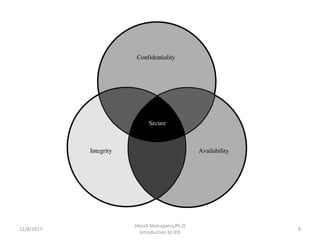
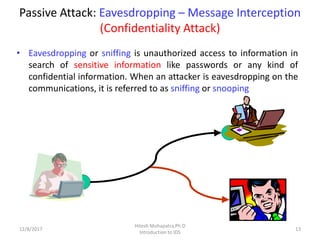
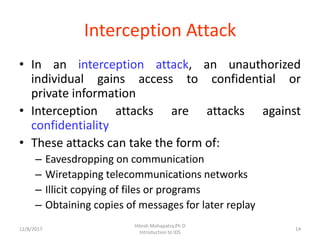
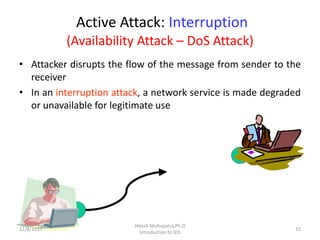
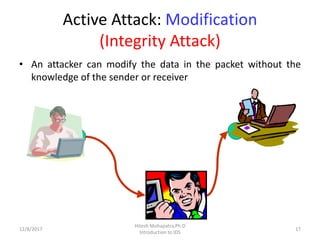
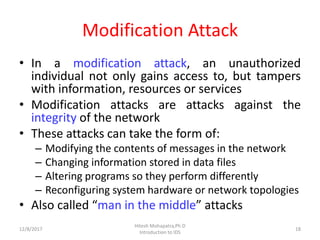
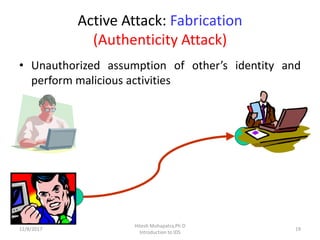
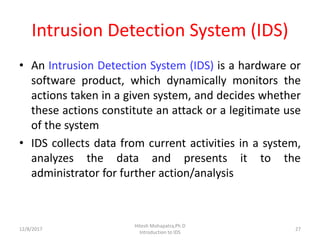
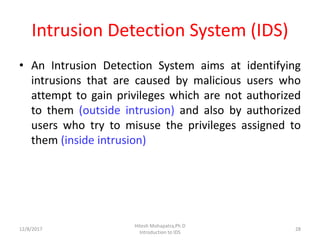
The document provides an introduction to intrusion detection systems (IDS). It defines key concepts related to information security like threats, attacks, and security goals of confidentiality, integrity and availability. It discusses different types of attacks such as passive eavesdropping and active attacks like interruption, modification and fabrication. The document then introduces IDS, explaining what it is, the need for it, types of intrusions from inside and outside, and classifications of IDS based on information source, type of information and usage frequency.
















![Brief History of Intrusion Detection
• In The Beginning…
– Manual Intrusion Detection in practice
• System administrator manually monitor user’s activity
• Ad hoc and non-scalable
• The Study of Intrusion Detection
– Was started by James P. Anderson [1] in 1980
“Computer Security Threat Monitoring and Surveillance”
• Anderson’s Technical Report
– Introduced the notion of audit trails
– Suggested that audit trails contain vital information that could be
valuable in tracking misuse and understanding user behavior
– Formed foundation of host-based intrusion and IDS in general
12/8/2017
Hitesh Mohapatra,Ph.D
Introduction to IDS
29](https://image.slidesharecdn.com/introductionids-171208140418/85/Introduction-IDS-29-320.jpg)
![Brief History of Intrusion Detection
• Dr. Dorothy Denning developed an Intrusion
Detection Expert System (IDES) [2] in early 80’s
– Proposed “An Intrusion Detection Model” in 1987 which is
the first general intrusion detection model
• Heberlein et al. [3] introduced the idea of network
intrusion detection in 1990 - A Network Security
Monitor (NSM)
• Mukherjee et al. [4], proposed Network Intrusion
Detection in 1994
• … and so on
12/8/2017
Hitesh Mohapatra,Ph.D
Introduction to IDS
30](https://image.slidesharecdn.com/introductionids-171208140418/85/Introduction-IDS-30-320.jpg)



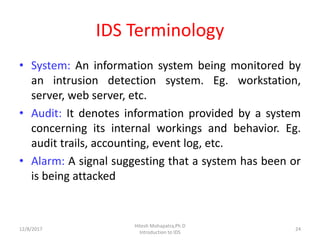
![Internal Intruders
• Anderson [1] divided internal intruders into three
subgroups, in increasing order of difficulty of
detection - masquerader, legitimate and
clandestine
• Masqueraders
– Assume identity of a legitimate user and penetrates
into a computer system
– Either an external penetrator who has succeded in
penetrating the access controls
– An employee with access to the computer system who
tries to exploit another legitimate user’s account
whose user id and password he may have obtained
12/8/2017
Hitesh Mohapatra,Ph.D
Introduction to IDS
34](https://image.slidesharecdn.com/introductionids-171208140418/85/Introduction-IDS-34-320.jpg)




![Application-Specific (AppIDS) and Database
IDS (DIDS)
• The concept of application-level intrusion detection was
introduced by Sielken [5] and has become an interesting field
of research very recently
• At the level of database, a file has an inherent structure which
is subdivided into tables, rows and columns
• HIDSs cannot detect changes to the structure or rows of the
tables whereas any AppIDS can identify these changes easily
• AppIDS use the semantics of the application to detect more
subtle attacks such as those carried out by internal intruders
12/8/2017
Hitesh Mohapatra,Ph.D
Introduction to IDS
46](https://image.slidesharecdn.com/introductionids-171208140418/85/Introduction-IDS-46-320.jpg)


![A Generic Intrusion Detection Model
• Dorothy Denning [2] proposed “An Intrusion-Detection
Model”
• It was published in IEEE Transactions on Software
Engineering in 1987
• The model is based on the hypothesis that security
violations can be detected by monitoring a system's audit
records for abnormal patterns of system usage
• The proposed model is independent of any particular
system, application environment, system vulnerability, or
type of intrusion, thereby providing a framework for a
general purpose intrusion detection system
12/8/2017
Hitesh Mohapatra,Ph.D
Introduction to IDS
57](https://image.slidesharecdn.com/introductionids-171208140418/85/Introduction-IDS-57-320.jpg)
