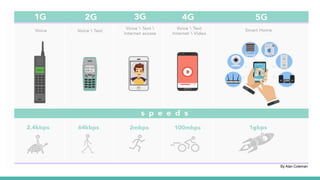
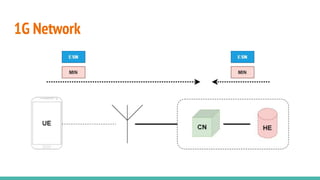
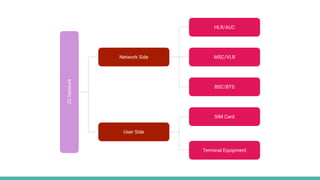
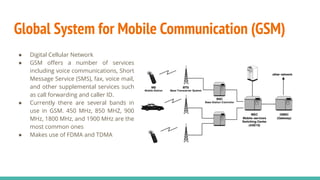
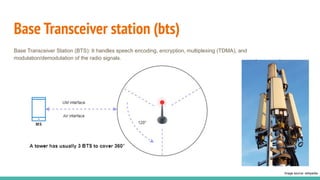
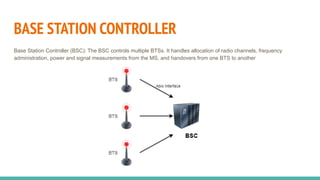
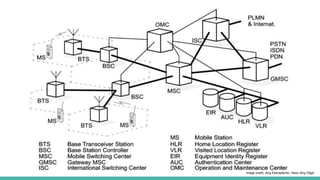
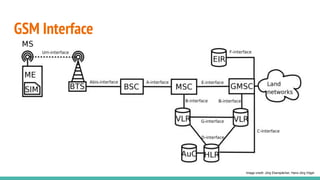
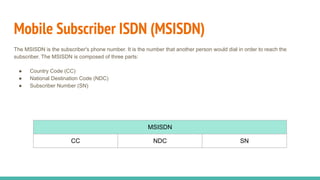
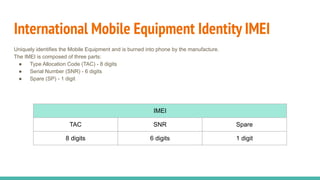
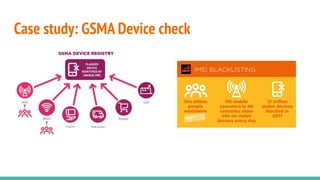
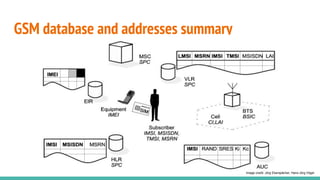
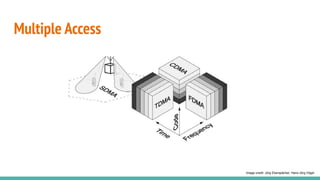
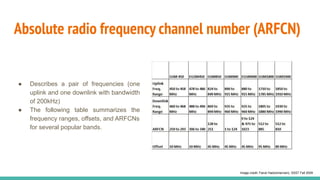
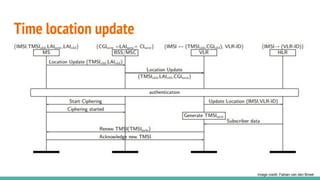
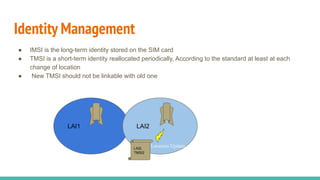
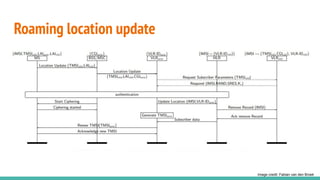
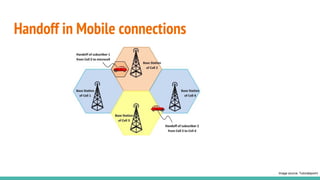
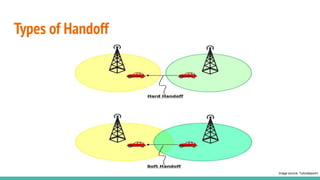
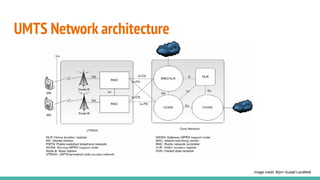
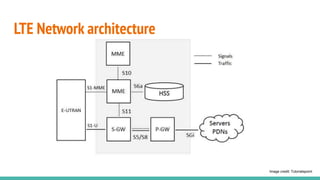
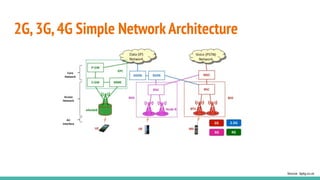
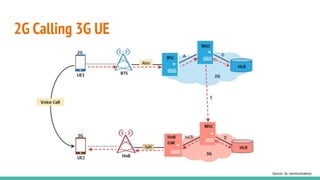
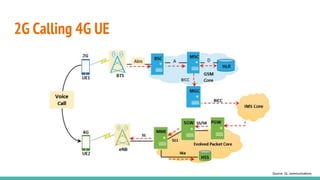
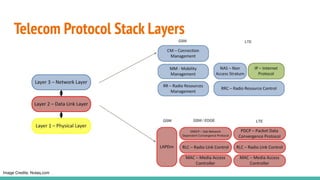
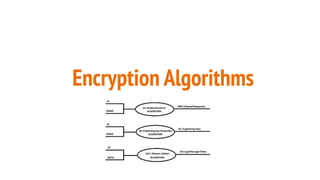
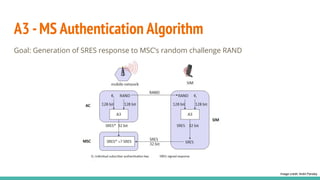
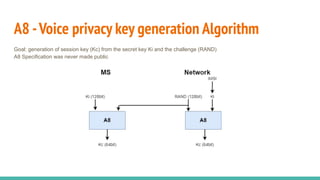
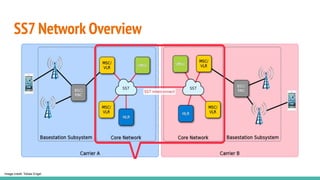
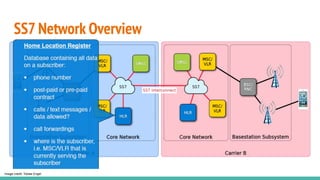
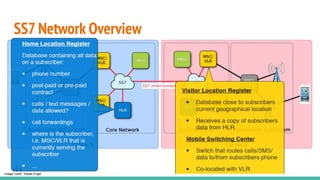
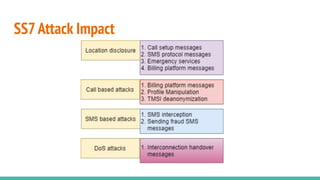
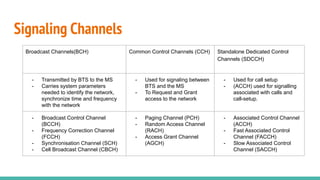
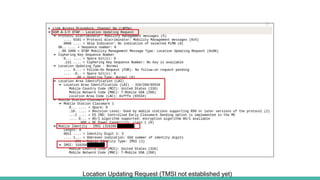
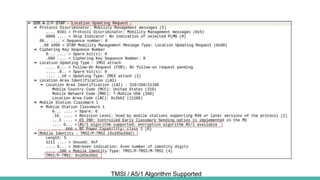
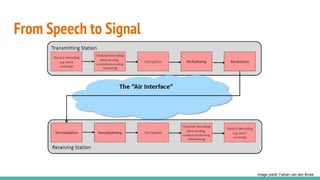
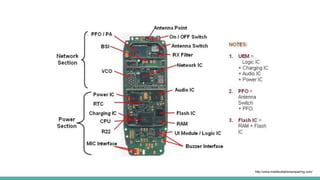
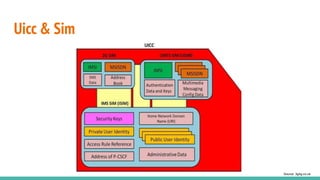
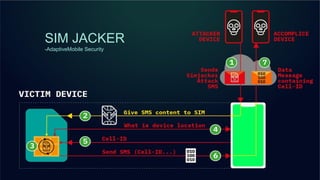
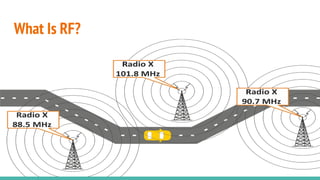
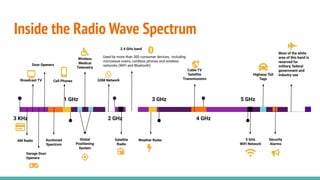
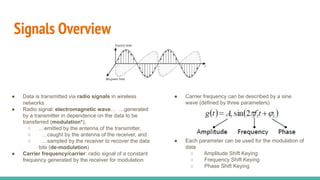
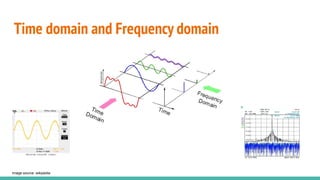
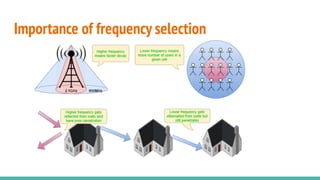
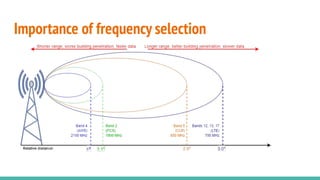
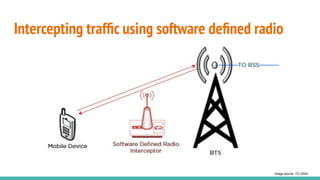
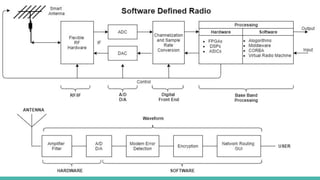
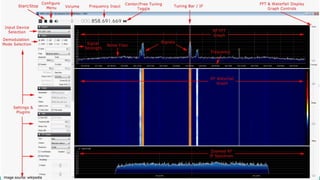
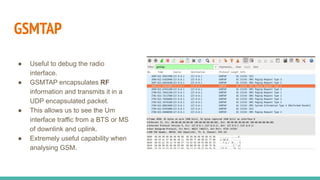
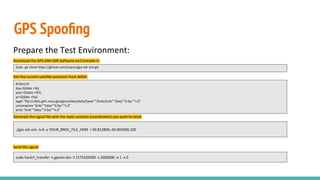
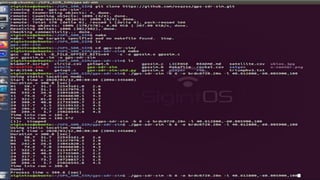
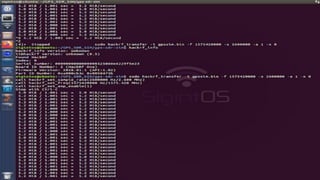
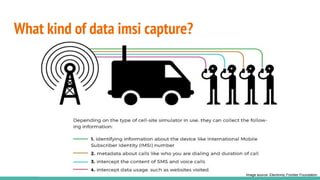
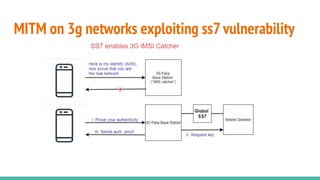
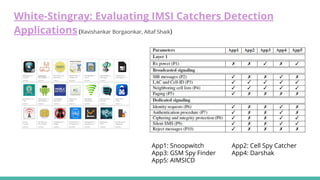
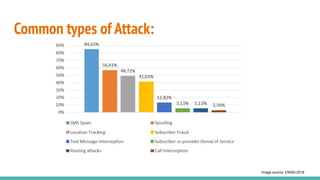
The document outlines a workshop on telecom security featuring experts Harshit Agrawal and Himanshu Mehta, discussing topics like GSM architecture, encryption algorithms, and security threats. The workshop covers the importance of mobile network security, technical details about telecommunications systems, and various vulnerabilities including IMSI catching and SIM cloning. It emphasizes the continuous evolution of security measures in telecom generations while acknowledging that threats persist as researchers and attackers adapt.

![/Speaker/Harshit/> whoami
USER INFORMATION
---------------------------------------------------
Harshit Agrawal
RF and Telecom Security Researcher
---------------------------------------------------
Primary Research area includes
RF Security, Telecom Security,
and IOT Security
Speaker at conferences like RSAC USA,
HITBSecConf Amsterdam, Cyberweek UAE
----------------------------------------------------
Twitter: @harshitnic
Email: harshit[dot]nic[at]gmail[dot]com
LinkedIn: https://linkedin.com/in/harshitnic](https://image.slidesharecdn.com/cisoharshithimanshuworkshoptelecom-201201093426/85/Telecom-Security-2-320.jpg)