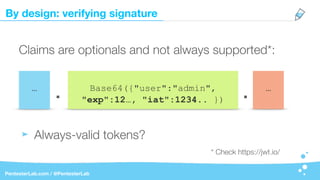
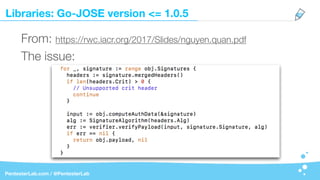
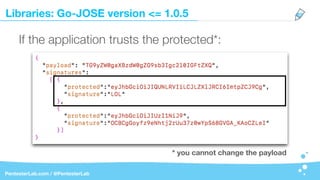
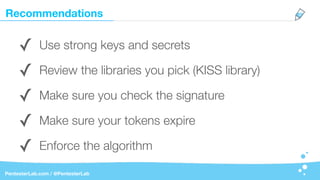
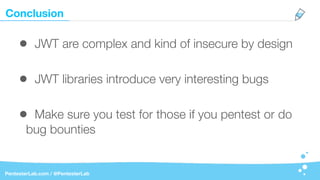
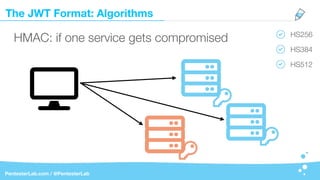
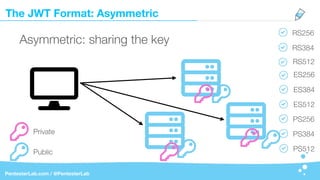
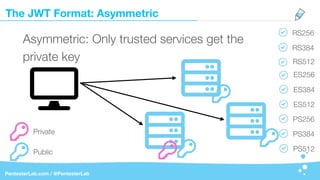
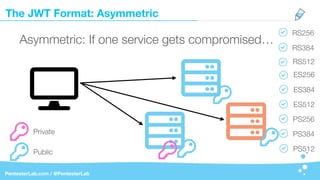
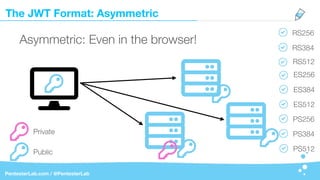
The document discusses the insecurities associated with JSON Web Tokens (JWT), highlighting their structure, usage, and potential vulnerabilities inherent in various libraries. It emphasizes the importance of strong keys, proper signature verification, and the need for tokens to expire, while also addressing specific attack strategies that exploit JWT implementations. Overall, it concludes that JWTs are complex and can pose security risks if not properly managed.









![The JWT Format: payload
PentesterLab.com / @PentesterLab
…
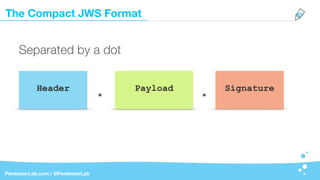
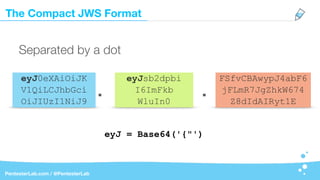
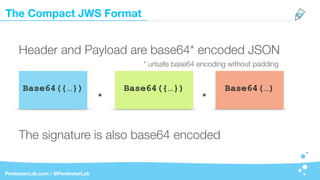
The payload may contain literally anything:
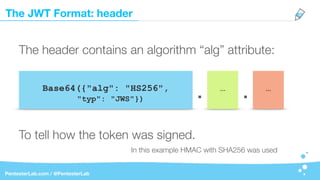
Base64({"user":"admin",
"roles": ["adm","users"]}). . …](https://image.slidesharecdn.com/jwt-insecuritywide-180324001930/85/Jwt-insecurity-23-320.jpg)