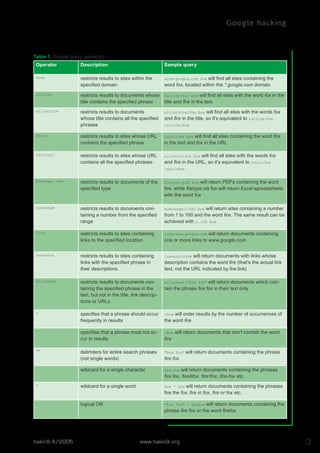
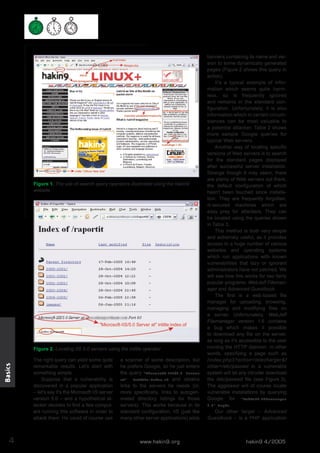
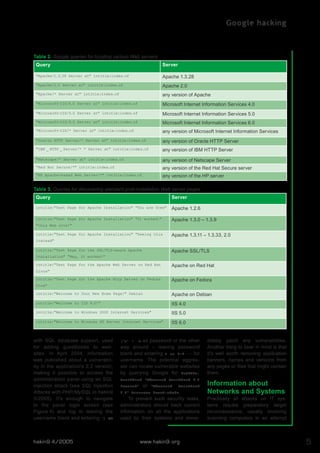
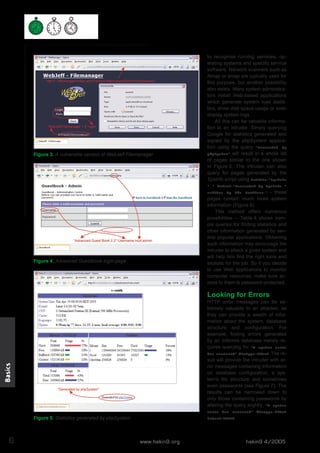
This document discusses how Google can be used to find confidential information and vulnerable systems on the internet. It provides examples of Google search queries that can locate specific versions of web servers, as well as queries to find unsecured installations of common web applications with known vulnerabilities like WebJeff Filemanager and Advanced Guestbook. The document encourages readers to think carefully about the type of sensitive data that users carelessly make public and how it could aid attackers.