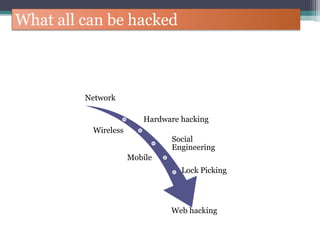
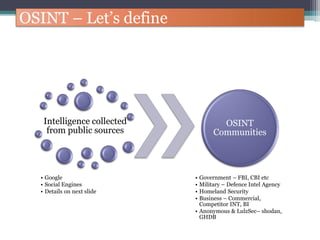
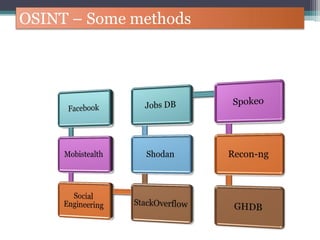
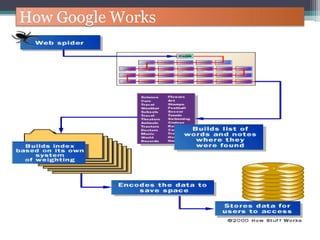
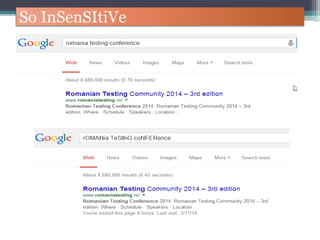
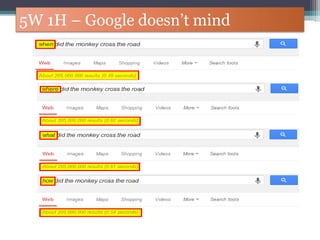
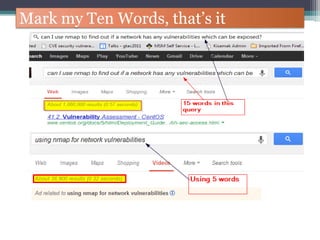
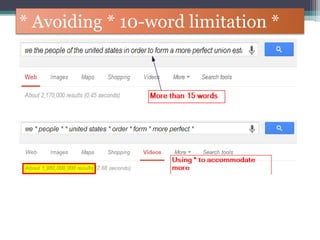
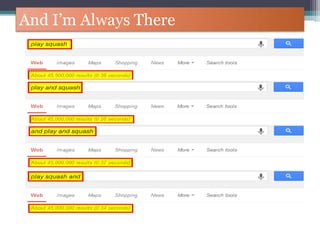
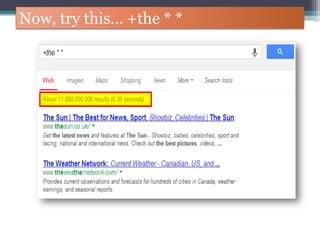
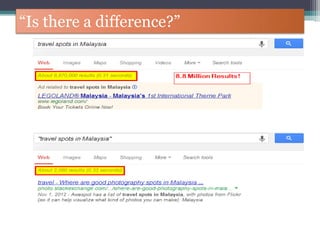
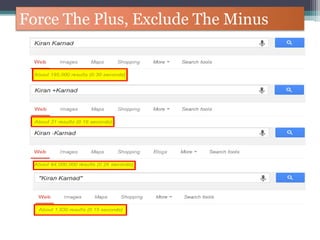
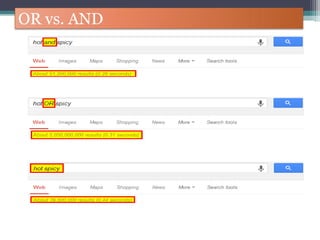
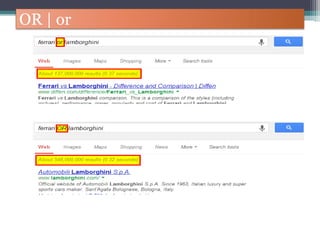
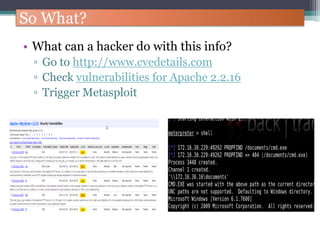
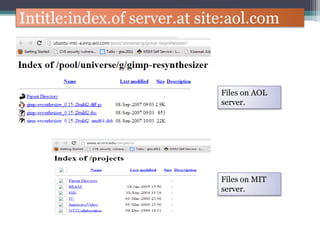
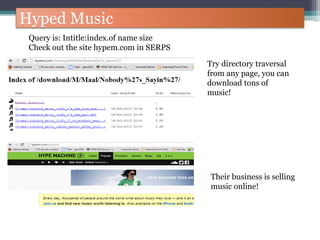
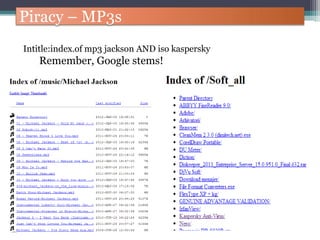
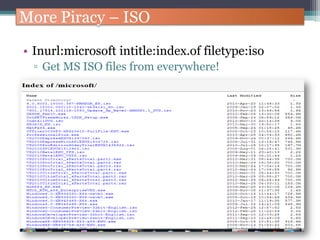
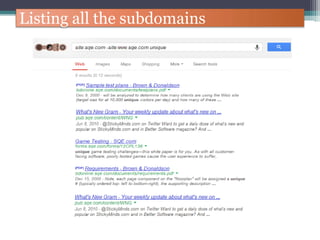
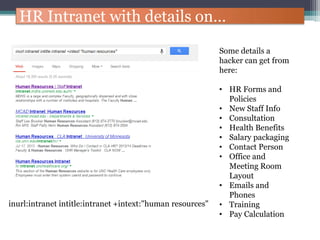
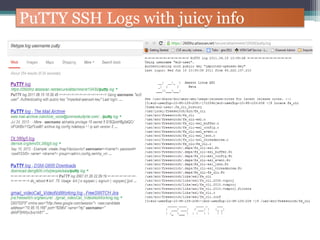
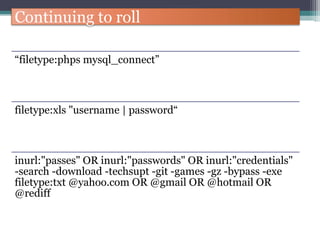
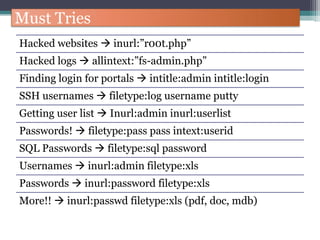
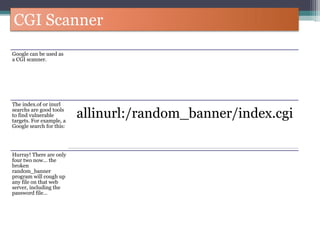
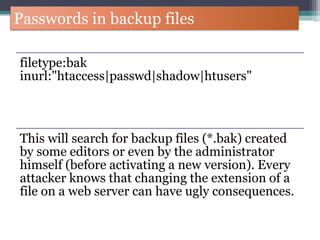
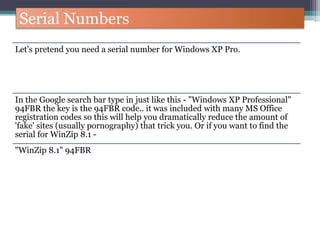
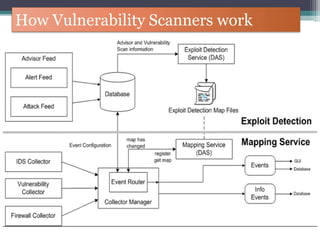
The document discusses how to use Google searches and operators to find sensitive information that could be useful for hackers. Some key points discussed include using intitle and inurl operators to find login portals and server configuration files containing passwords. Examples are given of searches to find passwords, credit card numbers, software serial numbers, and even live video feeds from unsecured cameras. The document warns that exploiting any found vulnerabilities would be unethical.