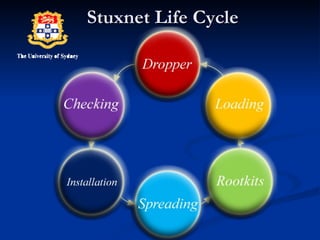
Stuxnet is a sophisticated malware that targeted Siemens supervisory control and data acquisition (SCADA) systems. It used multiple zero-day exploits to spread via USB devices and network shares to infect SCADA systems indirectly connected to the internet. Stuxnet installed rootkits to hide its files and injected itself into processes to remain undetected while sabotaging its targets. It was the first malware known to target and damage physical infrastructure.













![Thank You For any question don’t Forget to mail me at: [email_address] For more about me visit my Website http://www.amrthabet.co.cc Or My Blog http:// blog.amrthabet.co.cc](https://image.slidesharecdn.com/stuxnet-casestudy-110707064250-phpapp02/85/Stuxnet-Case-Study-16-320.jpg)
