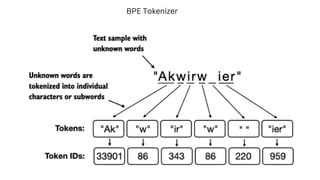
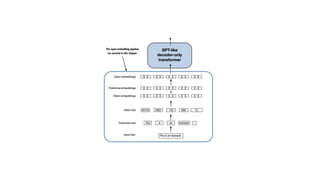
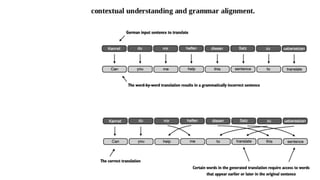
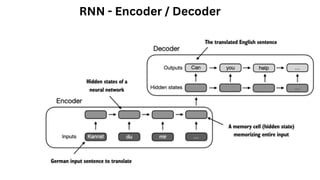
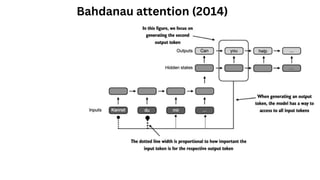
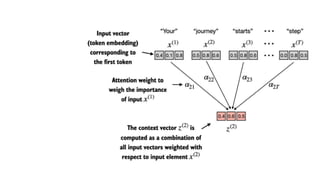
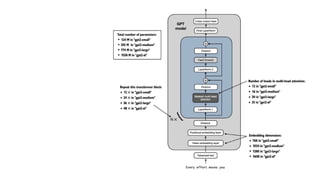
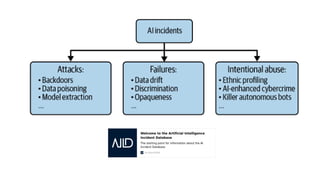
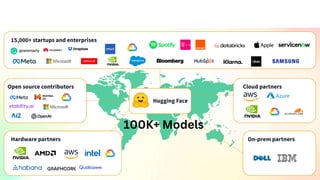
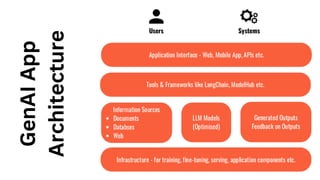
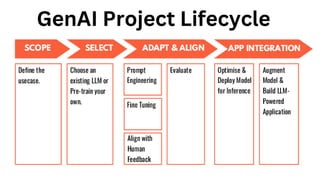
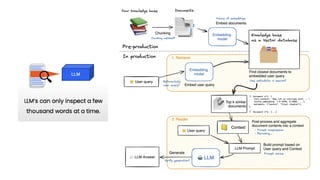
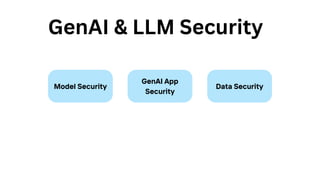
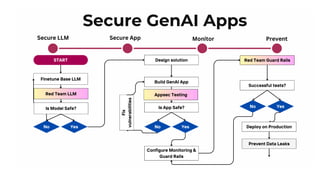
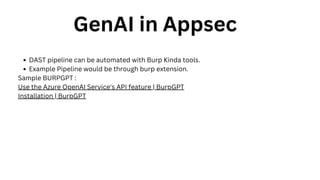
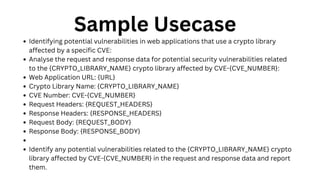
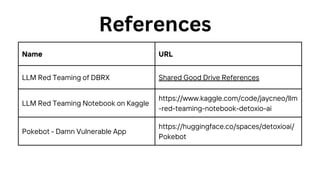
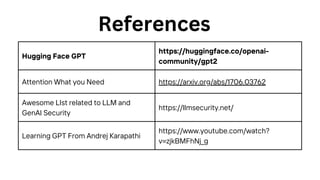
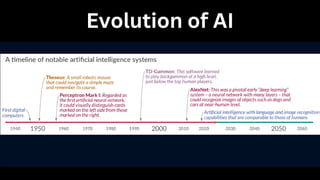
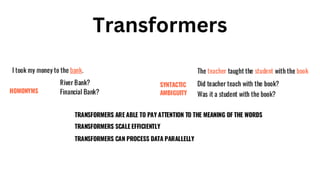
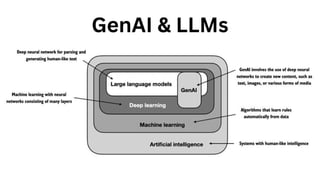
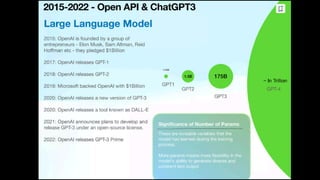
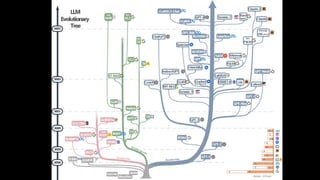
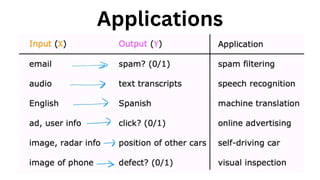
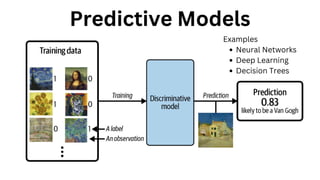
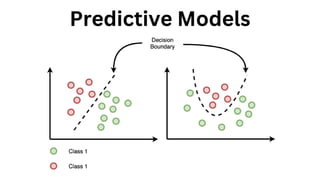
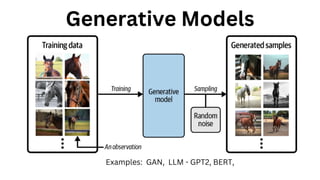
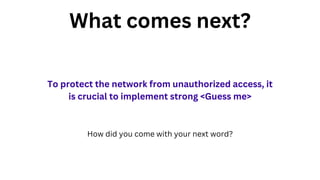
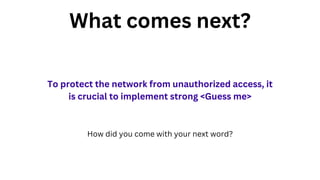
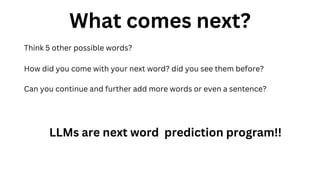
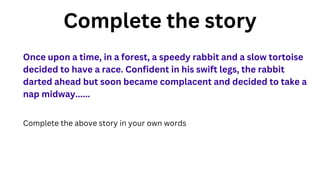
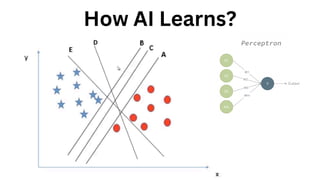
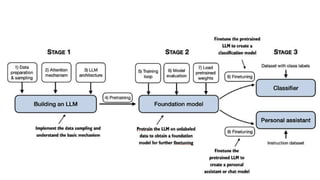
The document outlines an agenda for a hands-on workshop focused on generative AI (GenAI) and security. Topics include understanding GenAI fundamentals, architectures of large language models (LLMs), and practical sessions on penetration testing and securing GenAI applications. The workshop aims to enhance knowledge in AI-related security measures and vulnerabilities.










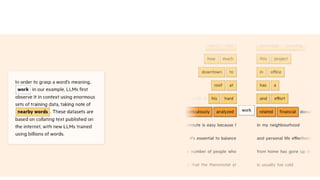
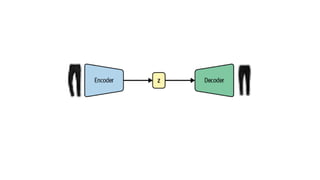
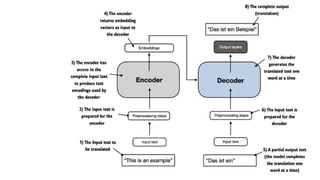
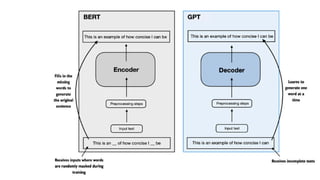


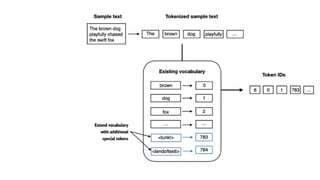
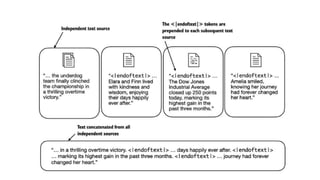
![[BOS] (beginning of sequence): This token marks the start of a text. It
signifies to the LLM where a piece of content begins.
[EOS] (end of sequence): This token is positioned at the end of a text,
and is especially useful when concatenating multiple unrelated texts,
similar to <|endoftext|>. For instance, when combining two different
Wikipedia articles or books, the [EOS] token indicates where one article
ends and the next one begins.
[PAD] (padding): When training LLMs with batch sizes larger than one,](https://image.slidesharecdn.com/genaiworkshop-240717060935-474126c7/85/Finetuning-GenAI-For-Hacking-and-Defending-41-320.jpg)