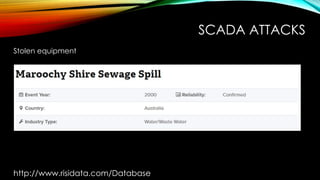
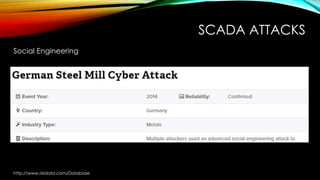
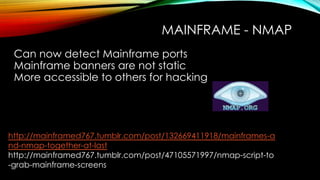
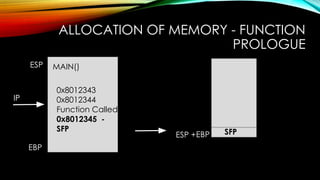
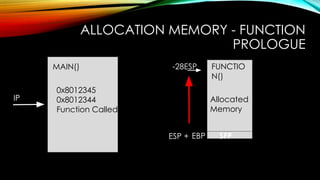
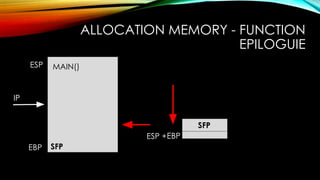
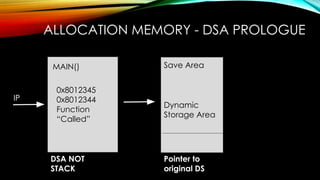
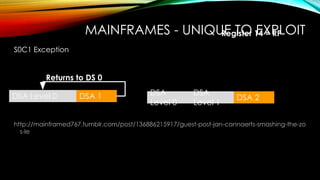
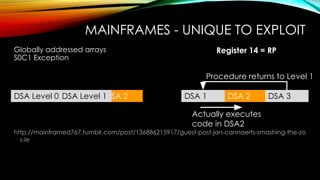
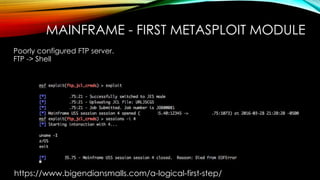
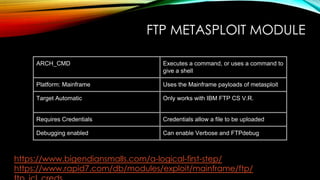
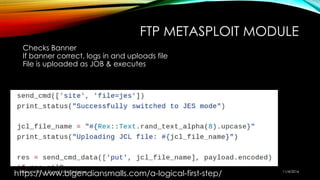
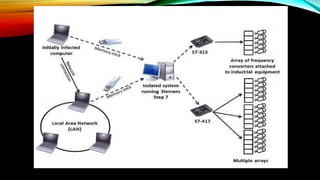
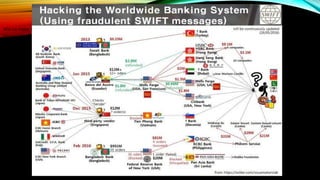
The document explores the vulnerabilities of mainframes, particularly in the context of SCADA systems, highlighting their outdated security measures and the potential for cyberattacks. It draws parallels between historical incidents like Stuxnet and the current state of mainframe security, emphasizing the need for modernization and better protection strategies. Ultimately, it serves as a cautionary note, advocating for increased awareness and research into mainframe security to avoid repeating past mistakes.