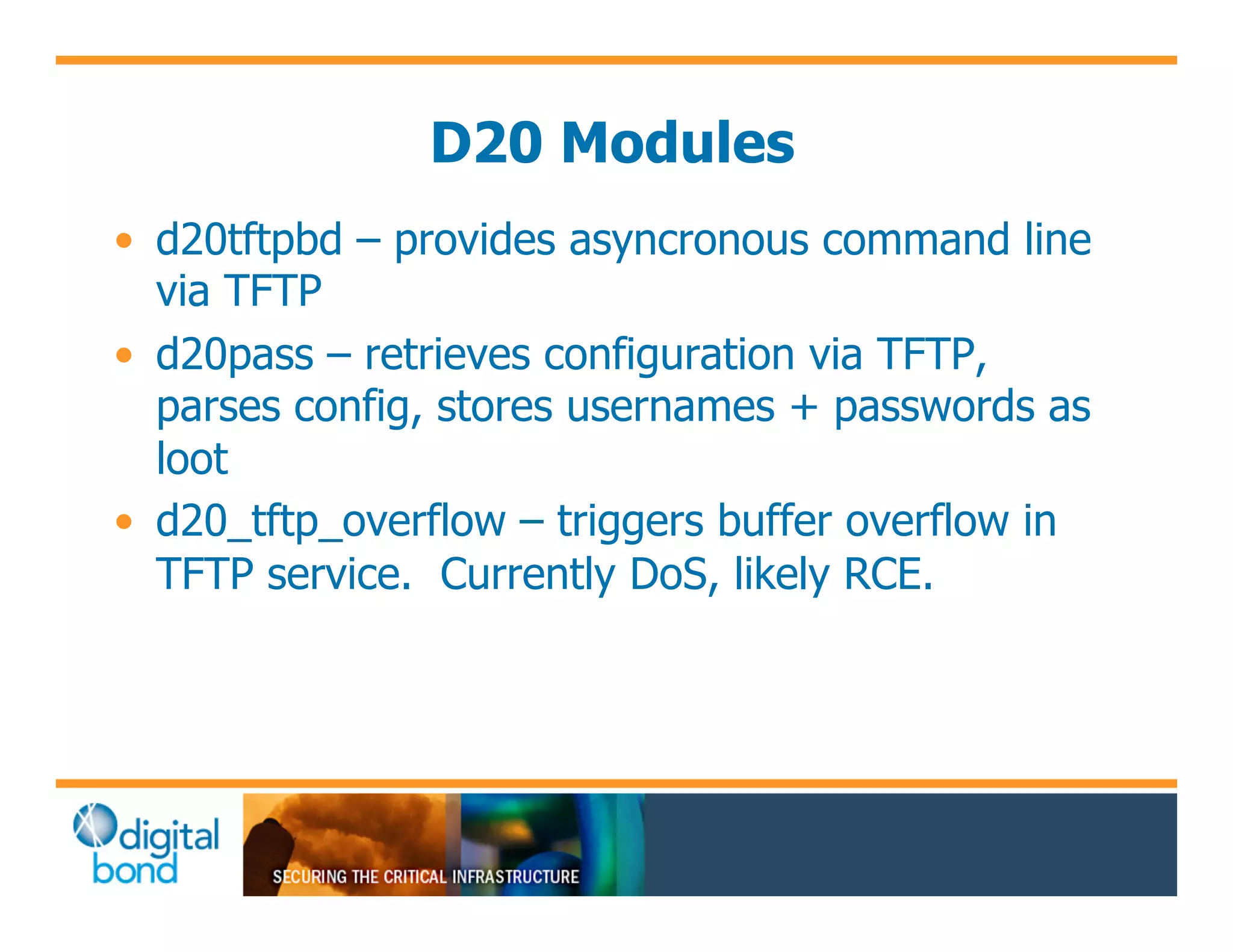
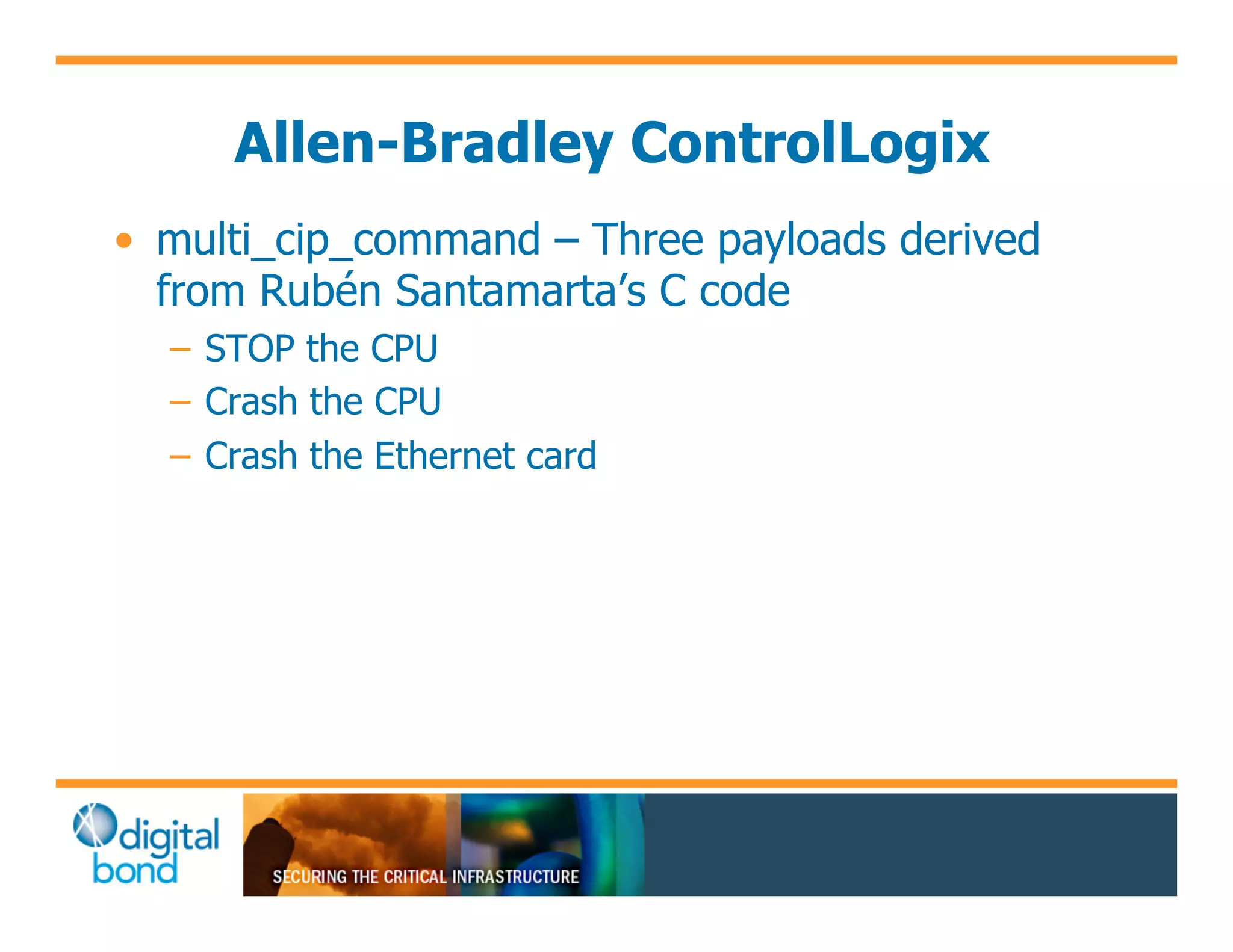
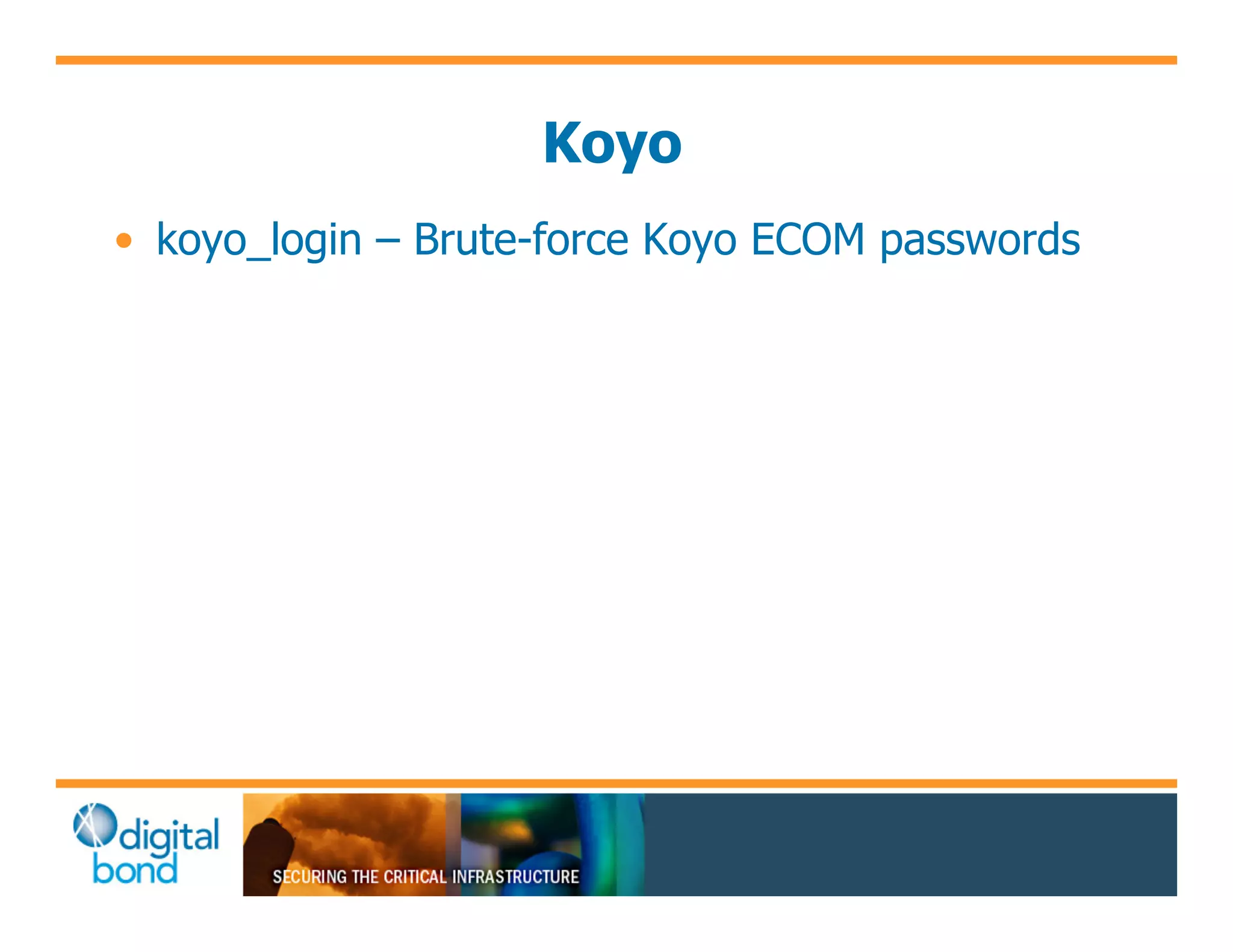
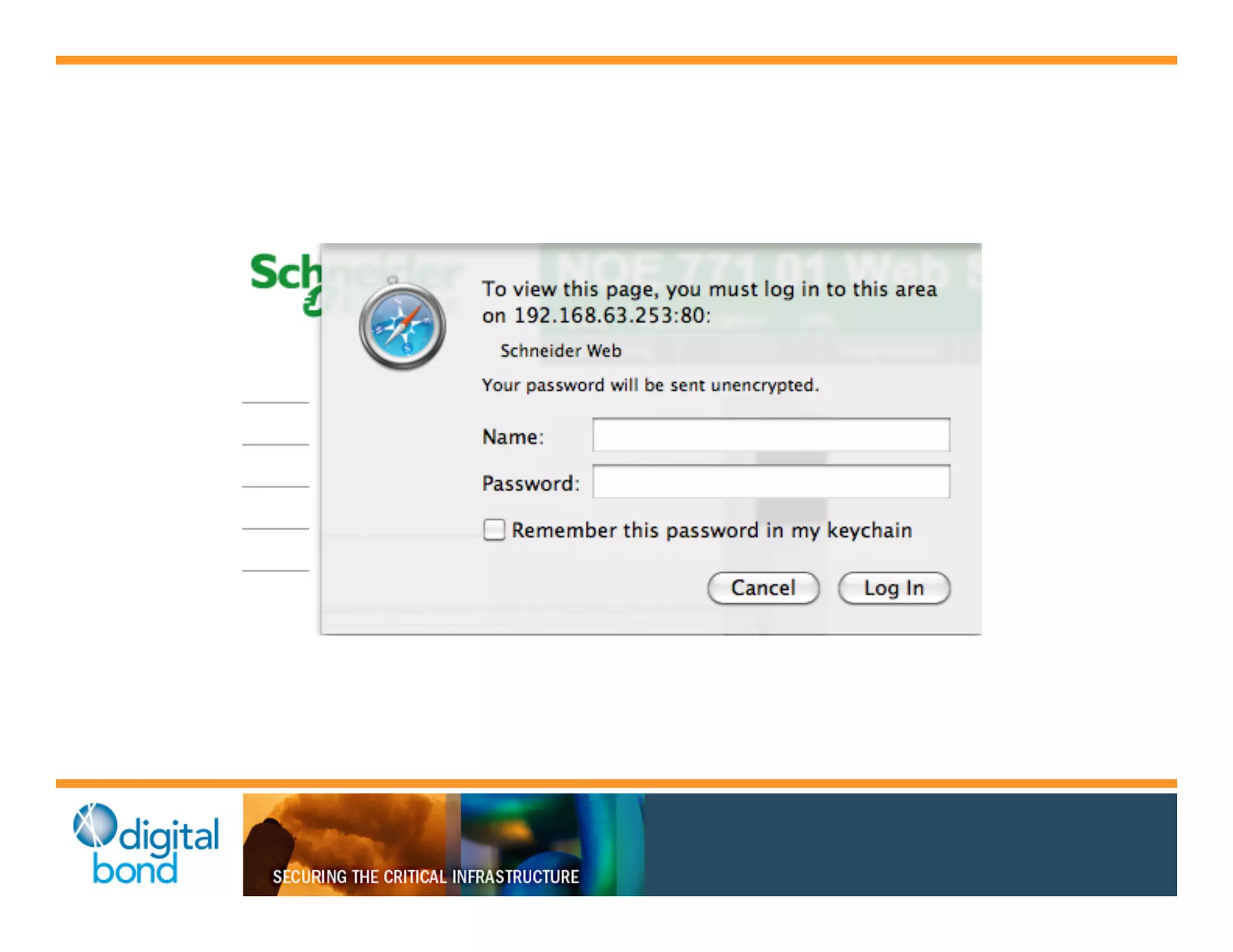
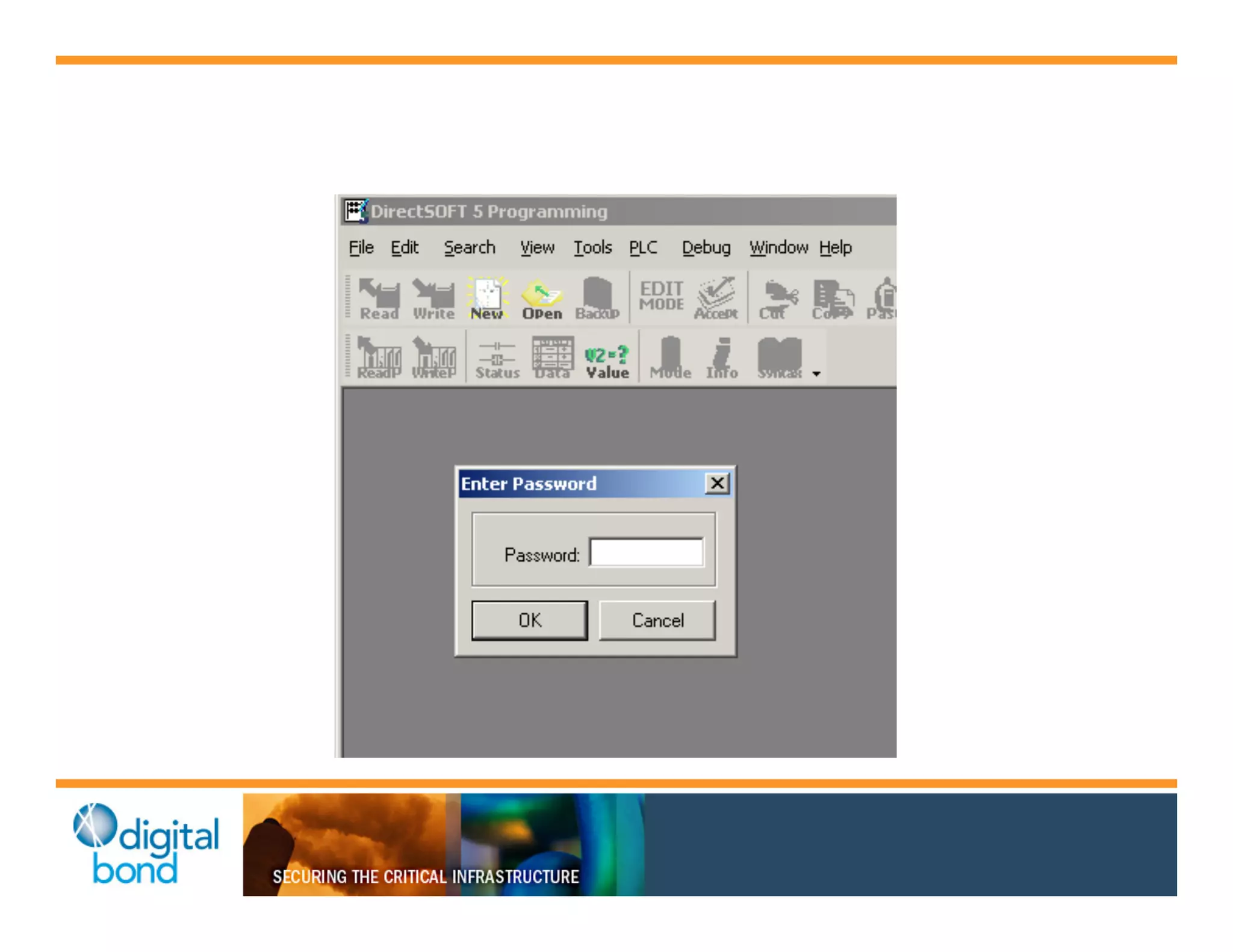
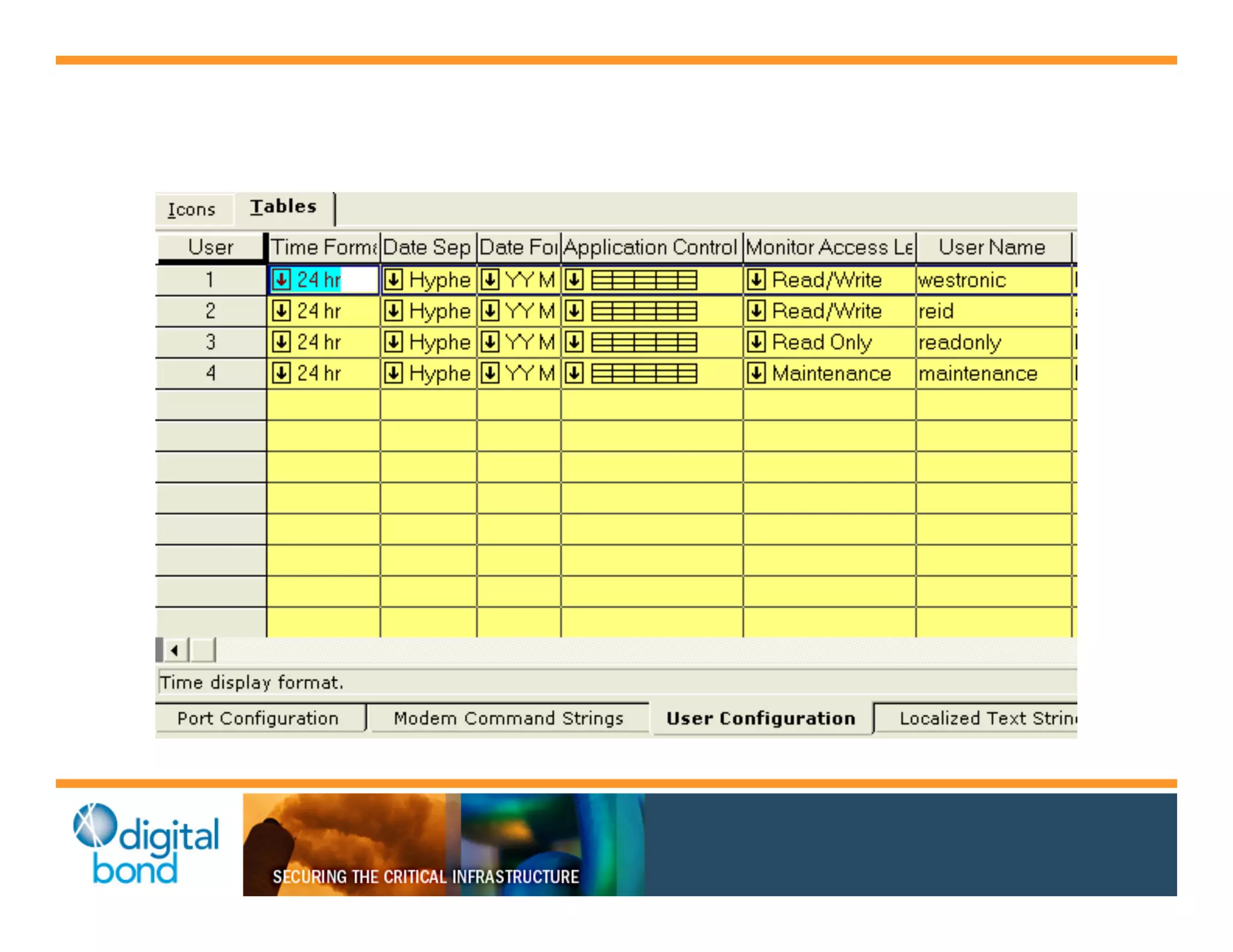
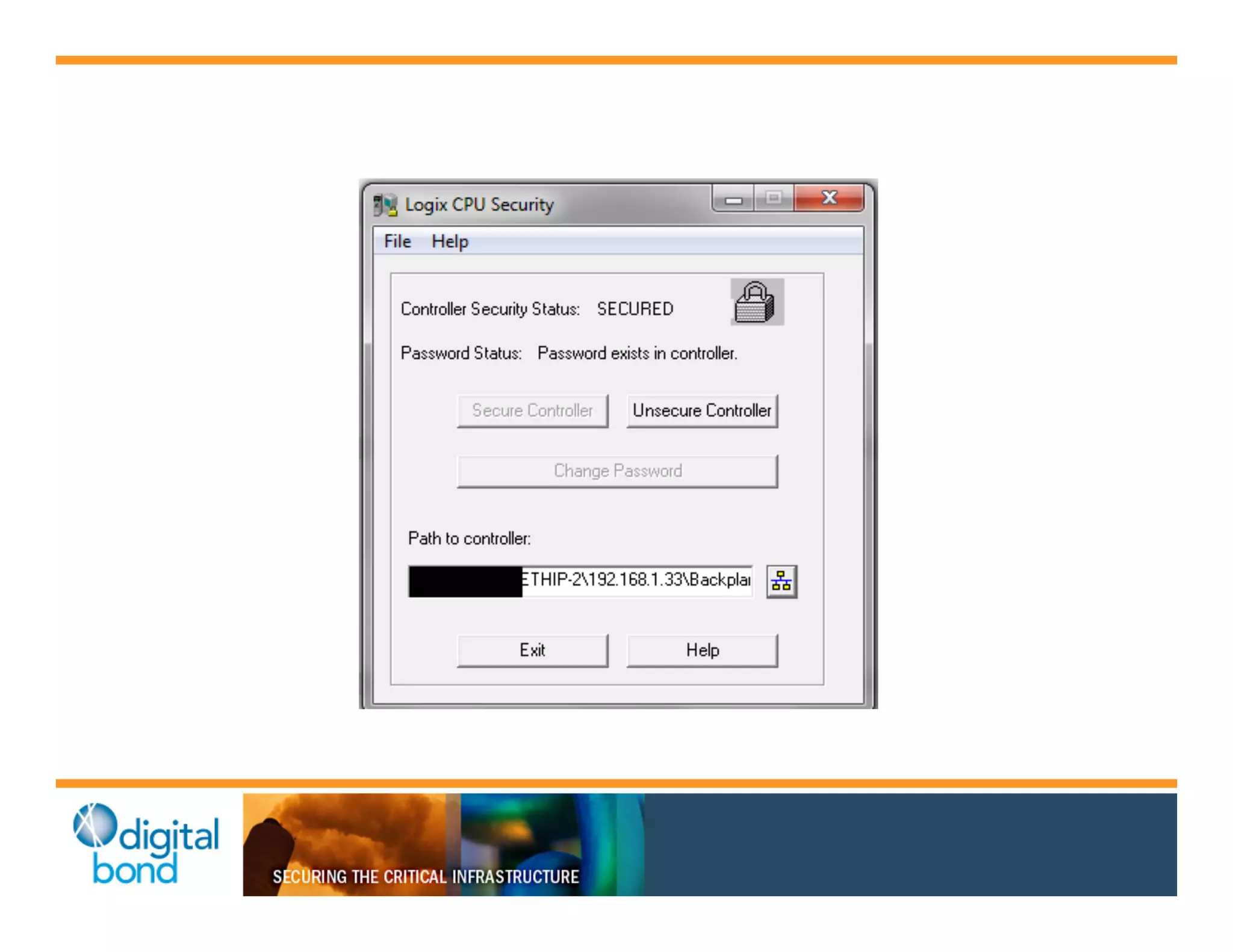
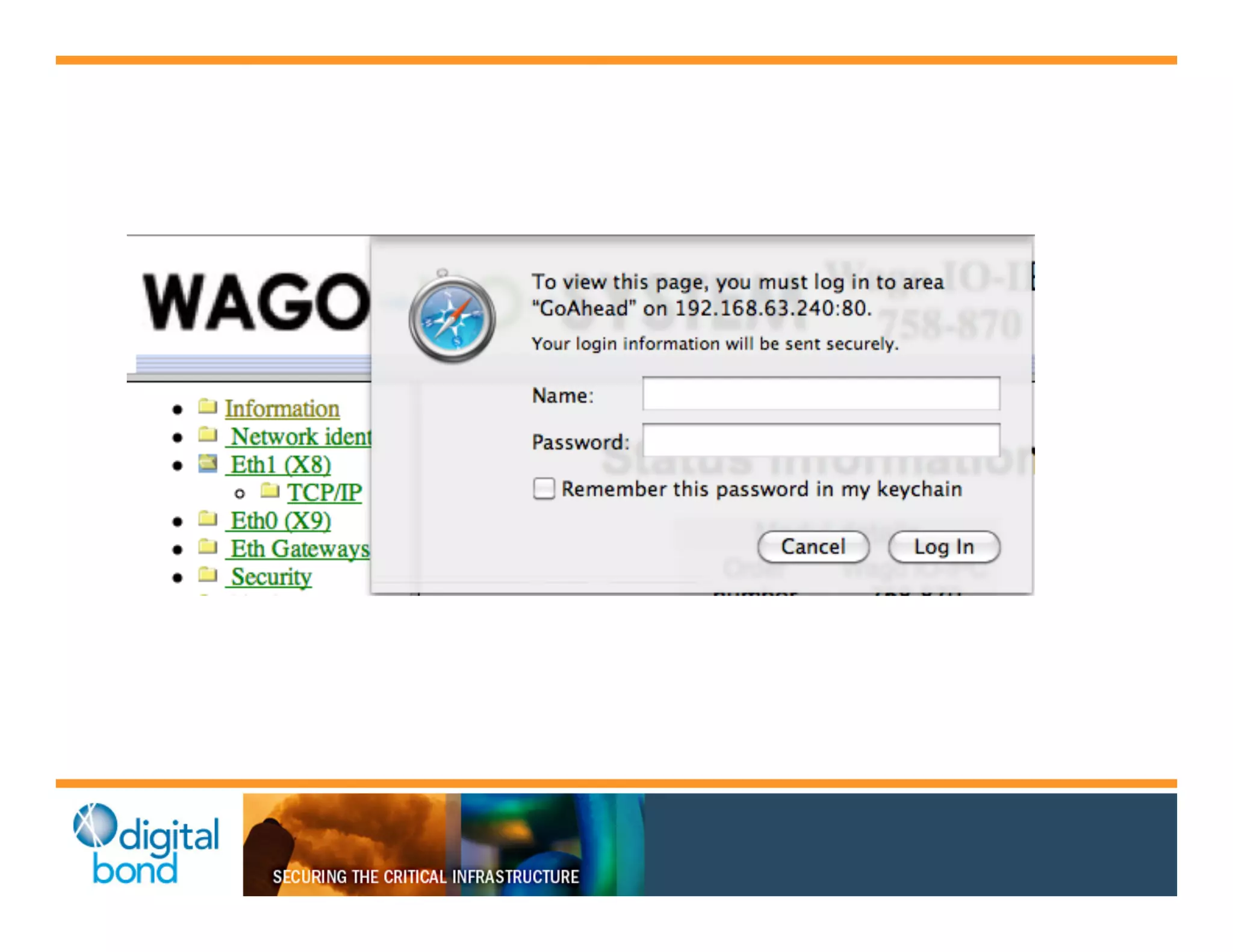
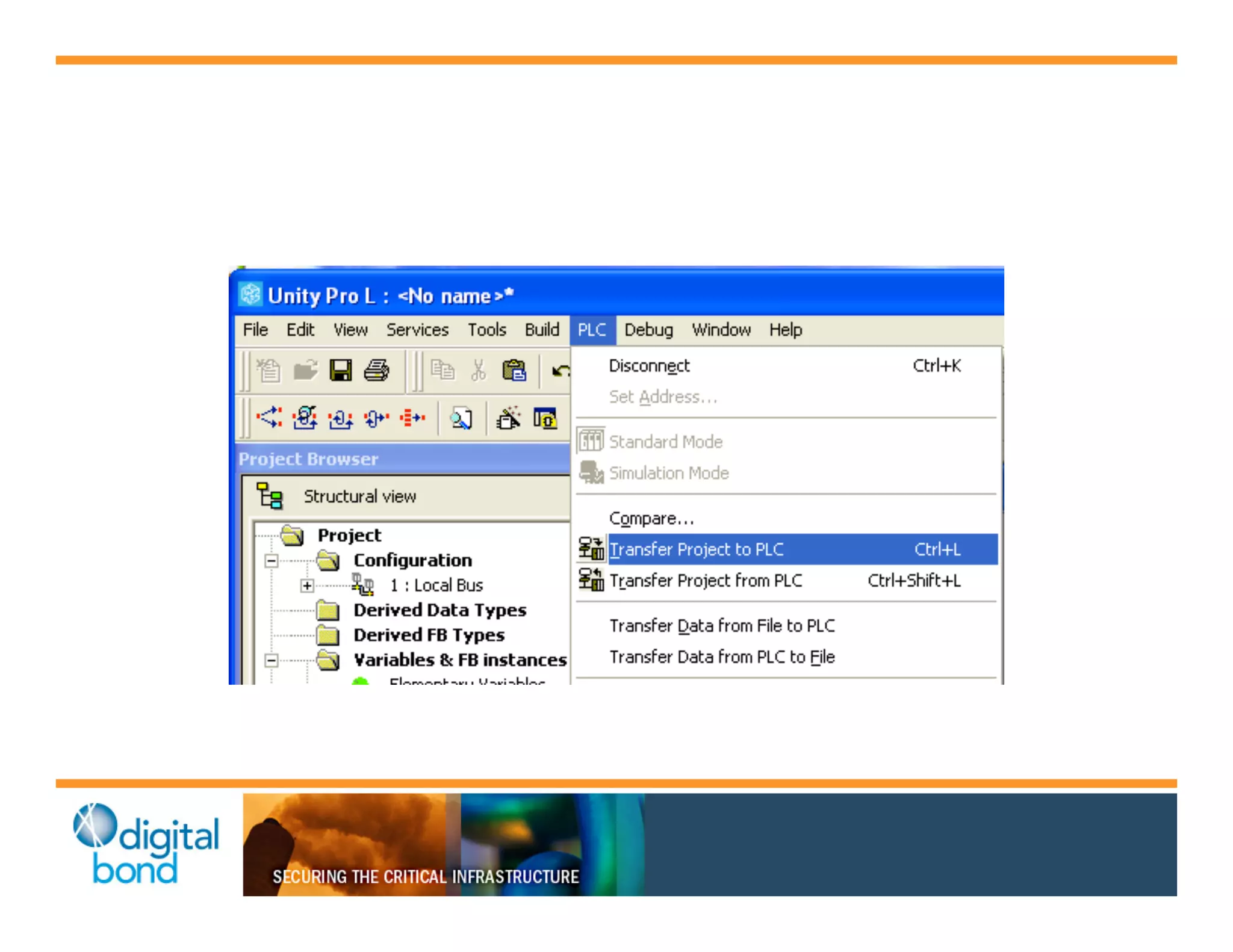
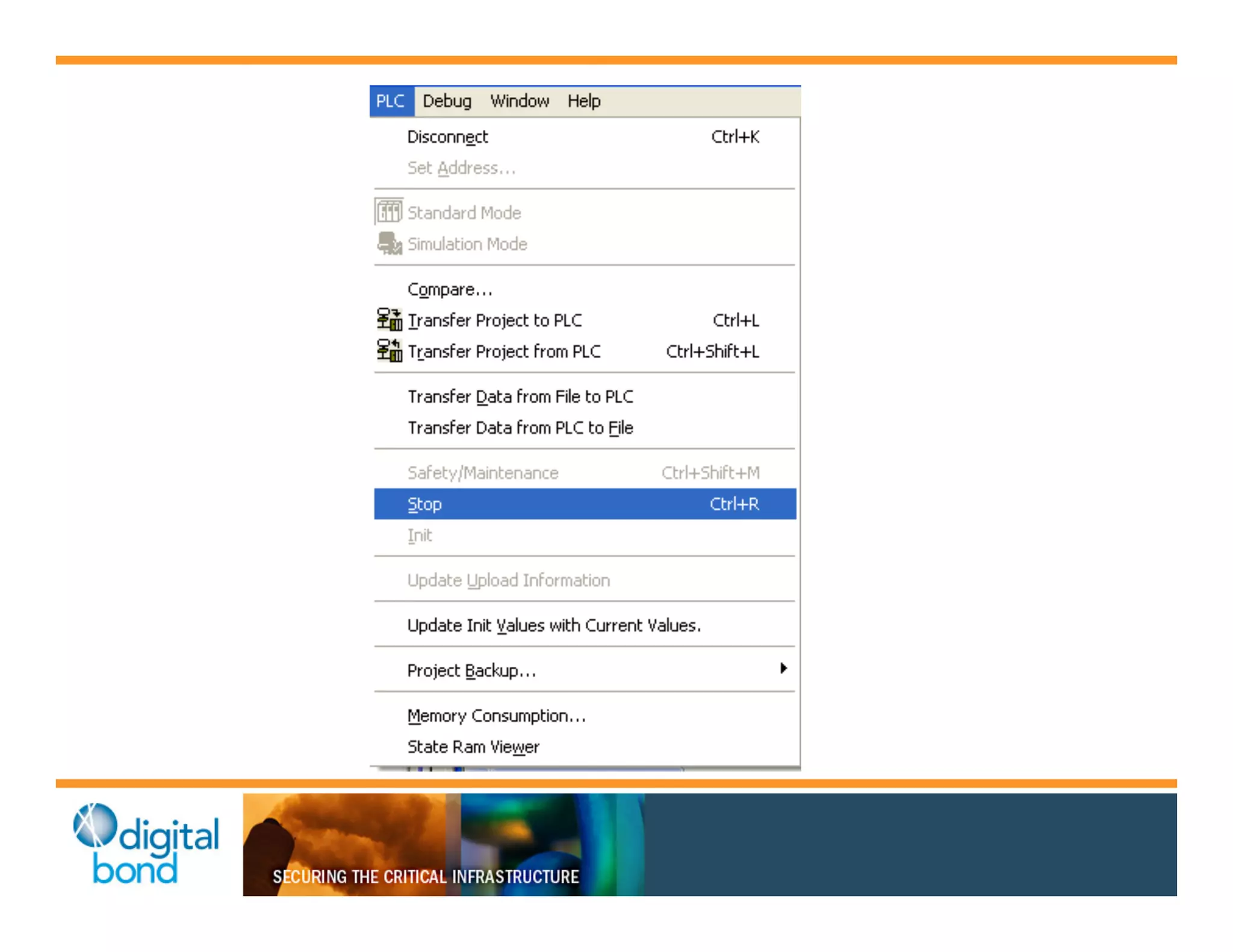
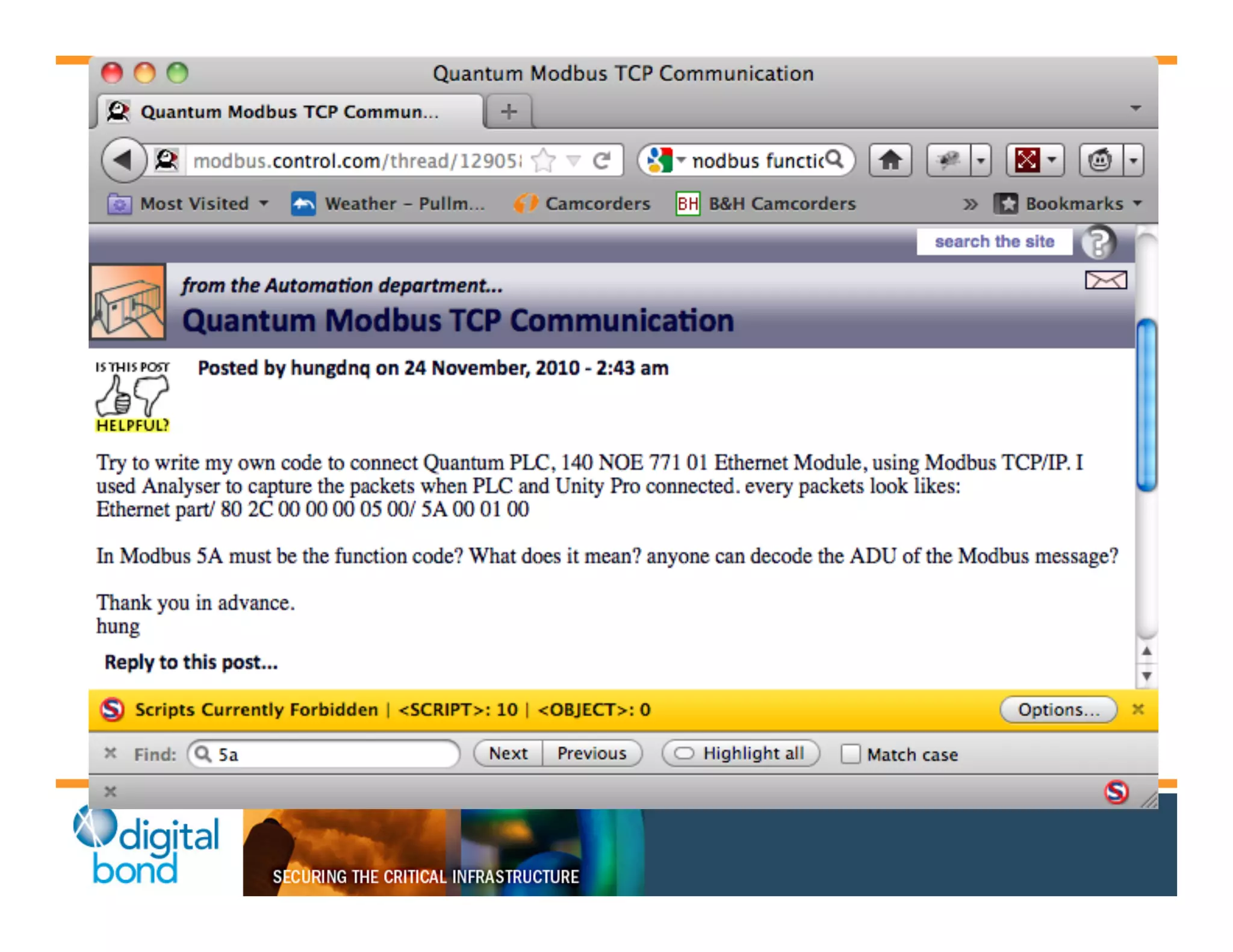
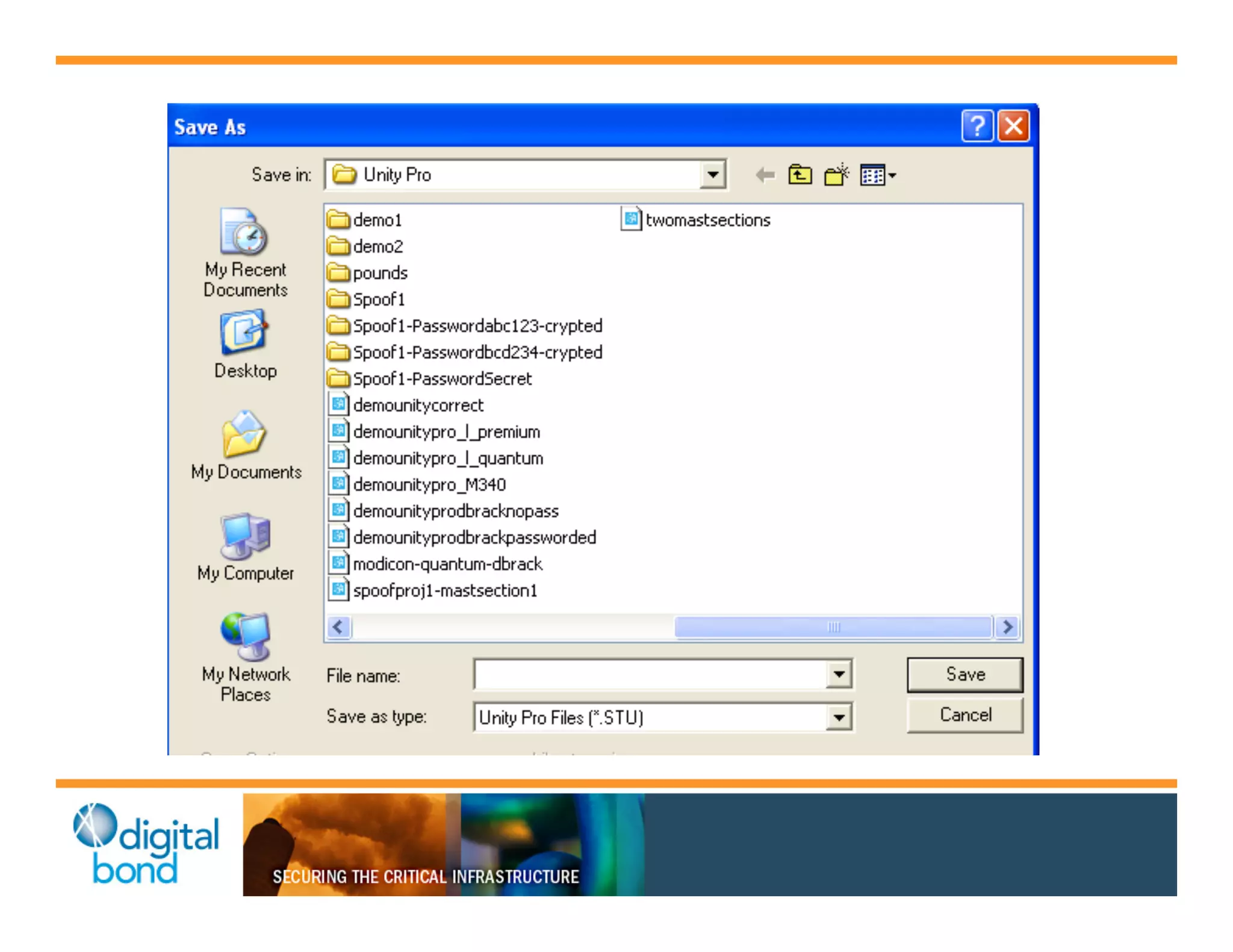
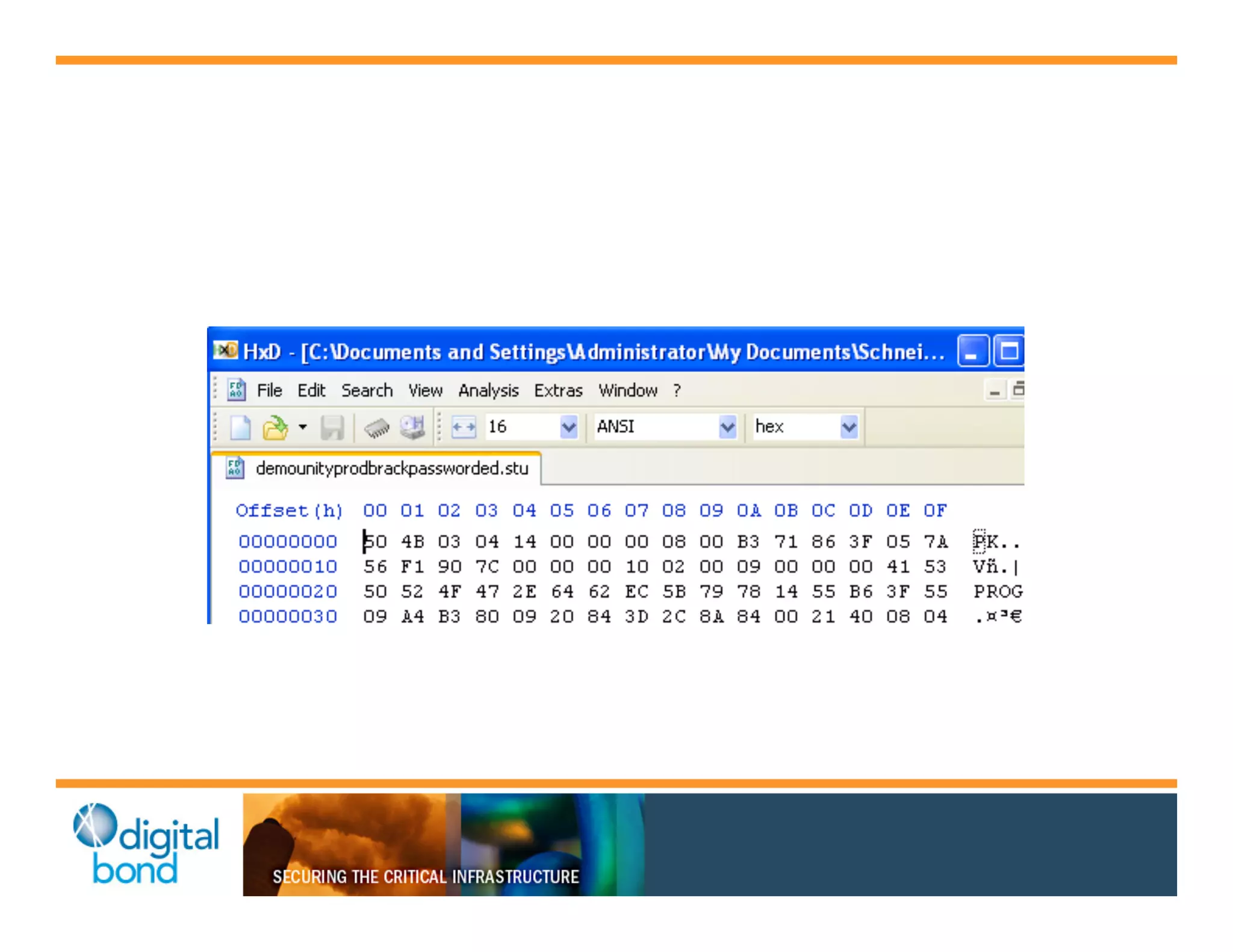
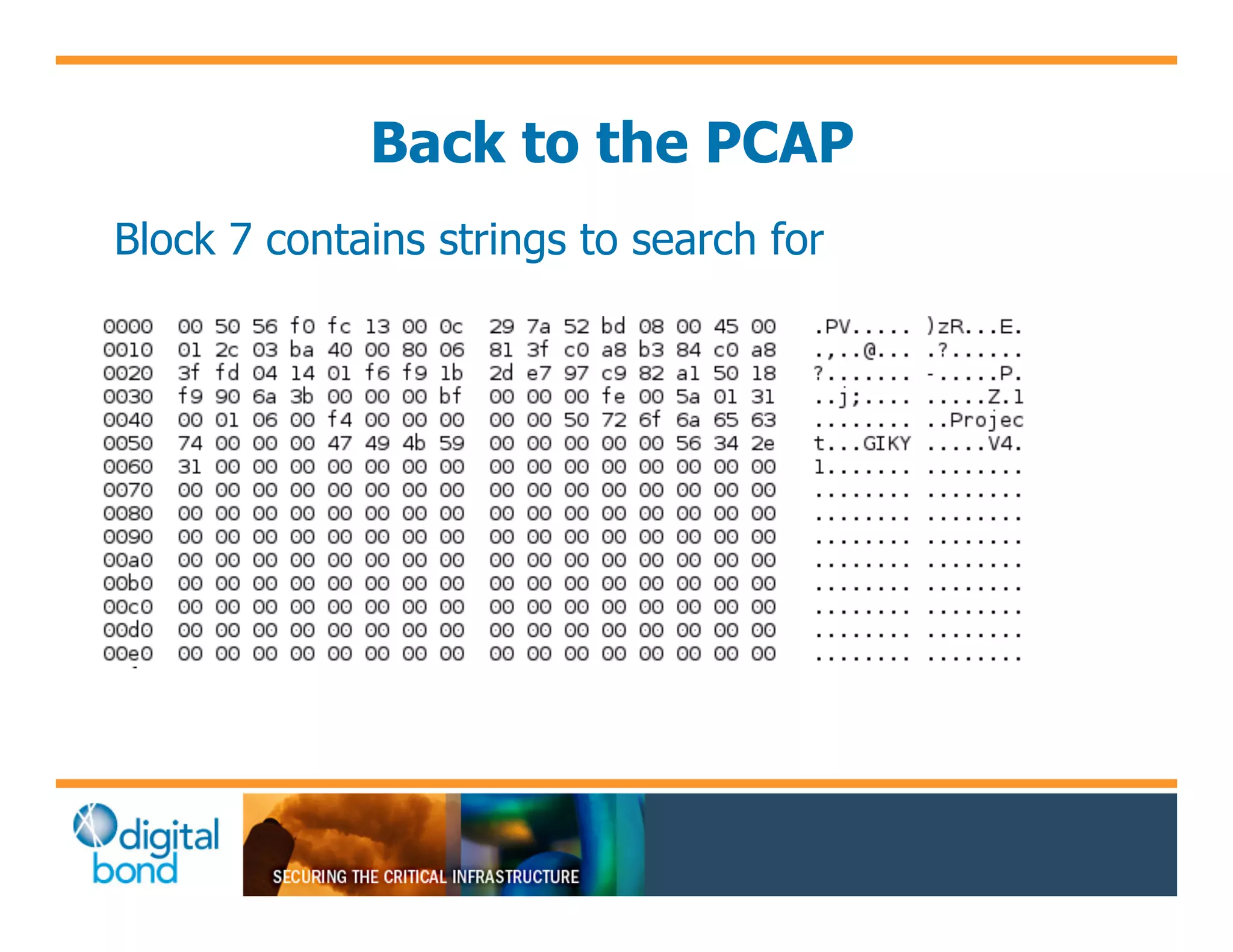
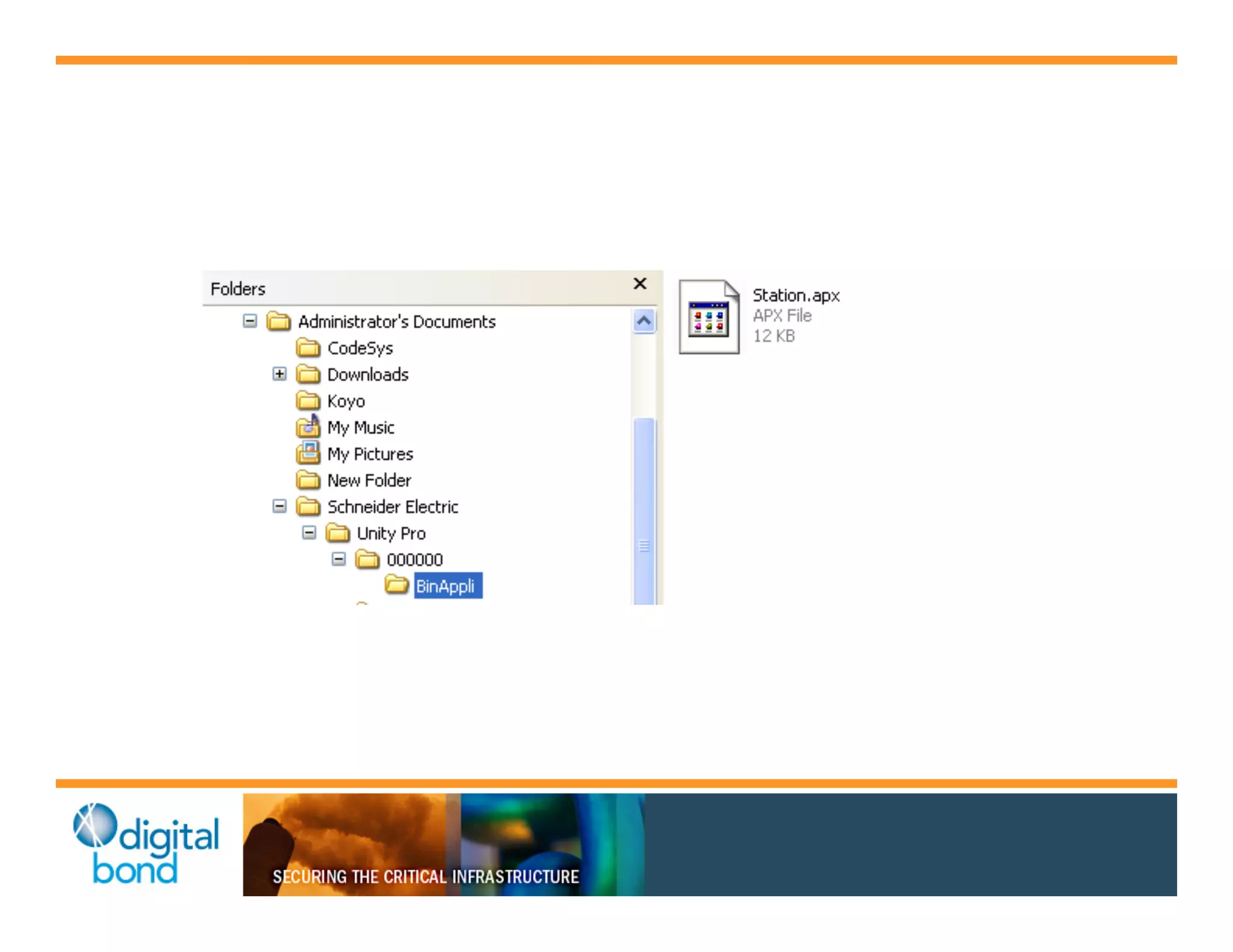
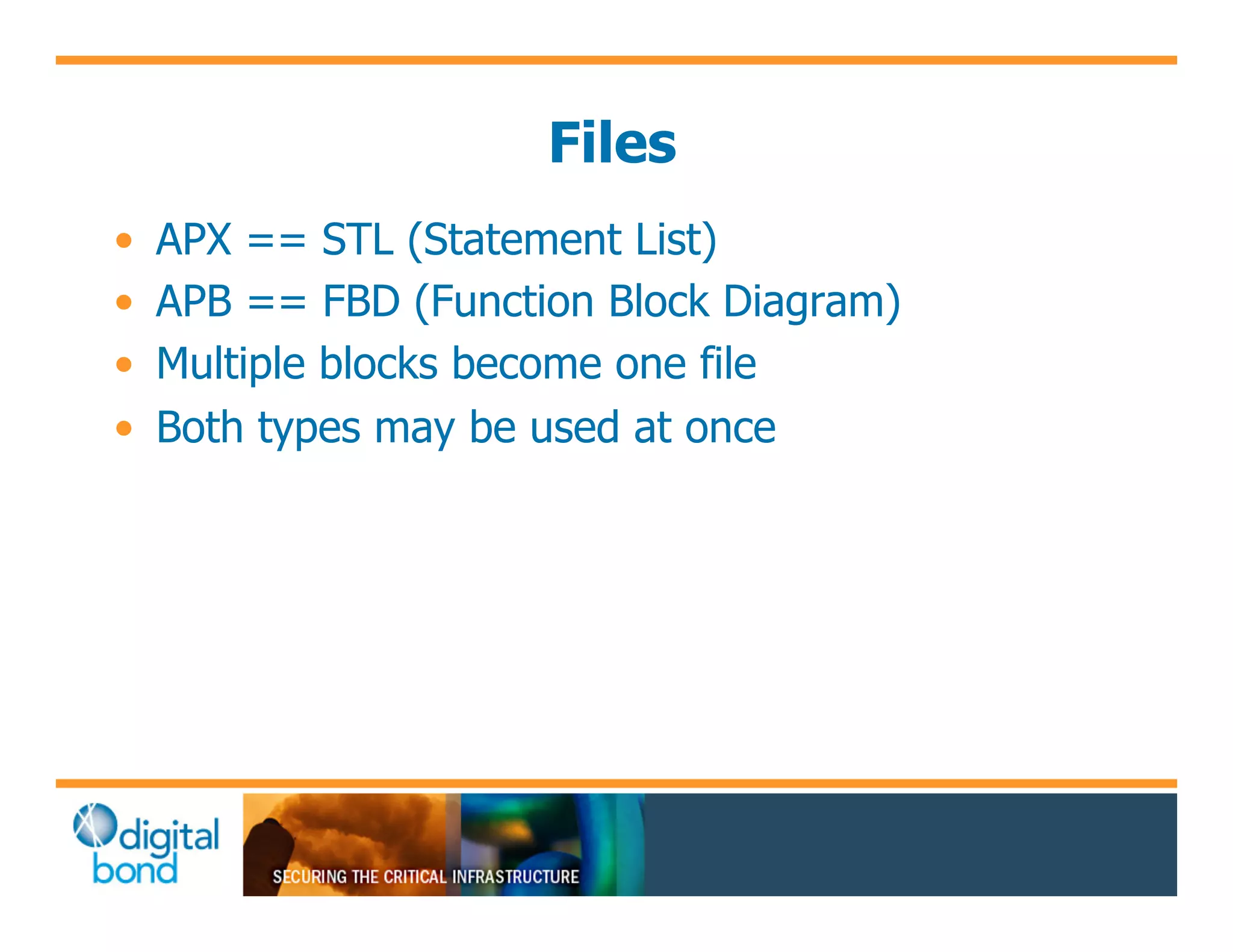
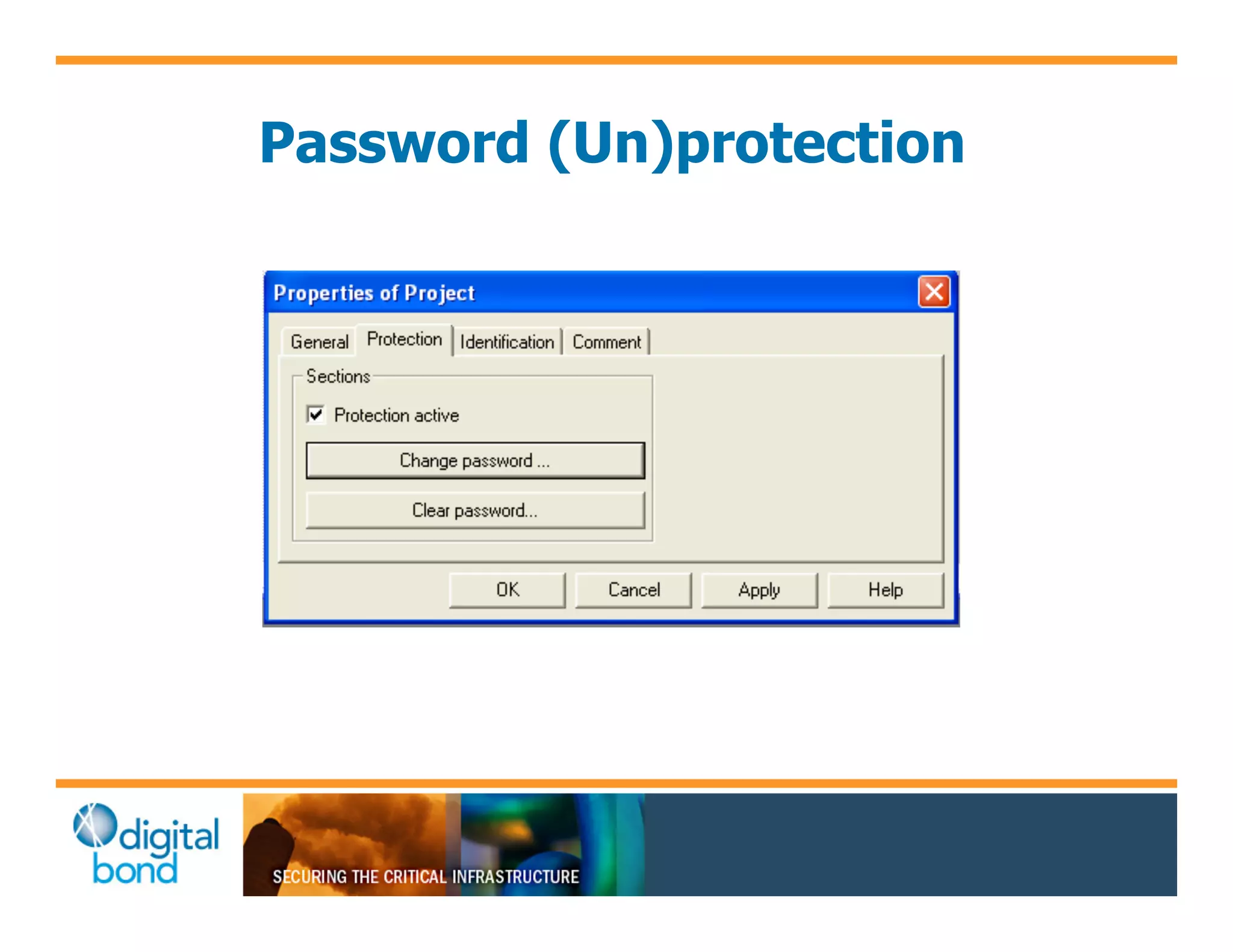
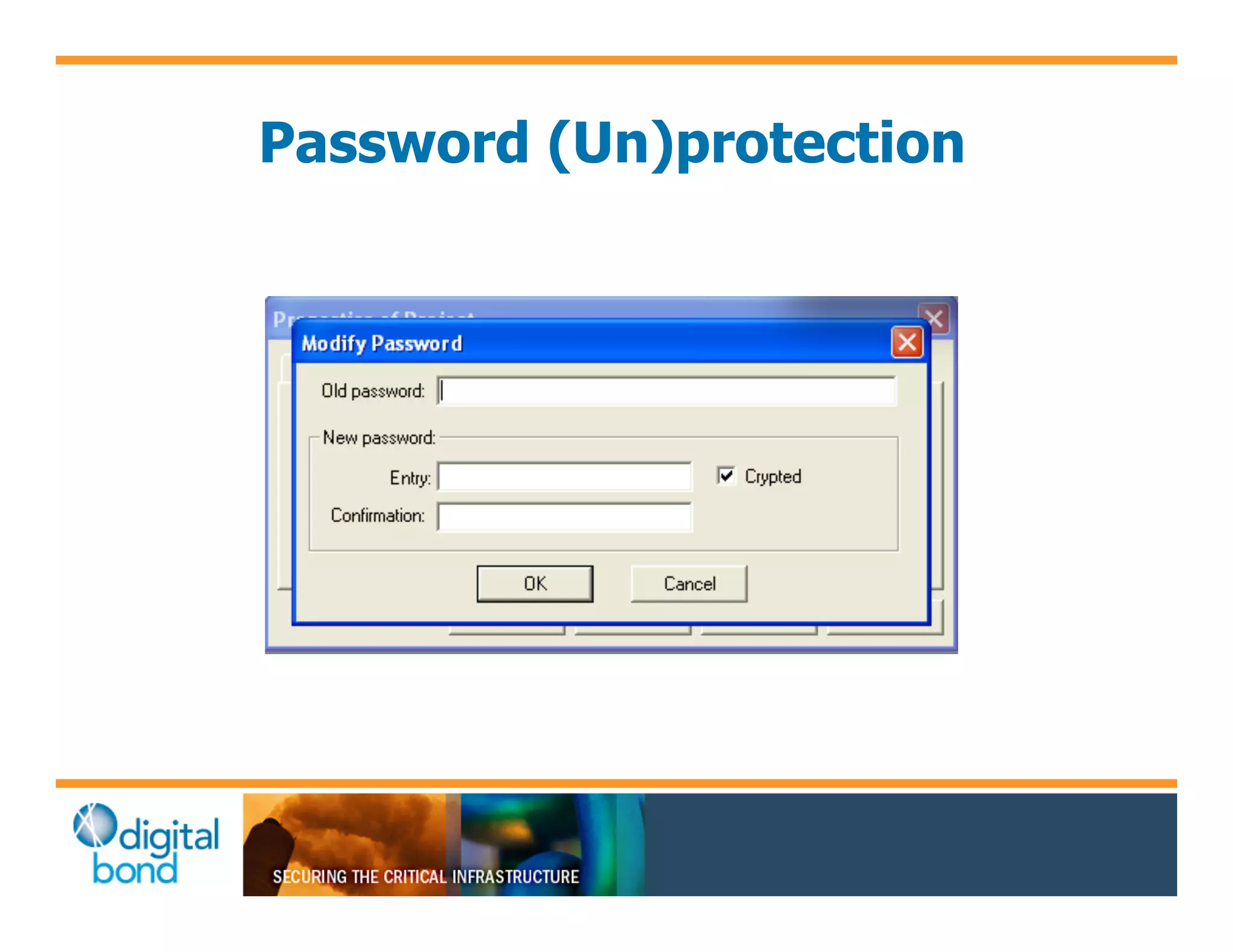
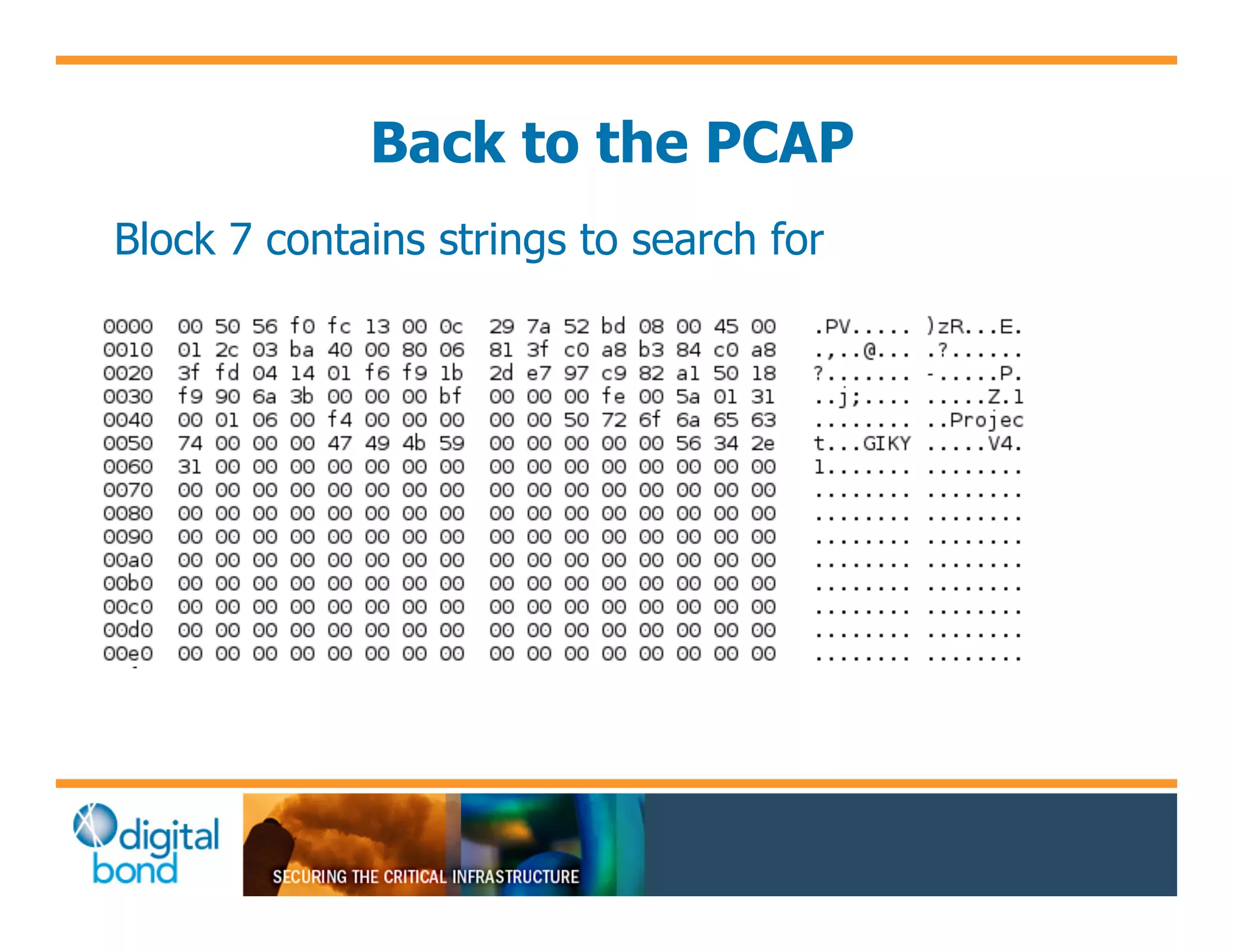
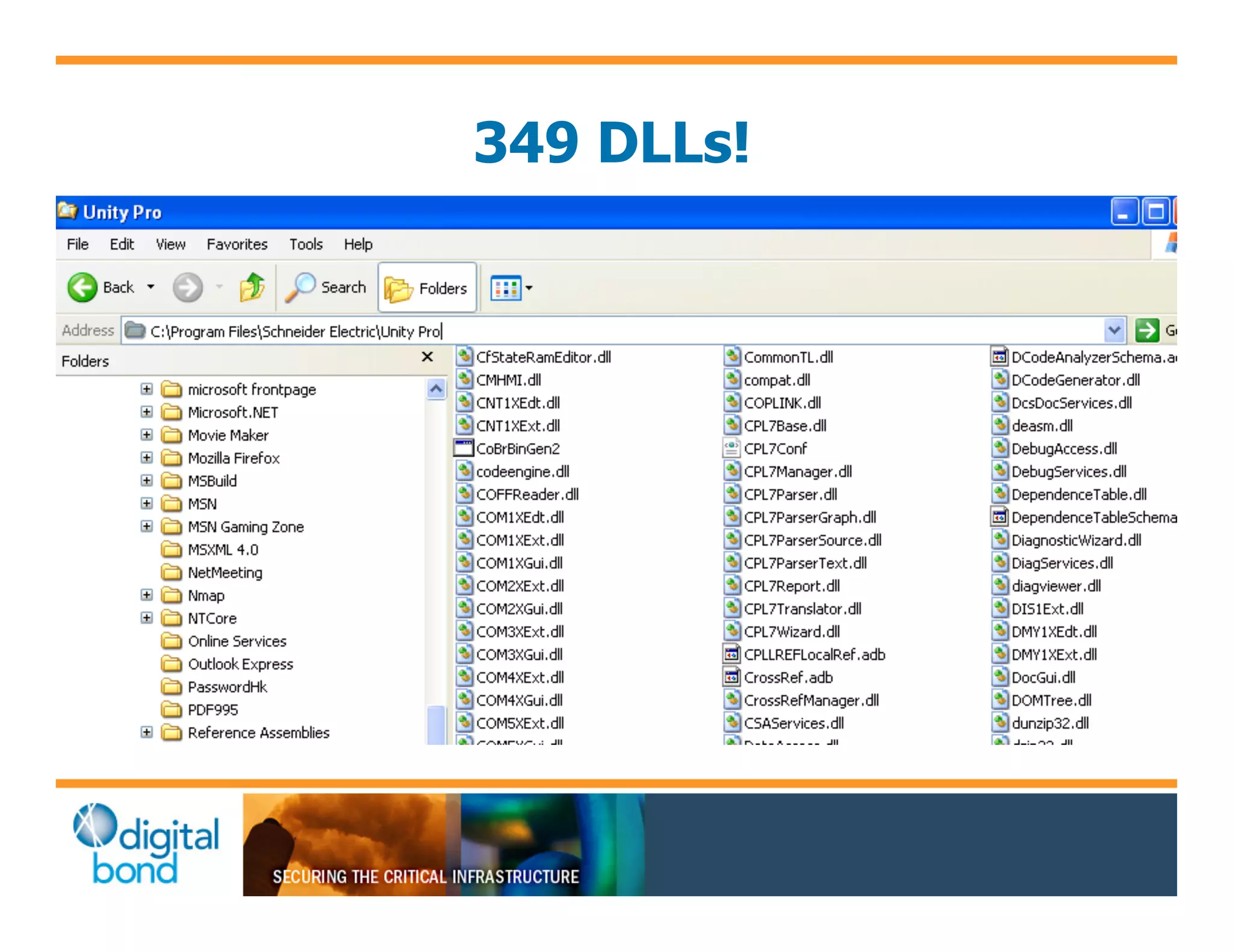
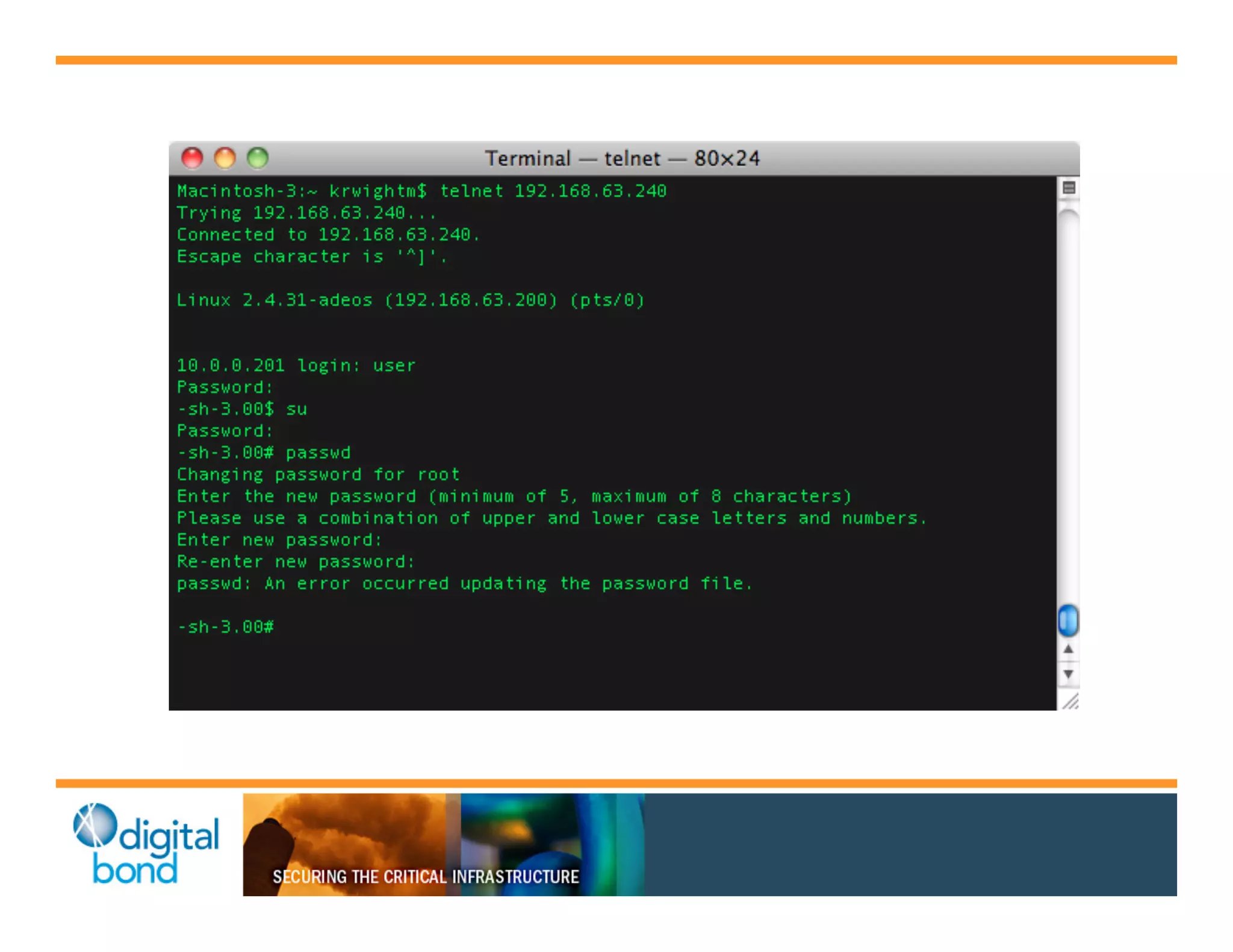
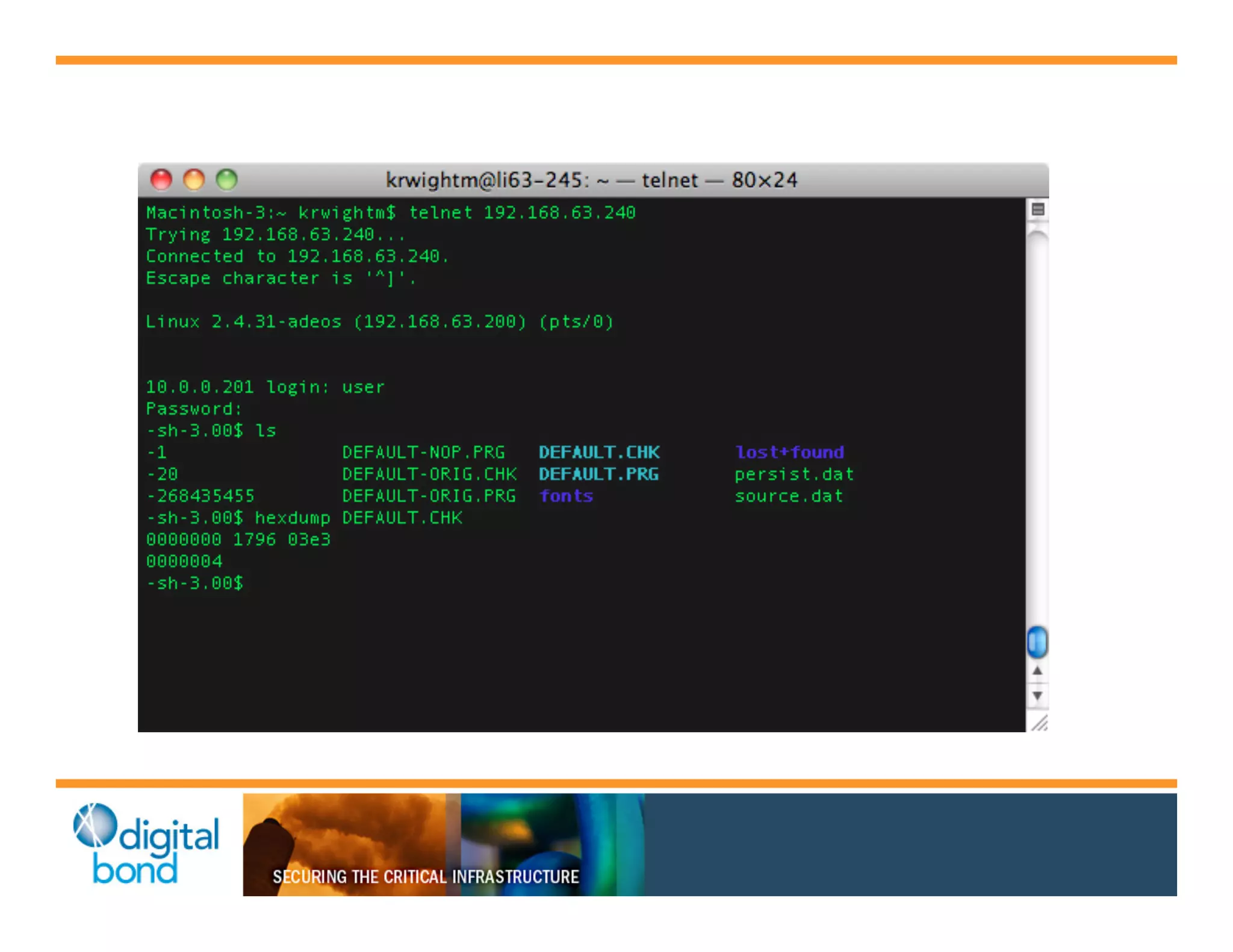
The document discusses various security vulnerabilities in programmable logic controllers (PLCs) from different manufacturers, highlighting the ease with which attackers can gain unauthorized access and modify configurations. It details specific exploits available for GE, Schneider, Koyo, and Rockwell PLCs, as well as weaknesses in their security mechanisms. The author calls for improved security measures and transparency from manufacturers in response to identified vulnerabilities.