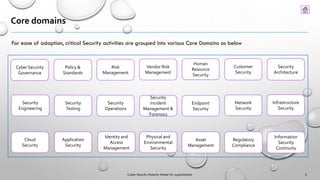
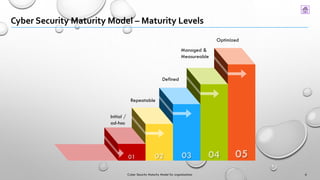
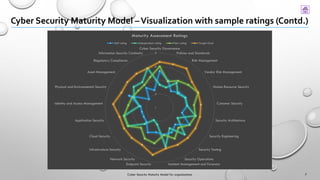
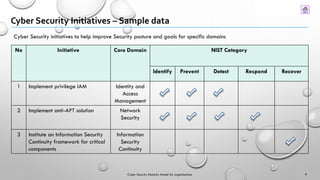
This document presents a Cyber Security Maturity Model (v1.0) designed to help organizations assess and improve their cybersecurity posture by utilizing established frameworks such as NIST and ISO standards. The model consists of five maturity levels that organizations can self-assess against various core domains of cybersecurity, with recommendations for enhancements and initiatives tailored to specific needs. Feedback on the model is encouraged for future revisions, and contact information for contributors is provided.