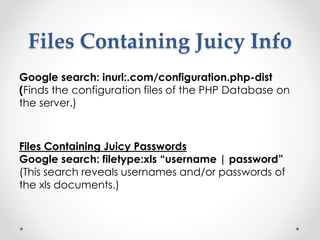
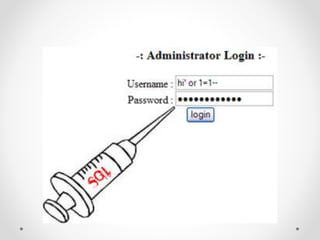
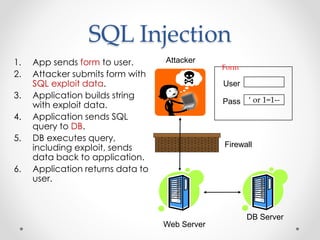
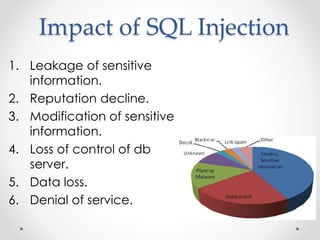
Google dorks are search operators used to refine Google searches. They can be used to access secure webpages, download files, or access security cameras. Common dorks include "site:", "inurl:", "intitle:", and "filetype:" or "ext:". SQL injection is a code injection technique that exploits security vulnerabilities in database applications. It works by inserting SQL commands into user input fields to alter the meaning of SQL queries and gain unauthorized access to databases. Defenses include input validation, prepared statements, limiting privileges, and intrusion detection systems.































![Defending Against Injection ctd.
• Use proper escapes strings, generally created
through PHP.
o $SQL = "SELECT * FROM users where username =
"mysql_real_escape_string($POST['user']);
• When someone tries to access the database
using a command like OR 1’”;, their query
would return ’ OR 1’, because your query
was created to have a defined escape string.](https://image.slidesharecdn.com/presentation-150818125558-lva1-app6892/85/Google-Dorks-and-SQL-Injection-36-320.jpg)


