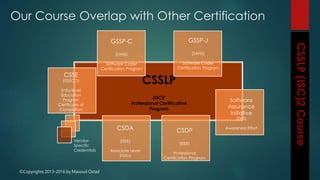
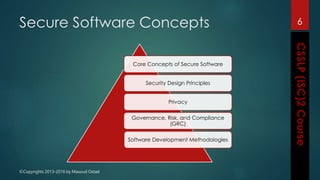
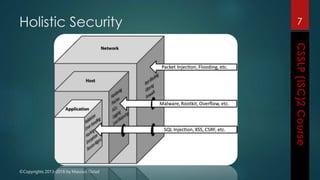
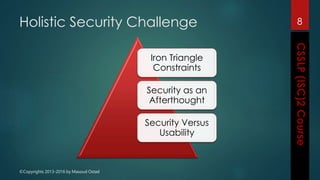
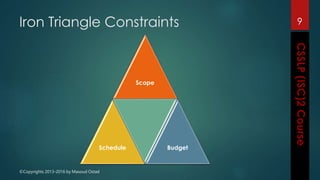
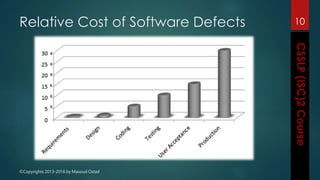
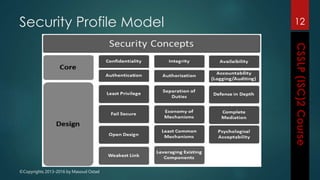
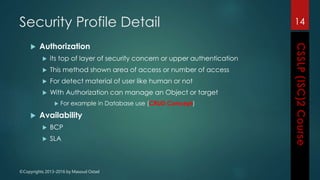
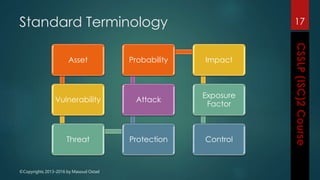
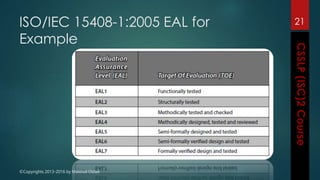
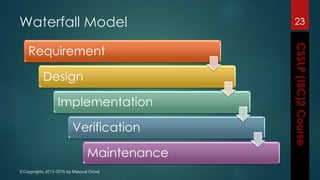
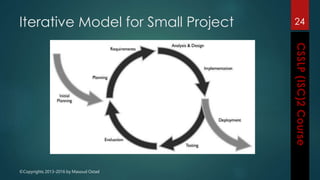
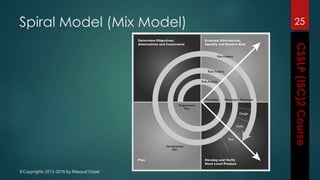
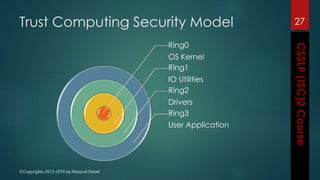
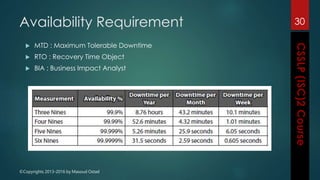
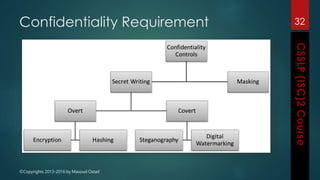
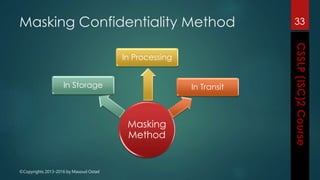
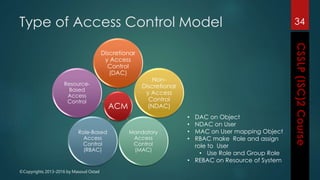
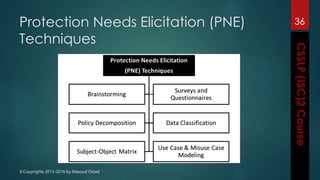
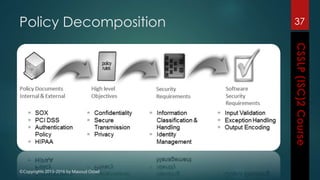
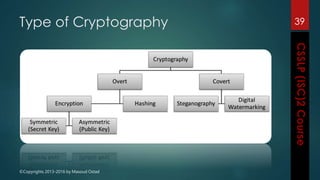
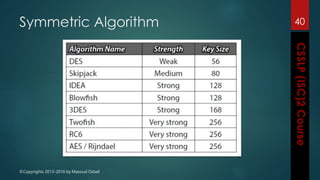
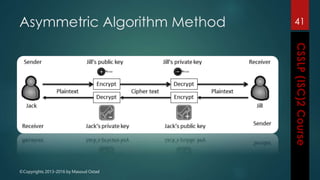
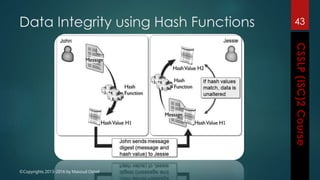
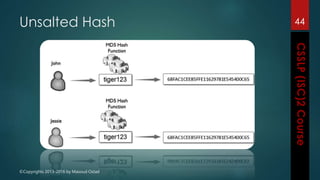
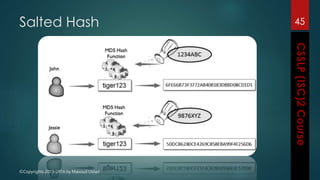
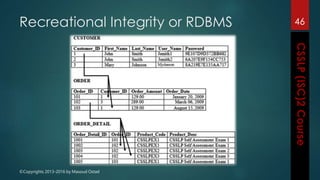
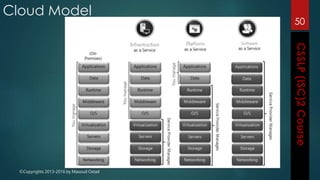
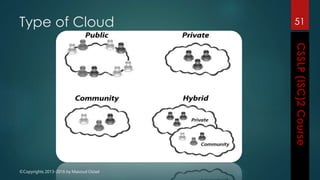
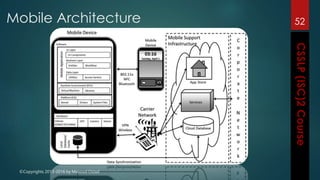
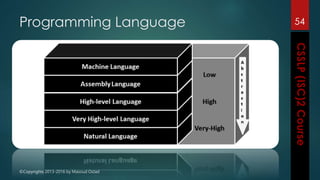
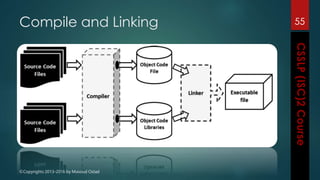
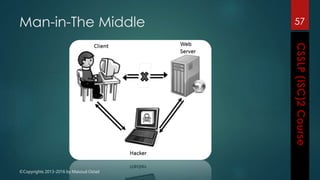
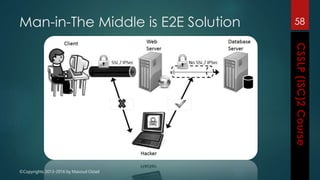
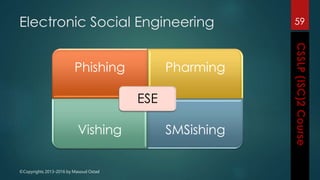
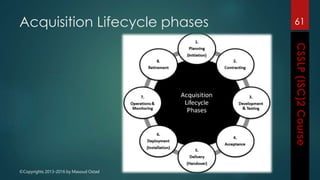
The document outlines the topics covered in a course on secure software development. It discusses secure software concepts, requirements, design, implementation, testing, deployment and maintenance. It also covers standards, methodologies, regulations and cryptography relevant to developing secure software.