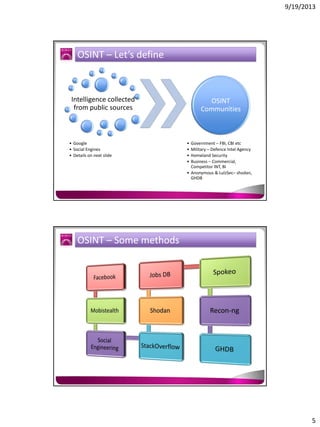
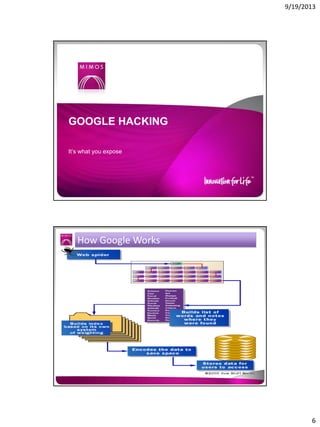
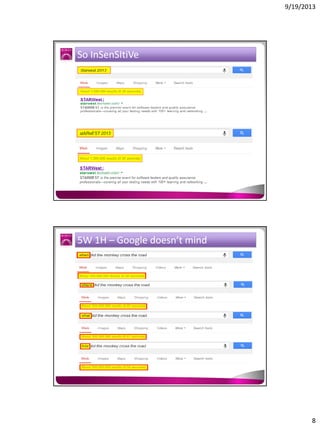
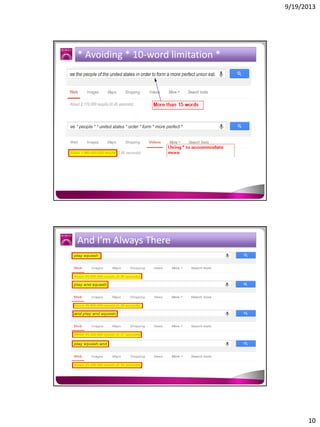
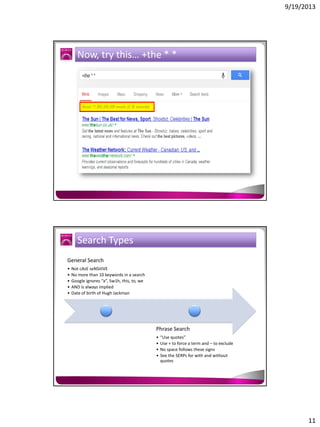
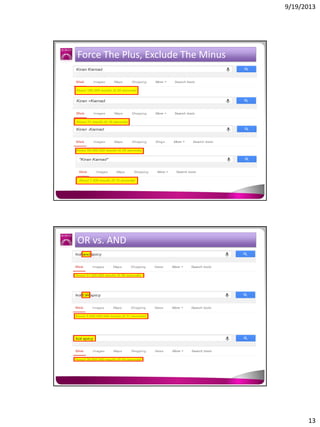
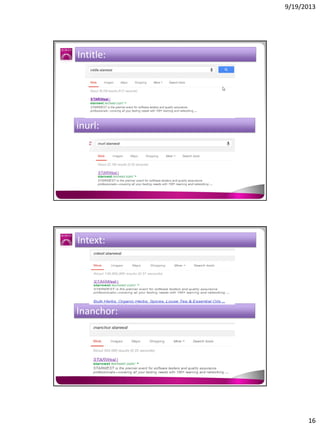
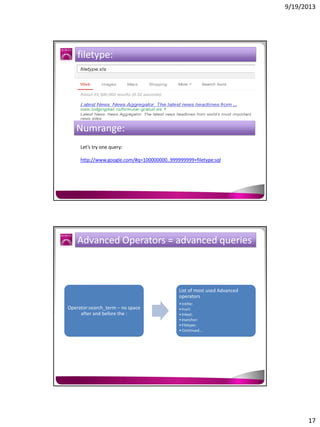
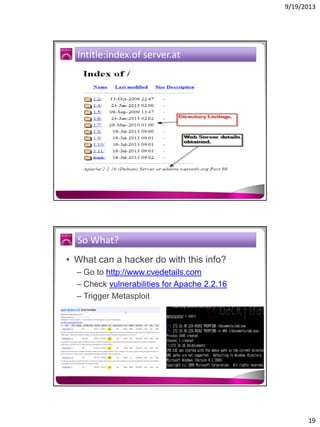
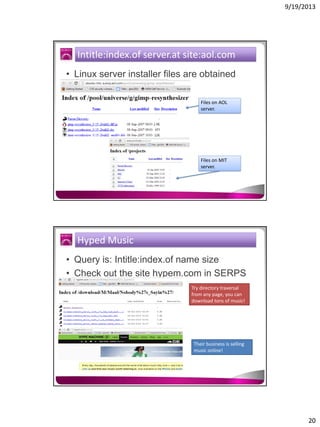
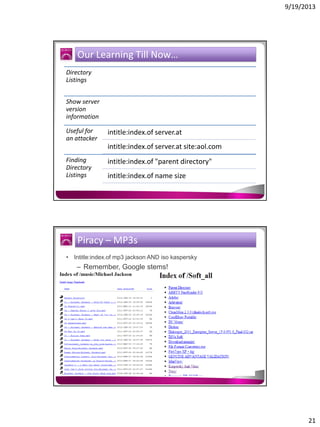
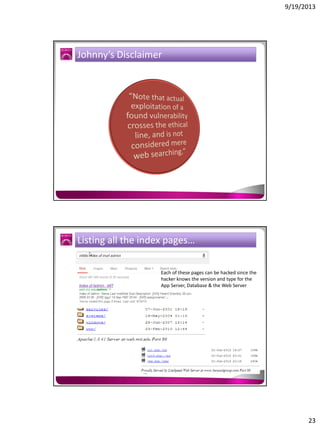
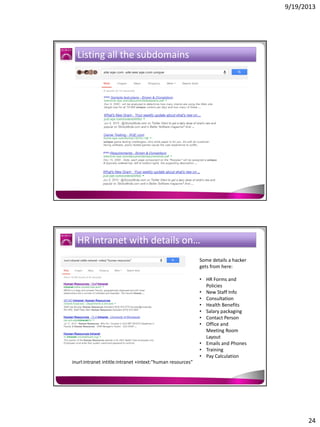
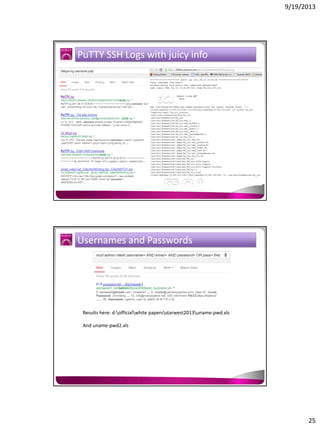
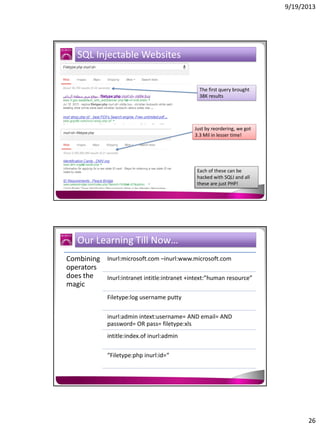
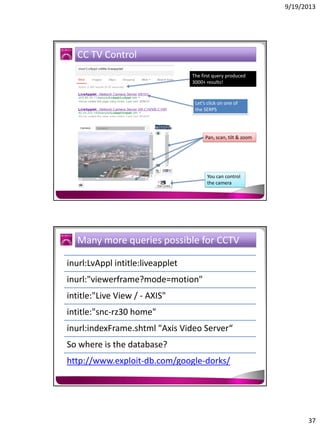
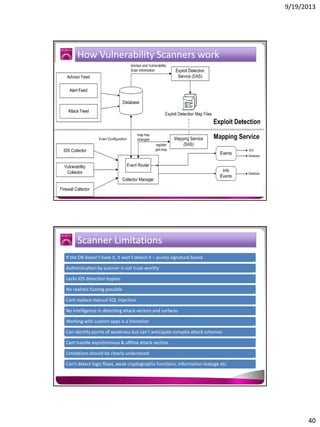
The document discusses the Google Hacking Database (GHDB) and its role in exposing vulnerabilities through various hacking techniques and methods. It shares insights on advanced search operators, types of information that can be targeted, and specific queries that hackers might use to access sensitive data. Additionally, it emphasizes the importance of security awareness and the limitations of vulnerability scanners in identifying complex attack vectors.