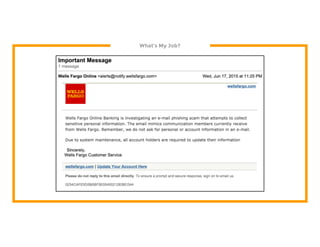
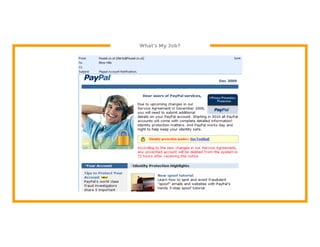
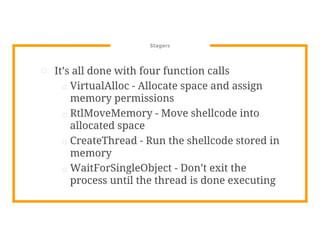
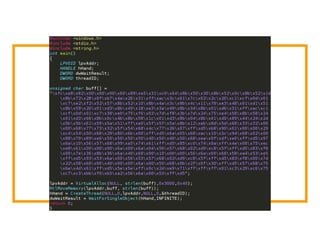
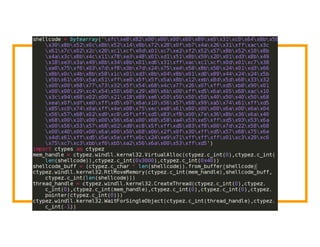
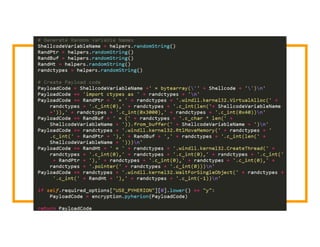
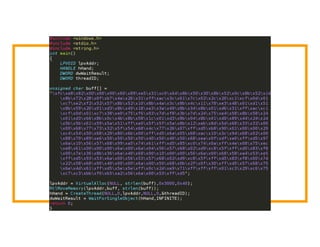
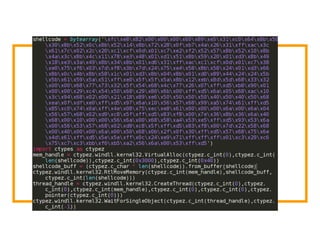
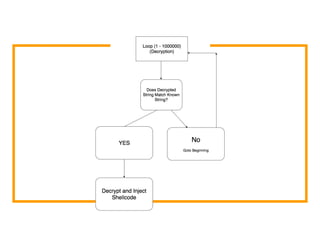
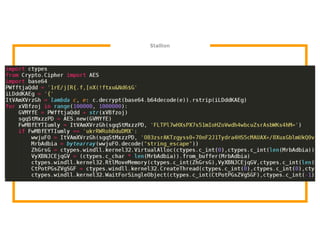
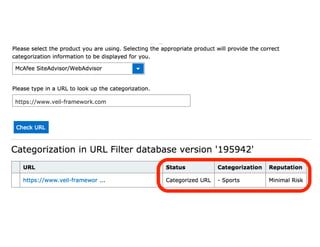
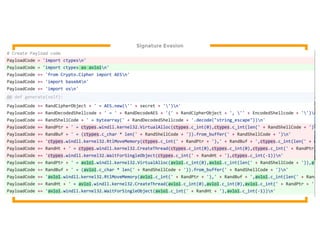
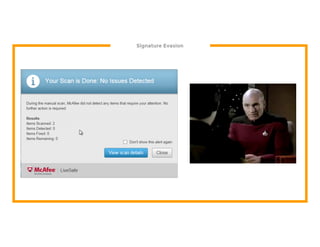
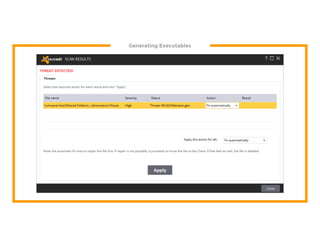
The document discusses the development of the Veil framework by penetration testers to automate the bypassing of antivirus protections for testing security systems. It highlights the importance of using non-standard programming languages like Python to evade detection and outlines the framework's methods, including shellcode injection techniques. The presentation emphasizes the need for organizations to test their security solutions effectively and adapt as antivirus detection evolves.