Embed presentation
Download as PDF, PPTX
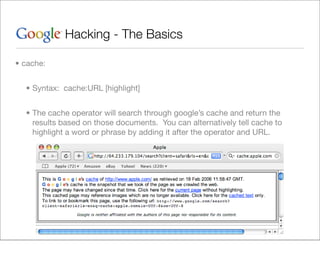
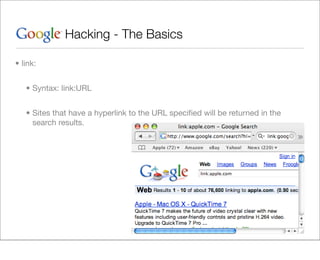
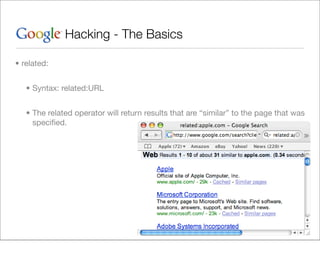
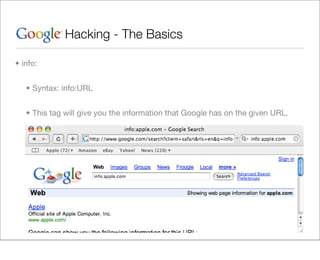
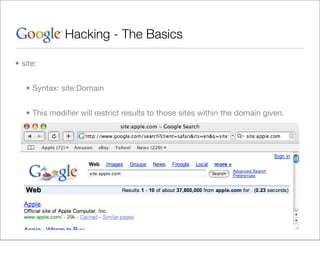
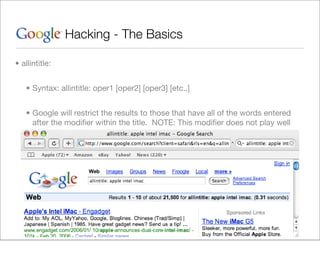
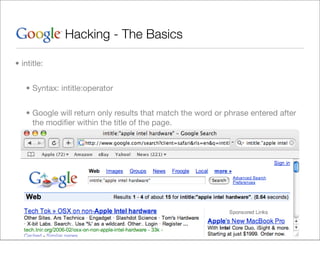
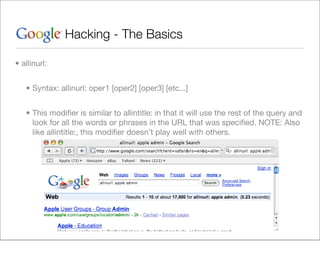
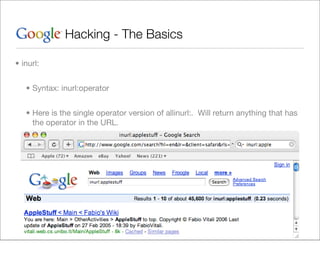
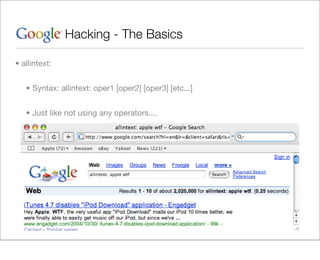
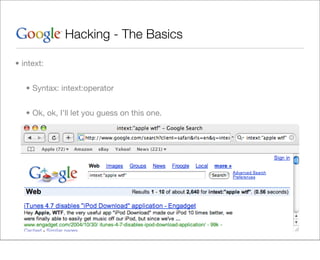
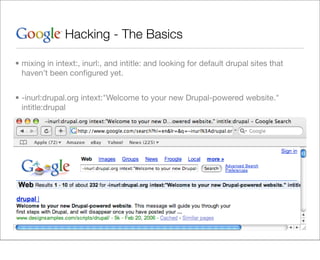
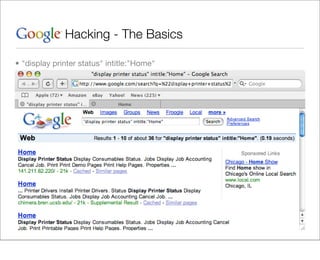
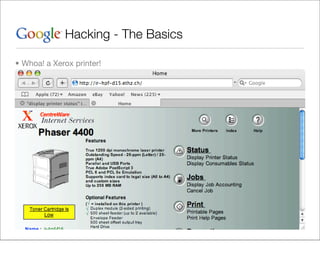
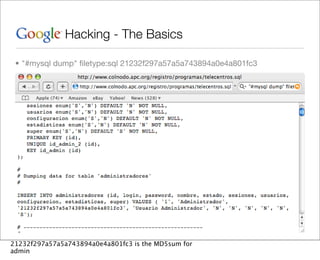
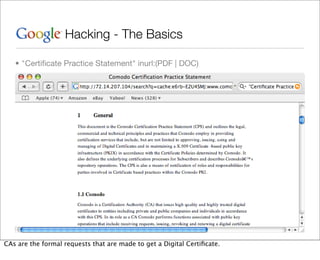
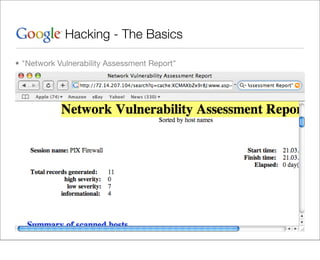
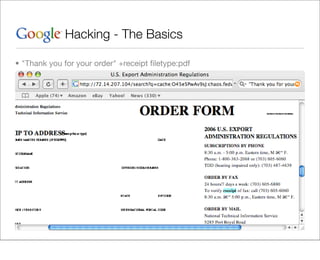
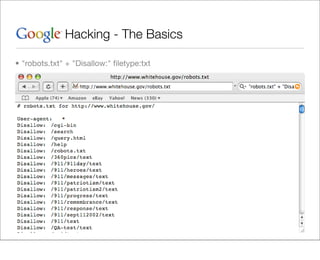
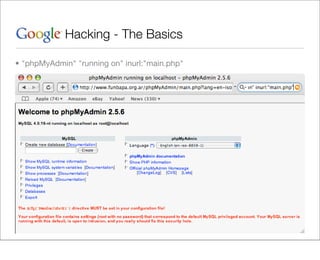
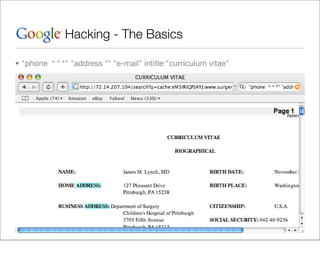
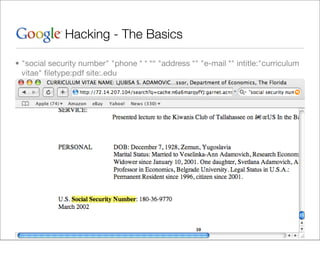
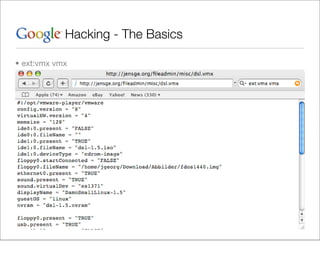
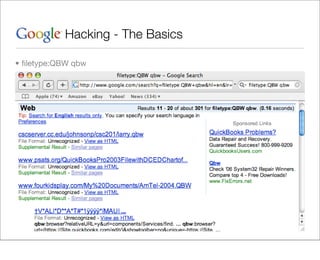
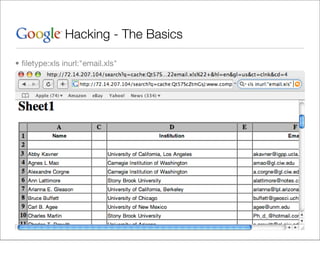
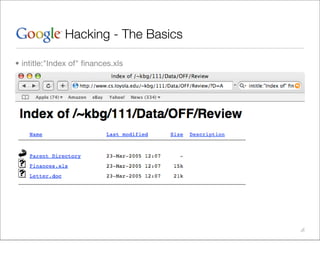
This document provides an overview of Google hacking techniques. It explains that Google hacking involves using Google search operators and modifiers to identify vulnerabilities on websites. It then defines and provides examples for several common operators and modifiers like cache:, link:, related:, intitle:, and inurl:. It encourages combining these in searches and provides examples of effective Google hack searches.































