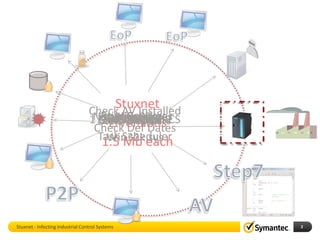
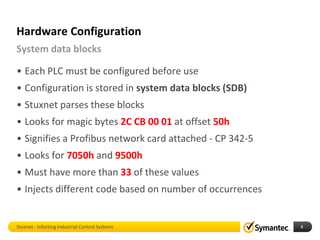
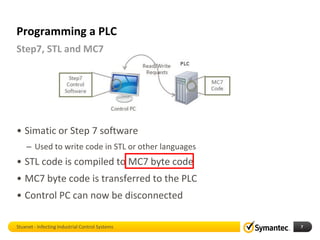
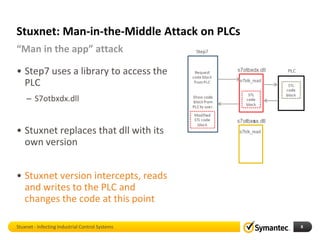
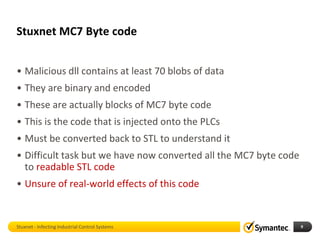
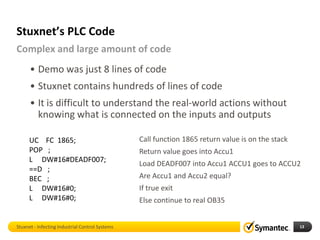
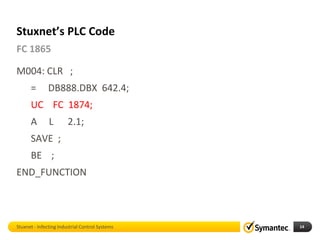
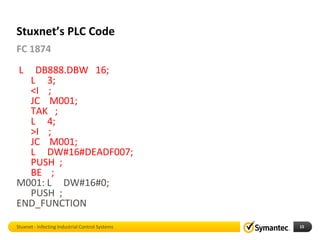
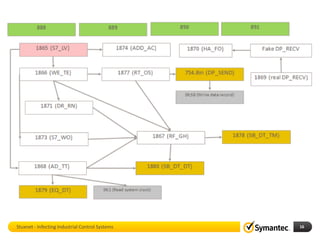
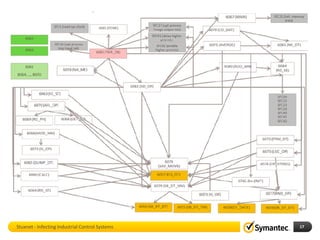
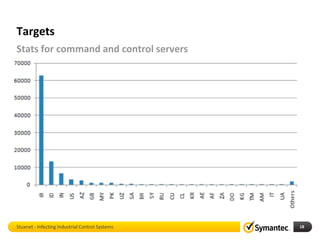
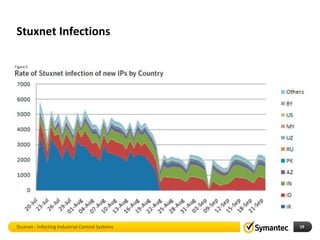
The document discusses Stuxnet, a sophisticated computer worm designed to target industrial control systems, particularly specific models of programmable logic controllers (PLCs). It outlines how Stuxnet infects these systems through a man-in-the-middle attack, manipulating the PLC code while appearing clean during read operations. The document also includes a demonstration of a proof of concept highlighting Stuxnet's capabilities and complexity.