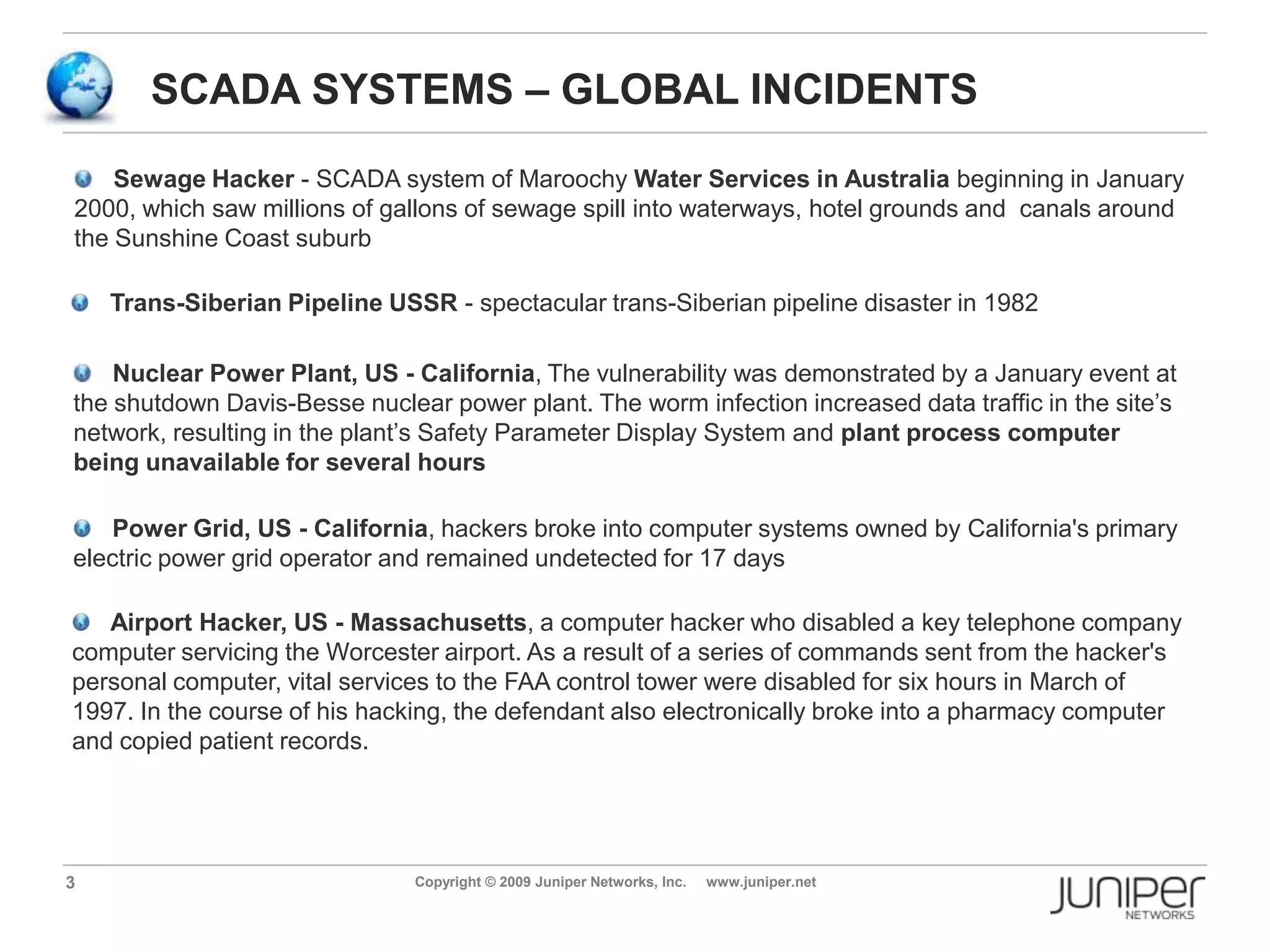
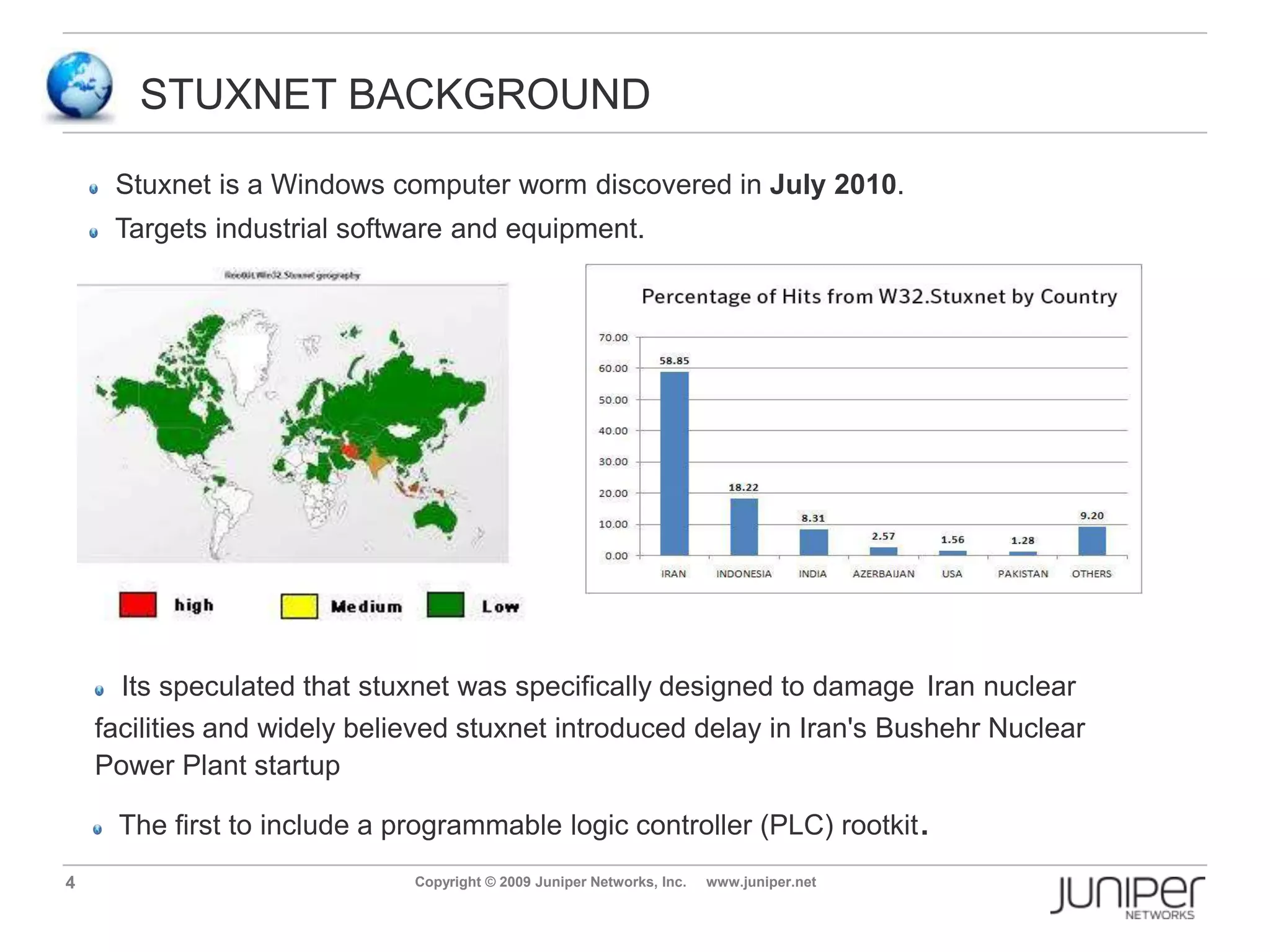
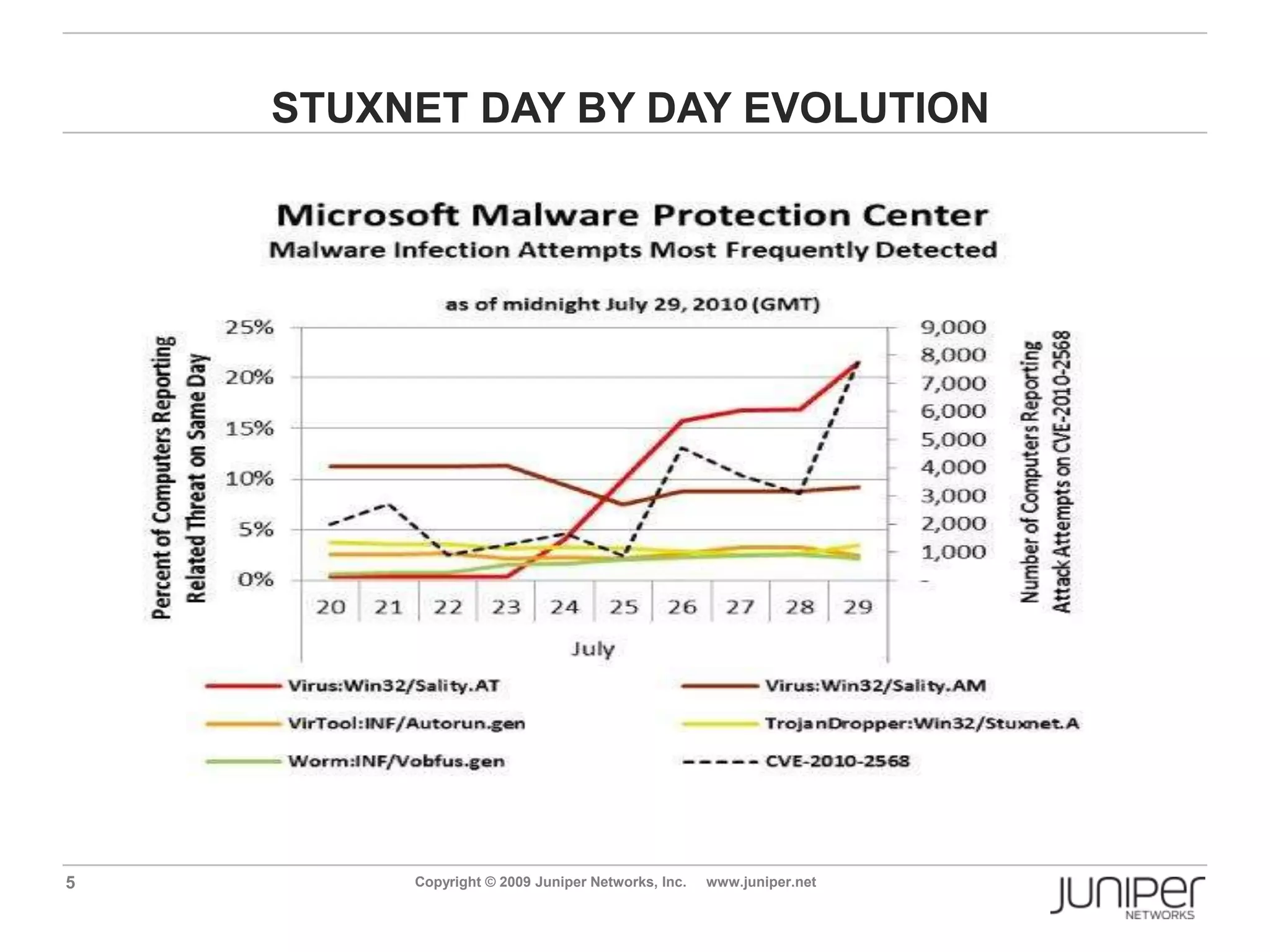
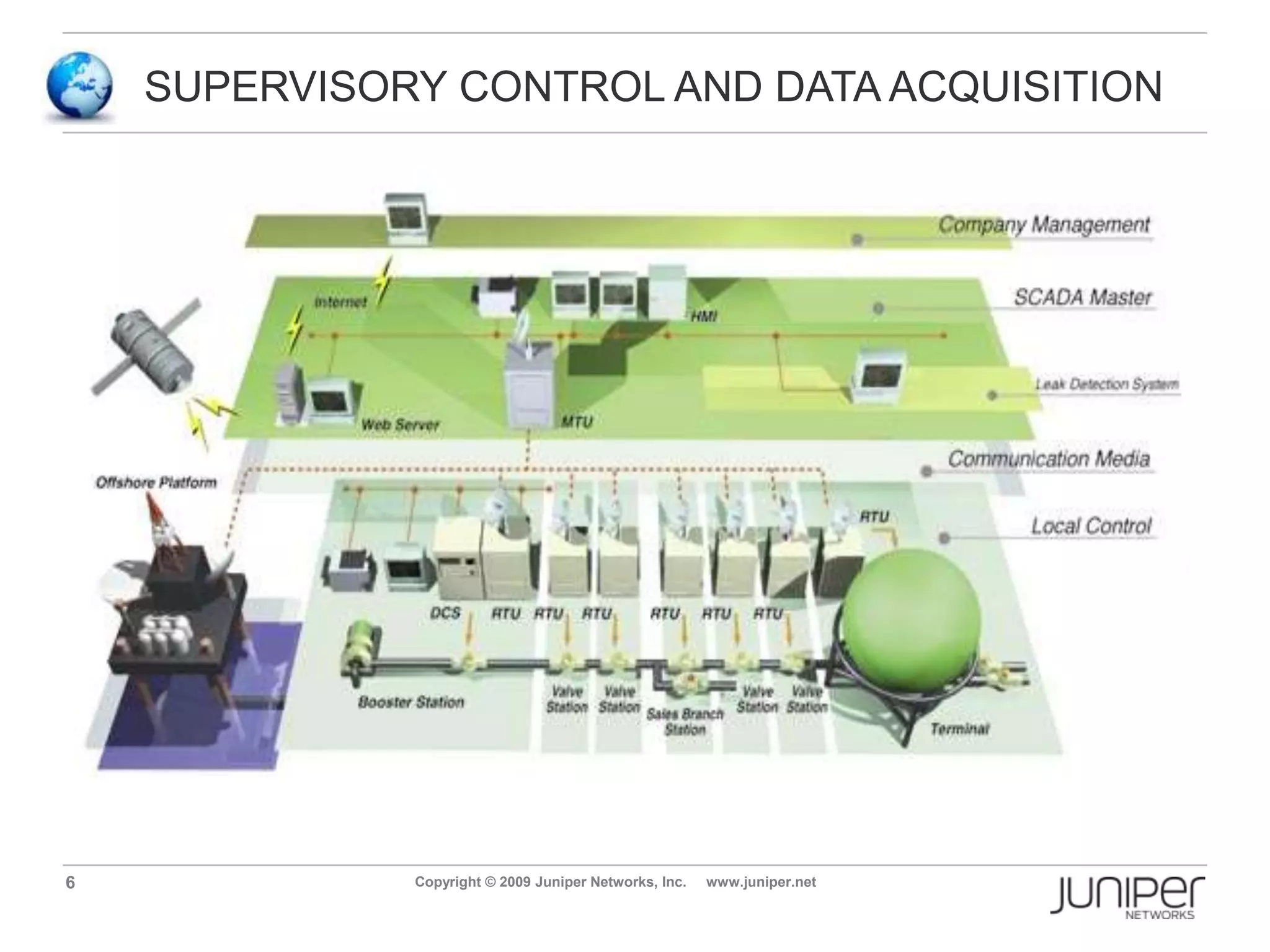
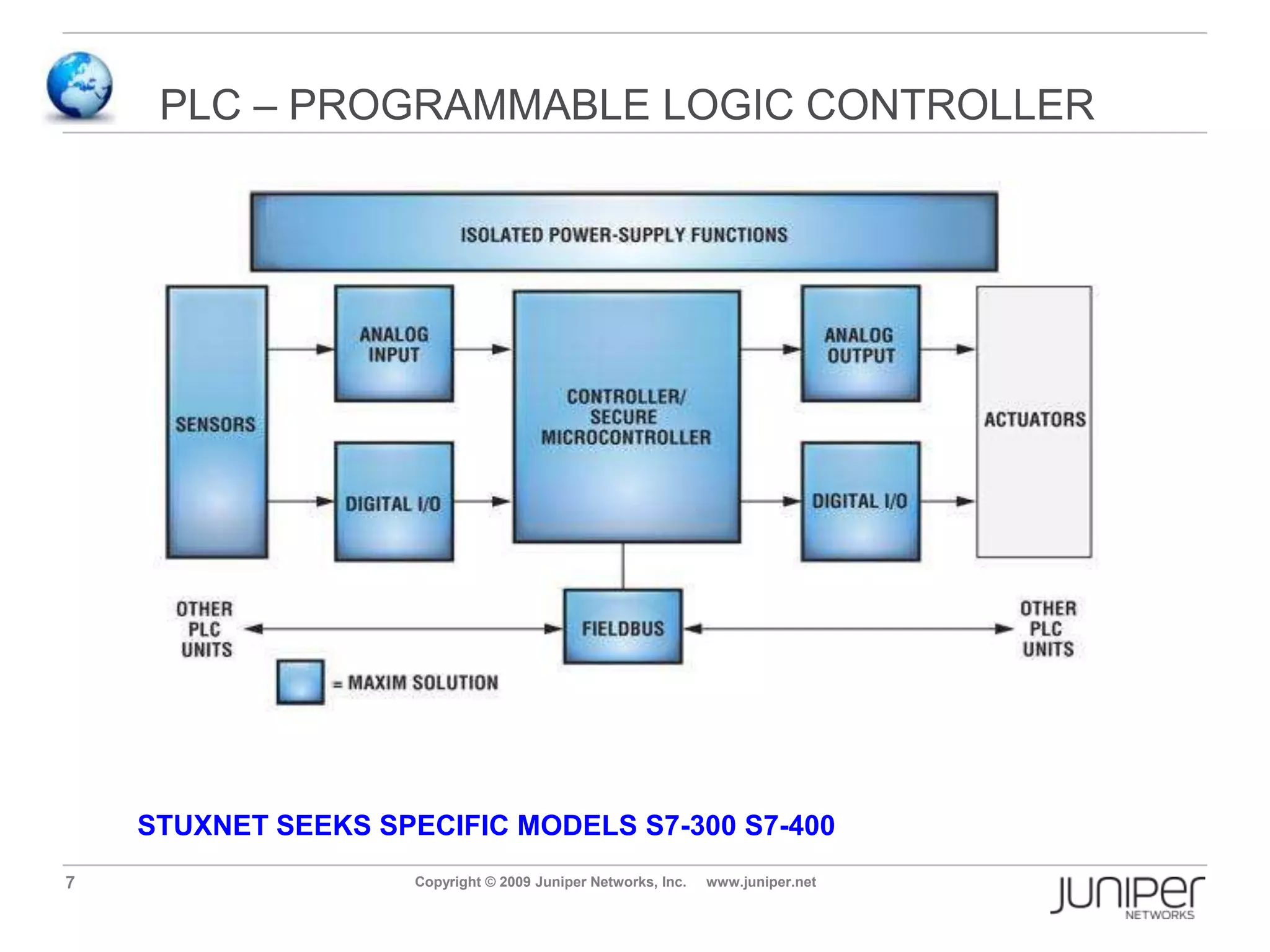
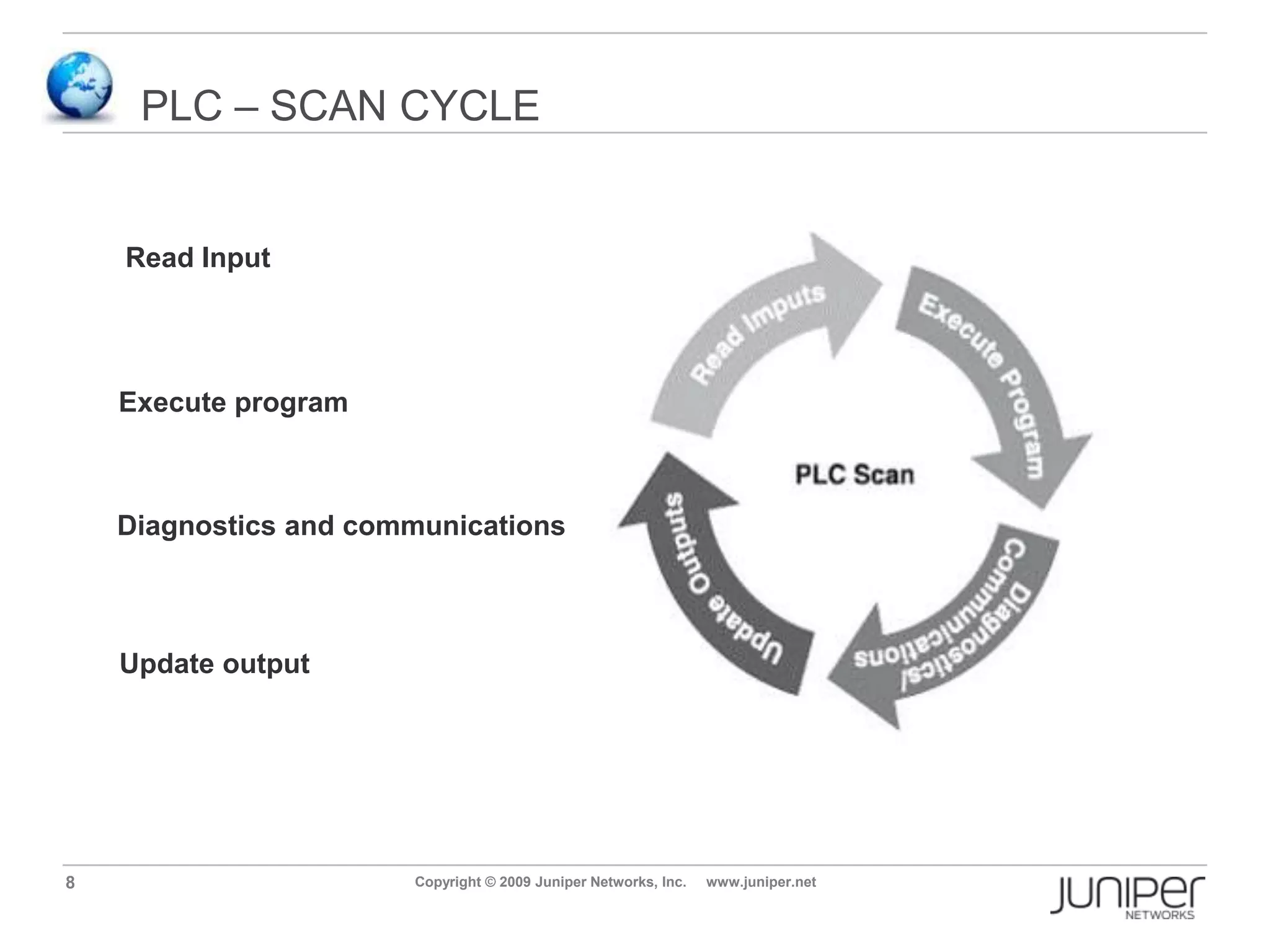
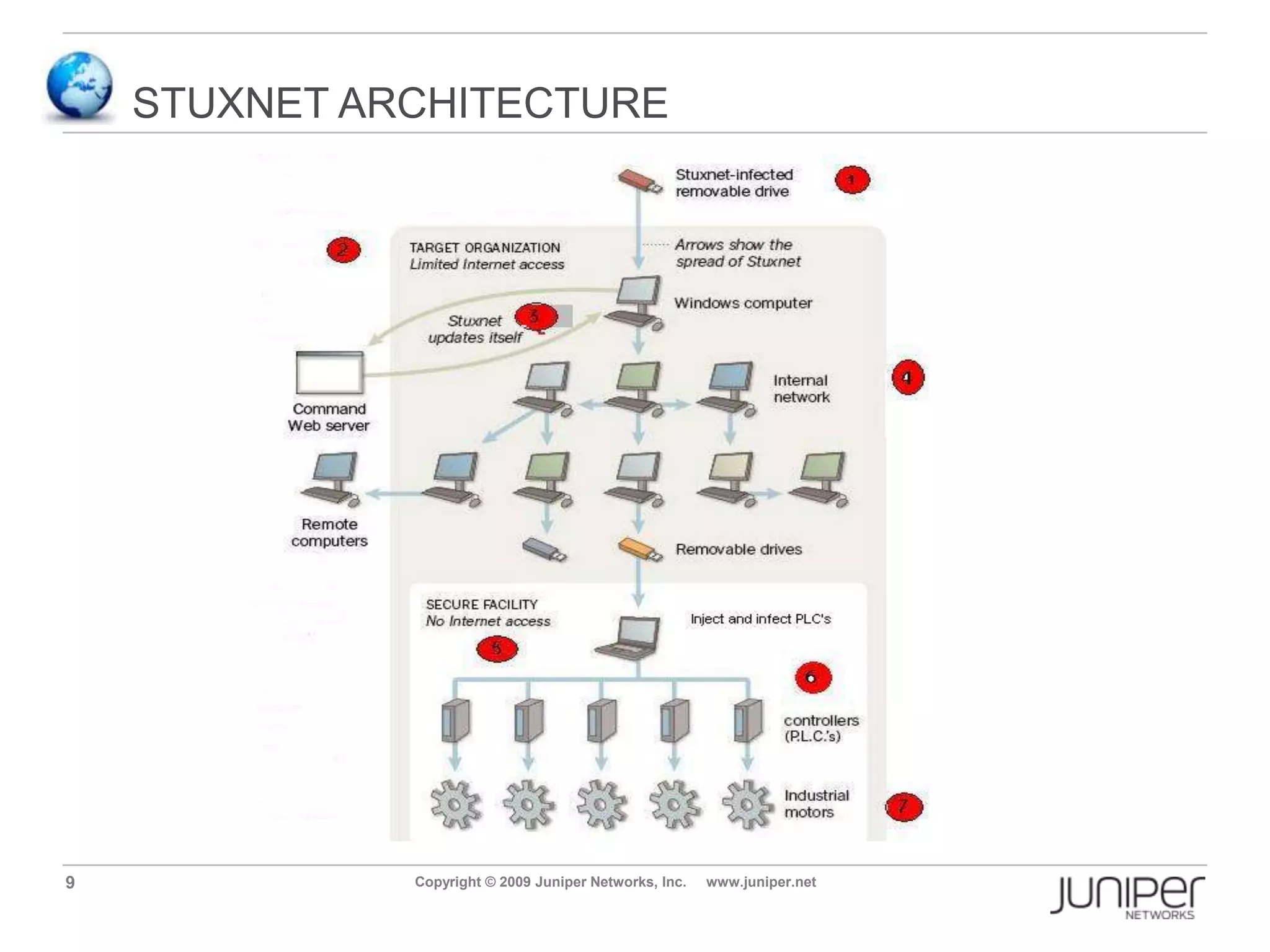
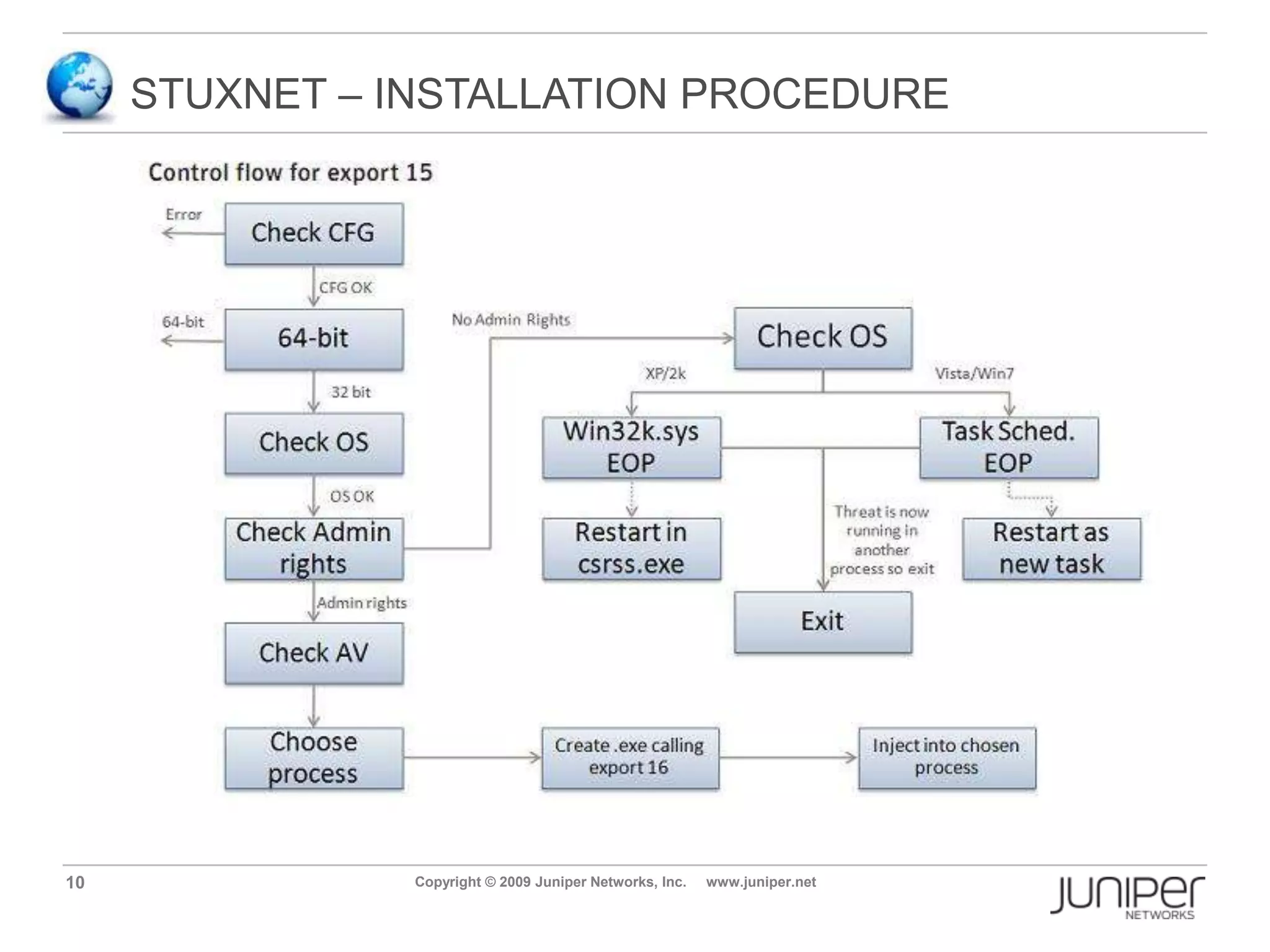
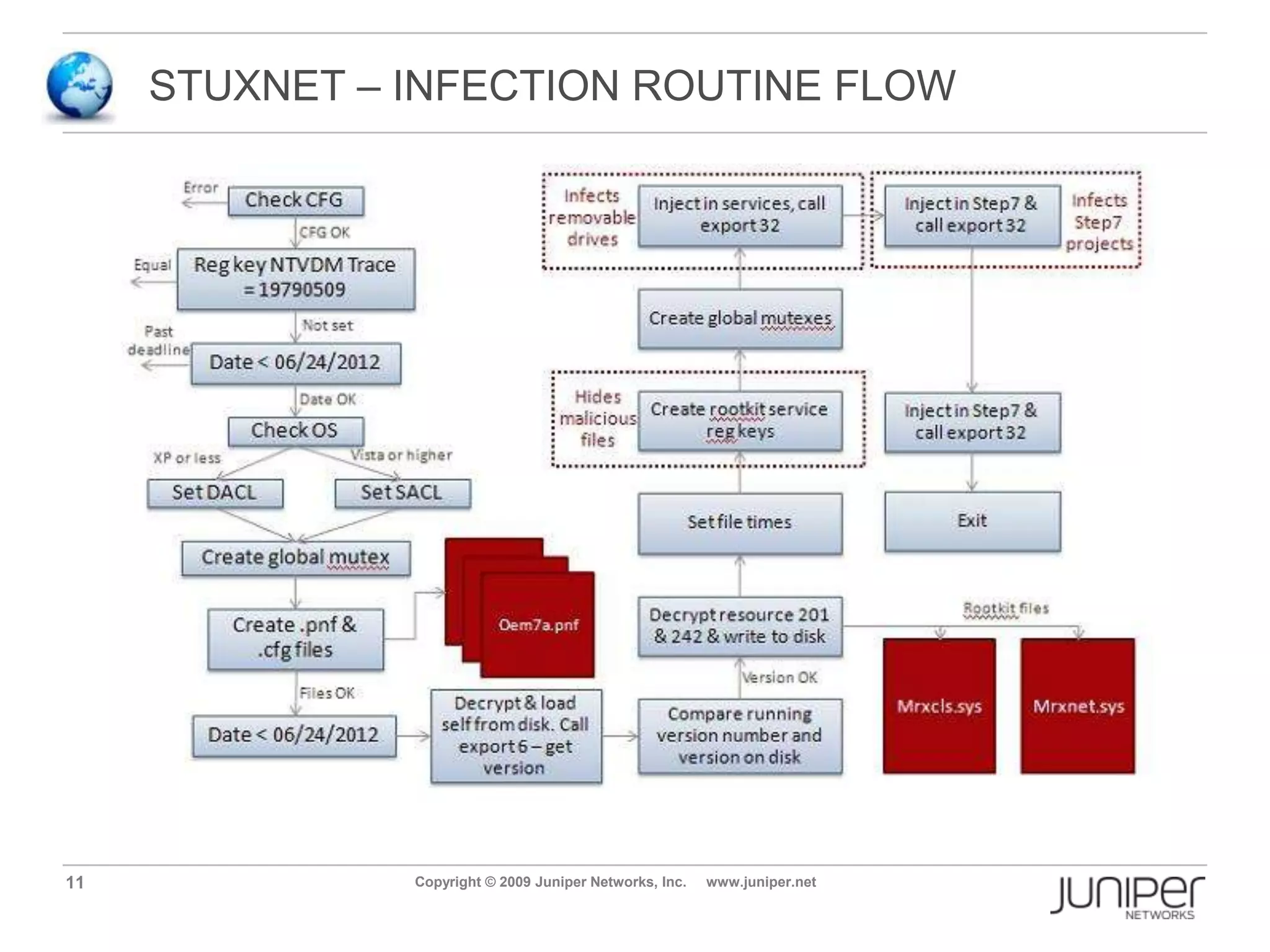
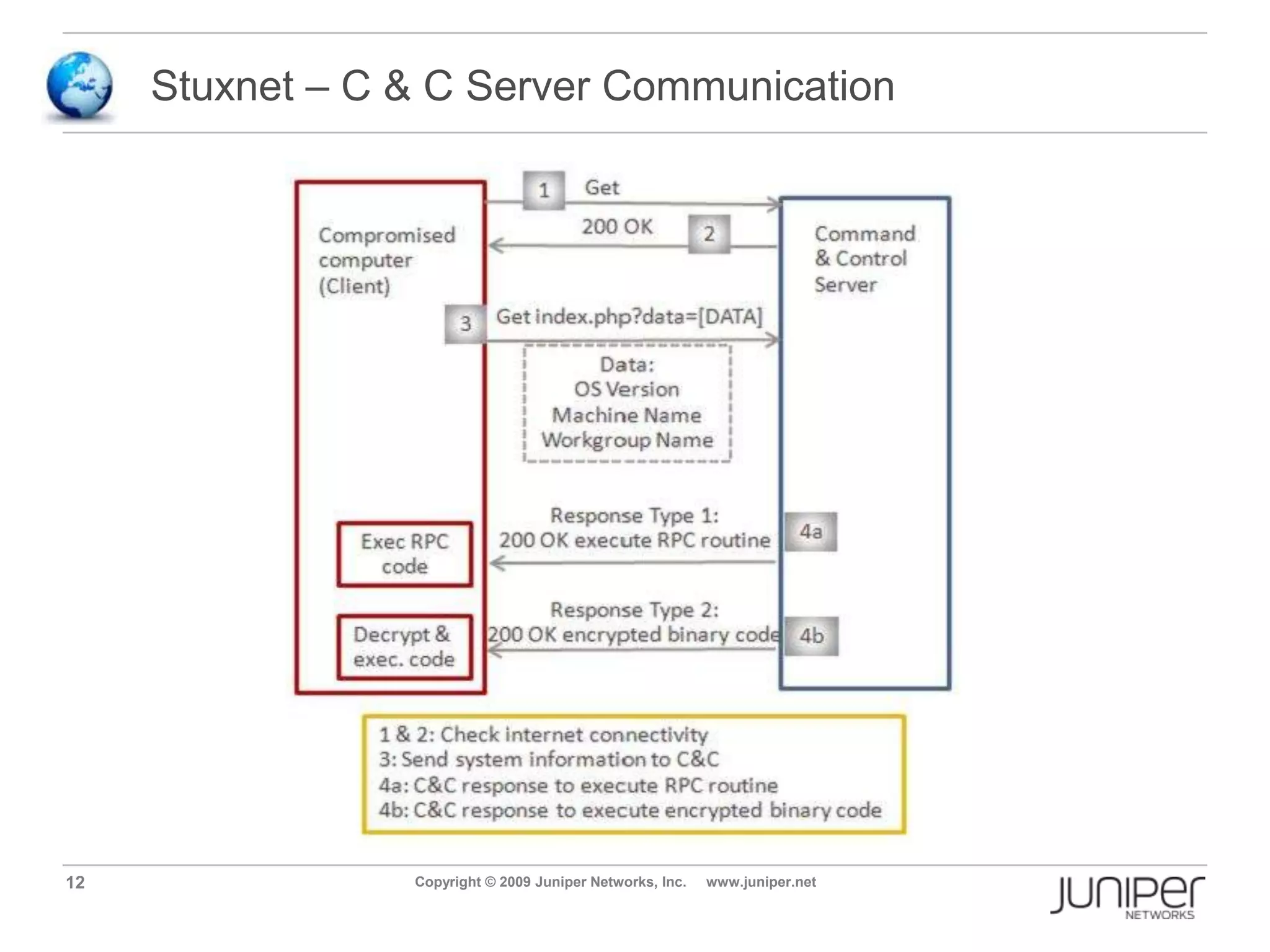
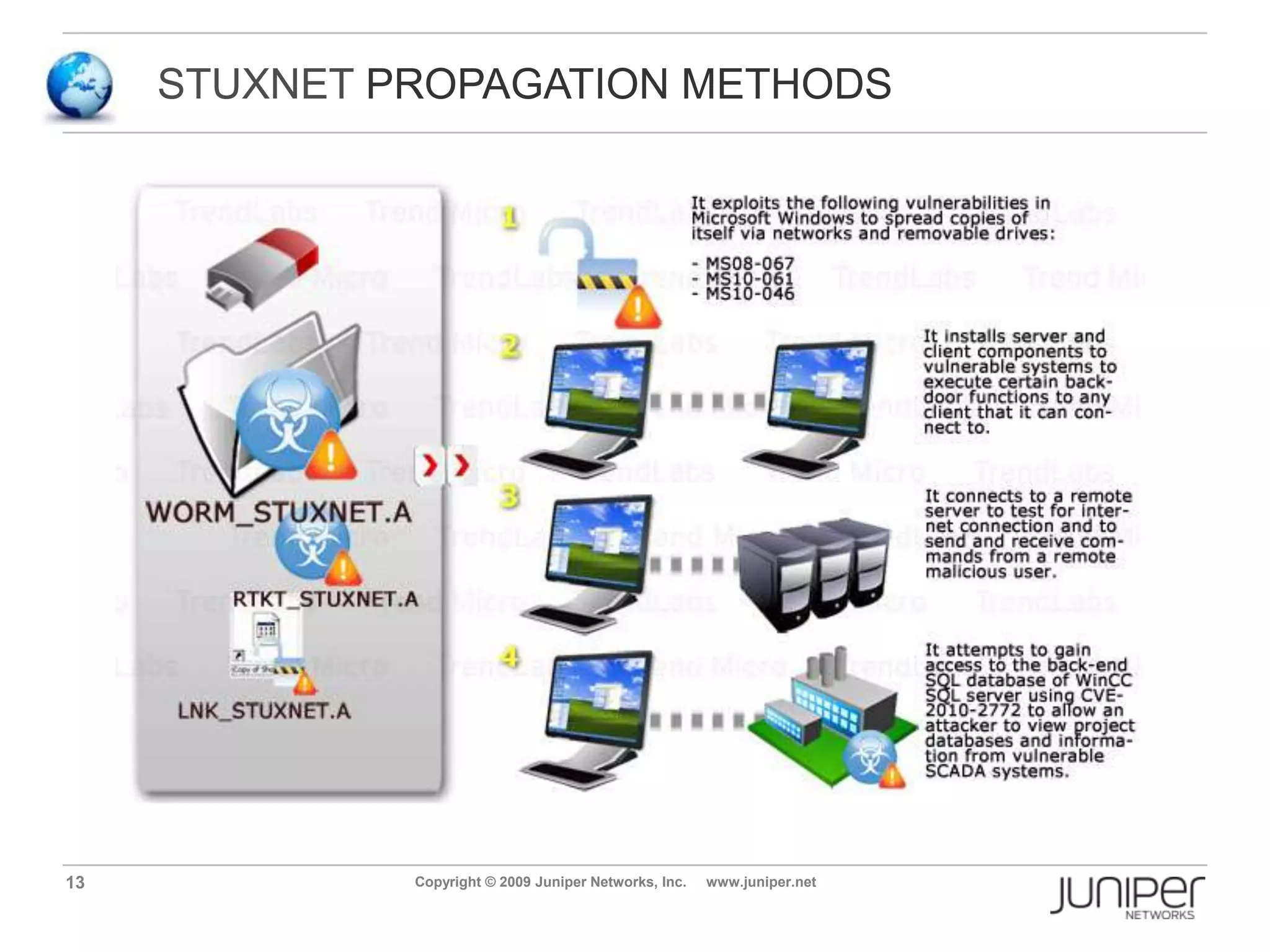
Stuxnet is a computer worm discovered in 2010 that targets industrial software and equipment. It is believed to have been designed to damage Iran's nuclear facilities. Stuxnet spreads through infected USB drives and seeks out specific models of programmable logic controllers used to automate industrial processes. It communicates with command and control servers to carry out its infection routine and propagate further through networks. Mitigation techniques for Stuxnet and other threats to industrial control systems include security information and event management systems, intrusion monitoring, and passive vulnerability scanning of control system networks.