This document provides an overview and introduction to the technique of "Google hacking", which involves using Google searches and advanced operators to uncover sensitive information on websites that may have been inadvertently exposed or indexed by Google. Some key points made include:
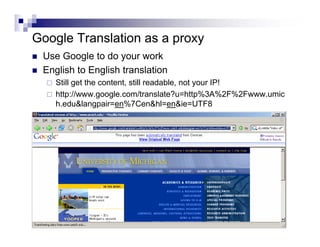
- Google hacking allows an attacker to perform reconnaissance without directly interacting with the target system.
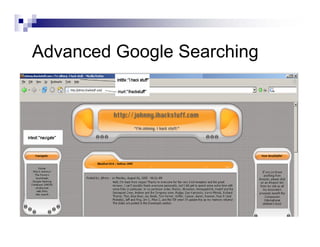
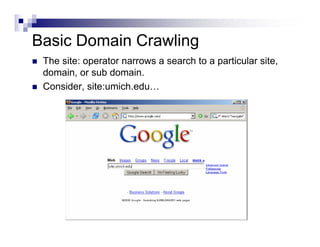
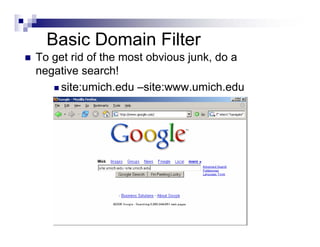
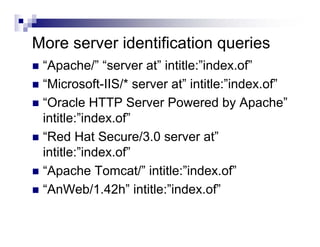
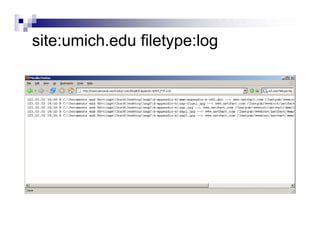
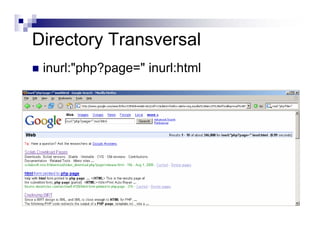
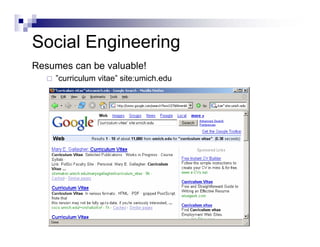
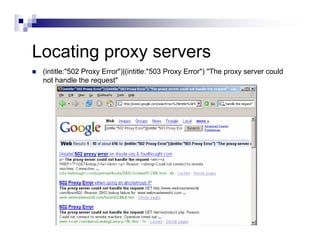
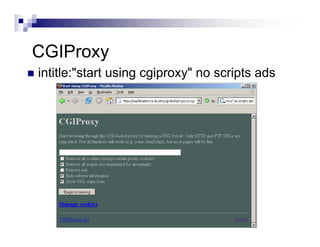
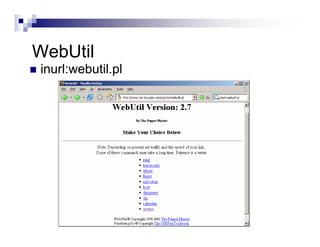
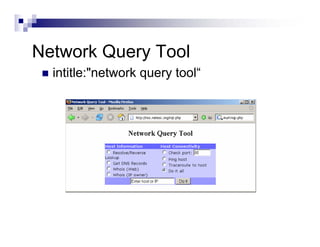
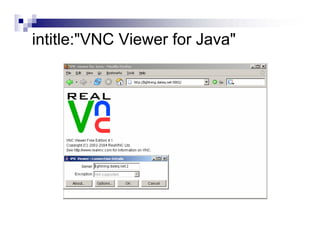
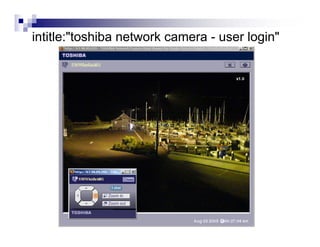
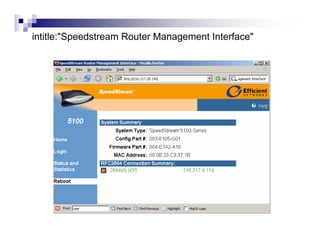
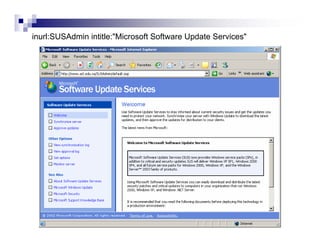
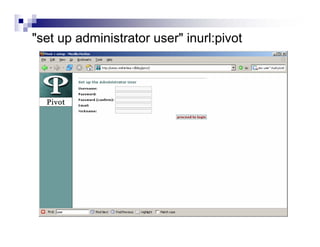
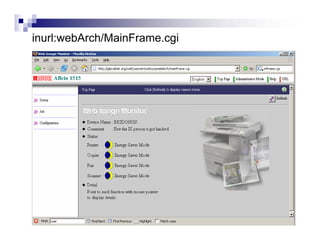
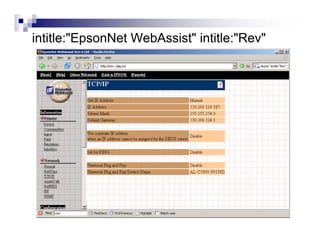
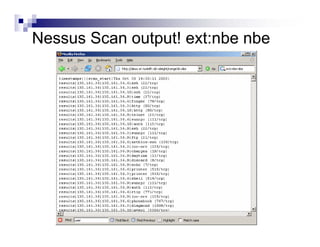
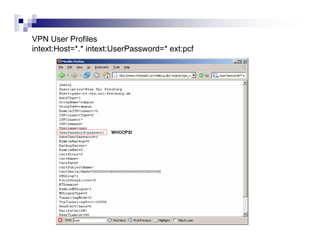
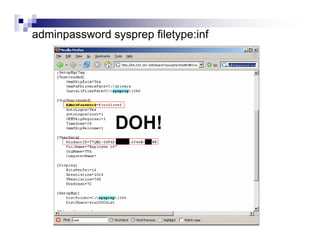
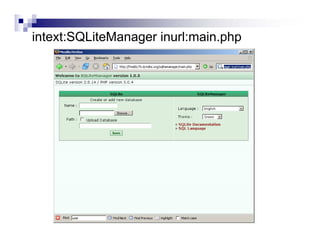
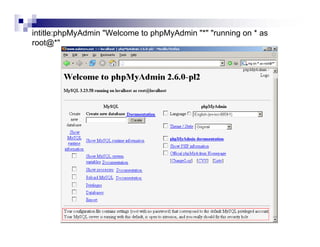
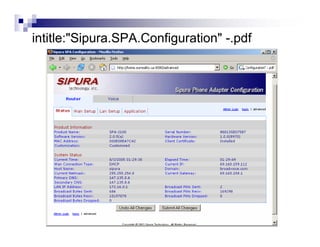
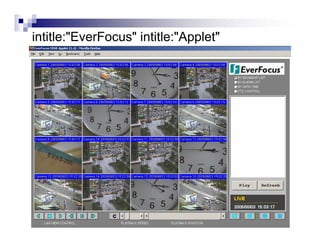
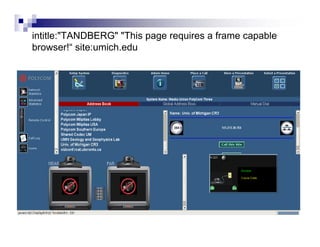
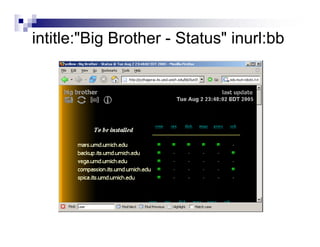
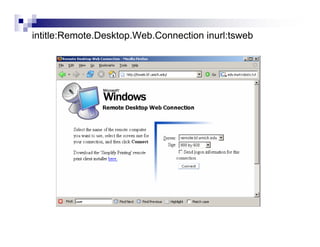
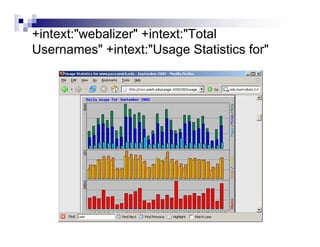
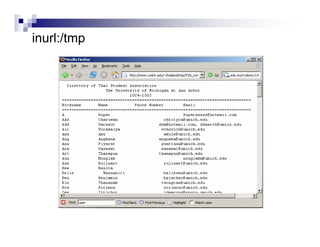
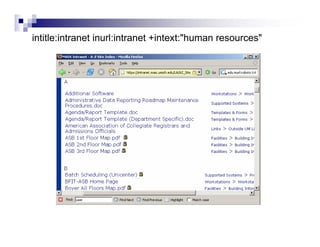
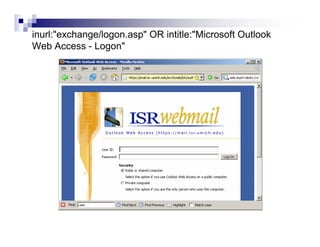
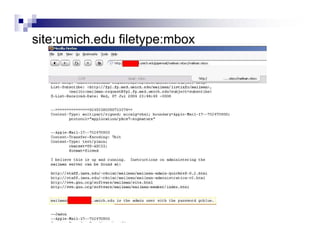
- Advanced operators like "site:", "intitle:", and "filetype:" allow narrowing searches to specific domains, page elements, or file types.
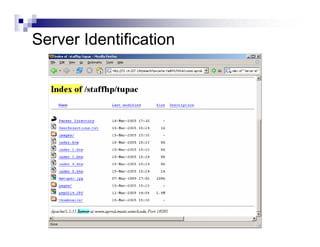
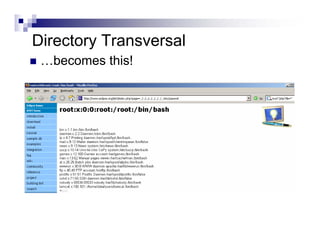
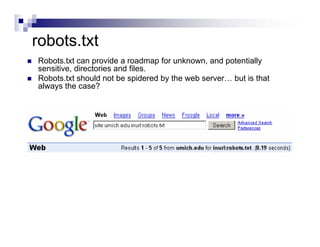
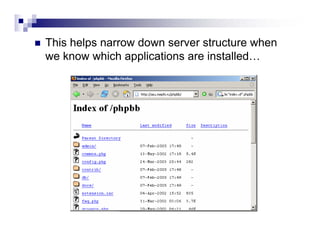
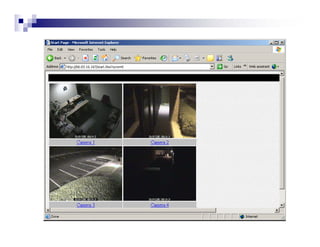
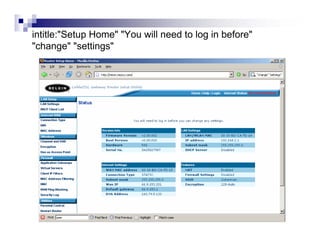
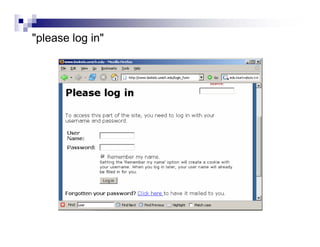
- Directory listings, server configuration files, backup files, and unprotected administrative interfaces are some examples of things that can be uncovered.
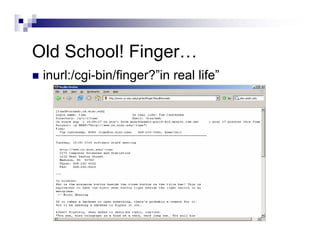
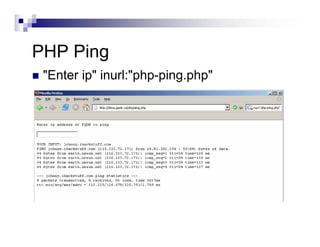
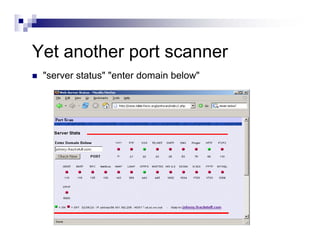
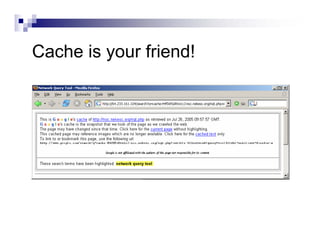
- The document demonstrates examples of Google queries that have uncovered sensitive information on various systems.